EVE-NG Firefox and ZOC Terminal
On Windows, I use the ZOC terminal for telnet/SSH session. Naturally, I wanted to also use ZOC as the terminal for the EVE-NG web console. So when you click on a node, it opens a tabbed session in ZOC automatically. This was not so straight forward and I burned alot of cycles trying to...11ty File Watchers Error
I have come across a file watchers error a couple of times now with new installs of 11ty and I am documenting the fix in this post for future me. The Error When starting a local 11ty dev server with the command: You get the following error: The Solution Some quick duck hunting lead me...Improving Performance and Search Rankings with Cloudflare for Fun and Profit
Making things fast is one of the things we do at Cloudflare. More responsive websites, apps, APIs, and networks directly translate into improved conversion and user experience. On November 10th, Google announced that Google Search will directly take web performance and page experience data into account when ranking results on their search engine results pages (SERPs), beginning in May 2021.
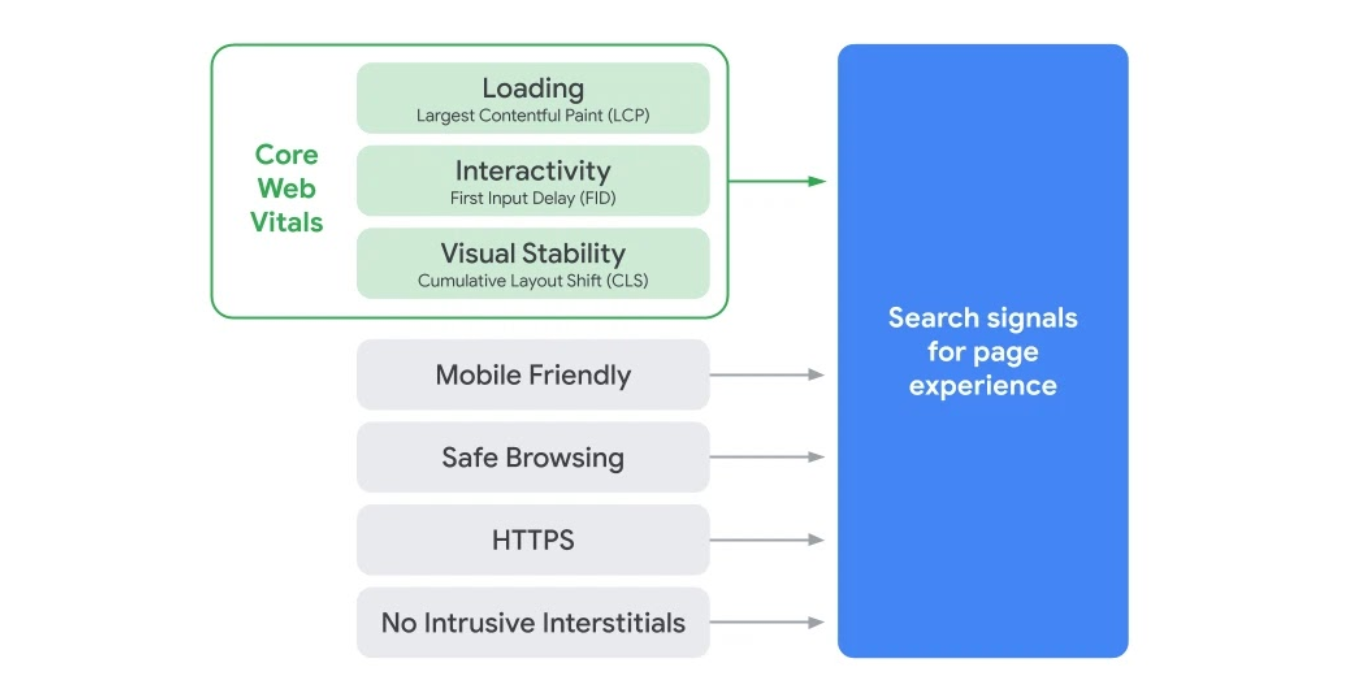
Specifically, Google Search will prioritize results based on how pages score on Core Web Vitals, a measurement methodology Cloudflare has worked closely with Google to establish, and we have implemented support for in our analytics tools.
