Sysadmin friendly high speed ethernet switching
Sysadmin friendly high speed ethernet switching
I’ve been on the lookout for a ethernet switch that I don’t hate, the problem with a lot of higher
I’ve been on the lookout for a ethernet switch that I don’t hate, the problem with a lot of higher
This is not the right way to do it, as will become abundantly clear. But it works.
rustup toolchain install nightly
rustup component add rust-src --toolchain nightly
apt install {binutils,gcc}-mips-linux-gnu
cargo new foo
cd foo
This will build for a while, then fail.
cargo +nightly build --release -Zbuild-std --target mips-unknown-linux-gnu
For some reason it’s trying to use cc to link. I tried putting this
in Cargo.toml, but it does nothing:
[target.mips-unknown-linux-gnu]
linker = "mips-linux-gnu-gcc"
But I found a workaround.
/usr/bin/cc to point to the mips gccIt does not work if you do this before the previous step.
PREV="$(readlink -v /usr/bin/cc)"
sudo rm /usr/bin/cc
sudo ln -s /usr/bin/mips-linux-gnu-gcc /usr/bin/cc
Same command again
cargo +nightly build --release -Zbuild-std --target mips-unknown-linux-gnu
It should succeed. Yay.
/usr/bin/ccsudo rm /usr/bin/cc
sudo ln -s "${PREV?}" /usr/bin/cc
cd target/mips-unknown-linux-gnu/release
patchelf --remove-needed ld.so.1 foo
patchelf --set-interpreter /lib/ld-musl-mips-sf.so.1 foo
Probably easiest to rm -fr target, and go back to the step “Build
most of it”.
$ ./foo
Hello, world!
Yay!
We have a long-standing joke that dates from the early 2000s, when the hyperscalers – there were not yet cloud builders as we now know them – started having hundreds of millions of users and millions of servers and storage arrays to run applications for them at the same time there was the beginnings of consolidation among the OEMs who created the servers and storage used by nearly all enterprises, including dot-com startups. …
What Happens When Hyperscalers And Clouds Buy Most Servers And Storage? was written by Timothy Prickett Morgan at The Next Platform.
As a sort of follow-up to my previous post on using the AWS CLI to track the specific Elastic Network Interfaces (ENIs) used by Amazon Elastic Kubernetes Service (EKS) cluster nodes, this post focuses on the EC2 instances themselves. I feel this is less of a “problem” than tracking ENIs, but I wanted to share this information nevertheless. In this post, I’ll show you which AWS CLI command to use to list all the EC2 instances associated with a particular EKS cluster.
If you read the previous post on tracking ENIs used by EKS, you might think that you could use a very similar AWS CLI command (aws ec2 describe-instances instead of aws ec2 describe-network-interfaces) to track the EC2 instances in a cluster—and you’d be mostly correct. Like the ENIs, EKS does add a cluster-specific tag to all EC2 instances in the cluster. However, just to make life interesting, the tag used for EC2 instances is not the same as the tag used for ENIs. (If someone at AWS knows of a technical reason why these tags are different, I’d love to hear it.)
Instead of using the cluster.k8s.amazonaws.com/name tag that is used Continue reading
More than a decade ago, executives at Arm Ltd saw the energy costs in datacenters soaring and sensed an opportunity to extend the low-power architecture of its eponymous systems-on-a-chip that has dominated the mobile phone markets from the get-go and took over the embedded device market from PowerPC into enterprise servers. …
Power Efficiency, Customization Will Drive Arm’s Role In AI was written by Jeffrey Burt at The Next Platform.
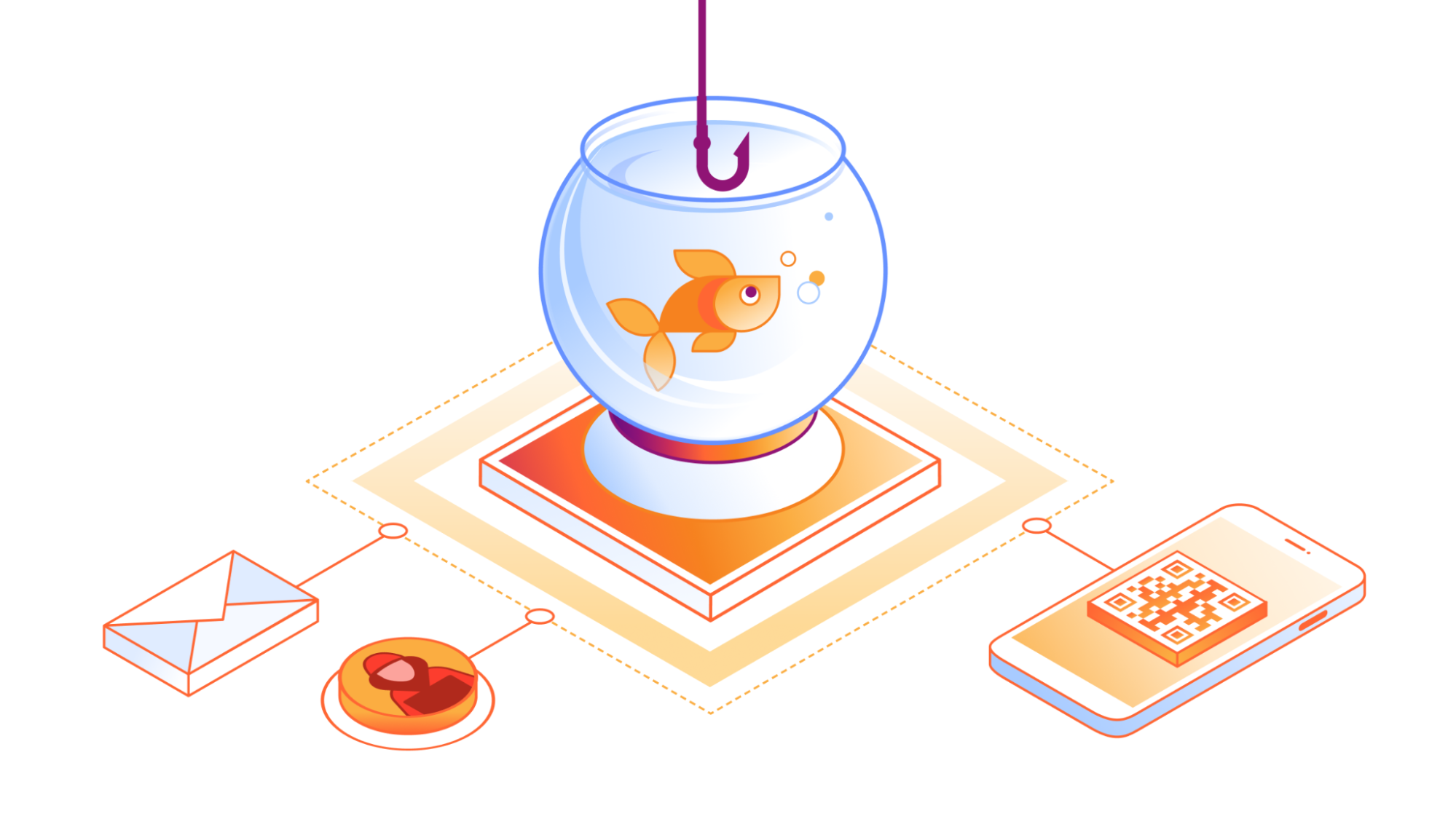
In the ever-evolving landscape of cyber threats, a subtle yet potent form of phishing has emerged — quishing, short for QR phishing. It has been 30 years since the invention of QR codes, yet quishing still poses a significant risk, especially after the era of COVID, when QR codes became the norm to check statuses, register for events, and even order food.
