Simplifying Security by Stepping Back
If you can step back and establish security practices that address each of the two types of vulnerabilities, you’ll go a long way toward simplifying security.The Hedge 81: Jana Iyengar and QUIC

QUIC is a middle-aged protocol at this point—it’s several years old, and widely deployed although TCP still dominates the transport layer of the Internet. In this episode of the Hedge, Jana Iyengar joins Alvaro Retana and Russ White to discuss the motivation for developing QUIC, and its ongoing development and deployment.
The Common Room: How an Artist Is Connecting Rural Indonesia One Village at a Time

A young person scrolls through Instagram to see the latest updates on their favorite profiles. To many around the world this doesn’t seem strange, but for a hamlet outside of a small village in Indonesia’s rural southwest, it’s revolutionary. And it’s in part thanks to the work of an Internet entrepreneur named Gustaff Harriman Iskandar. […]
The post The Common Room: How an Artist Is Connecting Rural Indonesia One Village at a Time appeared first on Internet Society.
Day Two Cloud 095: Grappling With The Open Source Business Model
Today on Day Two Cloud we get into a whole lot of things. For example, what is IT's value in the age of cloud? How can IT figure out what's actually providing value to the business vs. undifferentiated heavy lifting? How companies built on open-source software make their money? Our guest is Stu Miniman, Director of Market Insights at Red Hat.
The post Day Two Cloud 095: Grappling With The Open Source Business Model appeared first on Packet Pushers.
Day Two Cloud 095: Grappling With The Open Source Business Model
Today on Day Two Cloud we get into a whole lot of things. For example, what is IT's value in the age of cloud? How can IT figure out what's actually providing value to the business vs. undifferentiated heavy lifting? How companies built on open-source software make their money? Our guest is Stu Miniman, Director of Market Insights at Red Hat.Nokia Lab | LAB 5 RSVP-TE basic |
- basic RSVP-TE configuration
- what we need for RSVP-TE infrastructure?
- configure IGP with TE extension (e.g. OSPF)
- add all p2p and "system" interfaces to MPLS and RSVP context
- Do routers establish RSVP-TE adjacency? Why?
- create LSP from R1 to R6 with an "empty" path
- examine LSP signaling process(use debug or Wireshark)
- capture PATH and RESV messages and examine their content
- describe label signaling process
- examine PSB and RSB (see "useful debug commands" section)
- break some link with active RSVP session and capture PathTear and ResvTear messages
- describe tearing down process and message purpose
- RSVP-TE timers
- break some link with active RSVP session (e.g. LSP to_R6)
- examine LSP on Head-end and check LSP operation status
- What is LSP operation status?
- Continue reading
Netsim-tools Release 0.6: BGP, IS-IS, SR-MPLS, FRR
TL&DR: If you want to test BGP, OSPF, IS-IS, or SR-MPLS in a virtual lab, you might build the lab faster with netsim-tools release 0.6.
In the netsim-tools release 0.6 I focused on adding routing protocol functionality:
- IS-IS on Cisco IOS/IOS XE, Cisco NX-OS, Arista EOS, FRR, and Junos.
- BGP on the same set of platforms, including support for multiple autonomous systems, EBGP, IBGP full mesh, IBGP with route reflectors, next-hop-self control, and BGP/IGP interaction.
- Segment Routing with MPLS on Cisco IOS XE and Arista EOS.
You’ll also get:
netsim-tools Release 0.6: BGP, IS-IS, SR-MPLS, FRR
TL&DR: If you want to test BGP, OSPF, IS-IS, or SR-MPLS in a virtual lab, you might build the lab faster with netsim-tools release 0.6.
In the netsim-tools release 0.6 I focused on adding routing protocol functionality:
- IS-IS on Cisco IOS/IOS XE, Cisco NX-OS, Arista EOS, FRR, and Junos.
- BGP on the same set of platforms, including support for multiple autonomous systems, EBGP, IBGP full mesh, IBGP with route reflectors, next-hop-self control, and BGP/IGP interaction.
- Segment Routing with MPLS on Cisco IOS XE and Arista EOS.
You’ll also get:
Working with Linux VRFs
The concept of VRFs is likely one that you’re familiar with. They are the de facto standard when we talk about isolating layer 3 networks. As we’ve talked about previously, they are used extensively in applications such as MPLS VPNs and really provide the foundation for layer 3 network isolation. They do this by allowing the creation of multiple routing tables. Any layer 3 construct can then be mapped into the VRF. For instance, I could assign an IP address to an interface and then map that interface into the VRF. Likewise, I could configure a static route and specify that the route is part of a given VRF. Going one step further I could establish a BGP session off of one of the VRF interfaces and receive remote BGP routes into the VRF. VRFs are to layer 3 like VLANs are to layer 2.
So while we’ve talked about how they are typically used and implemented on networking hardware like routers and switches – we haven’t talked about how they’re implemented in Linux. Actually – they’re fairly new to the Linux space. The functionality was actually written by Cumulus Networks and then contributed to the Linux kernel (kudos Continue reading
Heavy Networking 575: Designing Better Networking And Security With SASE (Sponsored)
On today's Heavy Networking, sponsored by Palo Alto Networks, we examine what SASE means to you as a network engineer, its effects on how applications are protected and how you provide access to end users, and useful things to think about regarding how SASE services are provisioned and operated while you evaluate whether SASE is right for your org.
The post Heavy Networking 575: Designing Better Networking And Security With SASE (Sponsored) appeared first on Packet Pushers.
Heavy Networking 575: Designing Better Networking And Security With SASE (Sponsored)
On today's Heavy Networking, sponsored by Palo Alto Networks, we examine what SASE means to you as a network engineer, its effects on how applications are protected and how you provide access to end users, and useful things to think about regarding how SASE services are provisioned and operated while you evaluate whether SASE is right for your org.Join Tigera at KubeCon + CloudNativeCon Europe 2021
We are excited to be a sponsor of this year’s virtual KubeCon + CloudNativeCon Europe conference, taking place May 4–7, 2021 online. We hope you’ll join us by visiting our virtual booth, where a team of Tigera experts will be standing by to speak with you.
Visit us at our booth
Our team will be conducting live demos, Ask the Architect sessions, 1:1 chats, and more during our booth hours.

