My internship: Brotli compression using a reduced dictionary
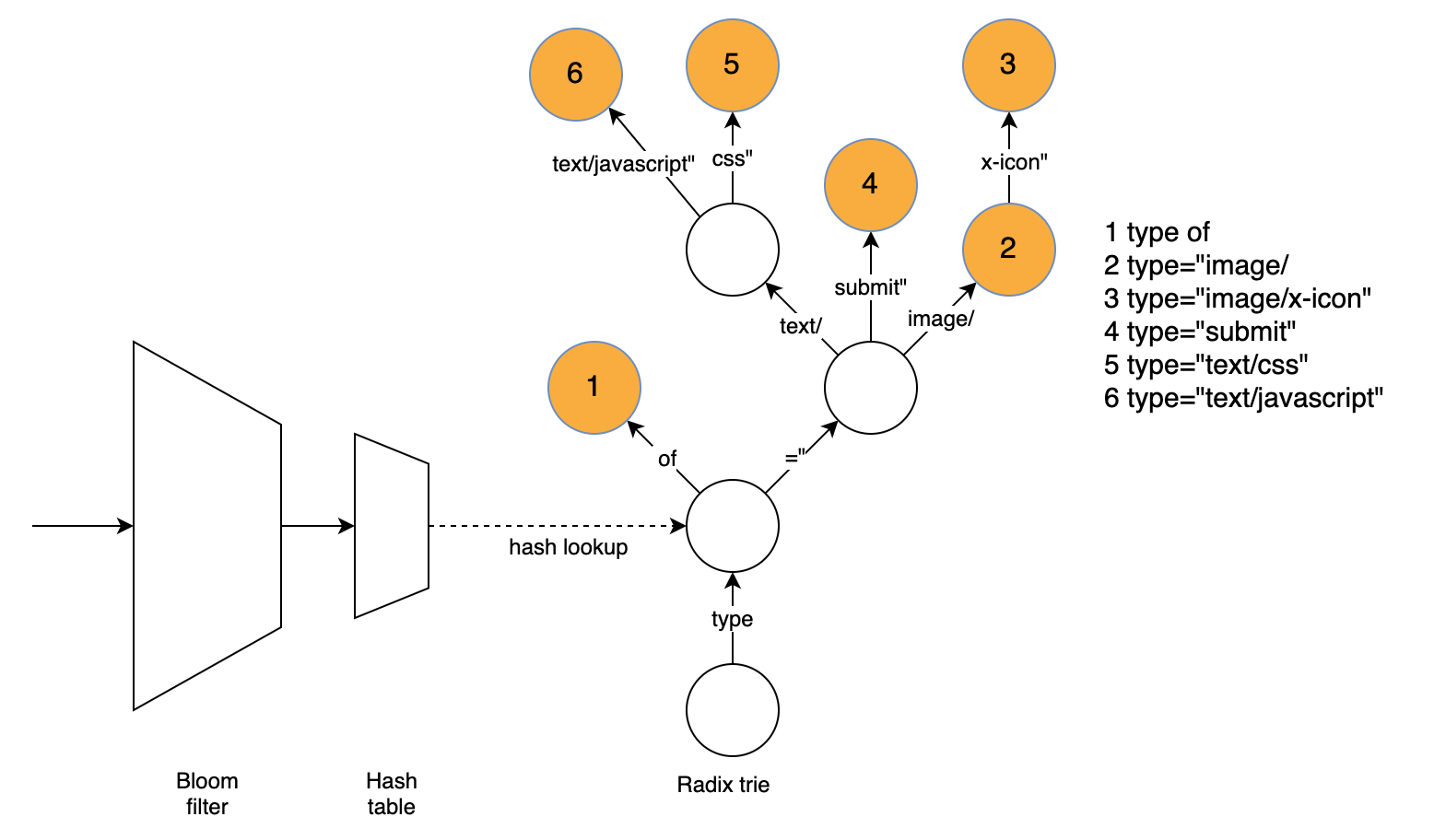
Brotli is a state of the art lossless compression format, supported by all major browsers. It is capable of achieving considerably better compression ratios than the ubiquitous gzip, and is rapidly gaining in popularity. Cloudflare uses the Google brotli library to dynamically compress web content whenever possible. In 2015, we took an in-depth look at how brotli works and its compression advantages.
One of the more interesting features of the brotli file format, in the context of textual web content compression, is the inclusion of a built-in static dictionary. The dictionary is quite large, and in addition to containing various strings in multiple languages, it also supports the option to apply multiple transformations to those words, increasing its versatility.
The open sourced brotli library, that implements an encoder and decoder for brotli, has 11 predefined quality levels for the encoder, with higher quality level demanding more CPU in exchange for a better compression ratio. The static dictionary feature is used to a limited extent starting with level 5, and to the full extent only at levels 10 and 11, due to the high CPU cost of this feature.
We improve on the limited dictionary use approach and add Continue reading
DENT
Introducing DENT OS, switchdev NOS for the rest of us talk, presented at the recent Open Source Summit, describes the Linux Foundation DENT project. The slides from the presentation are available.
Mark Your Calendars – The Modern Network for a Future Ready Business
Applications are going through a major transformation – they are becoming more dynamic, complex, and distributed. They are often built on cloud-native principles and run on-premises and in the cloud. As we speak with our customers and industry analysts, we consistently hear about the need to rethink how the network supports this transformation and why it is so important for the business.
VMware is hosting a global online event – The Modern Network for a Future Ready Business. VMware executives will join industry analysts, customers, and partners to create an event that will be memorable and worthwhile, whether you are a business leader, an architect, a developer, or part of enterprise IT.
In this virtual event, we will take a look at the traditional networking model, carefully identify its shortcomings when it comes to servicing the application and the end user and make the case for a new framework – the Modern Network. Traditional networking takes a bottom up approach – focusing on connecting boxes in the campus, branch and data center with little attention paid to the apps running on top of the infrastructure. In contrast, the Modern Network keeps the end user application experience front Continue reading
Tech Leaders on the Future of Remote Work

