Heavy Networking 634: Why (Not) MikroTik?
Today's Heavy Networking gets into networking hardware from MikroTik, a vendor you may not have heard of. Our guest is Kevin Myers, a senior network architect and consultant who uses MikroTik with a variety of clients big and small. We'll find out what MikroTik is good for, and not good for, management and support, and more. This is a non-sponsored episode.
The post Heavy Networking 634: Why (Not) MikroTik? appeared first on Packet Pushers.
Futurist Keynote: Professor Sue Black, June 14
SPONSORED POST Technology has changed the lives of countless people over the years, many of them women from underserved communities who have been helped through education and onto the career ladder by the improved methods of communication, collaboration, and information dissemination which IT innovation has consistently enabled. …
Futurist Keynote: Professor Sue Black, June 14 was written by Nicole Hemsoth at The Next Platform.
Sponsored Post: G-Core Labs, Close, Wynter, Pinecone, Kinsta, Bridgecrew, IP2Location, StackHawk, InterviewCamp.io, Educative, Stream, Fauna, Triplebyte

Who's Hiring?
- Close is building the sales communication platform of the future and we're looking for a Site Reliability Engineer to help us accomplish that goal. If you have a passion for databases (both SQL and NoSQL), significant experience building, managing, and monitoring infrastructure, databases, and backend services at scale and want to work with a rag-tag team of hardworking, but humble humans, then come check us out!
- Wynter is looking for system administrators, engineers, and developers to join its research panel. Participate in research surveys, get paid ($90-$180/hr) for your feedback and comments. Super low key commitment, 10-15 mins per survey. Learn more and sign up.
- DevOps Engineer: At Kinsta, we set out to create the best managed hosting platform in the world. If you are an experienced DevOps Engineer who is constantly looking for ways to innovate and improve, we might just be the place for you! As Kinsta’s DevOps Engineer, you will be instrumental in making sure that our infrastructure is always on the bleeding edge of technology, remaining stable and high-performing at all times. If you love working with Linux, have a background in PHP, and have worked with cutting-edge technologies, such as Continue reading
How to Retain Talent in Uncertain Circumstances
Recruiters may be calling your top talent right now. Here's what you can do to make your employees more likely to let those calls go to voice mail.Using OpenSSL with Ed Harmoush 2/6 Generating Certificates – Video
ED, HIS TLS COURSE, AND THE FREE OPENSSL CHEATSHEET Twitter @ed_pracnet https://practicalnetworking.net Practical TLS course: https://pracnet.net/tls OpenSSL Cheatsheet: https://pracnet.net/openssl FILES FOR THE CERT/KEY MATCHING EXERCISE: ZIP VERSION: packetpushers-pracnet-openssl.zip https://ln5.sync.com/dl/1f1f63d90/kqztwkp9-hkcz3yvq-tuzx79ke-aewxgaip TAR.GZ VERSION: packetpushers-pracnet-openssl.tar.gz https://ln5.sync.com/dl/0791b8d50/q973jpyb-qrmz3cpd-xeiar9zn-qu99gi5w FOR MORE INFO Hashing, Hashing Algorithms, and Collisions – Cryptography Symmetric Encryption vs Asymmetric Encryption Public & Private Keys – Signatures & […]
The post Using OpenSSL with Ed Harmoush 2/6 Generating Certificates – Video appeared first on Packet Pushers.
Friday Thoughts Pre-Cisco Live

It’s weird to think that I’m headed out to Cisco Live for the first time since 2019. The in-person parts of Cisco Live have been sorely missed during the pandemic. I know it was necessary all around but I didn’t realize how much I enjoyed being around others and learning from the community until I wasn’t able to do it for an extended period of time.
Now we’re back in Las Vegas and ready to take part in something that has been missed. I’ve got a busy lineup of meetings with the CCIE Advisory Council and Tech Field Day Extra but that doesn’t mean I’m not going to try and have a little fun along the way. And yes, before you ask, I’m going to get the airbrush tattoo again if they brought the artist back. It’s a tradition as old as my CCIE at this point.
What else am I interested in?