Tigera booth hours
Live demo and Ask the Expert sessions
We will have eight 30-minute interactive sessions focused on addressing questions about Kubernetes security and observability. Stop by our booth to check out the times for these sessions.
Private 1:1 chats & calls
Attendees can view each booth representative’s profile and initiate a private or group text chat, or request a video call.
Public booth chat
Our booth will have a built-in public chat window where booth representatives and attendees can post and reply to messages. Announcements about upcoming activities will be posted in this chat by Tigera representatives.
Enter our raffle to win Apple AirPods
We have 5 pairs of Apple AirPods to give away! The first 100 visitors to our booth will automatically be entered to win. Attendees Continue reading
SSHing to my Raspberry Pi 400 from a browser, with Cloudflare Tunnel and Auditable Terminal

A few weeks ago I received a Raspberry Pi 400 as a gift. I didn’t have time to do anything beyond plug it in and verify that it works. It’s great that the Pi 400 comes with everything you need except for a screen: there’s the computer itself, mouse, HDMI cable and power adapter.

The Pi 400 has been sitting gathering dust when Cloudflare launched Auditable Terminal giving me the perfect excuse to get out the Pi 400 and hook it up.
Auditable Terminal gives you a fully featured SSH client in your browser. You authenticate using Cloudflare Access and can log into a computer from anywhere just using the browser and get a terminal. And using Cloudflare Tunnel you can securely connect a computer to Cloudflare without punching holes in a firewall. And you end up with a consistent terminal experience across devices: 256 colours, Unicode support and the same fonts everywhere.
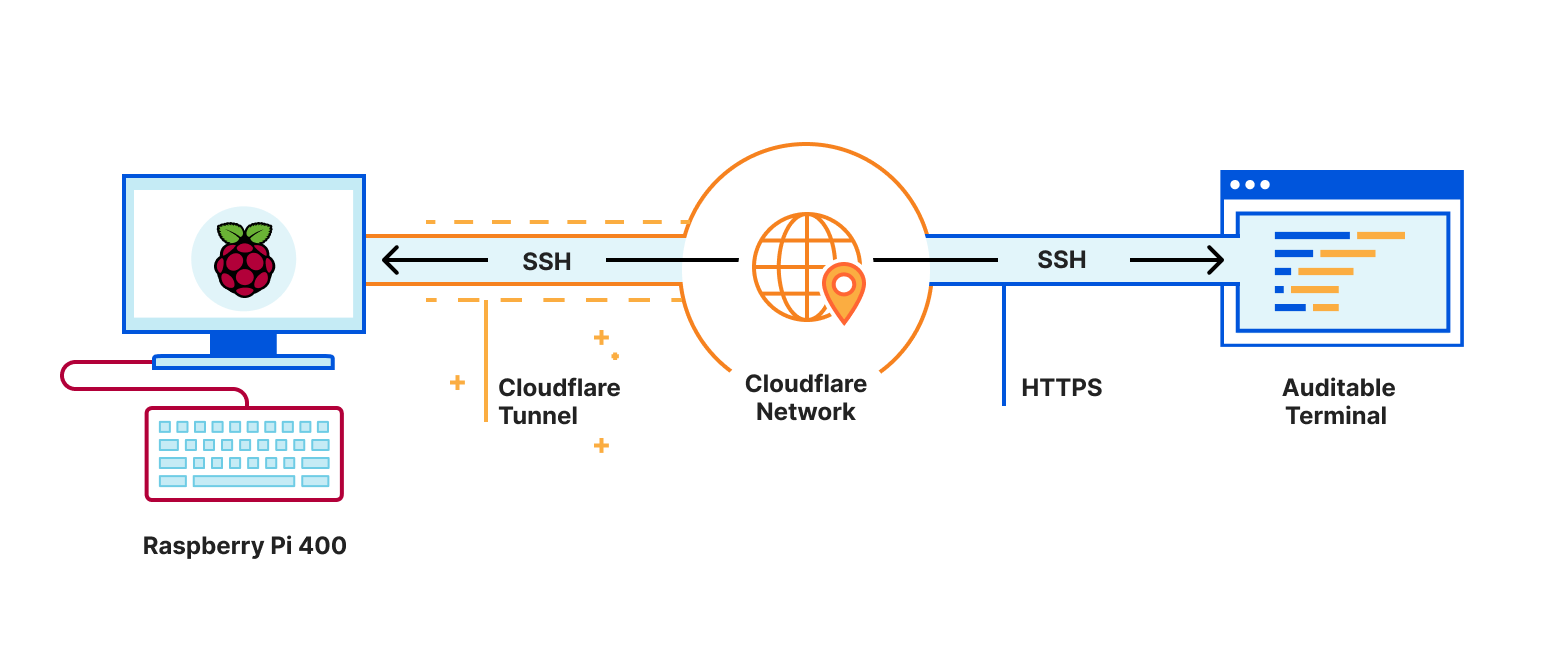
This is ideal for my use case: set up the Pi 400 on my home network, use Cloudflare Tunnel to connect it to the Cloudflare network, use Auditable Terminal to connect to the Pi 400 via Cloudflare and the tunnel using nothing more than a browser.
Here’s Continue reading
Nokia Lab | LAB 4 LDP |
- Basic LDP
- prepare basic and IGP configuration (Multi-area OSPF, area type - normal, add "system" to OSPF)
- enable LDP on P2P interfaces
- LDP session
- examine LDP neighbor discovery process
