Discussion Paper Now Available about the New-IP Proposal
In the run up to the ITU World Telecommunication Standardization Assembly (WTSA-20) later this year there has been some discussion about a proposal called the “New IP.” It is positioned as a top-down architecture to solve a number of use cases that are currently been developed in the ITU-T’s Future Network 2030 Focus Group.
The Internet Society is carefully following the developments in the run-up to WTSA-20. We are trying to understand if and how the New IP works with the Internet as we know it, if it actually solves problems that cannot be solved in the Internet, and, if the ITU-T is developing standards, where other standards development organizations (SDOs) have change control.
In order to get a sense of the environment we commissioned a discussion paper, “An analysis of the ‘New IP’ proposal to the ITU-T.” The paper helps inform us and the broader community whilst the public debate around these proposals shapes up. It also aims to inform and shape the discussion from the Internet’s Society’s perspective. Eventually the debate around it will inform our position and the potential further evolution of the discussion paper itself.
We would like to thank Chip Sharp for authoring the paper, with input Continue reading
Network Break 281: FCC Opens 6Ghz Band For Unlicensed Use; Arista Boosts WLAN Software
The FCC makes swathes of new spectrum available for Wi-Fi, Arista upgrades its WLAN software, Cisco and Google announce plans to partner on an SD-WAN solution for Google Cloud, Google rolls out a remote access product for the enterprise, and more tech news analysis on today's Network Break podcast.
The post Network Break 281: FCC Opens 6Ghz Band For Unlicensed Use; Arista Boosts WLAN Software appeared first on Packet Pushers.
Network Break 281: FCC Opens 6Ghz Band For Unlicensed Use; Arista Boosts WLAN Software
The FCC makes swathes of new spectrum available for Wi-Fi, Arista upgrades its WLAN software, Cisco and Google announce plans to partner on an SD-WAN solution for Google Cloud, Google rolls out a remote access product for the enterprise, and more tech news analysis on today's Network Break podcast.The Week in Internet News: Schools Still Face Equipment Challenges for Virtual Learning

Equipment shortages: As schools in the U.S. and other countries attempt to switch over to virtual learning during the COVID-19 pandemic, some are still trying to get students Internet access or devices to use to access the Internet. In Chicago, only about half of the 115,000 public school students who need a computer have received one, WBEZ reports. Another 43,000 computers will be handed out, and 10,000 have been ordered and will be coming “over the next few weeks.”
Equipment shortages, part 2: In California, the state is planning to distribute laptops, Chromebooks, or tablets to more than 70,000 students so they can participate in distance learning, MercuryNews.com reports. The state has requested funding and devices from companies, business leaders and philanthropists around the state.
Getting creative: Some schools are exploring alternatives when students don’t have Internet access or devices, NBC News says. A teacher in Tennessee turned to using a copy machine to print out packets and mail them to students. In Arkansas, where 23 percent of households lack Internet service, a local PBS affiliate is providing daily television programming tied to the state’s distance learning curriculum.