- I’m curious to see how Cisco responds to their last disappointing quarter. Are they going to tell us that it was supply chain? Are they going to double down on the software transition? And how much of the purchasing that happened was pull through? Does that mean Continue reading
AAE-1 & SMW5 cable cuts impact millions of users across multiple countries


Just after 1200 UTC on Tuesday, June 7, the Africa-Asia-Europe-1 (AAE-1) and SEA-ME-WE-5 (SMW-5) submarine cables suffered cable cuts. The damage reportedly occurred in Egypt, and impacted Internet connectivity for millions of Internet users across multiple countries in the Middle East and Africa, as well as thousands of miles away in Asia. In addition, Google Cloud Platform and OVHcloud reported connectivity issues due to these cable cuts.
The impact
Data from Cloudflare Radar showed significant drops in traffic across the impacted countries as the cable damage occurred, recovering approximately four hours later as the cables were repaired.
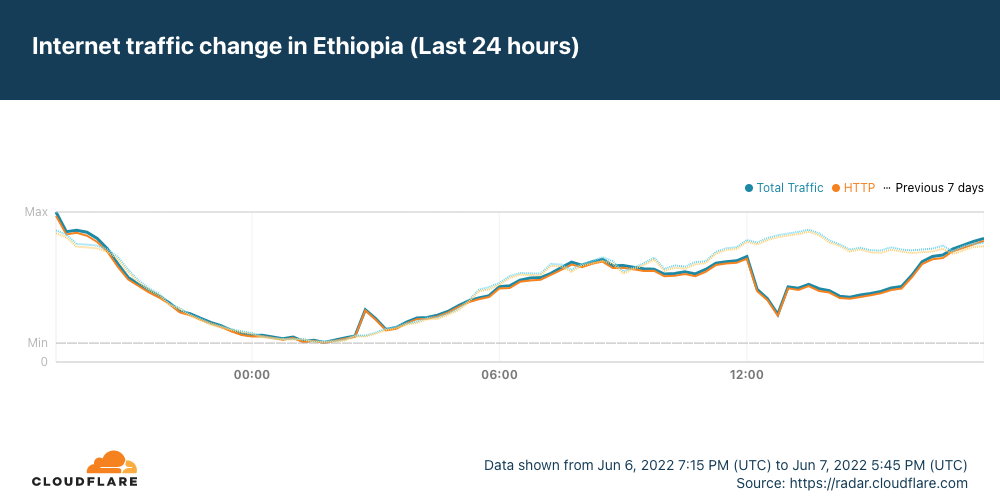
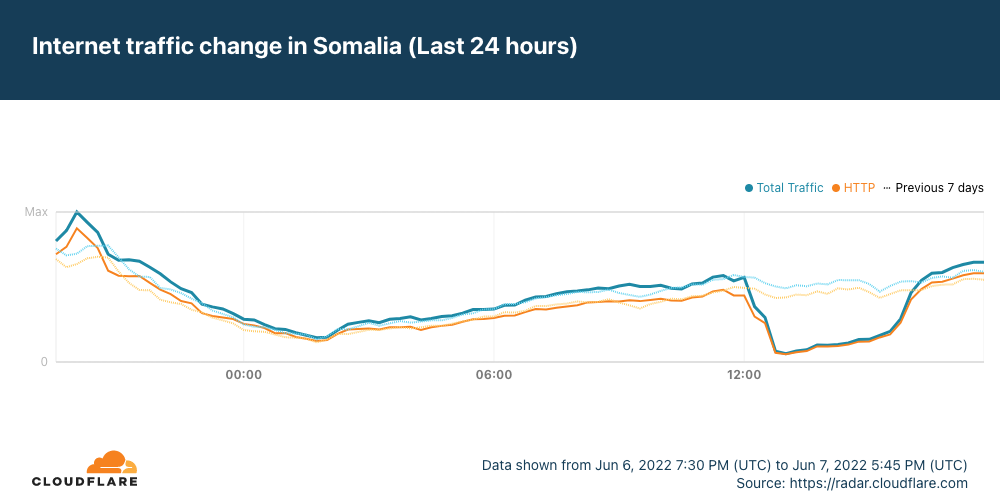
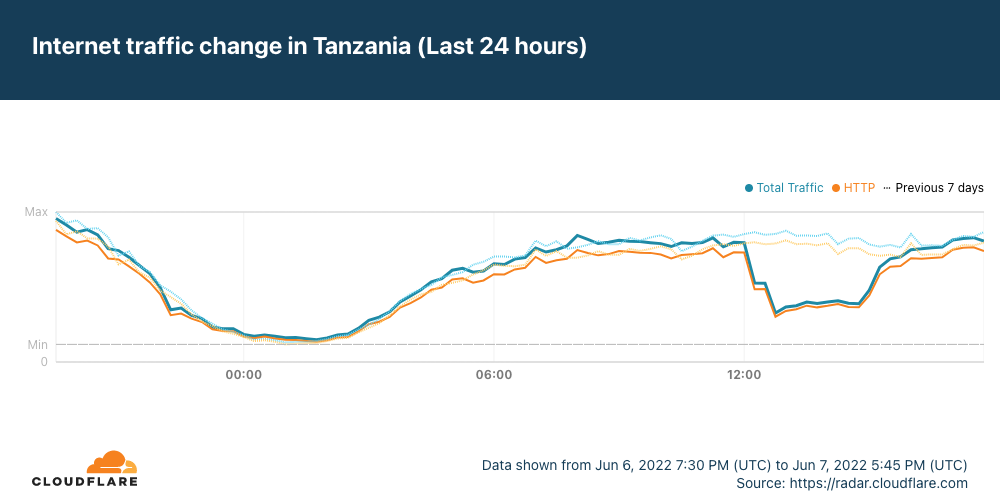
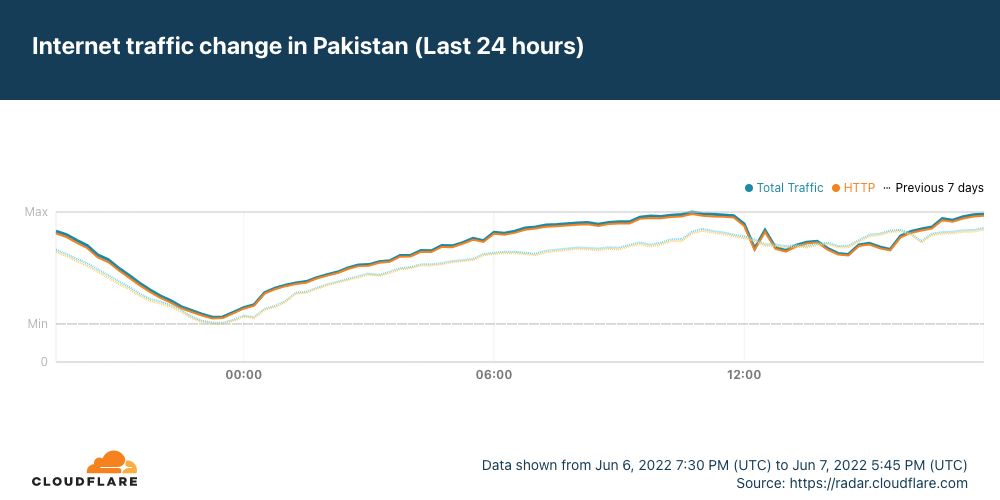
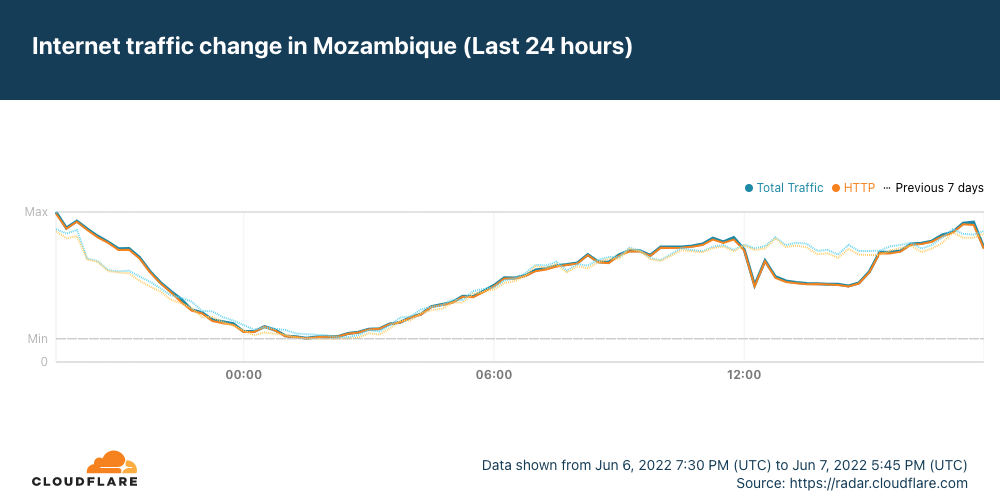
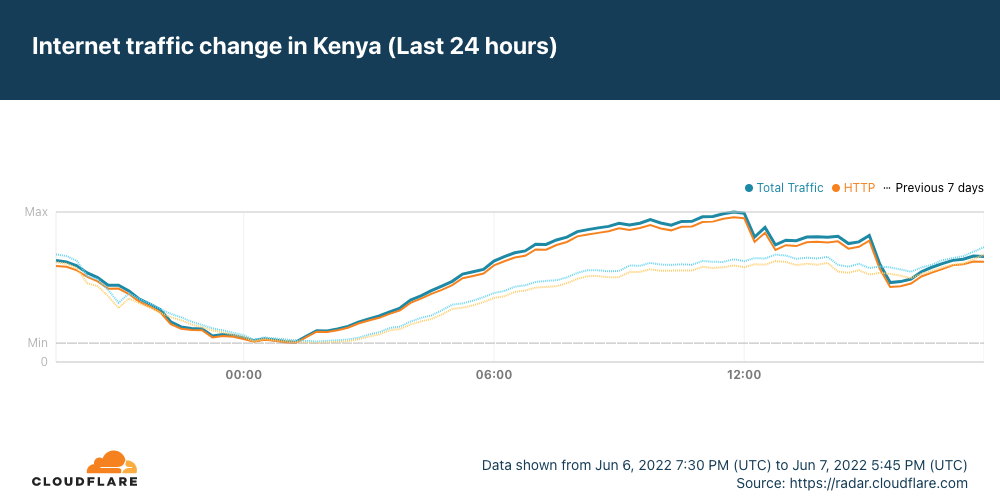
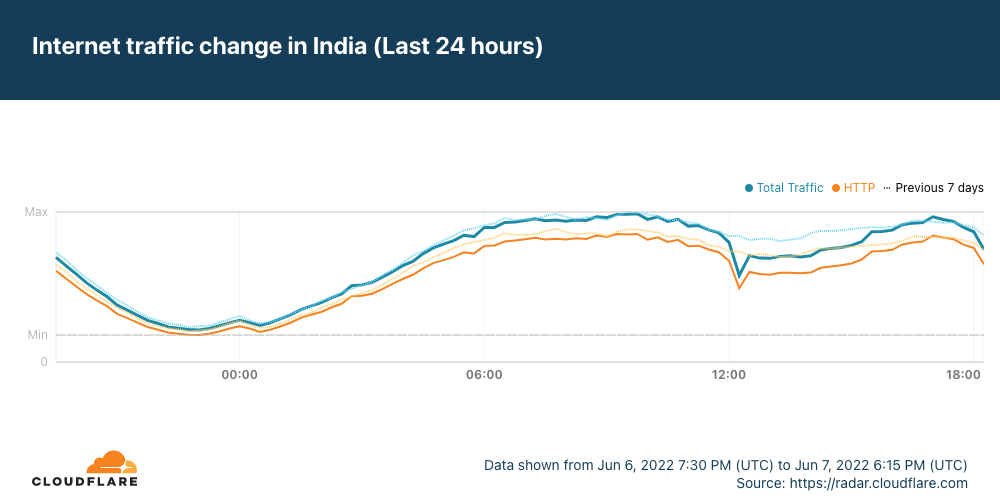
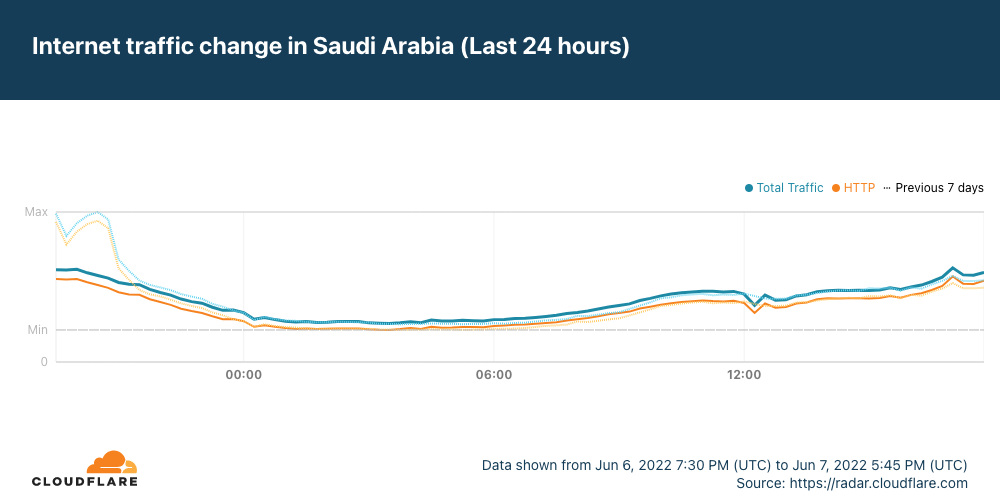
It appears that Saudi Arabia may have also been affected by the cable cut(s), but the impact was much less significant, and traffic recovered almost immediately.
In the graphs above, we show that Ethiopia was one of the impacted countries. However, as it is landlocked, there are obviously no submarine cable landing points within the country. The Afterfibre map from the Network Startup Resource Center (NSRC) shows that that fiber in Ethiopia connects to fiber in Somalia, which experienced an impact. In addition, Ethio Telecom also routes traffic through network providers in Kenya and Djibouti. Djibouti Telecom, one of these providers, in turn Continue reading
