Security Policy Self-Service for Developers and DevOps Teams
In today’s economy, digital assets (applications, data, and processes) determine business success. Cloud-native applications are designed to iterate rapidly, creating rapid time-to-value for businesses. Organizations that are able to rapidly build and deploy their applications have significant competitive advantage. To this end, more and more developers are creating and leading DevOps teams that not only drive application development, but also take on operational responsibilities formerly owned by platform and security teams.
What’s the Value of a Self-Service Approach?
Cloud-native applications are often designed and deployed as microservices. The development team that owns the microservice understands the behavior of the service, and is in the best position to define and manage the network security of their microservice. A self-service model enables developers to follow a simple workflow and generate network policies with minimal effort. When problems occur with. application connectivity, developers should be able to diagnose connectivity issues and resolve them quickly without having to depend on resources outside of the team.
Developers and DevOps teams can also take a leading role in managing security, which is an integral part of cloud-native applications. There are two aspects to security in the context of Kubernetes.
- Cluster security – is a uniform set Continue reading
Reflecting on Three Years of Board Service and a Commitment to Quality Improvement
Departing Trustee Glenn McKnight looks back at his three years of service as a member of the Internet Society Board of Trustees.
During the past three years we have seen a tremendous amount of productive work by a functional and focused Internet Society Board of Trustees. This included not only the normal board and committee work, but also the extra efforts associated with the selection of a new CEO, creation of the Internet Society Foundation, and meeting the challenges of the proposed PIR/Ethos transaction.
It’s important to learn from these experiences, but it’s also important to focus on achievements and to reassert the core values of the Internet Society as a force of good in the Internet ecosystem. We see the Internet Society focusing its efforts with purposeful strategic direction lead by CEO Andrew Sullivan and his team. As a departing Trustee, I would like to see the Internet Society explore more opportunities for members to learn from one other, including “Meet the Board” to foster improved communication and a means to help teach the community about the role of the Board of Trustees.
During these three years, my work beyond the normal board work has also involved committee Continue reading
Day Two Cloud 063: The How And Why Of Migrating Databases To The Cloud
Planning a database migration to the cloud? If you're going to do it right, prepare to dig in because you have many options and trade offs to consider, including whether to go with IaaS or PaaS, security and monitoring issues, and much, much more. Day Two Cloud dives into the inner workings of database migration with expert Joey D’Antoni, Principal Consultant at Denny Cherry & Associates.
The post Day Two Cloud 063: The How And Why Of Migrating Databases To The Cloud appeared first on Packet Pushers.
Day Two Cloud 063: The How And Why Of Migrating Databases To The Cloud
Planning a database migration to the cloud? If you're going to do it right, prepare to dig in because you have many options and trade offs to consider, including whether to go with IaaS or PaaS, security and monitoring issues, and much, much more. Day Two Cloud dives into the inner workings of database migration with expert Joey D’Antoni, Principal Consultant at Denny Cherry & Associates.Cloudflare and Human Rights: Joining the Global Network Initiative (GNI)

Consistent with our mission to help build a better Internet, Cloudflare has long recognized the importance of conducting our business in a way that respects the rights of Internet users around the world. We provide free services to important voices online - from human rights activists to independent journalists to the entities that help maintain our democracies - who would otherwise be vulnerable to cyberattack. We work hard to develop internal mechanisms and build products that empower user privacy. And we believe that being transparent about the types of requests we receive from government entities and how we respond is critical to maintaining customer trust.
As Cloudflare continues to expand our global network, we think there is more we can do to formalize our commitment to help respect human rights online. To that end, we are excited to announce that we have joined the Global Network Initiative (GNI), one of the world's leading human rights organizations in the information and communications Technology (ICT) sector, as observers.
Business + Human Rights
Understanding Cloudflare’s new partnership with GNI requires some additional background on how human rights concepts apply to businesses.
