Threat Intelligence Report: Targeted Snake Ransomware
In the last few weeks, VMware NSX threat telemetry revealed the submission of a Windows executable Ransomware sample, written in Go, which is related to the Snake Ransomware family.
This ransomware specifically targeted the Honda network, and was found to be quite sophisticated. The ransomware appears primarily to be targeting servers, as it has logic to check for the type of host it is infecting, and it attempts to stop many server-specific services/processes. Hard-coded strings are encrypted, source code is obfuscated, and the ransomware attempts to stop anti-virus, endpoint security, and server log monitoring and correlation components. This ransomware family has ties to Iran and has historically been observed targeting critical infrastructure such as SCADA and ICS systems. More recently, the malware has been observed targeting healthcare organizations. Most interestingly, and unlike other variants, the malware analyzed in this threat report does not drop any ransom note to desktop machines.
To learn more, read our Targeted Snake Ransomware Report.
The post Threat Intelligence Report: Targeted Snake Ransomware appeared first on Network and Security Virtualization.
On the Road to Better Routing Security: What Are MENA’s Next Steps?

In a region with a wealth of resources and network expertise but a higher than average number of global routing incidents, the Mutually Agreed Norms for Routing Security (MANRS) initiative can help networks champion a more secure routing environment.
Networks in the Middle East and North Africa (MENA) region fall between two regional Internet registries: Réseaux IP Européens Network Coordination Centre (RIPE NCC) and African Network Information Centre (AFRINIC). This gives these networks access to many resources and tools that support them to adopt best practices in routing security, including resource public key infrastructure (RPKI). There’s also great technical expertise in the region, with specialists working to keep more than 800 MENA-based networks up and running.

The region is, however, over represented in terms of routing incidents. Despite representing only 1.18% of all the networks visible on the Internet, the region has been responsible for 2.5-3% of global routing incidents so far this year as of October. Last month, the MANRS Observatory recorded 24 routing incidents from 22 networks in the region. The incidents range from Bogon announcements to more serious route leaks and route mis-originations, as detailed in the screen capture from MANRS Observatory above.
MANRS for Continue reading
Technologies that Didn’t: Asynchronous Transfer Mode
One of the common myths of the networking world is there were no “real” networks before the early days of packet-based networks. As myths go, this is not even a very good myth; the world had very large-scale voice and data networks long before distributed routing, before packet-based switching, and before any of the packet protocols such as IP. I participated in replacing a large scale voice and data network, including hundreds of inverse multiplexers that tied a personnel system together in the middle of the 1980’s. I also installed hundreds of terminal emulation cards in Zenith Z100 and Z150 systems in the same time frame to allow these computers to connect to mainframes and newer minicomputers on the campus.
All of these systems were run through circuit-switched networks, which simply means the two end points would set up a circuit over which data would travel before the data actually traveled. Packet switched networks were seen as more efficient at the time because the complexity of setting these circuits up, along with the massive waste of bandwidth because the circuits were always over provisioned and underused.
