Thoma Bravo Scoops Up Sophos for $3.9 Billion
The buyout firm spent nearly $3 billion purchasing other security vendors in 2018 including...
The buyout firm spent nearly $3 billion purchasing other security vendors in 2018 including...

Kubernetes is a powerful container orchestrator and has been establishing itself as IT architects’ container orchestrator of choice. But Kubernetes’ power comes at a price; jumping into the cockpit of a state-of-the-art jet puts a lot of power under you, but knowing how to actually fly it is not so simple. That complexity can overwhelm a lot of people approaching the system for the first time.
I wrote a blog series recently where I walk you through the basics of architecting an application for Kubernetes, with a tactical focus on the actual Kubernetes objects you’re going to need. The posts go into quite a bit of detail, so I’ve provided an abbreviated version here, with links to the original posts.
With a machine as powerful as Kubernetes, I like to identify the absolute minimum set of things we’ll need to understand in order to be successful; there’ll be time to learn about all the other bells and whistles another day, after we master the core ideas. No matter where your application runs, in Kubernetes or anywhere else, there are four concerns we are going to have to address:

remove the MacOS Catalina whining and nagging
The post Remove the macOS Catalina guilt trip from macOS Mojave | The Robservatory appeared first on EtherealMind.

Content crackdown: China and Russia plan to sign an agreement to crack down on what they consider “illegal” Internet content, The Register reports. It’s unclear what the agreement will cover but critics already fear the deal will enable the two countries to further crack down on free speech. China has even effectively banned cartoon character Winnie the Pooh because some people have compared the chubby bear to leader Xi Jinping.
Eyes on you: In more censorship-related news, Thailand has ordered restaurants and Internet cafes to log the Internet histories of users, Privacy News Online says. The Thai government already requires ISPs to keep a log of customers’ Internet histories for 90 days as part of the country’s Computer Crimes Act.
Poor access: Some of the U.S. states with the lowest levels of broadband access also have the highest poverty rates, notes a report from Axios. About 30 percent of low-income U.S. residents do not have access to broadband, says the story, citing a Census Bureau report.
Not so smart: A new “smart” doorbell may literally unlock a home’s doors to hackers, according to The Daily Swig. A security researcher found that the Wi-Fi connected doorbell had no authentication Continue reading

The upcoming Red Hat Ansible Engine 2.9 release has some really exciting improvements, and the following blog highlights just a few of the notable additions. In typical Ansible fashion, development of Ansible Network enhancements are done in the open with the help of the community. You can follow along by watching the GitHub project board, as well as the roadmap for the Red Hat Ansible Engine 2.9 release via the Ansible Network wiki page.
As was recently announced, Red Hat Ansible Automation Platform now includes Ansible Tower, Ansible Engine, and all Ansible Network content. To date, many of the most popular network platforms are enabled via Ansible Modules. Here are just a few:
A full list of the platforms that are fully supported by Red Hat via an Ansible Automation subscription can be found at the following location: https://docs.ansible.com/ansible/2.9/modules/network_maintained.html#network-supported
In the last four years we’ve learned a lot about developing a platform for network automation. We’ve also learned a lot about how users apply these platform artifacts as consumed in end-user Ansible Playbooks and Roles. In the Continue reading
Policy-based VPNs are a pain most of the time, especially when compared to route-based VPNs. Many of the policy-based VPNs …
The post Junos Policy-Based VPNs – Part 1 of 4 – Security Policies appeared first on Fryguy's Blog.
Hello my friend,
This is the third article where we use the Mellanox SN 2010 running Cumulus Linux. And today we cover enormously important topic: network security. More precisely, we will speak about the data plane and the control plane protection. Cisco IOS XR and Nokia SR OS accompany us in this journey.
Special thanks for Avi Alkobi from Mellanox and Pete Crocker and Attilla de Groot from Cumulus Networks for providing me the Mellanox switch and Cumulus license for the tests.
This blogpost is the continuation of the previous one, where we have brought the Mellanox SN 2010 to the operational with Cumulus Linux 3.7.9 on board. If you want to learn the details about this process, you are welcomed to read that article.