- What is the destination IP address of Hello messages?
- What address does SR-OS router use as a transport address for LDP control plane?
- What label mapping does SR-OS router generate by default?
- examine LIB and LFIB
- What is the difference between LIB and LFIB?
- configure ECMP 2 (e.g. on R1) and examine RT, LIB and LFIB
- create two additional loopback interfaces on R1 with addresses from the same subnet (e.g. 172.16.0.0/32, 172.16.0.1/32)
- export prefixes to LDP by policy
- examine LFIB on R2
- Does it contain entries with target prefixes? What about LIB?
- What is the reason for this difference?
A Digital Dystopia: How Calls for Backdoors to Encryption Would Ruin the Internet for Everyone

A little over a year into the COVID-19 pandemic, our reliance on private, safe, and secure communication has become more critical than ever. So it’s no surprise that organizations across all sectors are increasingly adopting encryption. It’s our strongest digital security tool online, keeping the information we share in daily activities like online banking, working […]
The post A Digital Dystopia: How Calls for Backdoors to Encryption Would Ruin the Internet for Everyone appeared first on Internet Society.
MUST READ: Deploy AWS Security Rules in a GitOps World with AWS, Terraform, GitLab CI, Slack, and Python
I know the title sounds like a buzzword-bingo-winning clickbait, but it’s true. Adrian Giacometti decided to merge the topics of two ipSpace.net online courses and automated deployment of AWS security rules using Terraform within GitLab CI pipeline, with Slack messages serving as manual checks and approvals.
Not only did he do a great job mastering- and gluing together so many diverse bits and pieces, he also documented the solution and published the source code:
- Part 1: Cloud & Network automation challenge: Deploy Security Rules in a DevOps/GitOps world with AWS, Terraform, GitLab CI, Slack, and Python (special guest FastAPI)
- Part 2: AWS, Terraform and FastAPI
- Part 3: GitLab CI, Slack, and Python
- Source code: aegiacometti/devops_cloud_challenge · GitLab
Want to build something similar? Join our Network Automation and/or Public Cloud course and get started. Need something similar in your environment? Adrian is an independent consultant and ready to work on your projects.

