Claris Rides Apple Hook for Low-Code Nirvana
The low-code vendor is Apple's only direct software play in the B2B space.
RPKI and the RTR protocol
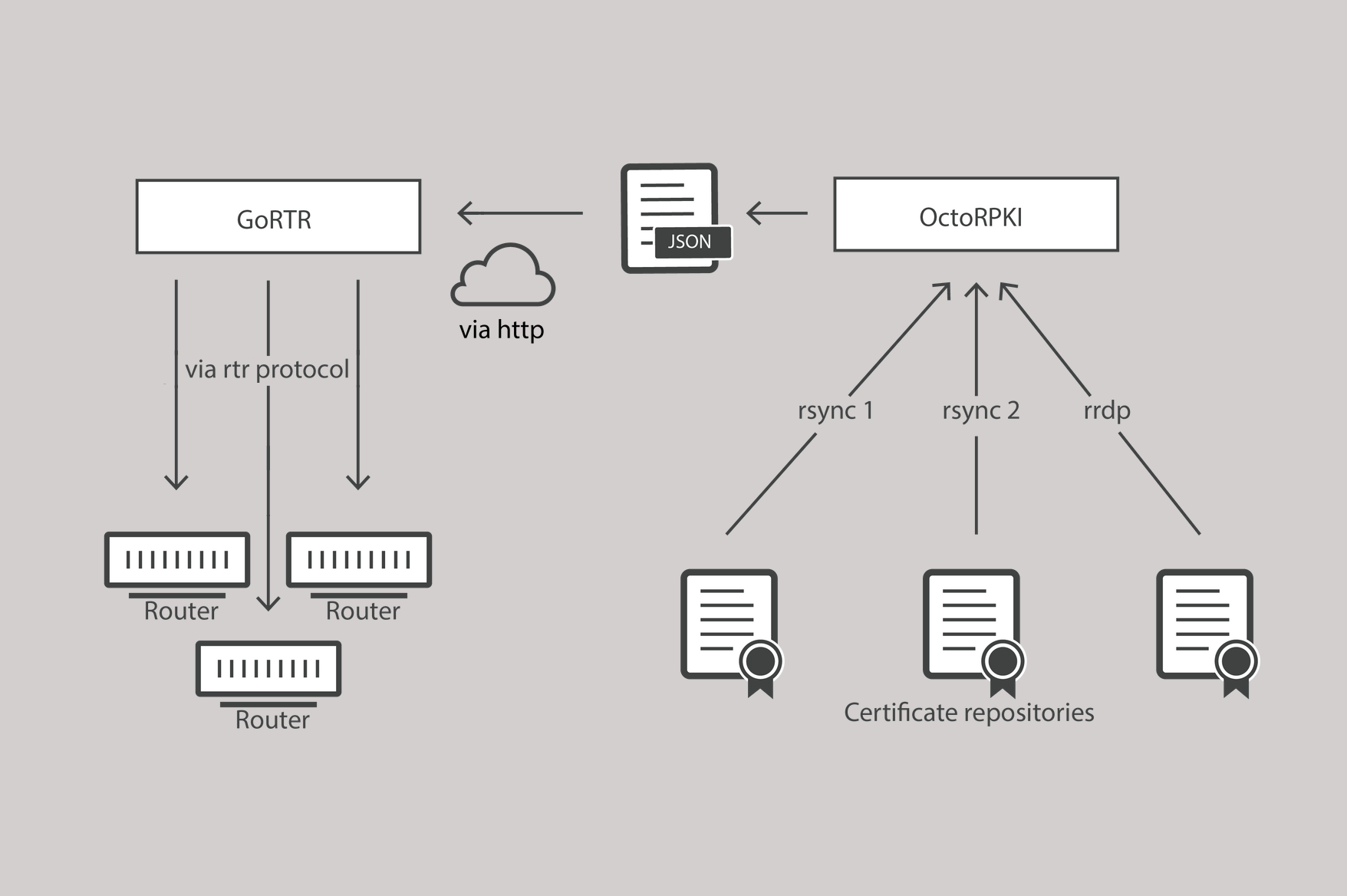
Today’s Internet requires stronger protection within its core routing system and as we have already said: it's high time to stop BGP route leaks and hijacks by deploying operationally-excellent RPKI!
Luckily, over the last year plus a lot of good work has happened in this arena. If you’ve been following the growth of RPKI’s validation data, then you’ll know that more and more networks are signing their routes and creating ROA’s or Route Origin Authorizations. These are cryptographically-signed assertions of the validity of an announced IP block and contribute to the further securing of the global routing table that makes for a safer Internet.
The protocol that we have not written much about is RTR. The Resource Public Key Infrastructure (RPKI) to Router Protocol - or RTR Protocol for short. Today we’re fixing that.
RPKI rewind
We have written a few times about RPKI (here and here). We have written about how Cloudflare both signs its announced routes and filters its routing inbound from other networks (both transits and peers) using RPKI data. We also added our efforts in the open-source software space with the release of the Cloudflare RPKI Toolkit.