Since 2020, Cloudflare’s cloud email security solution (previously known as Area 1) has been at the forefront of fighting against quishing attacks, taking a proactive stance in dissecting them to better protect our customers. Let’s delve into the mechanisms behind QR phishing, explore why QR codes are a preferred tool for attackers, and review how Cloudflare contributes to the fight against this evolving threat.
The impact of phishing and quishing are quite similar, as both can result in users having their credentials compromised, devices compromised, or even financial loss. They also leverage malicious attachments or websites to provide bad actors the ability to access something they normally wouldn’t be able to. Where they differ is that quishing is typically highly targeted and uses a QR code to further obfuscate itself from detection.
Since Continue reading
TL&DR: FRRouting advertises the IP prefix on the lo loopback interface with zero cost.
Let’s start with the background story. When we added FRRouting containers support to netlab, someone decided to use lo0 as the loopback interface name. That device doesn’t exist in a typical Linux container, but it’s not hard to add it:
$ ip link add lo0 type dummy
$ ip link set dev lo0 up
TL&DR: FRRouting advertises the IP prefix on the lo loopback interface with zero cost.
Let’s start with the background story. When we added FRRouting containers support to netlab, someone decided to use lo0 as the loopback interface name. That device doesn’t exist in a typical Linux container, but it’s not hard to add it:
$ ip link add lo0 type dummy
$ ip link set dev lo0 up
How many cores is enough for server CPUs? All that we can get, and then some. …
Ampere Readies 256-Core CPU Beast, Awaits The AI Inference Wave was written by Timothy Prickett Morgan at The Next Platform.

Welcome to the 17th edition of Cloudflare’s DDoS threat report. This edition covers the DDoS threat landscape along with key findings as observed from the Cloudflare network during the first quarter of 2024.
But first, a quick recap. A DDoS attack, short for Distributed Denial of Service attack, is a type of cyber attack that aims to take down or disrupt Internet services such as websites or mobile apps and make them unavailable for users. DDoS attacks are usually done by flooding the victim's server with more traffic than it can handle.
To learn more about DDoS attacks and other types of attacks, visit our Learning Center.
Quick reminder that you can access previous editions of DDoS threat reports on the Cloudflare blog. They are also available on our interactive hub, Cloudflare Radar. On Radar, you can find global Internet traffic, attacks, and technology trends and insights, with drill-down and filtering capabilities, so you can zoom in on specific countries, industries, and networks. There’s also a free API allowing academics, data sleuths, and other web enthusiasts to investigate Internet trends across the globe.
To learn how we prepare this report, refer Continue reading
One of my friends is running a large IPv6 network and has already experienced a shortage of IPv6 neighbor cache on some of his switches. Digging deeper into the root causes, he discovered:
In my larger environments, I see significant neighbor table cache entries, especially on network segments with hosts that make many long-term connections. These hosts have 10 to 20 addresses that maintain state over days or weeks to accomplish their processes.
What’s going on? A perfect storm of numerous unrelated annoyances:
One of my friends is running a large IPv6 network and has already experienced a shortage of IPv6 neighbor cache on some of his switches. Digging deeper into the root causes, he discovered:
In my larger environments, I see significant neighbor table cache entries, especially on network segments with hosts that make many long-term connections. These hosts have 10 to 20 addresses that maintain state over days or weeks to accomplish their processes.
What’s going on? A perfect storm of numerous unrelated annoyances: