Tech Bytes: Cloudflare Simplifies Wide Area Networks With Magic WAN (Sponsored)
Today on the Tech Bytes podcast we’re talking WAN architectures and how to simplify and secure them with sponsor Cloudflare. Cloudflare's Magic WAN is a network-as-a-service offering. Customers can connect data centers, branches, and users to Cloudflare's private network; add security services; and integrate with third-party SD-WANs.
The post Tech Bytes: Cloudflare Simplifies Wide Area Networks With Magic WAN (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Cloudflare Simplifies Wide Area Networks With Magic WAN (Sponsored)
Today on the Tech Bytes podcast we’re talking WAN architectures and how to simplify and secure them with sponsor Cloudflare. Cloudflare's Magic WAN is a network-as-a-service offering. Customers can connect data centers, branches, and users to Cloudflare's private network; add security services; and integrate with third-party SD-WANs.LwM2M Holds More Promise Than MQTT
While MQTT can work with LPWAN, lightweight M2M (LwM2M) is much more efficient and provides a simpler, full-stack set of protocols that offer simplified management of deployments with less power consumption and data.Network Break 382: Intel Charts DPU Roadmap; Juniper Brings Contrail SDN To Kubernetes
This week's Network Break podcast discuss Intel's roadmap for its Infrastructure Processing Units (IPUs). We get more insight into Nokia's deal to provide hardware for Azure, and examine why Juniper has extended its Contrail SDN platform to Kubernetes (hint: because of the cloud). Plus Cisco releases new Wi-Fi capabilities.MikroTik – ROSv7 – VPLS over IPv6 MPLS with LDPv6
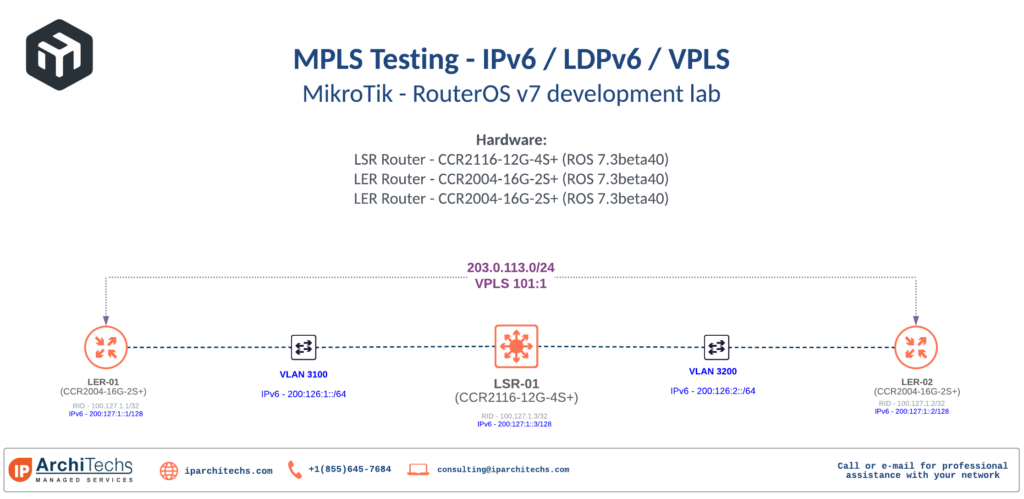
The great migration
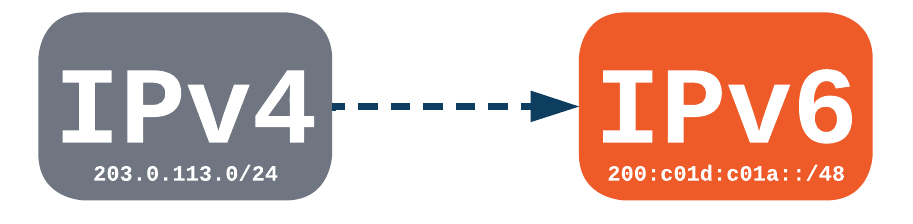
IPv6 adoption has really picked up in the last 12 months and MikroTik RouterOSv7 development is no exception. Dual stack networks are still the most common and easiest to initially deploy for carriers.
However, single stack networks with IPv4 as a service overlay are definitely on the horizon for MikroTik users now that MPLS can operate purely on IPv6.
Single stack networks are easier and cheaper to operate in the long run and are a natural evolution of dual stack networks as we begin to turn IPv4 off for underlay infrastructure.
LDPv6
There are a few different ways to distribute labels in IPv6 MPLS. SR-MPLS (less common and usually with IS-IS) and SRv6 are the other options besides LDPv6.
While I generally am in favor of SR-MPLS/SRv6 long term due to the protocol simplification and traffic management capabilities, having an IPv6 MPLS stack is a great starting point for MikroTik.
LDPv6 is defined by RFC 7552 and is fairly recent as it finalized in 2015. It generally operates in much the same way as LDPv4.
Use Cases
The most common use case among MikroTik users is more efficient subnetting of IPv4 and directly replaces LDPv4 for this Continue reading
Network performance update: Platform Week

