Cybera Injects Cloud Management Into Its SD-WAN Platform
 Cybera’s multi-tenant platform is built on an architecture that provides SD-WAN, cloud-based...
Cybera’s multi-tenant platform is built on an architecture that provides SD-WAN, cloud-based...
 Cybera’s multi-tenant platform is built on an architecture that provides SD-WAN, cloud-based...
Cybera’s multi-tenant platform is built on an architecture that provides SD-WAN, cloud-based...
IRB Routing over EVPN-VXLAN on Juniper QFX10K is now officially supported by Juniper! EVPN master Tom Dwyer informed me that support had been added. A quick check on the VXLAN Constraints page confirms the same. Although, note that IS-IS is still not yet officially supported.
So, what’s the use case? Let’s say there’s a vSRX, hosted in a blade chassis environment, which requires dynamic route updates from the core network. The blade chassis is connected to an EVPN-VXLAN fabric via multi-homed layer 2 uplinks utilising EVPN ESI. In order to establish a BGP peering with the core network, the vSRX must peer with the SPINE devices via the EVPN-VXLAN fabric.
This article explains how to establish an EBGP peering between a QFX10K IRB interface and a vSRX in an EVPN-VXLAN environment. The vSRX is hosted in an ESXi hypervisor, which is connected via LEAF1 and LEAF2. A /29 network is used on VNI300 and an EBGP peering is established between SPINE1 & vSRX1 and between SPINE2 & vSRX1. A default route is advertised by both QFX10K SPINEs towards vSRX1.
SPINE – QFX10K – 17.3R3
LEAF – QFX5110 – 17.3R3
vSRX – 15. Continue reading
Tom Limoncelly wrote another must-read ACM Queue article: Top Ten Things Executives Should Know About Software. If only someone as eloquent as Tom would write a networking equivalent...
If you missed DockerCon in San Francisco this year or were unable to watch the livestream, no need to worry – we have you covered. You can catch all the demos, get the latest announcements and find out what is next for the Docker ecosystem by watching the replay sessions on demand.
On Tuesday, we kicked off the first day of DockerCon with product announcements, demos and customer guest speakers. During the session, we presented Docker Enterprise 3.0, the only desktop-to-cloud enterprise container platform enabling organizations to build and share any application and securely run them anywhere – from hybrid cloud to the edge. Additionally, we announced this year’s winners of the Customer Innovation awards, featuring Carnival, Citizens Bank, Liberty Mutual, Lindsay Corporation and Nationwide.
On-stage, the Docker team also demonstrated Docker Applications, Docker Kubernetes Service (DKS) and new features and capabilities in Docker Desktop Enterprise – all designed to accelerate the application development and deployment pipeline. They keynote closed with a demonstration from R.O.S.I.E, the robot built by two Liberty Mutual engineers using Docker.
To learn first hand everything featured Continue reading
Today's Heavy Networking is a roundtable show where we talk with engineers about the challenges of building a networking career when you don't live in a big city. We talk about how to find jobs, get training, advance your skills, and build community. Our guests are Phil Gervasi, Ryan Booth, and Eric Stover.
The post Heavy Networking 447: Building A Networking Career Outside The Big City appeared first on Packet Pushers.
Recently I took the JNCIE-SEC lab (that will be another post) and wanted to cover one of the study points …
The post Junos IPv6 to IPv4 NAT appeared first on Fryguy's Blog.
 Delegates from 32 countries this week gathered at a conference in Prague to address security...
Delegates from 32 countries this week gathered at a conference in Prague to address security...
 Juniper’s Julius Francis discusses how open source must evolve and consider security,...
Juniper’s Julius Francis discusses how open source must evolve and consider security,...
 The company has simplified its service offerings in an attempt to lower cost and attract more...
The company has simplified its service offerings in an attempt to lower cost and attract more...
 SDxCentral Weekly Wrap for May 3, 2019: Dell EMC and Big Switch team up; Orange taps Dell for 5G...
SDxCentral Weekly Wrap for May 3, 2019: Dell EMC and Big Switch team up; Orange taps Dell for 5G...
 A year after HPE CEO Antonio Neri said “Dell doesn’t have an edge-to-cloud approach,” Dell...
A year after HPE CEO Antonio Neri said “Dell doesn’t have an edge-to-cloud approach,” Dell...

You’ve probably heard by now of the big launch of Cisco’s new 802.11ax (neé Wi-Fi 6) portfolio of devices. Cisco did a special roundtable with a group of influencers from the community called Just The Tech. Here’s a video from that event covering the APs that were released, the 9120:
Fred always does a great job of explaining the technical bits behind the APs. But one thing that caught my eye here is the name of the AP – Catalyst. Cisco has been using Aironet for their AP line since they purchased Aironet Wireless Communications back in 1999. The name was practically synonymous with wireless technologies for many people in the industry that worked exclusively with Cisco technologies.
So, is the name change something we should be concerned about?
Cisco moving toward a unified naming convention for their edge solutions makes a lot of sense. Ten years ago, wireless was still primarily 802.11g-based with 802.11n still a few months away from being proposed and ratified. Connectivity hadn’t quite yet reached the ubiquitous levels of wireless that we see today. The iPhone was only about to be on its third Continue reading
Wake up! It's HighScalability time:
Do you like this sort of Stuff? I'd greatly appreciate your support on Patreon. I wrote Explain the Cloud Like I'm 10 for people who need to understand the cloud. And who doesn't these days? On Amazon it has 45 mostly 5 star reviews (105 on Goodreads). They'll learn a lot and hold you in awe.