The problem, at that time, with packet-based networks was the sheer overhead of switching Continue reading
Heavy Strategy 005 – Infection Handling Open Source In Enterprise IT
The question: Is open source is viable for Enterprise IT ? The discussion resulted in describing the mechanics of onboarding new products as infection repsonse. Did the metaphor work ?Anchoring Trust: A Hardware Secure Boot Story
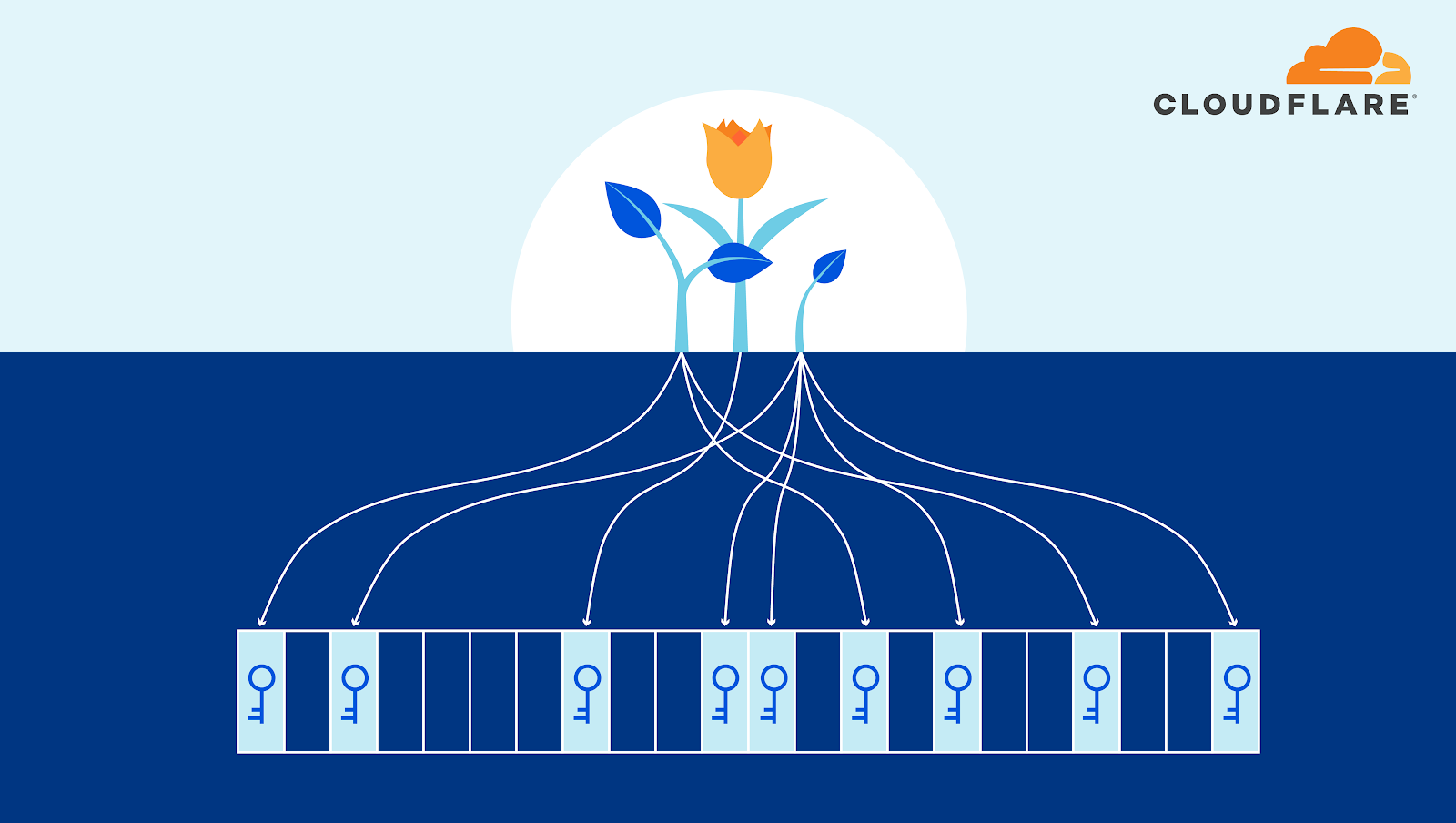
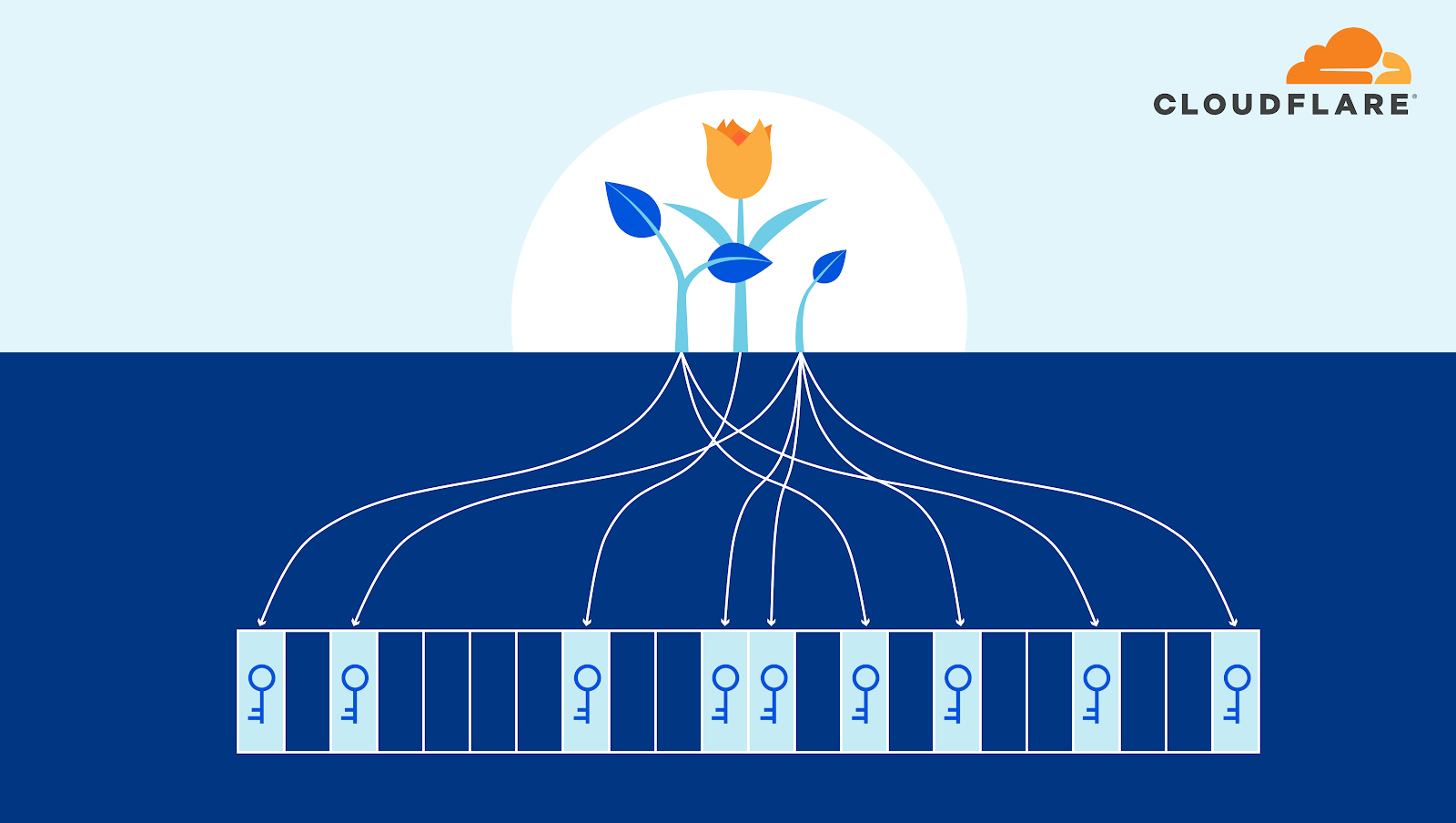
As a security company, we pride ourselves on finding innovative ways to protect our platform to, in turn, protect the data of our customers. Part of this approach is implementing progressive methods in protecting our hardware at scale. While we have blogged about how we address security threats from application to memory, the attacks on hardware, as well as firmware, have increased substantially. The data cataloged in the National Vulnerability Database (NVD) has shown the frequency of hardware and firmware-level vulnerabilities rising year after year.
Technologies like secure boot, common in desktops and laptops, have been ported over to the server industry as a method to combat firmware-level attacks and protect a device’s boot integrity. These technologies require that you create a trust ‘anchor’, an authoritative entity for which trust is assumed and not derived. A common trust anchor is the system Basic Input/Output System (BIOS) or the Unified Extensible Firmware Interface (UEFI) firmware.