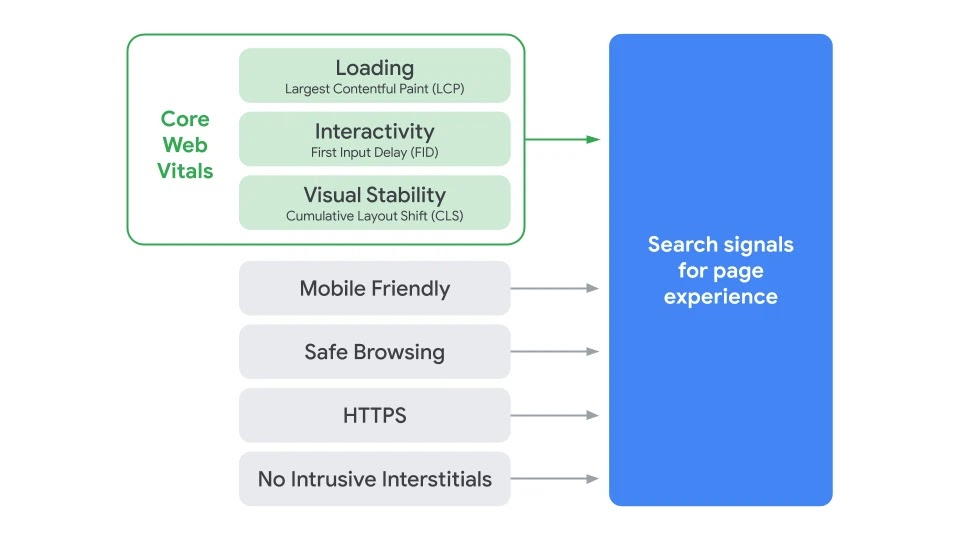
The Core Web Vitals metrics are Largest Contentful Paint (LCP, a loading measurement), First Input Delay (FID, a measure of interactivity), and Cumulative Layout Shift (CLS, a measure of visual stability). Each one is directly associated with user perceptible page experience milestones. All three can be improved using our performance products, and all three can be measured with our Cloudflare Browser Insights product, and soon, with our free privacy-aware Cloudflare Web Analytics.
SEO experts have always suspected faster pages lead to better search ranking. With the recent announcement from Continue reading
Multipass
Multipass is a command line tool for running Ubuntu virtual machines on Mac or Windows. Multipass uses the native virtualization capabilities of the host operating system to simplify the creation of virtual machines.multipass launch --name=mininet bionic
multipass exec mininet -- sudo apt update
multipass exec mininet -- sudo apt -y install mininet python-ryu
multipass exec mininet -- sudo apt -y install default-jre python-requests hping3
multipass exec mininet -- wget https://inmon.com/products/sFlow-RT/sflow-rt.tar.gz
multipass exec mininet -- tar -xzf sflow-rt.tar.gz
multipass exec mininet -- ./sflow-rt/get-app.sh sflow-rt mininet-dashboard
Run the above commands in a terminal to create the virtual machine. Multipass commands can easily be scripted to automate the creation and configuration of virtual machines.
multipass listList the virtual machines.
Name State IPv4 Image
test Running 192.168.64.2 Ubuntu 18.04 LTS
Encrypted VelvetSweatshop Password Still a Threat to Excel Files
Office documents, such as Word and Excel files, can be password-protected using a symmetric key encryption mechanism involving one password which is the key to both encrypt and decrypt a file. Malware writers use this key as an additional evasion technique to hide malicious code from anti-virus (AV) scanning engines. The problem is that encrypting a file introduces the disadvantage of requiring a potential victim to enter a password (which is normally included in the phishing or spam email containing the encrypted attachment). This makes the email and the attachment very suspicious, thus greatly reducing the chance that the intended victim will open the encrypted malicious attachment.