Pumping up encryption: Popular video conferencing app Zoom will Continue reading
Releasing kubectl support in Access
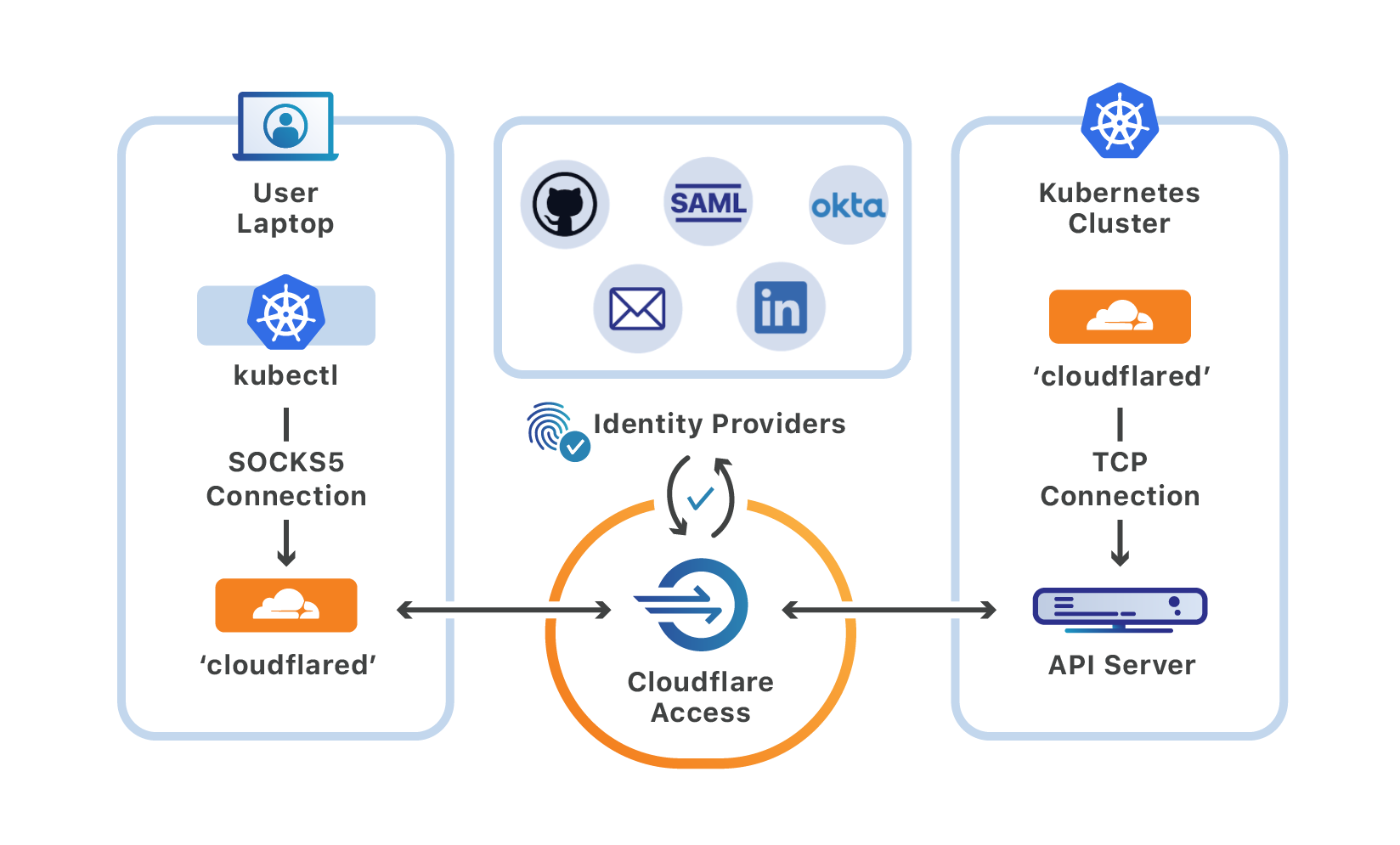
Starting today, you can use Cloudflare Access and Argo Tunnel to securely manage your Kubernetes cluster with the kubectl command-line tool.
We built this to address one of the edge cases that stopped all of Cloudflare, as well as some of our customers, from disabling the VPN. With this workflow, you can add SSO requirements and a zero-trust model to your Kubernetes management in under 30 minutes.
Once deployed, you can migrate to Cloudflare Access for controlling Kubernetes clusters without disrupting your current kubectl workflow, a lesson we learned the hard way from dogfooding here at Cloudflare.
What is kubectl?
A Kubernetes deployment consists of a cluster that contains nodes, which run the containers, as well as a control plane that can be used to manage those nodes. Central to that control plane is the Kubernetes API server, which interacts with components like the scheduler and manager.
kubectl is the Kubernetes command-line tool that developers can use to interact with that API server. Users run kubectl commands to perform actions like starting and stopping the nodes, or modifying other elements of the control plane.
In most deployments, users connect to a VPN that allows them to run commands against that Continue reading
HS. Part 4. Forging Microsoft SONiC configuration out of the network graph.
