Emulating congestion with Containerlab
The Containerlab dashboard above shows variation in throughput in a leaf and spine network due to large "Elephant" flow collisions in an emulated network, see Leaf and spine traffic engineering using segment routing and SDN for a demonstration of the issue using physical switches.This article describes the steps needed to emulate realistic network performance problems using Containerlab. First, using the FRRouting (FRR) open source router to build the topology provides a lightweight, high performance, routing implementation that can be used to efficiently emulate large numbers of routers using the native Linux dataplane for packet forwarding. Second, the containerlab tools netem set command can be used to introduce packet loss, delay, jitter, or restrict bandwidth of ports.
The netem tool makes use of the Linux tc (traffic control) module. Unfortunately, if you are using Docker desktop, the minimal virtual machine used to run containers does not include the tc module.
multipass launch dockerInstead, use Multipass as a convenient way to create and start an Ubuntu virtual machine with Docker support on your laptop. If you are already on a Linux system with Docker installed, skip forward to the git clone step.
multipass lsList the multipass virtual machines.
Continue reading
Live: BGP Labs and Netlab Testing @ SINOG 8
I’ll talk about the BGP labs and the magic behind the scenes that ensures the lab configurations are correct at the SINOG 8 meeting later today (selecting the English version of the website is counter-intuitive; choose English from the drop-down field on the right-hand side of the page).
The SINOG 8 presentations will be live-streamed; I should start around 13:15 Central European Time (11:15 GMT; figuring out the local time is left as an exercise for the reader).
More NPM packages on Cloudflare Workers: Combining polyfills and native code to support Node.js APIs
Today, we are excited to announce a preview of improved Node.js compatibility for Workers and Pages. Broader compatibility lets you use more NPM packages and take advantage of the JavaScript ecosystem when writing your Workers.
Our newest version of Node.js compatibility combines the best features of our previous efforts. Cloudflare Workers have supported Node.js in some form for quite a while. We first announced polyfill support in 2021, and later built-in support for parts of the Node.js API that has expanded over time.
The latest changes make it even better:
You can use far more NPM packages on Workers.
You can use packages that do not use the
node: prefix to import Node.js APIsYou can use more Node.js APIs on Workers, including most methods on
async_hooks,buffer,dns,os, andevents. Many more, such asfsorprocessare importable with mocked methods.
To give it a try, add the following flag to wrangler.toml, and deploy your Worker with Wrangler:
compatibility_flags = ["nodejs_compat_v2"]
Packages that could not be imported with nodejs_compat, even as a dependency of another package, will now load. This Continue reading
Looking for 240/4 Addresses
In the IANA IPv4 Address registry a block of addresses, 240.0.0.0/4 is marked as reserved for "Future Use"". If we have run out of available IPv4 addresses, then why are some quarter of a billion IPv4 addresses still sitting idle in an IANA registry waiting for an undefined Future Use?NB494: AT&T Sues Broadcom over VMware Support; Verizon Spends $20 Billion for Frontier
Take a Network Break! This week we cover an AT&T lawsuit against Broadcom over changes to a support contract for VMware software, why Verizon is spending $20 billion to buy Frontier, and new critical security patches from Cisco. ASML, which makes the machines that make high-end computer chips, gets antsy over US restrictions to China.... Read more »Public Videos: Network Connectivity and Graph Theory

In May 2024, I made public the first half of the Network Connectivity and Graph Theory videos by Rachel Traylor.
Now, you can also enjoy the second part of the webinar without a valid ipSpace.net account; it describes trees, spanning trees, and the Spanning Tree Protocol. Enjoy!
Optimizing OSPF RFC Access with Serper API and Large Language Models
Disclaimer: All Writings And Opinions Are My Own And Are Interpreted Solely From My Understanding. Please Contact The Concerned Support Teams For A Professional Opinion, As Technology And Features Change Rapidly.
This series of blog posts will focus on one feature at a time to simplify understanding.
At this point, ChatGPT—or any Large Language Model (LLM)—needs no introduction. I’ve been exploring GPTs with relative success, and I’ve found that API interaction makes them even more effective.
But how can we turn this into a workflow, even a simple one? What are our use cases and advantages? For simplicity, we’ll use the OpenAI API rather than open-source, self-hosted LLMs like Meta’s Llama.
Let’s consider an example: searching for all OSPF-related RFCs on the web. Technically, we’ll use a popular search engine, but to do this programmatically, I’ll use Serper. You can find more details at https://serper.dev. Serper is a powerful search API that allows developers to programmatically access search engine results. It provides a simple interface to retrieve structured data from search queries, making it easier to integrate search functionality into applications and workflows.
Let’s build the first building block and try to fetch results using Serper. When you sign Continue reading
Network CI/CD – Configuration Management with Napalm and Nornir

Hi all, welcome back to part 4 of the Network CI/CD blog series. So far, we've covered the purpose of a Network CI/CD pipeline, the problems it solves for Network Engineers, and how to set up GitLab, including creating projects, installing runners, and understanding GitLab executors. We also looked at how to use GitLab variables to securely hide secrets.
In this part, we'll explore how to manage a campus network using Nornir and Napalm and deploy configurations through a CI/CD pipeline. Let's get to it!