The good news (for the attackers) is that Microsoft Excel can automatically decrypt a given encrypted spreadsheet without asking for a password if the password for encryption happens to be VelvetSweatshop. This is a default key stored in Microsoft Excel program code for decryption. It’s a neat trick that attackers can leverage to encrypt malicious Excel files in order to evade static-analysis-based detection systems, while eliminating the need for a potential victim to enter a password.
The embedded VelvetSweatshop key in Excel is not a secret. It has been widely reported for many Continue reading
Using Edge Computing to Transform Networks in a 5G World
With 5G networks expanding and edge computing technology maturing, expect to soon see superfast, low latency networks delivering new applications.Many services, one cloudflared
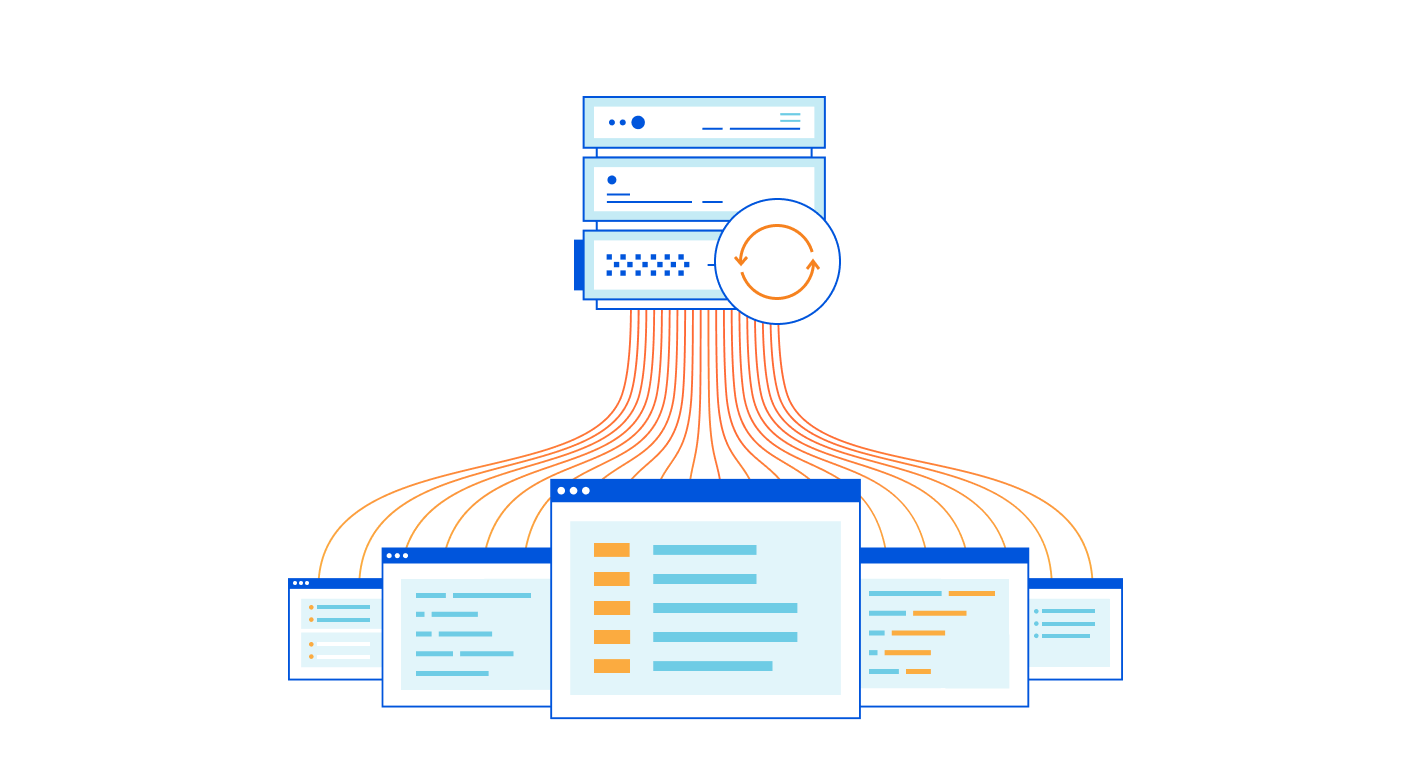
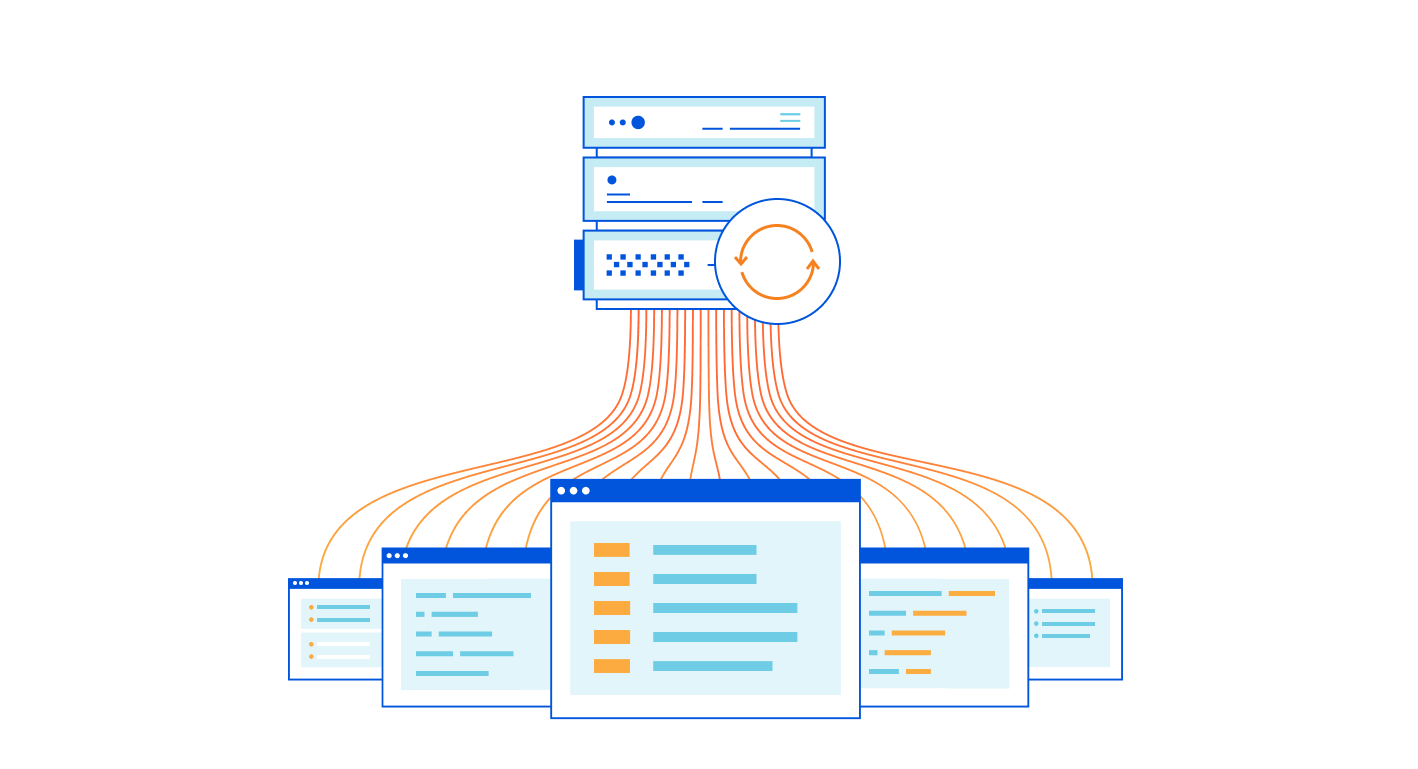
I work on the Argo Tunnel team, and we make a program called cloudflared, which lets you securely expose your web service to the Internet while ensuring that all its traffic goes through Cloudflare.
