OMG, It’s Graphs Everywhere
One of the subscribers watching the Graph Algorithms in Networks webinar found the webinar had an interesting impact on his perspective (according to his feedback):
This is genuine content that I haven’t seen anywhere else. It helps to get up to speed on computer science topics that are relevant to network professionals. After attending this webinar, I couldn’t unsee the graphs anymore that are almost everywhere in networking.
This webinar is available with Standard ipSpace.net Subscription as are other webinars by Rachel Traylor including Network Connectivity, Graph Theory, and Reliable Network Design, Queuing Theory and Reliability Theory: Networking through a Systems Analysis Lens. She’ll be back next week starting a series of deep dives into reliability topics. Hope you’ll enjoy them as much as our subscriber did the Graph Algorithms webinar.
OMG, It’s Graphs Everywhere
One of the subscribers watching the Graph Algorithms in Networks webinar found the webinar had an interesting impact on his perspective (according to his feedback):
This is genuine content that I haven’t seen anywhere else. It helps to get up to speed on computer science topics that are relevant to network professionals. After attending this webinar, I couldn’t unsee the graphs anymore that are almost everywhere in networking.
This webinar is available with Standard ipSpace.net Subscription as are other webinars by Rachel Traylor including Network Connectivity, Graph Theory, and Reliable Network Design, Queuing Theory and Reliability Theory: Networking through a Systems Analysis Lens. She’ll be back next week starting a series of deep dives into reliability topics. Hope you’ll enjoy them as much as our subscriber did the Graph Algorithms webinar.
Networking and Infrastructure News Roundup: February 5 Edition
In the news this week: Solutions to secure hybrid and multi-cloud environments, integrated SASE solutions, and more.Go Notes: Types
Go has many built in types that are found in other programming languages. It also supports the creation of custom types. Each type has a default zero value that is used when a variable is declared but not yet assigned a value. Boolean Booleans are true or false values. The zero...Go Notes: Pointers
https://codingpackets.com/blog/go-notes-pointers
Automate Leaf and Spine Deployment – Part2
The 2nd post in the ‘Automate Leaf and Spine Deployment’ series describes process used for validating the variable files format and content. The idea behind this offline pre-validation is to catch any errors in the variable files before device configuration is attempted. Fail fast based on logic instead of failing halfway through a build. It wont catch everything but will eliminate a lot of the needless errors that would break a fabric build.
The Role of Security in a Future Full of Cloud Services
The future of work will revolve around effectively using cloud technologies to conduct business. Security plays a critical role in that future.Developing NetBox Plugin – Part 4 – Small improvements
Welcome to part 4 of the tutorial on developing NetBox plugin. By now BgpPeering plugin is functional but there are few things here and there that could make it better. In this post, we'll go through many improvements that will make the plugin look better and increase its functionality.
Developing NetBox Plugin tutorial series
- Developing NetBox Plugin - Part 1 - Setup and initial build
- Developing NetBox Plugin - Part 2 - Adding web UI pages
- Developing NetBox Plugin - Part 3 - Adding search panel
- Developing NetBox Plugin - Part 4 - Small improvements
- Developing NetBox Plugin - Part 5 - Permissions and API
Contents
- Updating display name of BgpPeering objects
- Enforce the same network for local and remote IPs
- Allowing objects to be deleted
- Allowing objects to be edited
- Prettifying field labels
- Conclusion
- Resources
- BGP Peering Plugin GitHub repository
Updating display name of BgpPeering objects
We'll start improvements by changing default display name of BgpPeering Continue reading
Worth Reading: Visualizing BGP-LS Tables
When I’d first seen BGP-LS I immediately thought: “it would be cool to use this to fetch link state topology data from the network and build a graph out of it”. In those days the only open-source way I could find to do it involved Open DayLight controller’s BGP-LS-to-REST-API converter, and that felt like deploying an aircraft carrier to fly a kite.
Things have improved dramatically since then. In Visualizing BGP-LS Tables, HB described how he solved the challenge with GoBGP, gRPC interface to GoBGP, and some Python code to parse the data and draw the topology graph with NetworkX. Enjoy!
Worth Reading: Visualizing BGP-LS Tables
When I’d first seen BGP-LS I immediately thought: “it would be cool to use this to fetch link state topology data from the network and build a graph out of it”. In those days the only open-source way I could find to do it involved Open DayLight controller’s BGP-LS-to-REST-API converter, and that felt like deploying an aircraft carrier to fly a kite.
Things have improved dramatically since then. In Visualizing BGP-LS Tables, HB described how he solved the challenge with GoBGP, gRPC interface to GoBGP, and some Python code to parse the data and draw the topology graph with NetworkX. Enjoy!
An IPv6 Update for 2020
The common theme of many of reviews of the Internet in 2020 has been that the Internet has been used to plug the gap caused by shutting down many of our physical venues where we previously worked and played. No matter what aspect of the Internet you look at, its clear that we all made much more use of the Internet this year. Here I would like to ask the inevitable IPv6 question: What role did IPv6 play in 2020?Juniper to Mikrotik – MPLS Commands
About the Juniper to MikroTik series
In the world of network engineering, learning a new syntax for a NOS can be daunting if you need a specific config quickly. Juniper is a popular option for service providers/data centers and is widely deployed across the world.
This is a continuation of the Rosetta stone for network operating systems series. In this article we will be covering multi-protocol label switching (MPLS) using label distribution protocol (LDP). We are sticking with LDP as MikroTik does not have wide support for RSVP-TE.