Hello my friend,
The visualisation of the network graph is an important part of the network development and management, but we need to move on. Today we will focus on the configuration for Microsoft SONiC running as Docker containers.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
Network automation training – boost your career
To be able to understand and, more important, to create such a solutions, you need to have a holistic knowledge about the network automation. Come to our network automation training to get this knowledge and skills.

At this training we teach you all the necessary concepts such as YANG data modelling, working with JSON/YAML/XML data formats, Linux administration basics, programming in Bash/Ansible/Python for multiple network operation systems including Cisco IOS XR, Nokia SR OS, Arista EOS and Cumulus Linux. All the most useful things such as NETCONF, REST API, OpenConfig and many others are there. Don’t miss the opportunity to improve your career.
Brief description
As we pointed out Continue reading
Network Automation and Hammer of Thor
Imagine that you just stumbled upon the hammer Thor carelessly dropped, and you’re so proud of your new tool that everything looks like a nail even though it might be a lightbulb or an orange.
That happens to some people when they get the network automation epiphany: all of a sudden CLI and manual configuration should be banned, and everything can be solved by proper incantation of Git and Ansible commands or whatever other workflow you might have set up… even though the particular problem might have nothing to do with what you have just automated.
How Did Big Tech Celebrate Earth Day 2020?
Cisco, Google, IBM, Intel, and Microsoft stepped up their Earth Day commitments, promising...
MUST READ: When Programming a System with High Kinetic Energy
Kode Vicious (aka George V. Neville-Neil ) wrote another brilliant article on reducing risk in systems that can do serious harm. Here are just two of the gems:
The risks involved in these systems come from three major areas: marketing, accounting, and management.
There is a wealth of literature on safety-critical systems, much of which points in the same direction: toward simplicity. With increasing complexity comes increasing risk …
For whatever reason most networking- and virtualization vendors joined a lemming-like run in the opposite direction years ago.
EVPN-VXLAN | Virtual Gateway |QFX5k Forwarding | JUNOS
In this post, I want to discuss how to verify Virtual Gateway forwarding behaviour on Broadcom based Juniper QFX switches.
The general assumption with EVPN Anycast Gateway is that gateway flows are load-balanced across all gateway devices. And whilst EVPN provides the mechanism to support this behaviour, there is a requirement for the forwarding hardware to also support it.
The mechanism for an EVPN device to load balance gateway flows is to install the virtual gateway ESI as a next-hop for the virtual gateway MAC address. However, Broadcom based QFX switches do not support this behaviour and can only install a single VTEP as a next-hop. So this means that traffic flows heading towards the virtual gateway will only ever traverse via a single gateway device. This behaviour is well documented and there are some talks about Broadcom working with the vendors to improve gateway load-balancing with ESI functionality.
Now we understand the characteristics, let’s look at the steps to verify forwarding behaviour on a Broadcom based QFX switch. Here we’ll look at how to identify which VTEP is being used to reach the virtual-gateway MAC address and how the underlay is transporting the traffic.
Lab Setup
The lab setup Continue reading
SD-WAN Complexity Remains Adoption Burden, Says Aryaka
According to the vendor's latest annual survey, 37% of respondents named complexity as their No. 1...
Interview: Impact of COVID-19 on Networking Engineers and Public Cloud
Ben Friedman and his team (the video crew producing all the Tech Field Day events) published a number of interviews about the impact of COVID-19 on IT.
Among other things we discussed how busy networking engineers are trying to cope with unexpected demand, and how public cloud isn’t exactly infinitely elastic.
Juniper Branch SRX LACP Weirdness
Juniper SRX 300 Series firewalls may stop forwarding traffic in some situations. The firewall says it is forwarding the traffic, but it doesn’t work. Monitoring traffic looks OK, ARP entries are present, but traffic never gets to the destination, until you clear ARP. Turns out the problem comes from using LACP with fast timers and active mode. Luckily the fix is simple.