As I mentioned previously, I'm not a CI/CD expert at all and I'm still learning. The reason for creating this series is to share what I learn with the community. The pipeline we are building is far from perfect, but that's okay. The goal here is to create a simple pipeline that works and then build upon it as we go. This way, you can start small and gradually Continue reading
HN748: How AI and HPC Are Changing Data Center Networks
On today’s episode of Heavy Networking, Rob Sherwood joins us to discuss the impact that High Performance Computing (HPC)and artificial intelligence computing are having on data center network design. It’s not just a story about leaf/spine architecture. That’s the boring part. There’s also power and cooling issues, massive bandwidth requirements, and changes in how we... Read more »TNO002: How Simplification Helps MSPs Scale
Simplification is the theme of today’s episode. Host Scott Robohn and guest Jack Maxfield explore the operational impacts of simplification for a Managed Service Provider (MSP). They discuss the challenges of managing multi-vendor environments and how to use templating and tools to simplify the management process. Proactive client communication and the integration of network and... Read more »Repost: BGP, EVPN, VXLAN, or SRv6?
Did you know that some vendors use the ancient MPLS/VPN (RFC 4364) control plane when implementing L3VPN with SRv6?
That’s just one of the unexpected tidbits I discovered when explaining why you can’t compare BGP, EVPN, and SRv6.
Network CI/CD Pipeline – GitLab Variables

Hi all, welcome back to our Network CI/CD blog series. In the previous posts, we covered what CI/CD is and why you need it for Network Automation. We also covered GitLab basics and how to set up your first pipeline. In this post, we’ll look into how to keep your credentials secure by hiding them from the repository and using GitLab variables. Let’s get to it!
GitLab Variables
In GitLab CI/CD, variables play an important role in managing dynamic values throughout your pipeline. These variables can store anything from environment-specific settings to sensitive information like credentials. By using variables, you can easily manage and change values without hardcoding them in your scripts or playbooks.
GitLab provides a secure way to store sensitive data such as passwords or API tokens. You can define these variables in your project’s Settings > CI/CD > Variables section, and they will be securely injected into your pipeline during runtime.
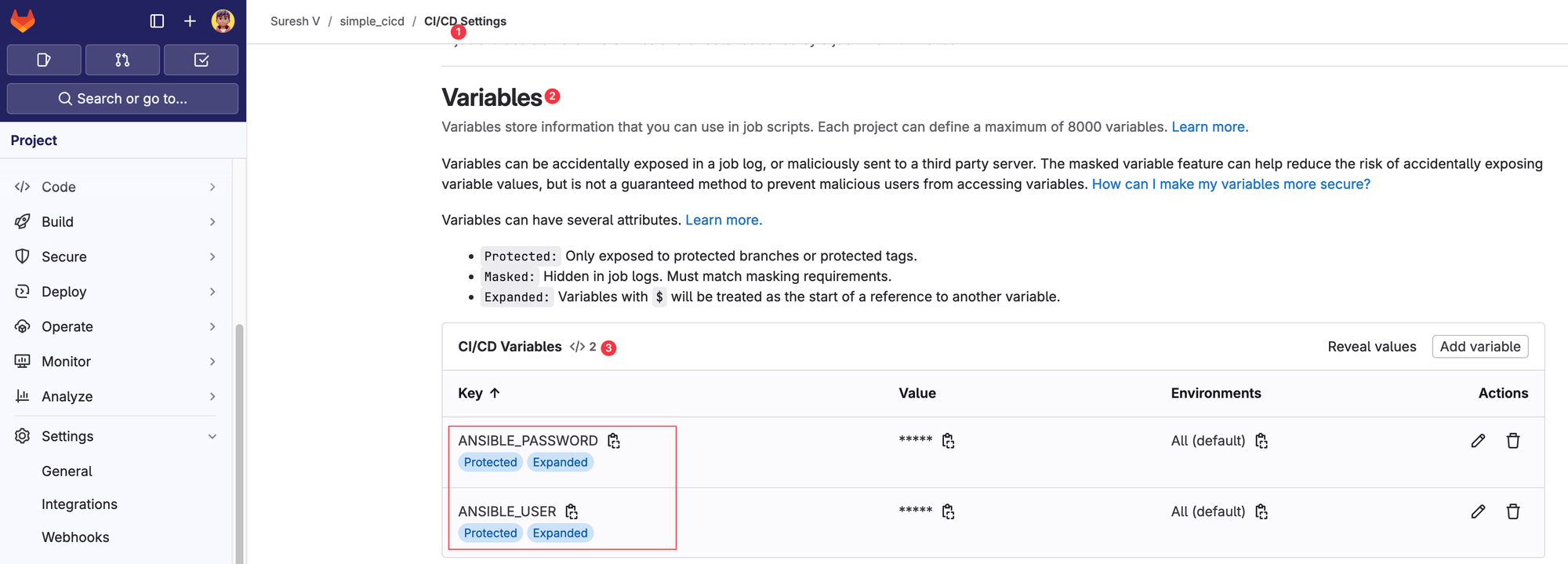
If you recall, in our previous examples, we had the username and password hardcoded in the Ansible variables file. This is not secure at all, and you should never expose sensitive information like credentials directly in your repository. By using GitLab variables, you can securely Continue reading
Hedge 242: The Myth of the Coder
In the early days of computer programming, some thought there was a difference between a coder and a programmer. Did this division ever really exist, and are there similar divisions in network engineering?
Free Network Configuration Backup with Netpicker