In 1945, following the end of World War II, 850 delegates Continue reading
Announcing wrangler dev — the Edge on localhost
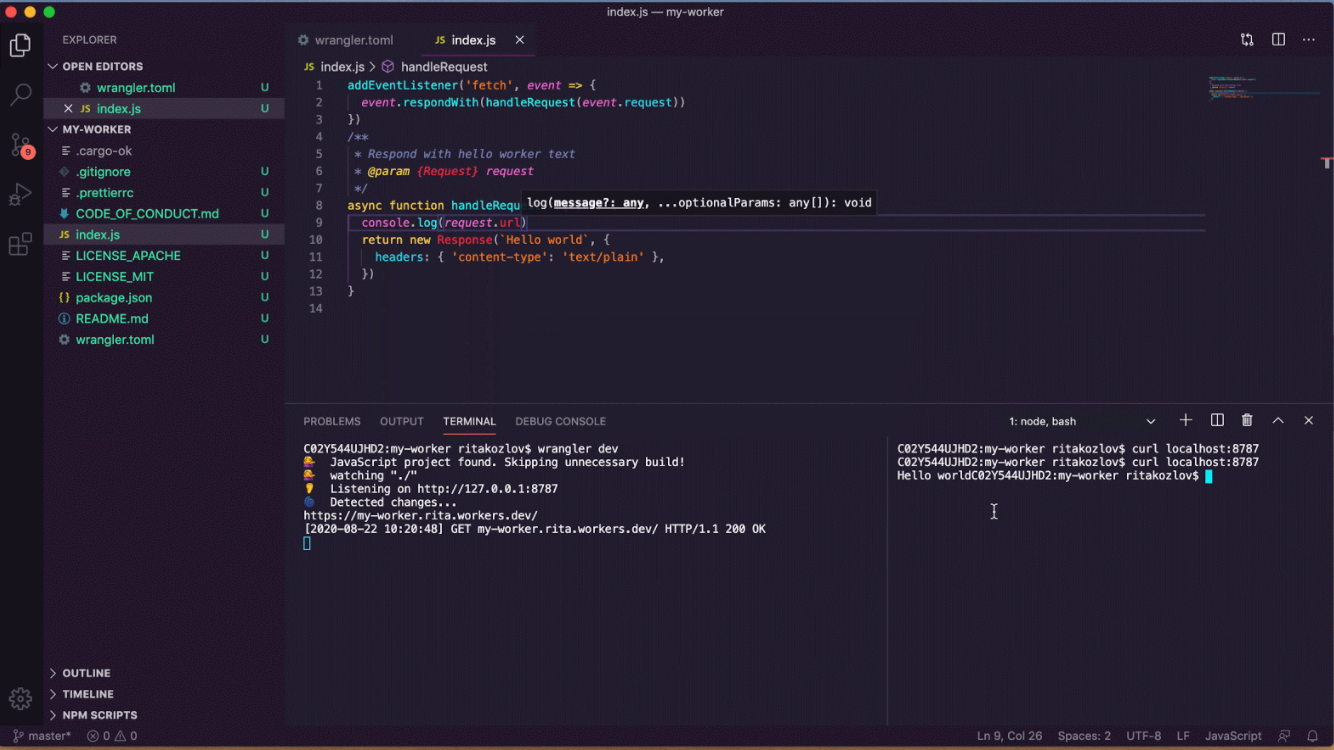
Cloudflare Workers — our serverless platform — allows developers around the world to run their applications from our network of 200 datacenters, as close as possible to their users.
A few weeks ago we announced a release candidate for wrangler dev — today, we're excited to take wrangler dev, the world’s first edge-based development environment, to GA with the release of wrangler 1.11.
Think locally, develop globally
It was once assumed that to successfully run an application on the web, one had to go and acquire a server, set it up (in a data center that hopefully you had access to), and then maintain it on an ongoing basis. Luckily for most of us, that assumption was challenged with the emergence of the cloud. The cloud was always assumed to be centralized — large data centers in a single region (“us-east-1”), reserved for compute. The edge? That was for caching static content.
Again, assumptions are being challenged.
Cloudflare Workers is about moving compute from a centralized location to the edge. And it makes sense: if users are distributed all over the globe, why should all of them be routed to us-east-1, on the opposite side of the world, Continue reading
Docker Swarm Services behind the Scenes
Remember the claim that networking is becoming obsolete and that everyone else will simply bypass the networking teams (source)?
Good news for you – there are many fast growing overlay solutions that are adopted by apps and security teams and bypass the networking teams altogether.