While this ensures that the device boots only signed firmware and operating system bootloaders, does it protect the entire boot process? What protects the BIOS/UEFI firmware from attacks?
The Boot Process
Before we discuss how we secure our boot process, we will first Continue reading
How Fast Can We Detect a Network Failure?
In the introductory fast failover blog post I mentioned the challenge of fast link- and node failure detection, and how it makes little sense to waste your efforts on fast failover tricks if the routing protocol convergence time has the same order of magnitude as failure detection time.
Now let’s focus on realistic failure detection mechanisms and detection times. Imagine a system connecting a hardware switching platform (example: data center switch or a high-end router) with a software switching platform (midrange router):
How Fast Can We Detect a Network Failure?
In the introductory fast failover blog post I mentioned the challenge of fast link- and node failure detection, and how it makes little sense to waste your efforts on fast failover tricks if the routing protocol convergence time has the same order of magnitude as failure detection time.
Now let’s focus on realistic failure detection mechanisms and detection times. Imagine a system connecting a hardware switching platform (example: data center switch or a high-end router) with a software switching platform (midrange router):
Take Back Control of IT with Cloud-Native IGA
Identity governance and administration (IGA) is all about security automation, delivering the needed efficiency, speed, accuracy, and consistent output.Workers KV – free to try, with increased limits!


In May 2019, we launched Workers KV, letting developers store key-value data and make that data globally accessible from Workers running in Cloudflare’s over 200 data centers.
Today, we’re announcing a Free Tier for Workers KV that opens up global, low-latency data storage to every developer on the Workers platform. Additionally, to expand Workers KV’s use cases even further, we’re also raising the maximum value size from 10 MB to 25 MB. You can now write an application that serves larger static files directly or JSON blobs directly from KV.
Together with our announcement of the Durable Objects limited beta last month, the Workers platform continues to move toward providing storage solutions for applications that are globally deployed as easily as an application running in a single data center today.
What are the new free tier limits?
The free tier includes 100,000 read operations and 1,000 each of write, list and delete operations per day, resetting daily at UTC 00:00, with a maximum total storage size of 1 GB. Operations that exceed these limits will fail with an error.
Additional KV usage costs $0.50 per million read operations, $5.00 per million list, write and delete operations Continue reading
Tech Bytes: Protecting Remote Workers From VPN Risks With Zscaler (Sponsored)
Many companies use VPNs to protect their distributed workforce. But VPNs present their own security challenges, from compromised clients to insecure VPN servers. Sponsor Zscaler explains how its cloud-based security service can provide safe, high-performance remote access. Our guest is Lisa Lorenzin, Director, Transformation Strategy at Zscaler.Tech Bytes: Protecting Remote Workers From VPN Risks With Zscaler (Sponsored)
Many companies use VPNs to protect their distributed workforce. But VPNs present their own security challenges, from compromised clients to insecure VPN servers. Sponsor Zscaler explains how its cloud-based security service can provide safe, high-performance remote access. Our guest is Lisa Lorenzin, Director, Transformation Strategy at Zscaler.
The post Tech Bytes: Protecting Remote Workers From VPN Risks With Zscaler (Sponsored) appeared first on Packet Pushers.
Upcoming Webinar: Network Troubleshooting

I’m teaching a webinar on troubleshooting theory on the 20th; register here. From the course description:
This training focuses on the half-split system of troubleshooting, which is widely used in the electronic and civil engineering domains. The importance of tracing the path of the signal, using models to put the system in context, and the use of a simple troubleshooting “loop” to focus on asking how, what, and why are added to the half-split method to create a complete theory of troubleshooting. Other concepts covered in this course are the difference between permanent and temporary fixes and a review of measuring reliability. The final third of the course contains several practical examples of working through problems to help in applying the theory covered in the first two sections to the real world.