Each week you can find the news describing the security breaches. In the modern economy, where the Internet plays already a key role, all the connected businesses (and almost all businesses are connected) are on the risk caused by casual network scanning and brood force attacks. In addition to that, big companies and governments are quite often the attack targets for other companies, governments and criminals. Therefore, Continue reading
Dinesh Dutt added another awesome chapter to the EVPN saga last week explaining how (and why) you could run VXLAN encapsulation with EVPN control plane on Linux hosts (TL&DR: think twice before doing it).
In the last part of current Azure Networking series I covered external VNet connectivity, including VNet peering, Internet access, Virtual Network Gateways, VPN connections, and ExpressRoute. The story continues on February 6th 2020 with Azure automation.
You’ll need Standard ipSpace.net Subscription to access both webinars.
“In a sense, Docker is almost a victim of its own success,” said 451 Research's Jay Lyman....
I often get asked about EVPN Layer 3 gateway options. And more specifically, what are the differences between IRB with Virtual Gateway Address (VGA) and IRB without VGA. There are many different options and configuration knobs available when configuring EVPN L3 gateway. But I’ve focused on the 3 most popular options that I see with my customers in EVPN-VXLAN environments in a centralised model. I’m also only providing the very basic configuration required.
Each IRB option can be considered an Anycast gateway solution seeing as duplicate IPs are used across all IRB gateways. However, there are some subtle, yet significant, differences between each option.
