Cloud Automation Example: Create a Virtual Network
One of the first hands-on exercises in our Networking in Public Cloud Deployments asks the attendees to automate something. They can choose the cloud provider they want to work with and the automation tool they prefer… but whatever they do has to be automated.
Most solutions include a simple CloudFormation, Azure Resource Manager, or Terraform template with a line or two of README.MD, but Eric Auerswald totally astonished me with a detailed and precise writeup. Enjoy!
Nokia Blends AI, Cloud for 5G Automation
Nokia AVA 5G Cognitive Operations is designed to increase automation of network operations by...
New Category of CDNs and Cloud Providers Join MANRS to Improve Routing Security

Today, we’re proud to announce the new MANRS Content Delivery Network (CDN) and Cloud Programme. This new program broadens support for the primary objective of MANRS – to implement crucial fixes needed to eliminate the most common threats to the Internet’s routing system.
The founding participants are: Akamai, Amazon Web Services, Azion, Cloudflare, Facebook, Google, Microsoft, and Netflix.
Now, let’s back up and explain how we got here.
What Is MANRS?
Mutually Agreed Norms for Routing Security (MANRS) is a global initiative, supported by the Internet Society, that requires collaboration among participants and shared responsibility for the global Internet routing system. It’s a community of security-minded organizations committed to making routing infrastructure more robust and secure.
Originally designed by and for network operators, the initiative has already been extended once to address the unique needs and concerns of Internet Exchange Points. These two facets of MANRS complement each other – the first secures customer-provider interconnections, while the second creates a safe public peering environment.
How Do CDNs and Cloud Providers Help?
CDNs are a geographically distributed group of servers that work together to provide fast delivery of Internet content across the globe, and today the majority of web traffic Continue reading
Daily Roundup: Microsoft Cloud Usage Spikes 775%
Microsoft cloud usage has spiked 775%; Google gifted $800 million to slow the spread of COVID-19;...
Coronavirus Sneezes All Over Server, Storage Markets
IDC predicts server market revenues will decline 3.4% year over year to $88.6 billion in 2020 while...
Tech Bytes: Four Phases Of Scaling Your Remote Workforce With Viavi Solutions (Sponsored)
As more employees work from home, organizations are struggling with the rollout and support of remote work forces. On today's Tech Bytes podcast we walk through the four phases of scaling up remote workers with our sponsor, Viavi Solutions. Viavi provides network performance monitoring and visibility products. Our guest is Bill Proctor, Customer Success Manager at Viavi.Tech Bytes: Four Phases Of Scaling Your Remote Workforce With Viavi Solutions (Sponsored)
As more employees work from home, organizations are struggling with the rollout and support of remote work forces. On today's Tech Bytes podcast we walk through the four phases of scaling up remote workers with our sponsor, Viavi Solutions. Viavi provides network performance monitoring and visibility products. Our guest is Bill Proctor, Customer Success Manager at Viavi.
The post Tech Bytes: Four Phases Of Scaling Your Remote Workforce With Viavi Solutions (Sponsored) appeared first on Packet Pushers.
Microsoft Cloud Usage Spikes 775% in COVID-19 Hot Spots
The company said the increase was in areas operating under enforced social distancing or...
5G Enterprise Plans Blossom at SK Telecom
The operator plans to build 5G mobile edge computing centers in 12 locations across South Korea to...
Google Gifts $800M to SMBs, Health Care as COVID-19 Spreads
The cloud giant is also working with Magid Glove & Safety to ramp up production of 2 million...
In New York City, Building a Network While Social Distancing

NYC Mesh connects people to “critical Internet lifeline” during COVID-19 pandemic
As COVID-19 spreads across the globe, cities are slowing to a halt and millions of people are self-isolating to help slow the spread of the virus.
The Internet has never been more important. It is a critical for up-to-date health information, a necessity for students to continue their education while at home and for their parent to continue working, enables access to government programs and supports like unemployment insurance, and can help alleviate the effects of social isolation.
Yet, in New York City alone, 1.5 million people don’t have access from their homes or mobile devices, largely due to high costs of connectivity.
A group of volunteers is working around the clock to change that, one antenna at a time.
NYC Mesh, a community network supported by the Internet Society, kicked into high gear earlier this month in advance of the pandemic, getting as many people connected as possible while it was still safe to do so, prioritizing those with no other Internet access. The ramp up –going from a couple of installs a week to one or more a day – was “a mad rush of Continue reading
The Week in Internet News: U.S. Senator Fears Attacks on Connectivity