Netpicker is a tool that brings together config backups, security/compliance checks, and automation in one place. Netpicker supports 130+ network vendors, including Cisco, Juniper, Arista, Palo Alto, and Fortinet. It also integrates well with tools like Netbox, Nautobot, and Infrahub for inventory, and Slurp’it for network discovery. You can also reuse your existing Python scripts to run checks or automate tasks across your network.
In this post, we'll go through how to set up Netpicker and configure device backups for free. We'll also look at how Netpicker stores these backups and how you can compare or view the diff to see what has changed over time.
Please note that this is a paid article. Netpicker has asked me to write and publish this blog post on their behalf, and I’ve charged a fee for it. As of writing this, Netpicker also sponsors my blog.
Netpicker Initial Setup
To get started, head over to the Netpicker website and fill out the form with your name and email. You’ll receive an email shortly with the download instructions. Netpicker comes with a free-for-life license that gives you unlimited device backups and basic automation. You’ll also get a ‘Professional’ license Continue reading
IPB159: IPv6 Basics – Router Advertisements
Our series on IPv6 basics continues with Router Advertisements (RAs) within the Neighbor Discovery Protocol. We look at how hosts bootstrap onto a network using ICMPv6, discuss the timing of sending out an RA, and then cover the configuration of RAs, including key flags and options. We also talk about the importance of understanding the... Read more »Wireshark tid-bit: Looking for the smoking gun
It’s not always the network which is at fault but it is usually the network that is the assumed culprit. Wireshark can be a vital tool when troubleshooting difficult scenarios or prove that the network is not root cause. The purpose of this post is to ask questions and promote out of the box thinking […]EVPN Designs: Scaling IBGP with Route Reflectors
In the previous blog posts, we explored the simplest possible IBGP-based EVPN design and tried to figure out whether BGP route reflectors do more harm than good. Ignoring that tiny detail for the moment, let’s see how we could add route reflectors to our leaf-and-spine fabric.
As before, this is the fabric we’re working with:
Bringing insights into TCP resets and timeouts to Cloudflare Radar
Cloudflare handles over 60 million HTTP requests per second globally, with approximately 70% received over TCP connections (the remaining are QUIC/UDP). Ideally, every new TCP connection to Cloudflare would carry at least one request that results in a successful data exchange, but that is far from the truth. In reality, we find that, globally, approximately 20% of new TCP connections to Cloudflare’s servers time out or are closed with a TCP “abort” message either before any request can be completed or immediately after an initial request.
This post explores those connections that, for various reasons, appear to our servers to have been halted unexpectedly before any useful data exchange occurs. Our work reveals that while connections are normally ended by clients, they can also be closed due to third-party interference. Today we’re excited to launch a new dashboard and API endpoint on Cloudflare Radar that shows a near real-time view of TCP connections to Cloudflare’s network that terminate within the first 10 ingress packets due to resets or timeouts, which we’ll refer to as anomalous TCP connections in this post. Analyzing this anomalous behavior provides insights into scanning, connection tampering, DoS attacks, connectivity issues, and other behaviors.