Video: Rogue IPv6 RA Challenges
IPv6 security-focused presentations were usually an awesome opportunity to lean back and enjoy another round of whack-a-mole, often starting with an attacker using IPv6 Router Advertisements to divert traffic (see also: getting bored at Brussels airport) .
Rogue IPv6 RA challenges and the corresponding countermeasures are thus a mandatory part of any IPv6 security training, and Christopher Werny did a great job describing them in IPv6 security webinar.
Video: Rogue IPv6 RA Challenges
IPv6 security-focused presentations were usually an awesome opportunity to lean back and enjoy another round of whack-a-mole, often starting with an attacker using IPv6 Router Advertisements to divert traffic (see also: getting bored at Brussels airport) .
Rogue IPv6 RA challenges and the corresponding countermeasures are thus a mandatory part of any IPv6 security training, and Christopher Werny did a great job describing them in IPv6 security webinar.
Key advantages of the Calico eBPF data plane
Project Calico and eBPF
Project Calico has offered a production-ready data plane based on eBPF since September 2020, and it’s been available for technical evaluation for even longer (since February 2020).


The pre-requisites and limitations are simple to review, it’s easy to enable, and it’s easy to validate your configuration. So, there’s never been a better time to start experiencing the benefits!
You do know what those are, don’t you? Don’t worry if not! That’s what this blog post is about. We’ve reached a point where the journey is easy to make, if you know why you want to get there.
Key advantages of using Calico with eBPF
Calico is already the most widely deployed Kubernetes network security solution. What can eBPF do to help our winning formula further? I’ll dive into the details, but let’s look at the highest possible level first.