Say you have some local service (a website, an API, a TCP server, etc), and you want to securely expose it to the internet using Argo Tunnel. First, you run cloudflared, which establishes some long-lived TCP connections to the Cloudflare edge. Then, when Cloudflare receives a request for your chosen hostname, it proxies the request through those connections to cloudflared, which in turn proxies the request to your local service. This means anyone accessing your service has to go through Cloudflare, and Cloudflare can do caching, rewrite parts of the page, block attackers, or build Zero Trust rules to control who can reach your application (e.g. users with a @corp.com email). Previously, companies had to use VPNs or firewalls to achieve this, but Argo Tunnel aims to be more flexible, more secure, and more scalable than the alternatives.
Some of our larger customers have deployed hundreds of services with Argo Continue reading
European Union, Use Facts to Make Cybersecurity Decisions – Not Myths

Nearly 450 million EU citizens are counting on the Council of the European Union to make decisions that protect their safety. The Council has a duty make these decisions based on reliable information.
In the next week, the Council of the European Union is expected to consider a resolution that argues that law enforcement “must be able to access data in a lawful and targeted manner.” This resolution is the first step of a wider push by the European Union to demand law enforcement access to encrypted data.
But are they relying on accurate information to make their decisions?
A report leaked from the European Commission in September, Technical solutions to detect child sexual abuse in end-to-end encrypted communications, tries to analyze different ways to spot illegal content in private communications that use end-to-end encryption. This leaked report could influence their decison-making on encryption policy in the EU.
The EU Commission’s report alludes to the idea that some access methods may be less risky than others. However, the bottom line is that each method presents serious security and privacy risks for billions of users worldwide.
Don’t take just my word for it. According to the Internet Society and the Continue reading
Fast Failover: Topologies
In the blog post introducing fast failover challenge I mentioned several typical topologies used in fast failover designs. It’s time to explore them.
The Basics
Fast failover is (by definition) adjustment to a change in network topology that happens before a routing protocol wakes up and deals with the change. It can therefore use only locally available information, and cannot involve changes in upstream devices. The node adjacent to the failed link has to deal with the failure on its own without involving anyone else.
Fast Failover: Topologies
In the blog post introducing fast failover challenge I mentioned several typical topologies used in fast failover designs. It’s time to explore them.
The Basics
Fast failover is (by definition) adjustment to a change in network topology that happens before a routing protocol wakes up and deals with the change. It can therefore use only locally available information, and cannot involve changes in upstream devices. The node adjacent to the failed link has to deal with the failure on its own without involving anyone else.
What Are Data Types Anyways?
There are actually quite a few resources out there for a novice programmer to learn about data types like strings, integers, floats, and more. The wikipedia page, as an example, covers a broad spectrum of potential meanings. Just about any book or tutorial focused on a particular programming language will start off by listing the types supported by that language. This makes sense, since they are the fundamental building block of being able to do pretty much anything in that language.Vendor Lock-In. Maybe Not So Evil. (Video)
Is vendor lock-in all that bad? Many argue yes. You’re tied to a vendor because you’ve used some of their proprietary technology, and so you’re (apparently) stuck with it forever, limiting your future business agility. I think that’s an incomplete argument, though.
Tools 1. Top 5 tools for network performance troubleshooting
Hello my friend,
some time ago we’ve been recently engaged in the troubleshooting of the performance issues. Namely, the speed of the communication between the application’s endpoints in two data centres was not persistent. Instead, it was deviating a lot having multiple TCP retransmissions for certain flows. The issues was successfully solved, and we’d like to share with you the tools we have used to identify and validate various aspects of traffic forwarding.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
Can automation help with performance troubleshooting?
Absolutely. During our network automation training we show how to utilise various Linux tools from configuration management tools (e.g. Ansible) and programming languages (Bash, Python). That gives you ready examples from our training, which you can use in your network immediately, and endless possibilities to create your own automated troubleshooting workflows.

Our network automation training has two faces: either live or self-paced. So you can choose yourself, what works better for you. On our side, we Continue reading
The Hedge Podcast #60: Ben Andresen and Growing Teams

How can managers grow teams that add value to the company? Teams are made up of people, and people need to grow, so the key is in learning how to grow people. Join us at the Hedge as we discuss learning paths, doing what’s right for the company and the person, and growing teams by growing people.