You can find the first two articles of the series here:
Juniper to MikroTik – BGP commands
Juniper to MikroTik – OSPF commands
While many commands have almost the exact same information, others are as close as possible. Since there isn’t always an exact match, sometimes you may have to run two or three commands to get the information needed.
Using EVE-NG for testing
We conducted utilized EVE-NG for all of the testing with the topology seen below.
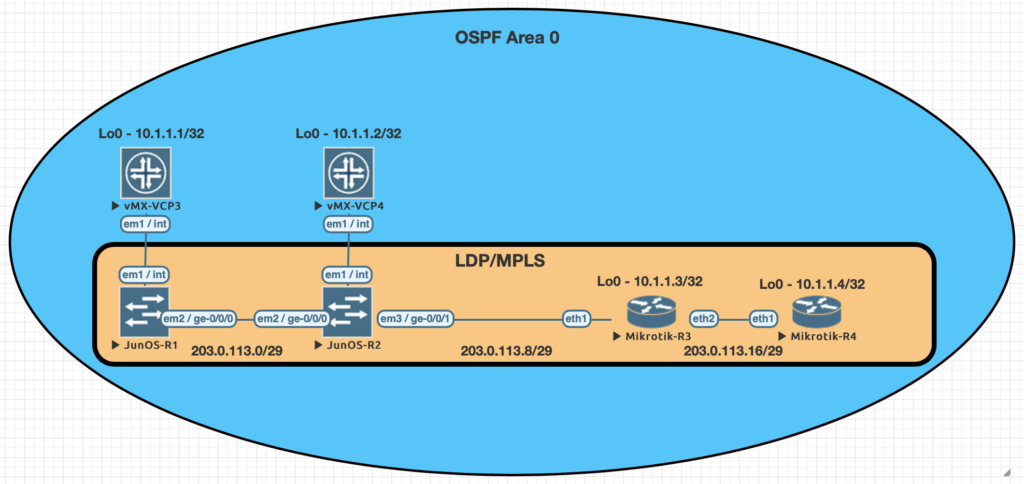
| Juniper Command | MikroTik Command |
|---|---|
| show ldp neighbor | mpls ldp neighbor print |
| show ldp interface | mpls ldp interface print |
| show route forwarding-table family mpls | mpls forwarding-table print |
| show ldp database | mpls Continue reading |
Worth Reading: Finding Bugs in C and C++ Compilers
Something to keep in mind before you start complaining about the crappy state of network operating systems: people are still finding hundreds of bugs in C and C++ compilers.
One might argue that compilers are even more mission-critical than network devices, they’ve been around for quite a while, and there might be more people using compilers than configuring network devices, so one would expect compilers to be relatively bug-free. Still, optimizing compilers became ridiculously complex in the past decades trying to squeeze the most out of the ever-more-complex CPU hardware, and we’re paying the price.
Keep that in mind the next time a vendor dances by with a glitzy slide deck promising software-defined nirvana.
Worth Reading: Finding Bugs in C and C++ Compilers
Something to keep in mind before you start complaining about the crappy state of network operating systems: people are still finding hundreds of bugs in C and C++ compilers.
One might argue that compilers are even more mission-critical than network devices, they’ve been around for quite a while, and there might be more people using compilers than configuring network devices, so one would expect compilers to be relatively bug-free. Still, optimizing compilers became ridiculously complex in the past decades trying to squeeze the most out of the ever-more-complex CPU hardware, and we’re paying the price.
Keep that in mind the next time a vendor dances by with a glitzy slide deck promising software-defined nirvana.
Friction Finders

Do you have a door that sticks in your house? If it’s made out of wood the odds are good that you do. The kind that doesn’t shut properly or sticks out just a touch too far and doesn’t glide open like it used to. I’ve dealt with these kinds of things for years and Youtube is full of useful tricks to fix them. But all those videos start with the same tip: you have to find the place where the door is rubbing before you can fix it.
Enterprise IT is no different. We have to find the source of friction before we can hope to repair it. Whether it’s friction between people and hardware, users and software, or teams going at each other we have to know what’s causing the commotion before we can repair it. Just like with the sticking door, adding more force without understand the friction points isn’t a long-term solution.
Sticky Wickets
Friction comes from a variety of sources. People don’t understand how to use a device or a program. Perhaps it’s a struggle to understand who is supposed to be in charge of a change control or a provisioning process. It could even Continue reading
Tempered Networks Tempts Users With Free Remote Access Offering
Tempered Networks lets you set up encrypted remote access for 25 devices for free with its new Airwall Teams offering.
The post Tempered Networks Tempts Users With Free Remote Access Offering appeared first on Packet Pushers.
Heavy Networking 560: Moving Big Data Sets From Far-Off Locations
Construction sites generate tons of data but often lack network connectivity. Today's Heavy Networking explores how one CTO has found ways to move huge data sets to HQ and the cloud using everything from Free Space Optics to LTE to consumer broadband. There are also stories about flying drones and robot dogs, and the operational impacts of SD-WAN. Our guest is Michael Shepherd, CTO of Rogers-O’Brien Construction.Heavy Networking 560: Moving Big Data Sets From Far-Off Locations
Construction sites generate tons of data but often lack network connectivity. Today's Heavy Networking explores how one CTO has found ways to move huge data sets to HQ and the cloud using everything from Free Space Optics to LTE to consumer broadband. There are also stories about flying drones and robot dogs, and the operational impacts of SD-WAN. Our guest is Michael Shepherd, CTO of Rogers-O’Brien Construction.
The post Heavy Networking 560: Moving Big Data Sets From Far-Off Locations appeared first on Packet Pushers.
