Microsoft Azure Sentinel Moves SIEM to the Cloud
 The vendor claims it’s the first cloud native security information and event management (SIEM)...
The vendor claims it’s the first cloud native security information and event management (SIEM)...
 The vendor claims it’s the first cloud native security information and event management (SIEM)...
The vendor claims it’s the first cloud native security information and event management (SIEM)...
In and industry where technology seems to change overnight sometimes, how should you decide what you should and shouldn’t invest time in? Are there techniques you can use to optimize navigating technology change? In this Short Take, Russ shares his take on how you should analyze new technologies and intelligently approach new tech to not be ahead or behind of the curve.
The post Short Take – Navigating Technology Change appeared first on Network Collective.
Here’s a short car video where I recommend shutting off notifications as a way to increase productivity. Spoiler alert. That’s pretty much the summary of the entire video, so you can save yourself the four minutes. Or…watch it to get the nuance. I’ll be okay either way. I’m not making money on YouTube ads.
Mellanox has become a leading provider of networking hardware, particularly at the high performance end of the market where the company accounts for more than 70 per cent of ports shipped with speeds above 10GbE according to Crehan Research. …
An Introduction to SmartNICs was written by Nicole Hemsoth at .
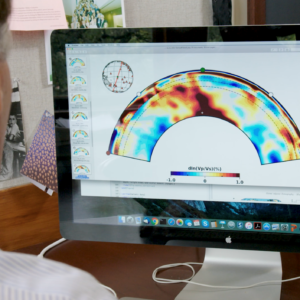 “The goal is to image the earth’s interior on a 3D scale,” says Jeroen Tromp, Blair Professor of Geology at Princeton University, leader of a team carrying out seismic research at the Oak Ridge Oak Ridge National Laboratory (ORNL) in Tennessee. …
“The goal is to image the earth’s interior on a 3D scale,” says Jeroen Tromp, Blair Professor of Geology at Princeton University, leader of a team carrying out seismic research at the Oak Ridge Oak Ridge National Laboratory (ORNL) in Tennessee. …
Summit Supercomputer Clears Path to Seismic Discoveries was written by Nicole Hemsoth at .

Taxing the Internet: A social media tax in Uganda has prompted many users to quit those same sites, The Guardian reports. The tax, intended to raise government revenues and discourage “idle talk,” amounts to 200 Ugandan shillings, or about U.S. 5 cents, per day. More than one million people have quit taxed mobile apps, the story says.
Tough measures: A large majority of Europeans support a proposal to require social media companies to direct all users who have seen take news toward fact-checks, Time.com says. A recent poll suggest that more than 86 percent of European residents surveyed support the Correct the Record proposal from advocacy group Avaaz.
Blockchain goes to pot: Blockchain technology can help marijuana dispensaries enforce daily legal limits on individual purchases, Forbes reports. Blockchain could help dispensaries keep track of attempts at smurfing, the practice of purchasing more than the daily legal limit by going to different dispensaries, and looping, purchasing more than the limit by returning later to the same seller, the story says.
Blockchain vs. censorship: A follow-up to a trend we noted earlier this year: China’s residents are turning to blockchain technologies to fight government censorship, The Conversation reports. Some users Continue reading


Recently we launched Firewall Rules, a new feature that allows you to construct expressions that perform complex matching against HTTP requests and then choose how that traffic is handled. As a Firewall feature you can, of course, block traffic. The expressions we support within Firewall Rules along with powerful control over the order in which they are applied allows complex new behaviour.
In this blog post I tell the story of Cloudflare’s Page Rules mechanism and how Firewall Rules came to be. Along the way I’ll look at the technical choices that led to us building the new matching engine in Rust.
Cloudflare offers two types of firewall for web applications, a managed firewall in the form of a WAF where we write and maintain the rules for you, and a configurable firewall where you write and maintain rules. In this article, we will focus on the configurable firewall.
One of the earliest Cloudflare firewall features was the IP Access Rule. It dates backs to the earliest versions of the Cloudflare Firewall and simply allows you to block traffic from specific IP addresses:
if request IP equals 203.0.113.1 then block Continue readingWe’re starting the Spring 2019 workshop season in March with open-enrollment workshops in Zurich (Switzerland). It was always hard to decide which workshop to do (there are so many interesting topics), so we’ll do two of them in the same week:
Rachel Traylor will continue her Graph Theory webinar on March 7th with a topic most relevant to networking engineers: trees, spanning trees and shortest-path trees, and I’ll continue with two topics I started earlier this year:
Read more ...Efficient large-scale fleet management via multi-agent deep reinforcement learning Lin et al., KDD’18
A couple of weeks ago we looked at a survey paper covering approaches to dynamic, stochastic, vehicle routing problems (DSVRPs). At the end of the write-up I mentioned that I couldn’t help wondering about an end-to-end deep learning based approach to learning policy as an alternative to the hand-crafted algorithms. Lenz Belzner popped up on Twitter to point me at today’s paper choice, which investigates exactly that.
The particular variation of DSVRP studied here is grounded in a ride-sharing platform with real data provided by Didi Chuxing covering four weeks of vehicle locations and trajectories, and customer orders, in the city of Chengdu. With the area covered by 504 hexagonal grid cells, the centres of which are 1.2km apart, we’re looking at around 475 square kilometers. The goal is to reposition vehicles in the fleet at each time step (10 minute intervals) so as to maximise the GMV (total value of all orders) on the platform. We’re not given information on the number of drivers, passengers, and orders in the data set (nor on the actual GMV, all results are relative), but Chengdu has a Continue reading
I use a Privacy Filter on my laptop screen when traveling. I’m doing a bit of time on planes these days, and it makes a big difference. Most of my code is Open Source, but other content is proprietary. High chance of competitors being on the same plane as me, so better to make it harder for others to see.
The only problem with these screens is that if you frequently take it off like I do, the adhesive strips collect dust, and stop sticking after a while. Recently someone asked me how to get them replaced.
3M does not sell replacement strips…but they do something even better: they give them away for free. Pretty cool ah?
Just go here, fill in the details, and they’ll send you some more. How good is that?
I use a Privacy Filter on my laptop screen when traveling. I’m doing a bit of time on planes these days, and it makes a big difference. Most of my code is Open Source, but other content is proprietary. High chance of competitors being on the same plane as me, so better to make it harder for others to see.
The only problem with these screens is that if you frequently take it off like I do, the adhesive strips collect dust, and stop sticking after a while. Recently someone asked me how to get them replaced.
3M does not sell replacement strips…but they do something even better: they give them away for free. Pretty cool ah?
Just go here, fill in the details, and they’ll send you some more. How good is that?
I use a Privacy Filter on my laptop screen when traveling. I’m doing a bit of time on planes these days, and it makes a big difference. Most of my code is Open Source, but other content is proprietary. High chance of competitors being on the same plane as me, so better to make it harder for others to see.
The only problem with these screens is that if you frequently take it off like I do, the adhesive strips collect dust, and stop sticking after a while. Recently someone asked me how to get them replaced.
3M does not sell replacement strips…but they do something even better: they give them away for free. Pretty cool ah?
Just go here, fill in the details, and they’ll send you some more. How good is that?