Tech Bytes: The Whys And How Of Decrypting Internal Traffic With ExtraHop (Sponsored)
ExtraHop is our sponsor for today's sponsored Tech Bytes conversation on traffic decryption. Packet data is a source of truth, and it's vital for security and operations teams to have that truth to find threats and get essential visibility into security and performance. We explore how ExtraHop's Reveal(x) NDR platform uses a variety of decryption techniques to bring visibility to encrypted data center traffic.
The post Tech Bytes: The Whys And How Of Decrypting Internal Traffic With ExtraHop (Sponsored) appeared first on Packet Pushers.
My Portable Video Rig – 2020

Will we see the return of 2 Beer Networking ?
The post My Portable Video Rig – 2020 appeared first on EtherealMind.
T-Mobile US Taps Sievert to Replace Legere As CEO
The move marks the end of John Legere’s run at the company, which began in September 2012.
Cumulus Linux 4.0 Supports New Mellanox, Broadcom Chips and Facebook Minipack
Cumulus Linux 4.0 widens its hardware support to 134 platforms across 14 ASICs including new...
AWS Absorbs More of Nokia’s 5G-Focused Software Platform
The engineering collaboration focuses on 5G platforms like mobile core, network and service...
Containers and VMs and Bare Metal, Oh My!
Discover the operational items that will significantly affect the effectiveness of your cloud...
Cumulus Networks 4th-Generation open, modern networking for applications of the future
The dynamics of IT are changing, especially when it comes to the demands on the network. As many have predicted, big data, mobile and the Internet of Things are putting significant and ever-increasing pressure on the network. Most networks and legacy management tools, therefore, are unprepared for the added stress placed on already-fragile infrastructures while the rest of the data center has sped ahead.
As more and more data is created and transferred between resources, the network must be increasingly resilient, dynamic and agile to adjust to application demands accordingly. As data and applications become increasingly distributed, there is an inherent architectural dependence on the interconnect, which enables these resources to work in concert to deliver application workloads. That interconnect, the network, must undergo its own transformation to meet the new needs of a modern network.
Our founders at Cumulus Networks recognized the challenges that were mounting nearly a decade ago and set out to build a more modern network, one that is modeled from the web-scale giants including Google, Amazon, and Facebook to better address applications of the future.
I’m very happy to announce that Cumulus Networks is now enabling customers to meet modern network challenges with our 4th-Generation Continue reading
The Week in Internet News: Let’s Encrypt Doubles the Number of Secure Websites

A more secure Internet: Let’s Encrypt, the nonprofit certificate authority, has helped the percentage of websites protected with HTTPS encryption jump from 40 percent in 2016 to 80 percent now, TechXplore notes. The free certificate service has “turned the implementation of HTTPS from a costly, complicated process to an easy step that’s within reach for all websites.” Let’s Encrypt has become the world’s largest certificate authority and provides more HTTPS certificates than all other certificate authorities combined.
The right to the Internet: A new study by Merten Reglitz, a lecturer in global ethics at the University of Birmingham, suggests Internet access should be a human right, Vice reports. Internet access is “highly conducive to a multitude of crucial human interests and rights,” the study says. “Internet access is a uniquely effective way for lobbying and holding accountable global players like global governance institutions and multinational corporations.”
You must include these apps: The Russian government may require PC and smartphone makers to pre-load Russia apps, ZDNet reports. The Russian parliament is debating a bill to require the pre-loaded apps. If the bill passes, the Russian government would publish a list of electronic devices that will need to comply Continue reading
Facts and Fiction: BGP Is a Hot Mess
Every now and then a smart person decides to walk away from their competence zone, and start spreading pointless clickbait opinions like BGP is a hot mess.
Like any other technology, BGP is just a tool with its advantages and limitations. And like any other tool, BGP can be used sloppily… and that’s what’s causing the various problems and shenanigans everyone is talking about.
Just in case you might be interested in facts instead of easy-to-digest fiction:
Read more ...Log every request to corporate apps, no code changes required
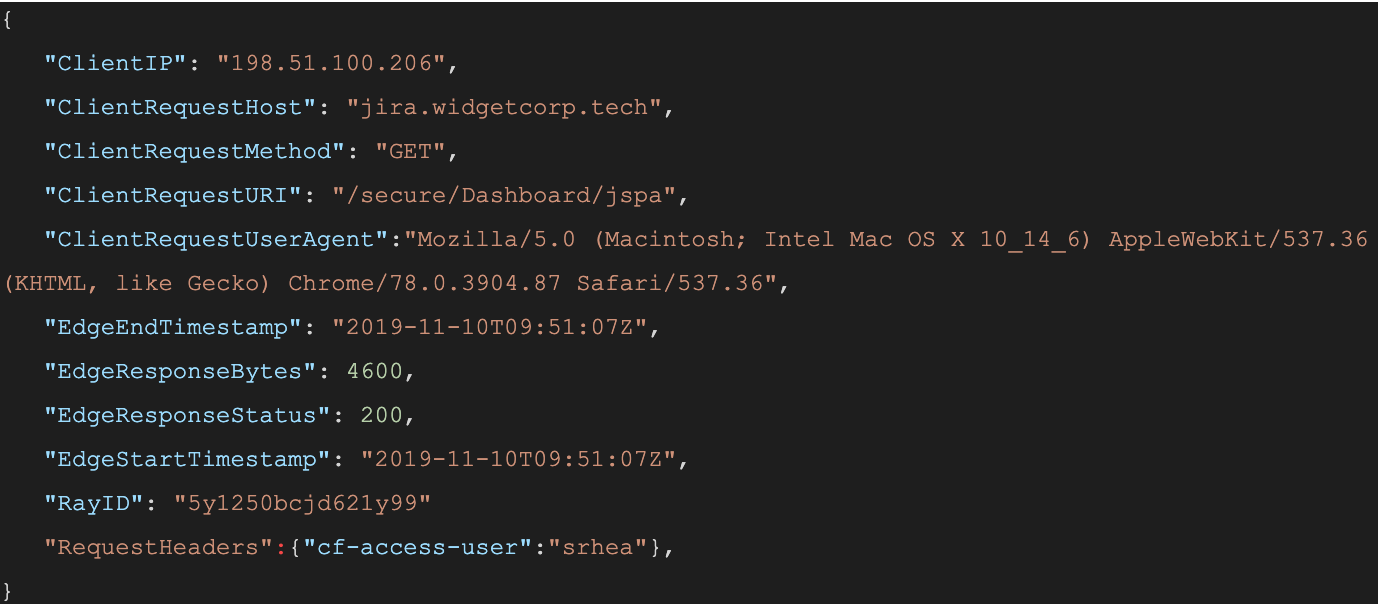
When a user connects to a corporate network through an enterprise VPN client, this is what the VPN appliance logs:
The administrator of that private network knows the user opened the door at 12:15:05, but, in most cases, has no visibility into what they did next. Once inside that private network, users can reach internal tools, sensitive data, and production environments. Preventing this requires complicated network segmentation, and often server-side application changes. Logging the steps that an individual takes inside that network is even more difficult.
Cloudflare Access does not improve VPN logging; it replaces this model. Cloudflare Access secures internal sites by evaluating every request, not just the initial login, for identity and permission. Instead of a private network, administrators deploy corporate applications behind Cloudflare using our authoritative DNS. Administrators can then integrate their team’s SSO and build user and group-specific rules to control who can reach applications behind the Access Gateway.
When a request is made to a site behind Access, Cloudflare prompts the visitor to login with an identity provider. Access then checks that user’s identity against the configured rules and, if permitted, allows the request to proceed. Access performs these checks on each request a user Continue reading