Dozens of top leaders and thinkers from the tech industry and beyond recently joined us for a series of fireside chats commemorating Cloudflare’s 10th birthday. Over the course of 24 hours of conversation, many of these leaders touched on how the workplace has evolved during the pandemic, and how these changes will endure into the future.
Here are some of the highlights.
On the competition for talent
Stewart Butterfield
Co-founder and CEO, Slack

The thing that I think people don't appreciate or realize is that this is not a choice that companies are really going to make on an individual basis. I've heard a lot of leaders say, “we're going back to the office after the summer.”
If we say we require you to be in the office five days a week and, you know, Twitter doesn't, Salesforce doesn't — and those offers are about equal — they'll take those ones. I think we would also lose existing employees if they didn't believe that they had the flexibility. Once you do that, it affects the market for talent. If half of the companies support distributed work or flexible hours and flexible time in the office, you can compensate Continue reading
Day Two Cloud 074: Why Is There Still Shadow IT?
Why are we talking about shadow IT in 2020? Didn't we DevOps shadow IT out of the picture? Turns out we didn't. All the initiatives and process changes that were supposed to eliminate the need for shadow IT didn't quite work out the way we expected. Guest Christopher Kusek stops by to talk about why shadow IT still exists, and how to deal with it.Day Two Cloud 074: Why Is There Still Shadow IT?
Why are we talking about shadow IT in 2020? Didn't we DevOps shadow IT out of the picture? Turns out we didn't. All the initiatives and process changes that were supposed to eliminate the need for shadow IT didn't quite work out the way we expected. Guest Christopher Kusek stops by to talk about why shadow IT still exists, and how to deal with it.
The post Day Two Cloud 074: Why Is There Still Shadow IT? appeared first on Packet Pushers.
Appreciating the Networking Fundamentals
When I started creating the How Networks Really Work series I wondered whether our subscribers (mostly seasoned networking engineers) would find it useful. Turns out at least some of them do; this is what a long-time subscriber sent me:
How Networks Really Work is great, it’s like looking from a plane and seeing how all the roads are connected to each other. I know networking just enough to design and manage a corporate network, but there are many things I have learned, used and forgotten along the way.
So, getting a broad vision helps me remember why I chose something and maybe solve my bad choices. There are many things that I may never use, but with the movement of all things in the cloud it’s great to know, or at least understand, how things really work.
Parts of the webinar are accessible with free ipSpace.net subscription; you need one of the paid subscriptions to watch the whole webinar.
Appreciating the Networking Fundamentals
When I started creating the How Networks Really Work series I wondered whether our subscribers (mostly seasoned networking engineers) would find it useful. Turns out at least some of them do; this is what a long-time subscriber sent me:
How Networks Really Work is great, it’s like looking from a plane and seeing how all the roads are connected to each other. I know networking just enough to design and manage a corporate network, but there are many things I have learned, used and forgotten along the way.
So, getting a broad vision helps me remember why I chose something and maybe solve my bad choices. There are many things that I may never use, but with the movement of all things in the cloud it’s great to know, or at least understand, how things really work.
Parts of the webinar are accessible with free ipSpace.net subscription; you need one of the paid subscriptions to watch the whole webinar.