 VPN flaw uncovered in Cisco, F5, and more; Google Anthos soars to the clouds; and AT&T avoids...
VPN flaw uncovered in Cisco, F5, and more; Google Anthos soars to the clouds; and AT&T avoids...
 Vodafone Spain is to work with Huawei on a pilot in Andalusia, while Telefónica teams up with...
Vodafone Spain is to work with Huawei on a pilot in Andalusia, while Telefónica teams up with...

List of technical features that matter
The post A List Of What Makes WiFi 6 Technically Better ? appeared first on EtherealMind.
It is unlikely we can tell you anything new about the extended Berkeley Packet Filter, eBPF for short, if you've read all the great man pages, docs, guides, and some of our blogs out there.
But we can tell you a war story, and who doesn't like those? This one is about how eBPF lost its ability to count for a while1.
They say in our Austin, Texas office that all good stories start with "y'all ain't gonna believe this… tale." This one though, starts with a post to Linux netdev mailing list from Marek Majkowski after what I heard was a long night:
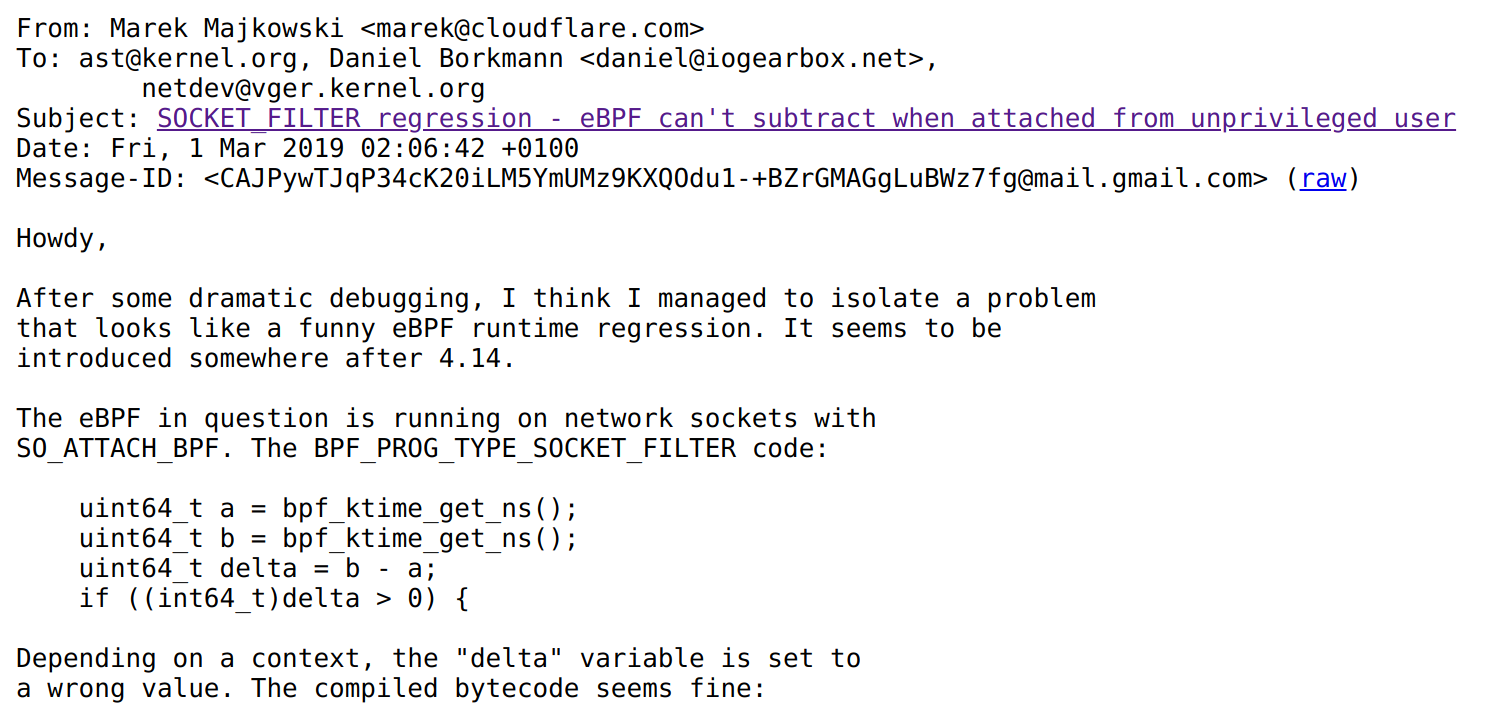
Marek's findings were quite shocking - if you subtract two 64-bit timestamps in eBPF, the result is garbage. But only when running as an unprivileged user. From root all works fine. Huh.
If you've seen Marek's presentation from the Netdev 0x13 conference, you know that we are using BPF socket filters as one of the defenses against simple, volumetric DoS attacks. So potentially getting your packet count wrong could be a Bad Thing™, and affect legitimate traffic.
Let's try to reproduce this bug with Continue reading
Welcome to Technology Short Take #113! I hope the collection of links and articles I’ve gathered for you contains something useful for you. I think I have a pretty balanced collection this time around; there’s a little bit of something for almost everyone. Who says you can’t please everyone all the time?
kube-iptables-tailer, which turns packet drops from iptables into Kubernetes events that can be logged for easier troubleshooting. The GitHub repository for the project is here.