Regardless of the transport technology used, whether it be MPLS or VXLAN, a layer 3 gateway is required to route beyond a given segment.
This Week: Data Center Deployment with EVPN/VXLAN by Deepti Chandra provides in-depth analysis and examples of EVPN gateway scenarios. I highly recommend reading this book!
Duplicate IP | Unique MAC | No VGA
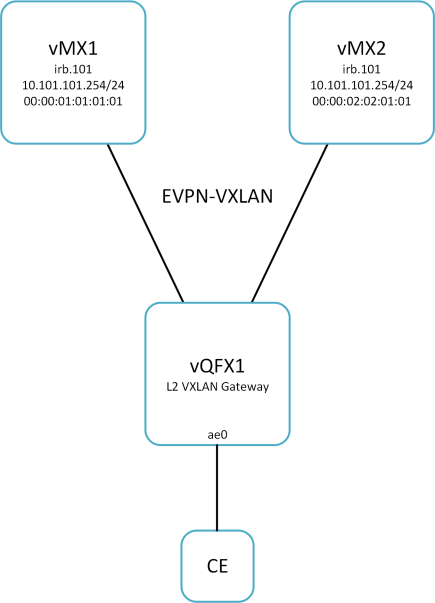
Duplicate IPs are configured on all gateway IRBs and unique MAC addresses are used (manually configured or IRB default). Virtual Gateway Address is not used.
EVPN provides the capability to automatically synchronise gateways Continue reading
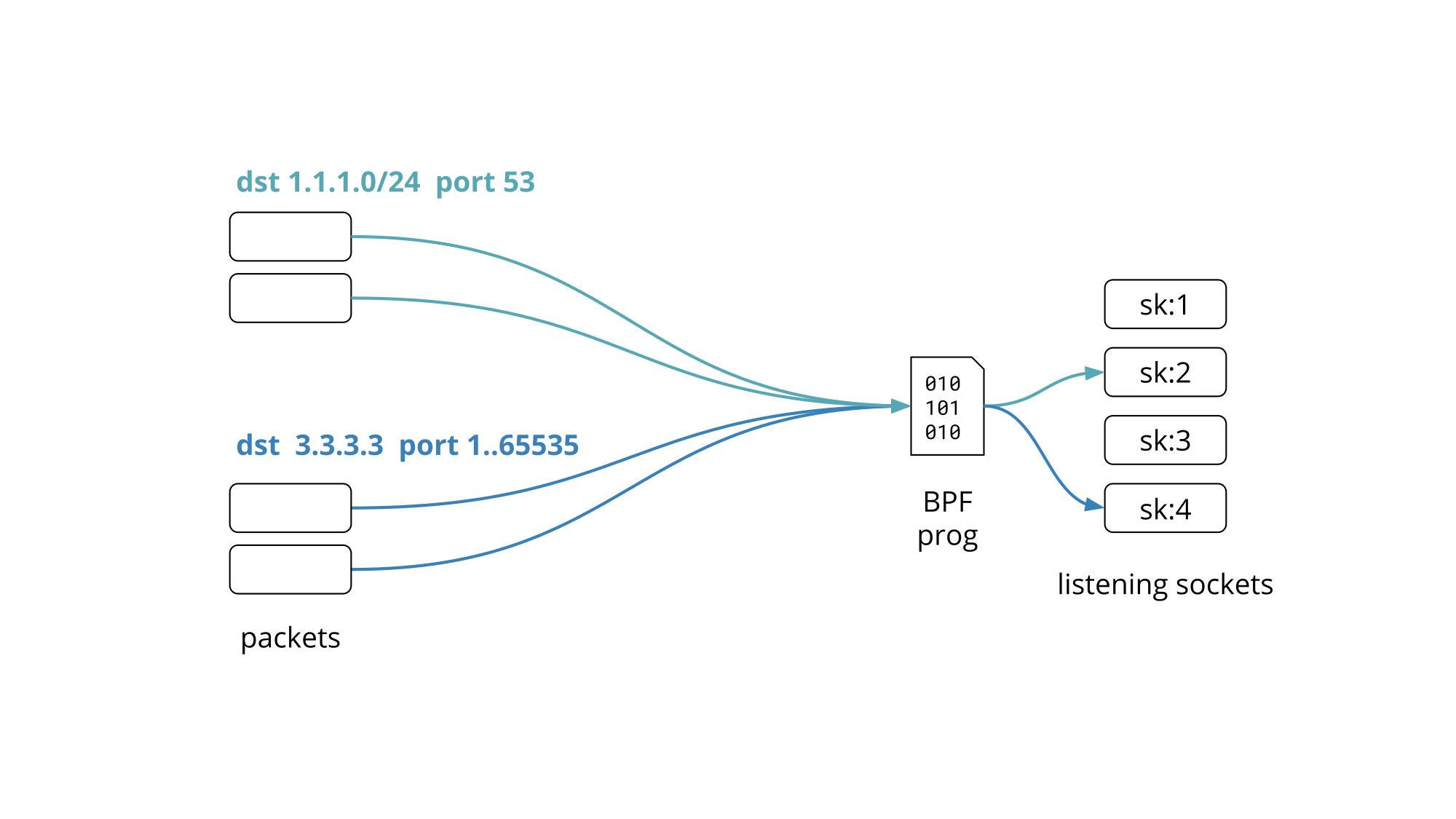
We recently gave a presentation on Programming socket lookup with BPF at the Linux Plumbers Conference 2019 in Lisbon, Portugal. This blog post is a recap of the problem statement and proposed solution we presented.
Our edge servers are crowded. We run more than a dozen public facing services, leaving aside the all internal ones that do the work behind the scenes.
Quick Quiz #1: How many can you name? We blogged about them! Jump to answer.
These services are exposed on more than a million Anycast public IPv4 addresses partitioned into 100+ network prefixes.
To keep things uniform every Cloudflare edge server runs all services and responds to every Anycast address. This allows us to make efficient use of the hardware by load-balancing traffic between all machines. We have shared the details of Cloudflare edge architecture on the blog before.
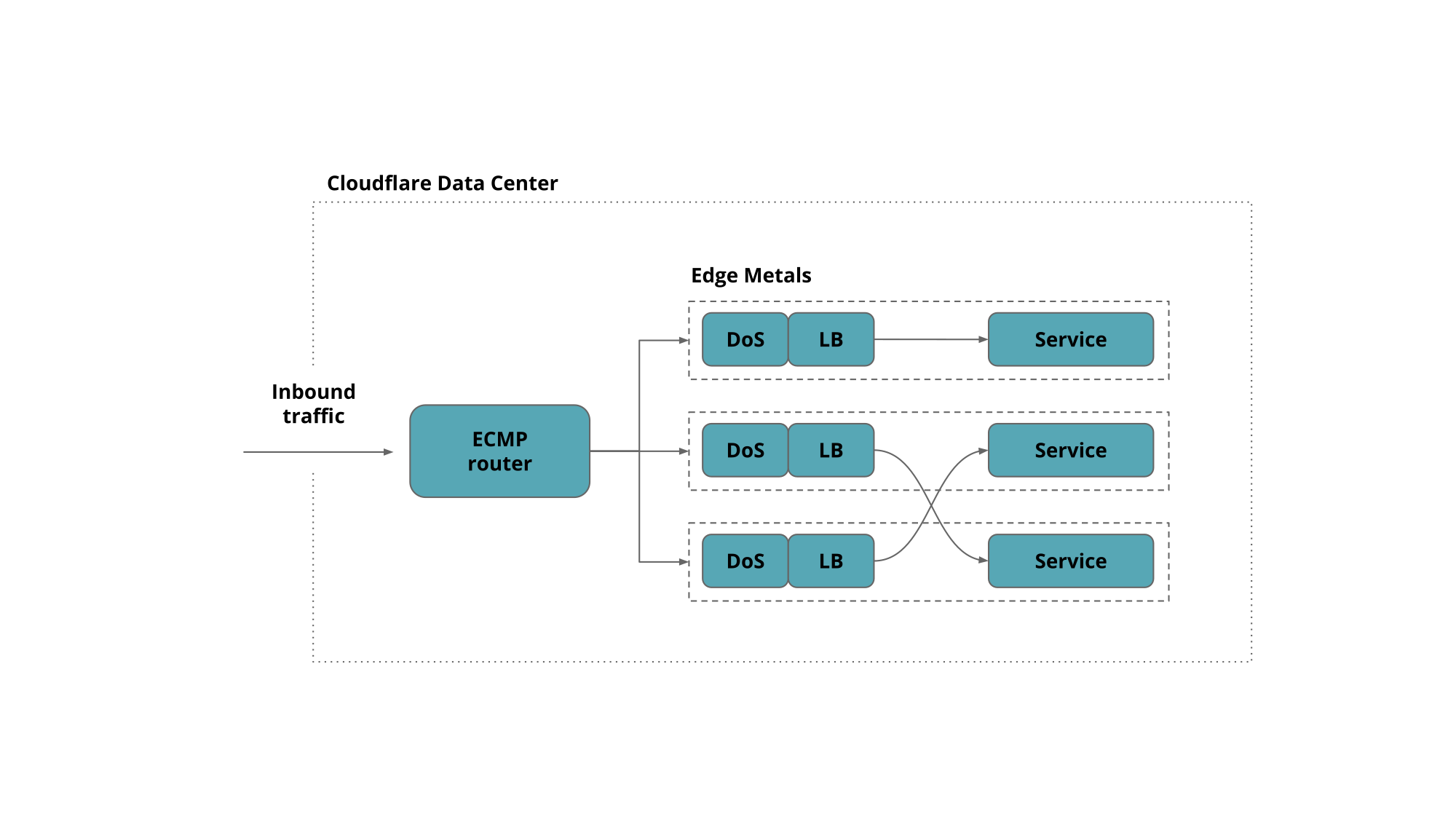
Granted not all services work on all the addresses but rather on a subset of them, covering one or several network prefixes.
So how do you set up your network services to listen on hundreds of IP addresses without driving the network stack over the edge?
Cloudflare engineers have had to ask themselves this question Continue reading
