How inspiration from your data center can modernize your campus network.
Campus networks are undergoing a rapid evolution as they draw inspiration from their data center peers from both a technology and cost perspective. At the forefront of this evolution is open networking, led by innovation and cost efficiencies that apply equally across data center and campus networks.
Interestingly, Cumulus Linux was originally intended for data center networking, but without a doubt, we’re seeing the lines between data center and campus blurring with campus standing to benefit significantly, and it’s about time. It’s the data center that has historically benefited from innovation, especially in compute and storage. The data center network, however, seemed to lag for more than a decade until our founders set out in 2010 to develop a fundamentally different approach to the data center with Cumulus Networks.
Cumulus Networks introduced an open, modern and innovative network operating system called Cumulus Linux. Cumulus Linux was originally designed to emulate the network architecture of the web-scale giants including Google, Amazon, Apple, Microsoft and Facebook allowing you to automate, customize and scale your data center network like no other, and for the first time, bringing this capability to the masses.
Cumulus Networks is building the modern data center network for applications Continue reading
How Did We End with 1500-byte MTU?
A subscriber sent me this intriguing question:
Is it not theoretically possible for Ethernet frames to be 64k long if ASIC vendors simply bothered or decided to design/make chipsets that supported it? How did we end up in the 1.5k neighborhood? In whose best interest did this happen?
Remember that Ethernet started as a shared-cable 10 Mbps technology. Transmitting a 64k frame on that technology would take approximately 50 msec (or as long as getting from East Coast to West Coast). Also, Ethernet had no tight media access control like Token Ring, so it would be possible for a single host to transmit multiple frames without anyone else getting airtime, resulting in unacceptable delays.
Read more ...Kubernetes, Ransomware to Hit Cloud and Data in 2020
Ransomware attacks shot up 500% in the last year with damage costs expected to soar up to $11...
Tech Bytes: Implementing Sensible Network Segmentation With Tufin (Sponsored)
Today's Tech Bytes podcast looks at how to implement sensible network segmentation to ensure compliance with security policies and accelerate business agility. Tufin is our sponsor, and we speak with guest Sagi Bar-Zvi, Strategic Pre-Sales Manager at Tufin.
The post Tech Bytes: Implementing Sensible Network Segmentation With Tufin (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Implementing Sensible Network Segmentation With Tufin (Sponsored)
Today's Tech Bytes podcast looks at how to implement sensible network segmentation to ensure compliance with security policies and accelerate business agility. Tufin is our sponsor, and we speak with guest Sagi Bar-Zvi, Strategic Pre-Sales Manager at Tufin.Heavy Networking 478: Leveraging LTE For SD-WAN With Cradlepoint (Sponsored)
Today's Heavy Networking show is sponsored by Cradlepoint, which provides wireless WAN networking. Our guest Marc Bresniker, VP of Product Management, joins us to discuss using LTE for WAN connections including IoT, and to explore the benefits of using Cradlepoint's LTE solutions as part of your SD-WAN strategy.
The post Heavy Networking 478: Leveraging LTE For SD-WAN With Cradlepoint (Sponsored) appeared first on Packet Pushers.
Network Break 256: Startup Forward Networks Nabs $35 Million; Vodafone Dials OpenRAN For Incumbent Alternatives
Today's Network Break podcast is chock full of inspirational cynicism. We cover fresh funding for Forward Networks, Vodafone trialing OpenRAN gear, SUSE closing the door on OpenStack, Extreme Networks shifting StackStorm to the Linux Foundation, and more tech news.
The post Network Break 256: Startup Forward Networks Nabs $35 Million; Vodafone Dials OpenRAN For Incumbent Alternatives appeared first on Packet Pushers.
Network Break 256: Startup Forward Networks Nabs $35 Million; Vodafone Dials OpenRAN For Incumbent Alternatives
Today's Network Break podcast is chock full of inspirational cynicism. We cover fresh funding for Forward Networks, Vodafone trialing OpenRAN gear, SUSE closing the door on OpenStack, Extreme Networks shifting StackStorm to the Linux Foundation, and more tech news.Forcepoint Web Security Footprint Spans 160 Global PoPs
The vendor rolled out its Web Security platform across 160 points of presence as it builds out a...
Toshiba Taps Cybera’s SD-WAN for Retail Terminals
Under the agreement, Cybera becomes Toshiba's preferred SD-WAN vendor in the Asia-Pacific...
Intel Snaps Up Smart Edge Amid 5G Push
The company is expanding into edge computing, which it estimates will be a $65 billion silicon...
Lenovo’s Charles Ferland Shares What’s in Store for SDN, NFV, and Telecoms
Hear from Lenovo's Charles Ferland as he dives into the company's latest ideas in telecom...
Overcoming the Barriers to Micro-segmentation
It should come as no surprise how much emphasis organizations place on security today. Threats are becoming more and more sophisticated and the number of threats grow to uncontrollable rates every day.
One of the biggest downsides is that the rising cost of data breaches in 2019 alone, a global average of $3.92 million as reported by the Ponemon Institute and IBM Security July 2019 report, is enough to cause organizations to rethink or increase emphasis on their security strategies and how they can help secure their most important assets by improving the cyber hygiene in their organizations.
What is Cyber Hygiene?
Cyber hygiene refers to what an organization can do to improve their security postures around physical hardware, software, and applications. If you’ve seen Pat Gelsinger’s keynote from 2017, he goes into the 5 pillars of good cyber hygiene and what organizations can do to improve basic and fundamental security for their business.
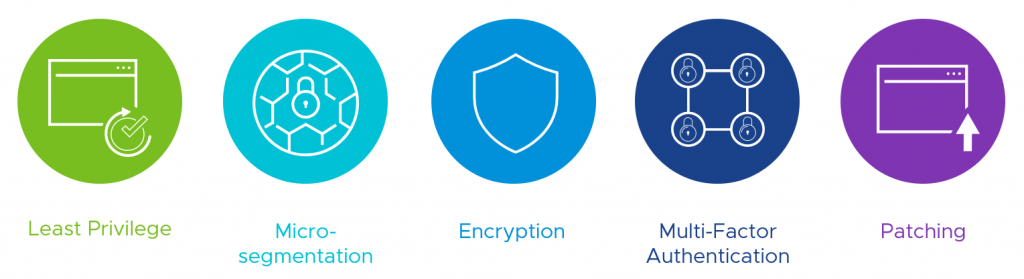
Over the last several years, VMware has been focusing on helping organizations move to Software-Defined Data Centers (SDDC) to improve their agility and meet the speed of business. As more organizations adopted the SDDC model, VMware found itself in a unique position Continue reading