US Pledges $1B to Roast Huawei With Open RAN 5G
The proposed funding pales in comparison to the amount of money Huawei and other RAN stalwarts are...
Managing Financial Network Threats with SD-Branch
Financial networks are at a constant risk — especially since they rely on risky IoT devices....
Arista Networks Buys Big Switch
Several incumbent networking players, including Cisco, Dell Technologies, VMware, Juniper Networks,...
Dyndns and Openvpn – Remote Management
I have visited my home and was doing some hobby IT setup with Raspberry Pi’s, the problem is that i had problems many times accessing my home PC is another Remote Location due to many reasons, lets say crappy ISP. I contacted my ISP and they said I need to take a static IP and also pay for opening up two non standard ports. Its like you pay to get tortured and then additional headache of Port forwarding.
To add more to the pain, the IP that i get from my upstream provider is a Private IP, wow I havent seen that for a while. Anyways, to get around this I was thinking about using OPENVPN as a solution along with Dyndns.
Now, setup is very simple
Clint-pc (Location 1) ———-AWS(OPENVPN)————Client-pc (Location 2)
Why AWS -> Accessible and Cost
Problem is changing IP, I dont have any business requirement or criticality to buy a Elastic IP , but whole point will be lost if my clients wont know what to access, worse I will never have access to location-2 if am in location-1 to change IP Addresses
I have mapped OPENVPN with dyndns script.
https://help.dyn.com/ddclient/
This really solved Continue reading
Writing Tip: Auto-spelling to Avoid Words

Autocorrect to improve my writing
The post Writing Tip: Auto-spelling to Avoid Words appeared first on EtherealMind.
Verizon Exec Launches Privafy, Challenges Firewall, SD-WAN, VPN Vendors
The security startup has about a dozen paying customers and is “working with some of the largest...
Day Two Cloud 032: The Foggy Path To Cloud Certification
Certifications are a tried and true way to boost skills and knowledge, burnish your resume, and create new opportunities. But when it comes to cloud, which certifications should you pursue? Can cloud cert programs keep up with technology churn and rapid rollout of new services? How should you study? What if you fail? We tackle all these questions and more with guest Mike Pfeiffer.
The post Day Two Cloud 032: The Foggy Path To Cloud Certification appeared first on Packet Pushers.
Day Two Cloud 032: The Foggy Path To Cloud Certification
Certifications are a tried and true way to boost skills and knowledge, burnish your resume, and create new opportunities. But when it comes to cloud, which certifications should you pursue? Can cloud cert programs keep up with technology churn and rapid rollout of new services? How should you study? What if you fail? We tackle all these questions and more with guest Mike Pfeiffer.Red Hat, Cloud Save IBM
More than 2,000 IBM clients were using its container systems, and it signed 21 Red Hat deals in Q4...
Migration from VMware NSX for vSphere to NSX-T
Migration to VMware NSX-T Data Center (NSX-T) is top of mind for customers who are on NSX for vSphere (NSX-V). Broadly speaking, there are two main methods to migrate from NSX for vSphere to NSX-T Data Center: In Parallel Migration and In Place Migration. This blog post is a high-level overview of the above two approaches to migration.
2 Methods for VMware NSX Migration
Customers could take one of two approaches for migration.
In Parallel Migration:
In this method, NSX-T infrastructure is deployed in parallel along with the existing NSX-V based infrastructure. While some components of NSX-V and NSX-T, such as management, could coexist, compute clusters running the workloads would be running on its own hardware. This could be net new hardware or reclaimed unused hardware from NSX-V.
Migration of the workload in this approach could take couple of different approaches.
- Cattle: New workloads are deployed on NSX-T and the older workloads are allowed to die over time.
- Pets: Lift and shift workloads over to the new NSX-T infrastructure.
In Place Migration
There is simpler method though! A method that doesn’t require dedicated hardware. It’s an in place migration approach. Curious? This method uses Continue reading
ShortestPathFirst Now Has a New, Shorter Domain Name – spfirst.net
ShortestPathFirst now has a new, shorter domain name (spfirst.net) that we intend to use for future correspondence, marketing and business initiatives. We will continue to maintain the longer domain (shortestpathfirst.net) for backward compatibility and for business continuity but for all intents and purposes will use the new domain name where possible. Stay tuned for lots …Continue reading "ShortestPathFirst Now Has a New, Shorter Domain Name – spfirst.net"
5G and Me: And Security
In today’s uber-connected world, everyone has dealt with that little voice in the back of the...
Vapor IO Raises $90M to Build ‘Nationwide’ Edge Computing Network
It also reached an agreement for Cloudflare to deploy its cloud services on Vapor IO’s Kinetic...
Juniper to MikroTik – MPLS and VPNv4 interop

Juniper to MikroTik – a new series
Previously, I’ve written a number of articles that compared syntax between Cisco and MikroTik and have received some great feedback on them.
As such, I decided to begin a series on Juniper to MikroTik starting with MPLS and L3VPN interop as it related to a project I was working on last year.
In the world of network engineering, learning a new syntax for a NOS can be overwhelming if you need a specific set of config in a short timeframe. The command structure for RouterOS can be a bit challenging if you are used to Juniper CLI commands.
If you’ve worked with Juniper gear and are comfortable with how to deploy that vendor, it is helpful to draw comparisons between the commands, especially if you are trying to build a network with a MikroTik and Juniper router.
Lab Overview
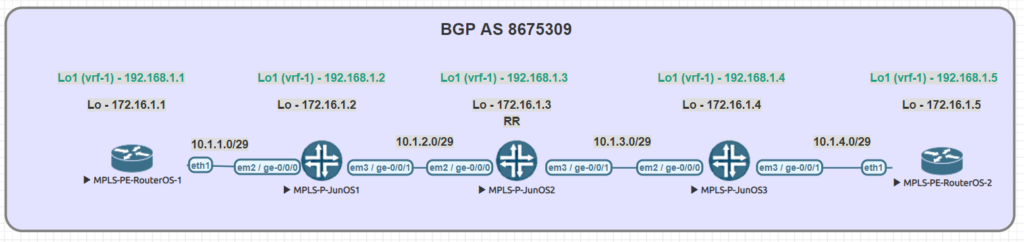
The lab consists of (3) Juniper P routers and (2) MikroTik PE routers. Although we did not get into L3VPN in this particular lab, the layout is the same.
A note on route-targets
It seems that the format of the route-target has some bearing on this being successful. Normally i’ll use a format like Continue reading
Network Field Day 22
Happy Days have returned! I have been invited to attend Network Field Day #22 (#NFD22) in San Jose, CA on …
The post Network Field Day 22 appeared first on Fryguy's Blog.
Getting More Bang for Your VXLAN Bucks
A little while ago I explained why you can’t use more than 4K VXLAN segments on a ToR switch (at least with most ASICs out there). Does that mean that you’re limited to a total of 4K virtual ethernet segments?
Of course not.
You could implement overlay virtual networks in software (on hypervisors or container hosts), although even there the enterprise products rarely give you more than a few thousand logical switches (to use NSX terminology)… but that’s a product, not technology limitation. Large public cloud providers use the same (or similar) technology to run gazillions of tenant segments.
Read more ...