That sounds awesome in a VC pitch deck. Let’s see how well that concept works out in reality using Docker Swarm as an example (Kubernetes is probably even worse).
Implementing IP’s Longest Prefix Match in Pandas
Longest Prefix Match (LPM) is the algorithm used in IP networks to forward packets. The algorithm is used to select the one entry in the routing table (for those that know, I really mean the FIB–forwarding information base–here when I say routing table) that best matches the destination address in...Webinar: How the Internet Really Works
My next upcoming live webinar on Safari Books is How the Internet Really Works. This was originally a three-hour webinar which I’ve added some material to so it’s now four hours… I’m working with Pearson to add further material and break this into two three-hour webinars, so this will probably be the last four-hour version of this I teach.
Technologies that Didn’t: The Fiber Distributed Data Interface
Token Ring, in its original form, was—on paper—a very capable physical transport. For instance, because of the token passing capabilities, it could make use of more than 90% of the available bandwidth. In contrast, Ethernet systems, particularly early Ethernet systems using a true “single wire” broadcast domain, cannot achieve nearly that kind of utilization—hence “every device on its own switch port.” The Fiber Distributed Data Interface, or FDDI, is like Token Ring in many ways. For instance, FDDI uses a token to determine when a station connected to the ring can transmit, enabling efficient use of bandwidth.
And yet, Ethernet is the common carrier of almost all wired networks today, and even wireless standards mimic Ethernet’s characteristics. What happened to FDDI?
FDDI is a 100Mbit/second optical standard based on token bus, which used an improved timed token version of the token passing scheme developed for token ring networks. This physical layer protocol standard had a number of fairly unique features. It was a 100Mbit/second standard at a time when Ethernet offered a top speed of 10Mbits/second. Since FDDI could operate over a single mode fiber, it could support distances of 200 kilometers, or around 120 miles. Because it was Continue reading
The State of Routing Security at DNS Registries

The Domain Name System (DNS) is an important component of the Internet, but it was not designed with security in mind. In the last 20 years or so, much attention has been directed at improving its inherently insecure aspects.
This includes the deployment of DNS Security Extensions (DNSSEC) that enables cryptographic validation of DNS records, and more recently DNS-over-TLS and DNS-over-HTTPS, which encrypts DNS transactions between hosts and resolvers.
The DNS, though, is also dependent on the global routing system for sending DNS queries from resolvers to servers, and then returning the responses. The integrity of the routing system is, therefore, extremely important for ensuring DNS transactions are delivered efficiently to the correct destination. Yet, at present, few DNS registries are implementing Routing Public Key Infrastructure (RPKI), a public key infrastructure framework designed to secure the Internet’s routing infrastructure, specifically the Border Gateway Protocol (BGP).
A survey of 4,138 zones – that included 1,201 generic top-level domains (gTLDs), 308 country code top-level domains (ccTLDs), 271 reverse map zones, and 1,780 sub-ccTLD zones – showed a total of 6,910 route origins for the name servers that are serving these zones.
Yet, just 22% of these had valid Route Origin Authorisations (ROA), Continue reading
Improving the Wrangler Startup Experience
Today I’m excited to announce wrangler login, an easy way to get started with Wrangler! This summer for my internship on the Workers Developer Productivity team I was tasked with helping improve the Wrangler user experience. For those who don’t know, Workers is Cloudflare’s serverless platform which allows users to deploy their software directly to Cloudflare’s edge network.
This means you can write any behaviour on requests heading to your site or even run fully fledged applications directly on the edge. Wrangler is the open-source CLI tool used to manage your Workers and has a big focus on enabling a smooth developer experience.
When I first heard I was working on Wrangler, I was excited that I would be working on such a cool product but also a little nervous. This was the first time I would be writing Rust in a professional environment, the first time making meaningful open-source contributions, and on top of that the first time doing all of this remotely. But thanks to lots of guidance and support from my mentor and team, I was able to help make the Wrangler and Workers developer experience just a little bit better.
The Problem
The main improvement Continue reading
Worth Reading: Hardware Packet Capture Failures
Greg Ferro is back with some great technical content, this time explaining why hardware-based packet capture might return unexpected results.