Introducing Fast, Automated Packet Capture for Kubernetes
If you’re an SRE or on a DevOps team working with Kubernetes and containers, you’ve undoubtedly encountered network connectivity issues with your microservices and workloads. Something is broken and you’re under pressure to fix it, quickly. And so you begin the tedious, manual process of identifying the issue using the observability tools at your disposal…namely metrics and logs. However, there are instances where you may need to go beyond these tools to confirm a potential bug with applications running in your cluster.
Packet capture is a valuable technique for debugging microservices and application interaction in day-to-day operations and incident response. But generating pcap files to diagnose connectivity issues in Kubernetes clusters can be a frustrating exercise in a dynamic environment where hundreds, possibly thousands of pods are continually being created and destroyed.
First, you would need to identify on which node your workload is running, match your workload against its host-based interface, and then (with root access to the node) use tcpdump to generate a file for packet analysis. Then you would need to transfer the pcap files to your laptop and view them in Wireshark. If this doesn’t initially generate the information you need to identify and resolve the Continue reading
Key Features to Look for in a Remote Network Management Tool
As network administration products and services flood the market, here are the essential capabilities you should check for.History of Cable Networks with Rouzbeh Yassini

Cable networks account for the majority of the connectivity at the network edge. Given we started with dial-up over plain old telephone lines, and then with DSL, and were promised “ATM to the home,” how did cable networks grab the edge? Rouzbeh Yassini joins Russ White and Donald Sharp to give us the history of cable networks.
Heavy Strategy 004 – Is Kubernetes A Thing
Kubernetes is operational not transformational.My Cisco DevNet Core Exam Journey

On 23 October 2020, I took and passed the Cisco Certified DevNet Professional Core exam (350-901 DEVCOR) on my first attempt. I explain here the resources I used to study and pass this exam. My background and experience Before I explain what and how I have studied, you need to understand what I already knew, what was my background and experience with some of the topics of the exam before I started to study for it. At the end of April 2018, I already passed a Cisco specialist certification on…
The post My Cisco DevNet Core Exam Journey appeared first on AboutNetworks.net.
Bienvenue Cloudflare France! Why I’m helping Cloudflare grow in France

If you'd like to read this post in French click here.

I am incredibly excited to announce that I have joined Cloudflare as its Head of France to help build a better Internet and expand the company’s growing customer base in France. This is an important milestone for Cloudflare as we continue to grow our presence in Europe. Alongside our London, Munich, and Lisbon offices, Paris marks the fourth Cloudflare office in the EMEA region. With this, we’ll be able to further serve our customers’ demand, recruit local talent, and build on the successes we’ve had in our other offices around the globe. I have been impressed by what Cloudflare has built in EMEA including France, and I am even more excited by what lies ahead for our customers, partners, and employees.
Born in Paris and raised in Paris, Normandie and Germany, I started my career more than 20 years ago. While a teenager, I had the chance to work on one of the first Apple IIe’s available in France. I have always had a passion for technology and continue to be amazed by the value of its adoption with businesses large and small. In former roles as Solution Engineer Continue reading