In September 2021, we shared extensive benchmarking results of 1,000 networks all around the world. The results showed that on a range of tests (TCP connection time, time to first byte, time to last byte), and on different measures (p95, mean), Cloudflare was the fastest provider in 49% of networks around the world. Since then, we’ve worked to continuously improve performance, with the ultimate goal of being the fastest everywhere and an intermediate goal to grow the number of networks where we’re the fastest by at least 10% every Innovation Week. We met that goal during Security Week (March 2022), and we’re carrying the work over to Platform Week (May 2022).
We’re excited to update you on the latest results, but before we do: after running with this benchmark for nine months, we've also been looking for ways to improve the benchmark itself — to make it even more representative of speeds in the real world. To that end, we're expanding our measured networks from 1,000 to 3,000, to give an even more accurate sense of real world performance across the globe.
In terms of results: using the old benchmark of 1,000 networks, we’re the fastest in 69% of them. Continue reading
How Ramadan shows up in Internet trends


What happens to the Internet traffic in countries where many observe Ramadan? Depending on the country, there are clear shifts and changing patterns in Internet use, particularly before dawn and after sunset.
This year, Ramadan started on April 2, and it continued until May 1, 2022, (dates vary and are dependent on the appearance of the crescent moon). For Muslims, it is a period of introspection, communal prayer and also of fasting every day from dawn to sunset. That means that people only eat at night (Iftar is the first meal after sunset that breaks the fast and often also a family or community event), and also before sunrise (Suhur).
In some countries, the impact is so big that we can see in our Internet traffic charts when the sun sets. Sunrise is more difficult to check in the charts, but in the countries more impacted, people wake up much earlier than usual and were using the Internet in the early morning because of that.
Cloudflare Radar data shows that Internet traffic was impacted in several countries by Ramadan, with a clear increase in traffic before sunrise, and a bigger than usual decrease after sunset. All times Continue reading
Proof of Stake and our next experiments in web3


A little under four years ago we announced Cloudflare's first experiments in web3 with our gateway to the InterPlanetary File System (IPFS). Three years ago we announced our experimental Ethereum Gateway. At Cloudflare, we often take experimental bets on the future of the Internet to help new technologies gain maturity and stability and for us to gain deep understanding of them.
Four years after our initial experiments in web3, it’s time to launch our next series of experiments to help advance the state of the art. These experiments are focused on finding new ways to help solve the scale and environmental challenges that face blockchain technologies today. Over the last two years there has been a rapid increase in the use of the underlying technologies that power web3. This growth has been a catalyst for a generation of startups; and yet it has also had negative externalities.
At Cloudflare, we are committed to helping to build a better Internet. That commitment balances technology and impact. The impact of certain older blockchain technologies on the environment has been challenging. The Proof of Work (PoW) consensus systems that secure many blockchains were instrumental in the bootstrapping of the web3 ecosystem. However, these Continue reading
Public access for our Ethereum and IPFS gateways now available


Today we are excited to announce that our Ethereum and IPFS gateways are publicly available to all Cloudflare customers for the first time. Since our announcement of our private beta last September the interest in our Eth and IPFS gateways has been overwhelming. We are humbled by the demand for these tools, and we are excited to get them into as many developers' hands as possible. Starting today, any Cloudflare customer can log into the dashboard and configure a zone for Ethereum, IPFS, or both!
Over the last eight months of the private beta, we’ve been busy working to fully operationalize the gateways to ensure they meet the needs of our customers!
First, we have created a new API with end-to-end managed hostname deployment. This ensures the creation and management of gateways as you continue to scale remains extremely quick and easy! It is paramount to give time and focus back to developers to focus on your core product and services and leave the infrastructural components to us!
Second, we’ve added a brand new UI bringing web3 to Cloudflare's zone-level dashboard. Now, regardless of the workflow you are used to, we have parity between our UI and API to ensure Continue reading
Serving Cloudflare Pages sites to the IPFS network