The primary part of the RPKI (Resource Continue reading
Addressing the Web’s Client-Side Security Challenge

Modern web architecture relies heavily on JavaScript and enabling third-party code to make client-side network requests. These innovations are built on client-heavy frameworks such as Angular, Ember, React, and Backbone that leverage the processing power of the browser to enable the execution of code directly on the client interface/web browser. These third-party integrations provide richness (chat tools, images, fonts) or extract analytics (Google Analytics). Today, up to 70% of the code executing and rendering on your customer’s browser comes from these integrations. All of these software integrations provide avenues for potential vulnerabilities.
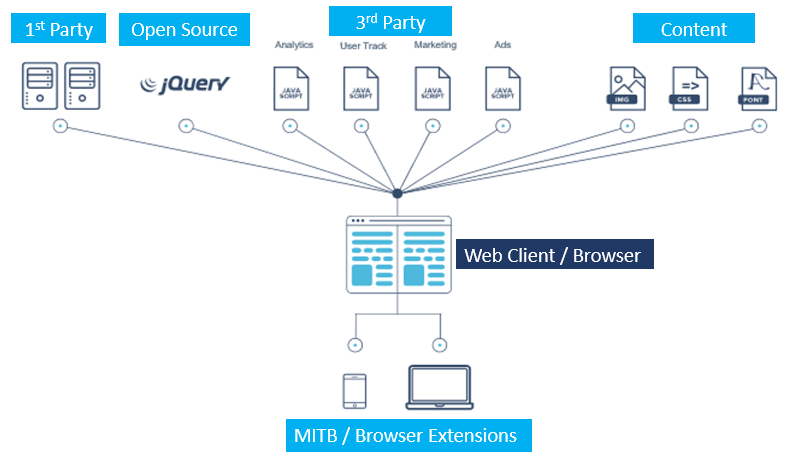
Unfortunately, these unmanaged, unmonitored integrations operate without security consideration, providing an expansive attack surface that attackers have routinely exploited to compromise websites. Today, only 2% of the Alexa 1000 global websites were found to deploy client-side security measures to protect websites and web applications against attacks such as Magecart, XSS, credit card skimming, session redirects and website defacement.
Improving website security and ensuring performance with Cloudflare Workers
In this post, we focus on how Cloudflare Workers can be used to improve security and ensure the high performance of web applications. Tala has joined Cloudflare’s marketplace to further our common goals of ensuring website security, preserving data privacy and Continue reading
The Myth of Lossless vMotion
As a response to my Live vMotion into VMware-on-AWS Cloud blog post Nico Vilbert pointed me to his blog post explaining the details of cross-Atlantic vMotion into AWS.
Today I will not go into yet another rant pointing out all the things that can go wrong, but focus on a minor detail: “no ping was dropped in the process.”
The vMotion is instantaneous and lossless myth has been propagated since the early days of vMotion when sysadmins proudly demonstrated what seemed to be pure magic to amazed audiences… including the now-traditional terminal window running ping and not losing a single packet.
Read more ...The Myth of Lossless vMotion
As a response to my Live vMotion into VMware-on-AWS Cloud blog post Nico Vilbert pointed me to his blog post explaining the details of cross-Atlantic vMotion into AWS.
Today I will not go into yet another rant pointing out all the things that can go wrong, but focus on a minor detail: “no ping was dropped in the process.”
The vMotion is instantaneous and lossless myth has been propagated since the early days of vMotion when sysadmins proudly demonstrated what seemed to be pure magic to amazed audiences… including the now-traditional terminal window running ping and not losing a single packet.
Virtual Conferences – Nice In Theory
As COVID-19 (Corona) has spread around the world, and while we can argue how serious that is, a lot of tech conferences have been cancelled, and rightfully so. Safety always comes first.
People have suggested that virtual conferences could be a replacement, but as I’ll explain in this blog, they can never really replace a standard conference, rather just be a complement.
First, let me just clear a couple of things:
- Safety comes first, if the prize of safety is to cancel a tech conference, that’s a small prize to pay
- We should generally try to travel less and replace some of the travel with the use of collaboration apps such as Webex, Zoom etc
- There are virtual conferences, such as the PacketPushers VDC, that do work in a virtual format
The first challenge is that we are all in different time zones. When I go to Cisco Live in the US, I adjust to the US time. If I’m staying here in Sweden, I’m not going to stay up late to watch a stream coming from the US.
When you travel to a conference, you are away from work and family, you have dedicated that time to make the Continue reading
The First Ethiopia Internet Development Conference: Meeting Challenge and Opportunity Head On

When it comes to Ethiopia’s future online, there are many reasons to feel optimistic.
The country has one of the fastest-growing economies in the region, is strategically placed, and has a population of over 105 million, 60% of whom are under the age of 30. All of these are assets to make it a regional digital giant.
But this won’t happen unless Ethiopia takes some strategic moves. Internet penetration is still very low compared to its peers in Africa. The rural areas are still largely unconnected to the Internet. Only cities enjoy 3G access and 4G is only available in the capital. In spite of successive price cuts by Ethio telecom in the last year, the Internet is not affordable for the majority of Ethiopians.