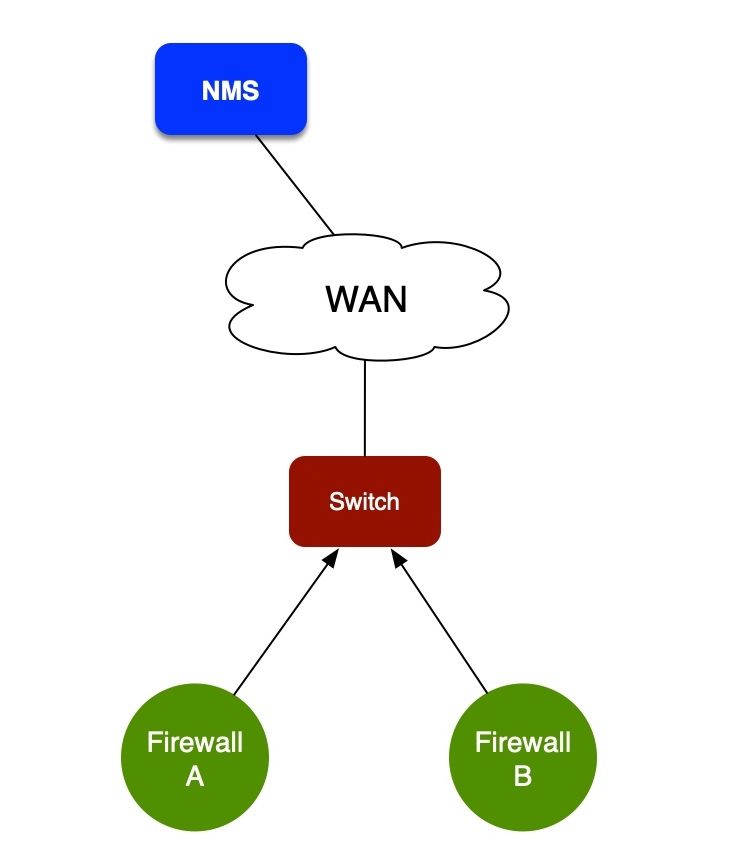
Alert: Firewall Offline
Here’s the situation we saw: Our NMS reported a Juniper SRX320 offline. All other devices at the site were still working, but the firewall was unreachable. Traffic from the firewall to the NMS goes via the firewall’s default gateway. Firewall A in this diagram was unreachable, but Firewall B was fine.
OK, what’s happening? Why is my firewall unreachable?
Firewall says its fine?
Try to ping Firewall A, no response. From the default gateway, we can see an ARP entry for the firewall, but no response to ping. We can log in to Firewall B, and we see an ARP entry for Firewall A. Crucially: we can ping Firewall A from Firewall B. Hmmm. That’s strange. Why can we ping it from one locally connected device but not another?
From Firewall B, we SSH across Continue reading
Juniper Branch SRX LACP Weirdness
Juniper SRX 300 Series firewalls may stop forwarding traffic in some situations. The firewall says it is forwarding the traffic, but it doesn’t work. Monitoring traffic looks OK, ARP entries are present, but traffic never gets to the destination, until you clear ARP. Turns out the problem comes from using LACP with fast timers and active mode. Luckily the fix is simple.
Alert: Firewall Offline
Here’s the situation we saw: Our NMS reported a Juniper SRX320 offline. All other devices at the site were still working, but the firewall was unreachable. Traffic from the firewall to the NMS goes via the firewall’s default gateway. Firewall A in this diagram was unreachable, but Firewall B was fine.
OK, what’s happening? Why is my firewall unreachable?
Firewall says its fine?
Try to ping Firewall A, no response. From the default gateway, we can see an ARP entry for the firewall, but no response to ping. We can log in to Firewall B, and we see an ARP entry for Firewall A. Crucially: we can ping Firewall A from Firewall B. Hmmm. That’s strange. Why can we ping it from one locally connected device but not another?
From Firewall B, we SSH across Continue reading
Untangle Rolls Out Predictive Routing to SD-WAN Router
The technology is designed to translate information from packet headers, out of band information,...
WiFi 6 Feeds Need for Speed With 5X Spectrum Boost
It’s the largest swath of spectrum allocated for WiFi since 1989, and it comes as WiFi 6 begins...