0
Futzing and moseying: interviews with professional data analysts on exploration practices Alspaugh et al., VAST’18
What do people actually do when they do ‘exploratory data analysis’ (EDA)? This 2018 paper reports on the findings from interviews with 30 professional data analysts to see what they get up to in practice. The only caveat to the results is that the interviews were conducted in 2015, and this is a fast-moving space. The essence of what and why is probably still the same, but the tools involved have evolved.
What is EDA?
Exploration here is defined as “open-ended information analysis,” which doesn’t require a precisely stated goal. It comes after data ingestion, wrangling and profiling (i.e., when you have the data in a good enough state to ask question of it). The authors place it within the overall analysis process like this:
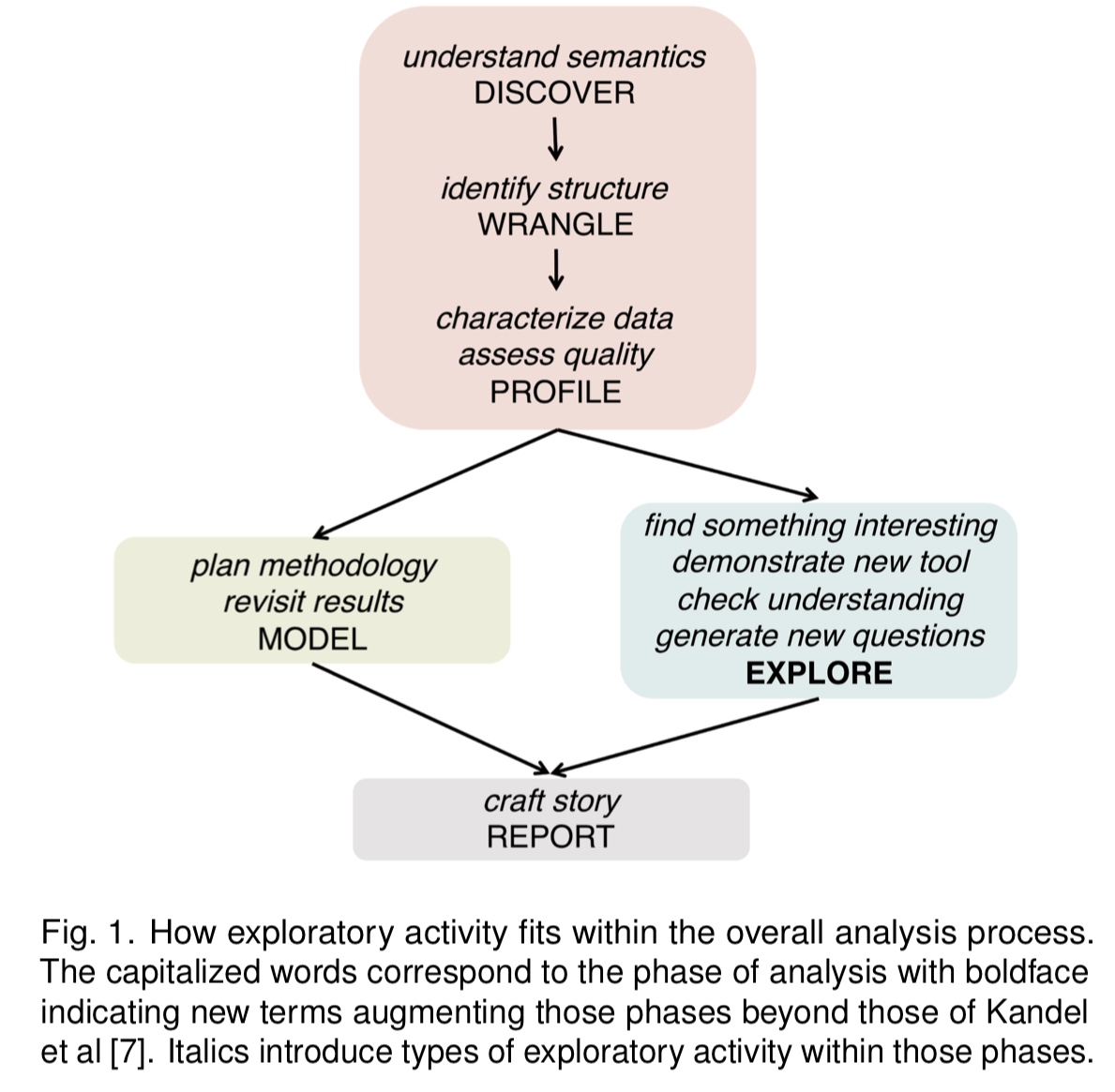
That looks a lot more waterfall-like than my experience of reality though. I’d expect to see lots of iterations between explore and model, and possibly report as well.
The guidance given to survey participants when asking about EDA is as follows:
EDA is an approach to analyzing data, usually undertaken at the beginning of an analysis, to Continue reading