cURL. The wonderful HTTP plumbing tool that powers both a lot of command line debugging and bash scripts, but also exists as a strong foundation in our applications in the form of libcurl.
This is the quick and easy way I learned to edit some files within a Docker container. Professional DevOps engineers might be doing it in a different way, this is the network engineers way of doing things 
-Rakesh
Gregor Hohpe published an excellent series on Martin Fowler’s web site focusing on various aspects of lock-in. If nothing else, you SHOULD read the shades of lock-in part, and combine it with my thoughts on lock-in in data center networking.

Today is the 31st Anniversary of National Coming Out Day. I wanted to highlight the importance of this day, share coming out resources, and publish some stories of what it's like to come out in the workplace.
Thirty-one years ago, on the anniversary of the National March on Washington for Lesbian and Gay Rights, we first observed National Coming Out Day as a reminder that one of our most basic tools is the power of coming out. One out of every two Americans has someone close to them who is gay or lesbian. For transgender people, that number is only one in 10.
Coming out - whether it is as lesbian, gay, bisexual, transgender or queer - STILL MATTERS. When people know someone who is LGBTQ, they are far more likely to support equality under the law. Beyond that, our stories can be powerful to each other.
Each year on October 11th, National Coming Out Day continues to promote a safe world for LGBTQ individuals to live truthfully and openly. Every person who speaks up changes more hearts and minds, and creates new advocates for equality.
For more on coming out, visit HRC's Coming Out Continue reading