These three key benefits apply across all supported environments:
- General performance
- Native Kubernetes service handling
- Source IP preservation and Direct Server Return, or DSR
- Each of these benefits is significant and worth discussing in more detail.
Performance
Calico’s eBPF data plane achieves high performance in several ways. Firstly, it achieves higher throughput and/or less CPU Continue reading
How Queen Elizabeth II’s Platinum Jubilee had an impact on the Internet

“I declare before you all that my whole life, whether it be long or short, shall be devoted to your service and the service of our great imperial family to which we all belong.”
— Queen Elizabeth II birthday speech, April 21, 1947

The rising and setting of the sun has an impact on human behaviour and on Internet trends, and events like this weekend's celebration of Queen Elizabeth II’s Platinum Jubilee also show up in Internet trends.
When Elizabeth II's reign started, on February 6, 1952 (the coronation was on June 2, 1953), the Turing machine had already been proposed (1936), and with that the basis for computer science. ARPANET, which became the technical foundation of the Internet, was still a dream that came to fruition in the late 60s — the World Wide Web is from 1989 and in 2014 we celebrated its Silver Jubilee. So, with that in mind, let’s answer the question: did the 2022 celebrations of the first British monarch with a 70th anniversary on the throne have an impact on the UK’s Internet traffic?
First, some details about the Platinum Jubilee. There was a four-day bank holiday (June 2-5) in the UK Continue reading
Strong Showing for First Experimental RISC-V Supercomputer
A European team of university students has cobbled together the first RISC-V supercomputer capable of showing balanced power consumption and performance. …
Strong Showing for First Experimental RISC-V Supercomputer was written by Nicole Hemsoth at The Next Platform.
Using OpenSSL with Ed Harmoush 1/6 Generating Public & Private Keys – Video
Ethan Banks and Ed Harmoush kick off a six-part video series on using OpenSSL. The first video covers the generation of public and private keys in OpenSSL.
The post Using OpenSSL with Ed Harmoush 1/6 Generating Public & Private Keys – Video appeared first on Packet Pushers.
Pump-Up your ITIL with Automation

In the world of automation and agility, it seems that Information Technology Infrastructure Library (ITIL) doesn’t have a role to play anymore, being marked as an “old school” framework. Can it be the end of the methodology after it served numerous IT organizations for so long as a guideline and blueprint for their processes?
This series of articles shows how automation, and more specifically Red Hat Ansible Automation Platform and the principles of Infrastructure as Code (IaC), can help bring some of the ITIL topics into the agile and automated bliss:
- Configuration management
- Change and release management
- Incident and problem management
So let’s step into the topic of configuration management and what everybody still knows as CMDB (Configuration Management Database) even if ITIL has since long titled it as CMS (Configuration Management System). This name change was meant to highlight the fact that the function can be fulfilled by a combination of multiple databases and tools, but it won’t matter here, so we’ll stick to the infamous CMDB term.
Do you love your CMDB? Probably not, according to my experience with numerous customers. The data is generally outdated and wrong, considered useless, which means that its maintenance is considered a Continue reading
A new portal for Project Galileo participants

This post is also available in 日本語, Deutsch, Français, Español and Português.

Each anniversary of Project Galileo serves as an impetus for big-picture thinking among the Cloudflare team about where to take the initiative next. For this eighth anniversary, we want to help participants get the most out of their free security and performance services and simplify the onboarding process.
Organizations protected under Galileo are a diverse bunch, with 111 countries represented across 1,900+ web domains. Some of these organizations are very small and sometimes operated solely by volunteers. It is understandable that many do not have IT specialists or other employees with technical knowledge about security and performance capabilities. We strive to give them the tools and training to succeed, and we felt it was imperative to take this effort to a new level.
Introducing the Cloudflare Social Impact Projects Portal
To provide Galileo participants with one place to access resources, configuration tips, product explainers, and more, we built the Cloudflare Social Impact Projects Portal.
The crisis in Ukraine was a key source of inspiration for this endeavor. With overall applications for the project skyrocketing by 177% in March 2022, we were rushing to onboard new Continue reading