Networked virus: U.S. Senator Mark Warner has raised concerns about cyberattacks targeting Internet connectivity while many people are working from home due to the COVID-19 outbreak, The Hill reports. Warner, vice chairman on the Senate Intelligence Committee, wrote letters to network device vendors asking that they pump up the security of their products.
Sharing the WiFi: The U.S. Federal Communications Commission will allow schools and libraries to share their WiFi connections with the surrounding communities during the coronavirus pandemic, a change in the normal FCC policy about their WiFi networks, KRCRTV.com reports. Schools and libraries can set their own WiFi-sharing policies, the FCC said. Meanwhile, some libraries want to extend their WiFi networks using bookmobiles, Vice.com says. It’s unclear if FCC rules allow this expansion of service, however.
Tracking you and the virus: Some countries are tracking the coronavirus outbreak by tracking residents’ mobile phones, Science Magazine says. However, tracking phones also raises privacy concerns. “We don’t live in a culture of public trust when it comes to data,” says David Leslie, an ethicist at the Alan Turing Institute. “We live in this age that has been called the age of surveillance capitalism, where … our Continue reading
Comcast’s Jeffrey Lewis: ‘Job No. 1 Is Customer Experience’
Comcast's Jeffery Lewis sat down to share his thoughts on ActiveCore and how it is improving the...
Network Break 277: Juniper’s Mist Systems Announces Premium Analytics; Cato Launches Clientless Remote Access
Today's Network Break podcast examines a new analytics service from Juniper's Mist Systems for engineers and lines of business, a new clientless remote access service from Cato Networks, the impact of increased traffic on Facebook and cloud services, how co-lo sites are restricting physical access, and more.
The post Network Break 277: Juniper’s Mist Systems Announces Premium Analytics; Cato Launches Clientless Remote Access appeared first on Packet Pushers.
Network Break 277: Juniper’s Mist Systems Announces Premium Analytics; Cato Launches Clientless Remote Access
Today's Network Break podcast examines a new analytics service from Juniper's Mist Systems for engineers and lines of business, a new clientless remote access service from Cato Networks, the impact of increased traffic on Facebook and cloud services, how co-lo sites are restricting physical access, and more.Heavy Networking 508: Should Network Engineers Learn Advanced Programming Languages?
Today's Heavy Networking explores what it's like to get deeply into programming while still being attached to the world of networking. We discuss the transition from day-to-day networking tasks to spending more time with code, the role of programming in automation, and more. Our guests are Matt Stone, Brent Salisbury, Dave Tucker, and Daryn Johnson.Heavy Networking 508: Should Network Engineers Learn Advanced Programming Languages?
Today's Heavy Networking explores what it's like to get deeply into programming while still being attached to the world of networking. We discuss the transition from day-to-day networking tasks to spending more time with code, the role of programming in automation, and more. Our guests are Matt Stone, Brent Salisbury, Dave Tucker, and Daryn Johnson.
The post Heavy Networking 508: Should Network Engineers Learn Advanced Programming Languages? appeared first on Packet Pushers.
Introducing Quicksilver: Configuration Distribution at Internet Scale
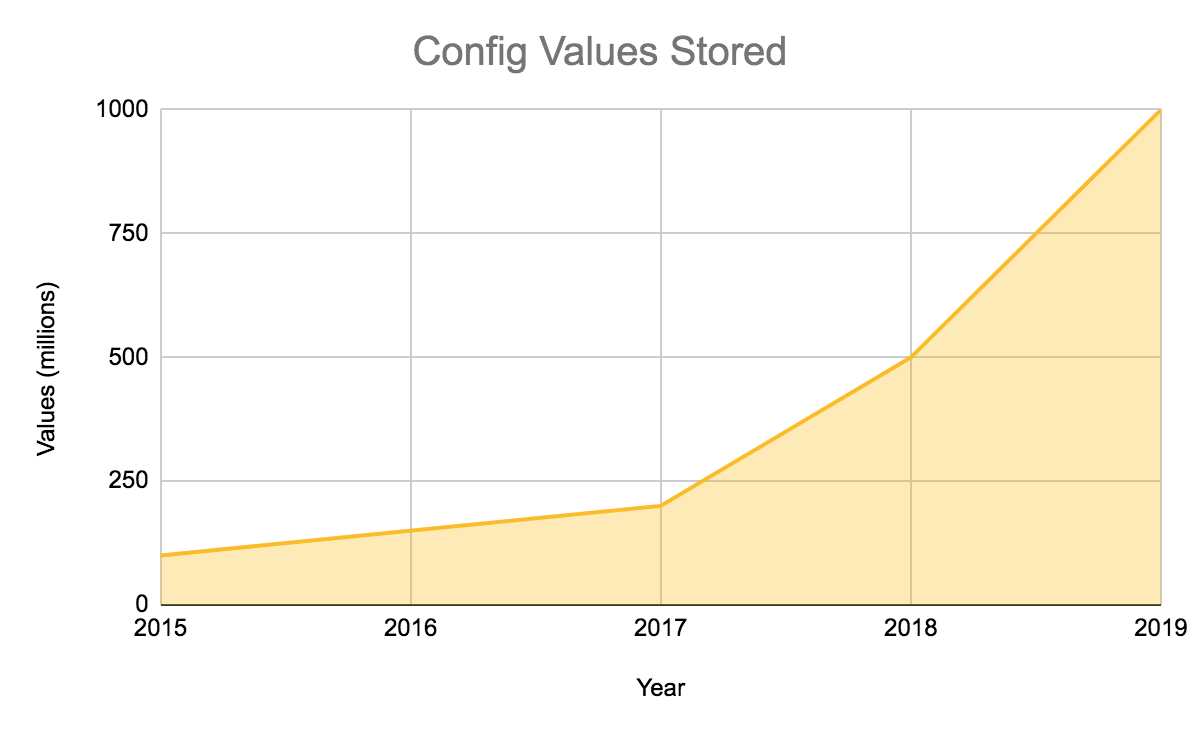
Cloudflare’s network processes more than fourteen million HTTP requests per second at peak for Internet users around the world. We spend a lot of time thinking about the tools we use to make those requests faster and more secure, but a secret-sauce which makes all of this possible is how we distribute configuration globally. Every time a user makes a change to their DNS, adds a Worker, or makes any of hundreds of other changes to their configuration, we distribute that change to 200 cities in 90 countries where we operate hardware. And we do that within seconds. The system that does this needs to not only be fast, but also impeccably reliable: more than 26 million Internet properties are depending on it. It also has had to scale dramatically as Cloudflare has grown over the past decade.
Historically, we built this system on top of the Kyoto Tycoon (KT) datastore. In the early days, it served us incredibly well. We contributed support for encrypted replication and wrote a foreign data wrapper for PostgreSQL. However, what worked for the first 25 cities was starting to show its age as we passed 100. In the summer of 2015 we decided to Continue reading