Four years ago, Cloudflare went Interplanetary by offering a gateway to the IPFS network. This meant that if you hosted content on IPFS, we offered to make it available to every user of the Internet through HTTPS and with Cloudflare protection. IPFS allows you to choose a storage provider you are comfortable with, while providing a standard interface for Cloudflare to serve this data.
Since then, businesses have new tools to streamline web development. Cloudflare Workers, Pages, and R2 are enabling developers to bring services online in a matter of minutes, with built-in scaling, security, and analytics.
Today, we're announcing we're bridging the two. We will make it possible for our customers to serve their sites on the IPFS network.
In this post, we'll learn how you will be able to build your website with Cloudflare Pages, and leverage the IPFS integration to make your content accessible and available across multiple providers.
A primer on IPFS
The InterPlanetary FileSystem (IPFS) is a peer-to-peer network for storing content on a distributed file system. It is composed of a set of computers called nodes that store and relay content using a common addressing system. In short, a set of participants Continue reading
Gaining visibility in IPFS systems


We have been operating an IPFS gateway for the last four years. It started as a research experiment in 2018, providing end-to-end integrity with IPFS. A year later, we made IPFS content faster to fetch. Last year, we announced we were committed to making IPFS gateway part of our product offering. Through this process, we needed to inform our design decisions to know how our setup performed.
To this end, we've developed the IPFS Gateway monitor, an observability tool that runs various IPFS scenarios on a given gateway endpoint. In this post, you'll learn how we use this tool and go over discoveries we made along the way.
Refresher on IPFS
IPFS is a distributed system for storing and accessing files, websites, applications, and data. It's different from a traditional centralized file system in that IPFS is completely distributed. Any participant can join and leave at any time without the loss of overall performance.
However, in order to access any file in IPFS, users cannot just use web browsers. They need to run an IPFS node to access the file from IPFS using its own protocol. IPFS Gateways play the role of enabling users to do this using only Continue reading
The Path the Resolverless DNS
Using the DNS without directly using recursive resolvers seems like an approach that is totally alien to the DNS as we know it, so it might be useful to ask: How did we get to this point where a resolverless form of DNS name resolution makes some sense? And, to whom does it make sense?Networking Hardware/Software Disaggregation in 2022
I started preparing the materials for the SDN – 10 years later webinar, and plan to publish a series of blog posts documenting what I found on various aspects of what could be considered SDN1. I’m pretty sure I missed quite a few things; your comments are most welcome.
Let’s start with an easy one: software/hardware disaggregation in network devices.
Open-Source Network Operating Systems
I found several widely-used open-source2 network operating systems:
Networking Hardware/Software Disaggregation in 2022
I started preparing the materials for the SDN – 10 years later webinar, and plan to publish a series of blog posts documenting what I found on various aspects of what could be considered SDN1. I’m pretty sure I missed quite a few things; your comments are most welcome.
Let’s start with an easy one: software/hardware disaggregation in network devices.
Open-Source Network Operating Systems
I found several widely-used open-source2 network operating systems:
Learning BGP Module 2 Lesson 2: Peering, Part 2 – Video
Russ White continues the discussion about BGP peering in part two of this lesson. Topics covered include: -Challenges with link-local next hop with IPv6 -How different BGP implementations handle these challenges -Promiscuous peering -Mitigating the attack surface of promiscuous peers -BGP Capabilities -Filtering before advertising/RFC 8212 You can subscribe to the Packet Pushers’ YouTube channel […]
The post Learning BGP Module 2 Lesson 2: Peering, Part 2 – Video appeared first on Packet Pushers.
Part 1: Rethinking Cache Purge, Fast and Scalable Global Cache Invalidation
There is a famous quote attributed to a Netscape engineer: “There are only two difficult problems in computer science: cache invalidation and naming things.” While naming things does oddly take up an inordinate amount of time, cache invalidation shouldn’t.
In the past we’ve written about Cloudflare’s incredibly fast response times, whether content is cached on our global network or not. If content is cached, it can be served from a Cloudflare cache server, which are distributed across the globe and are generally a lot closer in physical proximity to the visitor. This saves the visitor’s request from needing to go all the way back to an origin server for a response. But what happens when a webmaster updates something on their origin and would like these caches to be updated as well? This is where cache “purging” (also known as “invalidation”) comes in.
Customers thinking about setting up a CDN and caching infrastructure consider questions like:
- How do different caching invalidation/purge mechanisms compare?
- How many times a day/hour/minute do I expect to purge content?
- How quickly can the cache be purged when needed?
This blog will discuss why invalidating cached assets is hard, what Cloudflare has done to make Continue reading
Learning BGP Module 2 Lesson 1: Peering Part 1 – Video
The first video in this second module of Russ White’s BGP course covers peering, including why BGP uses TCP for transport, passive and active peer, multi-hop peering, collisions, and more. Russ White is a network architect, author, and instructor. You can subscribe to the Packet Pushers’ YouTube channel for more videos as they are published. […]
The post Learning BGP Module 2 Lesson 1: Peering Part 1 – Video appeared first on Packet Pushers.