It’s not that the government has not wanted to connect the rural areas. In fact, the rationale that the Ethiopian government had to keep the monopoly was to use the money generated from cities to invest in the rural areas. However, this strategy has clearly not worked since Ethiopia’s rural areas are not better connected than those in countries that have not had a government monopoly on the sector, such as Kenya.
It is Continue reading
Daily Roundup: Nokia CEO Walks the Plank
Nokia CEO walked the plank; VMware's winning streak came to a screeching halt; and Marvell injected...
Internet Society Ethiopia Chapter Launched Today!

We are excited about the momentum behind Ethiopia.
It is a rare moment in any country’s history to undergo such a positive transformation. It’s a time of immense optimism and investment potential. It’s not a surprise as the country also has one of the fastest-growing economies in the region, is strategically placed, and has a young population of over 105 million – half of whom are under the age of 18.
While we’ve been active in the Internet world for many years, the time to start a Chapter in Ethiopia is absolutely now. With that, let me share our “why” and introduce ourselves.
We are the Internet Society Ethiopia Chapter.
The idea of starting an Internet Society Chapter came to us during a workshop in the city of Bahir Dar, where we became conscious of the fact that more than 85% of the Ethiopia population is losing countless opportunities every day because they don’t have access to the Internet. We believe the Internet is for everyone and we are here to work with all people – from communities to businesses to governments and ordinary people to connect the unconnected and create a bigger and stronger Internet in Ethiopia. What drives Continue reading
Infor, Snowflake Unite to Birst Open BI Analytics
Joint customers will be able utilize Birst's integrated end-to-end platform for building automated...
Network Break 273: Fortinet Pits Deep Learning Appliance Against Malware; Nokia ‘Reviews Options’ As Earnings Struggle
Take a Network Break. This week's IT news analysis covers a new anti-malware appliance from Fortinet, VMware security software for data centers and clouds, Nokia's efforts to buy time as it gets its 5G house in order, and financial results from multiple vendors.Network Break 273: Fortinet Pits Deep Learning Appliance Against Malware; Nokia ‘Reviews Options’ As Earnings Struggle
Take a Network Break. This week's IT news analysis covers a new anti-malware appliance from Fortinet, VMware security software for data centers and clouds, Nokia's efforts to buy time as it gets its 5G house in order, and financial results from multiple vendors.
The post Network Break 273: Fortinet Pits Deep Learning Appliance Against Malware; Nokia ‘Reviews Options’ As Earnings Struggle appeared first on Packet Pushers.
Similarities Between AWS VPC and Cisco SDA – Intra-Subnet Communication
Update March 6, 2020: This post will be obsolete soon by a new version
Forewords
There are two main reasons for writing this document:
First, Cisco SDA is an on-prem LAN model while the AWS VPC is an off-prem DC solution. I wanted to point out that these two solutions, even though used for very different purposes, use the same kind of Control-Plane operation and Data-Plane encapsulation and are managed via QUI. This is kind of my answer to ever going discussion about is there DC-networks, Campus-networks and so on, or is there just networks.
Second, my own curiosity to understand the operation of AWS VPC.
I usually start by introducing the example environment and then explaining the configuration, moving to Control-Plane operation and then to Data-Plane operation. However, this time I take a different approach. This article first introduces the example environment but then the Data-Plane operation is discussed before Control-Plane operation. This way it is easier to understand what information is needed and how that information is gathered.
Continue reading
Cisco’s Wendy Nather: Never Say This to a CISO
When Cisco acquired Duo Security, Nather’s was the only CISO advisory team. Cisco quickly saw the...
Marvell Injects New Life Into Infrastructure Chips
The chips are designed to power networking equipment like switches, routers, secure gateways,...
Nokia Taps New Captain After Missing 5G Boat
Pekka Lundmark, who currently serves as president and CEO of Fortum, an energy company also...
Heavy Networking 504: The State Of Optical Networking In 2020
If you're new to DWDM and optical networking, this Heavy Networking episode aims to peel back some of the layers of these technologies to help you understand how they work, and whether you have business applications that could use DWDM. My guest is Chris Tracy, a network and systems engineer at ESnet.Heavy Networking 504: The State Of Optical Networking In 2020
If you're new to DWDM and optical networking, this Heavy Networking episode aims to peel back some of the layers of these technologies to help you understand how they work, and whether you have business applications that could use DWDM. My guest is Chris Tracy, a network and systems engineer at ESnet.
The post Heavy Networking 504: The State Of Optical Networking In 2020 appeared first on Packet Pushers.
Tech Bytes: Is SDN A Revolution Or An Evolution Of Traditional Networks? (Sponsored)
On today's Tech Bytes podast we talk with sponsor CodiLime about the benefits of SDN, how SDN works, and CodiLime's network engineering services that help organizations of all sizes migrate to SDN. Our guest Monika Antoniak, head of R&D at CodiLime.
The post Tech Bytes: Is SDN A Revolution Or An Evolution Of Traditional Networks? (Sponsored) appeared first on Packet Pushers.