HS 024 – Is Shadow IT a Good Thing
Shadow IT does not always lead to bad outcomHS 024 – Is Shadow IT a Good Thing
Shadow IT does not always lead to bad outcom
The post HS 024 – Is Shadow IT a Good Thing appeared first on Packet Pushers.
Cloudflare’s approach to handling BMC vulnerabilities


In recent years, management interfaces on servers like a Baseboard Management Controller (BMC) have been the target of cyber attacks including ransomware, implants, and disruptive operations. Common BMC vulnerabilities like Pantsdown and USBAnywhere, combined with infrequent firmware updates, have left servers vulnerable.
We were recently informed from a trusted vendor of new, critical vulnerabilities in popular BMC software that we use in our fleet. Below is a summary of what was discovered, how we mitigated the impact, and how we look to prevent these types of vulnerabilities from having an impact on Cloudflare and our customers.
Background
A baseboard management controller is a small, specialized processor used for remote monitoring and management of a host system. This processor has multiple connections to the host system, giving it the ability to monitor hardware, update BIOS firmware, power cycle the host, and many more things.
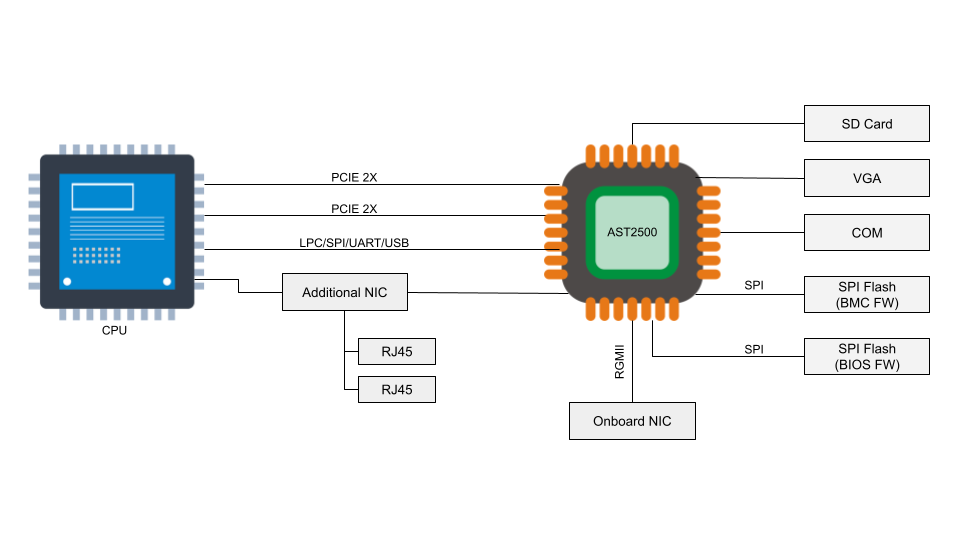
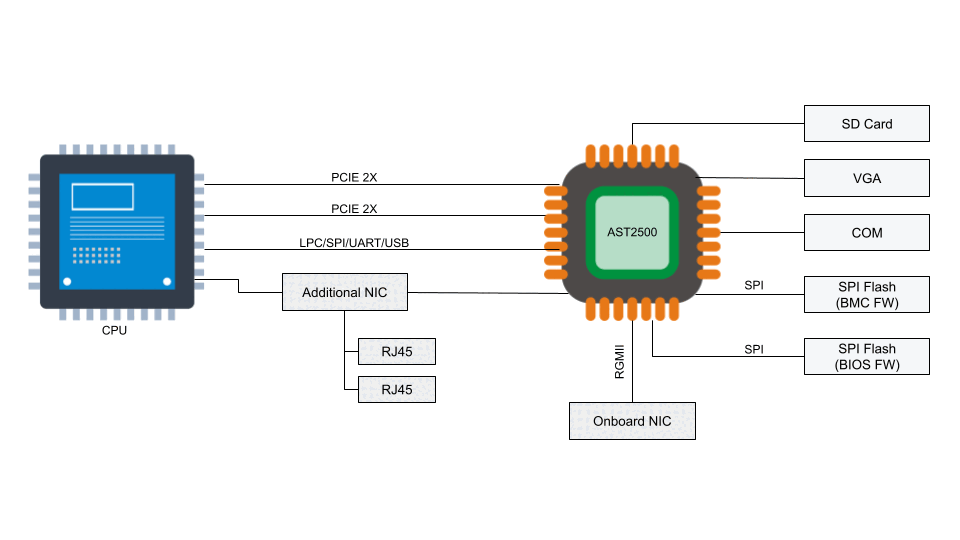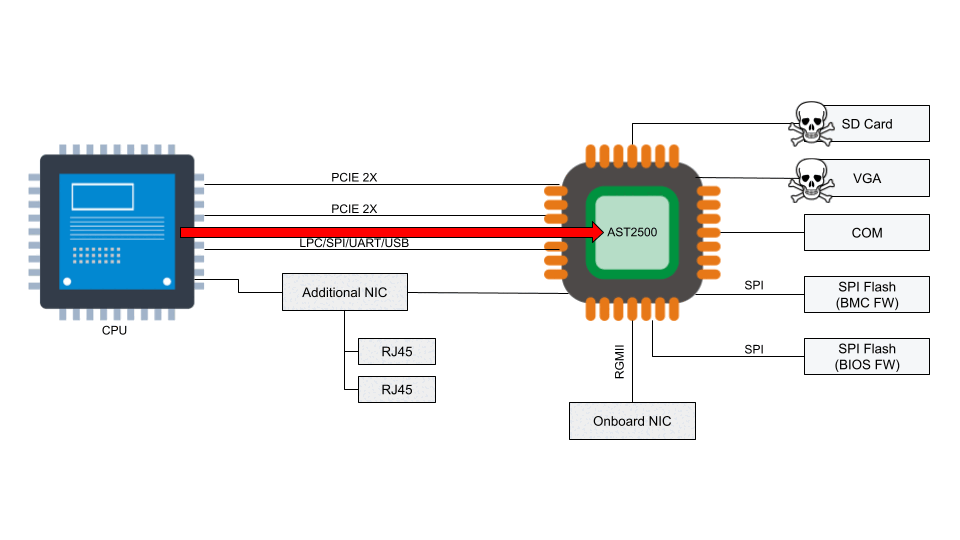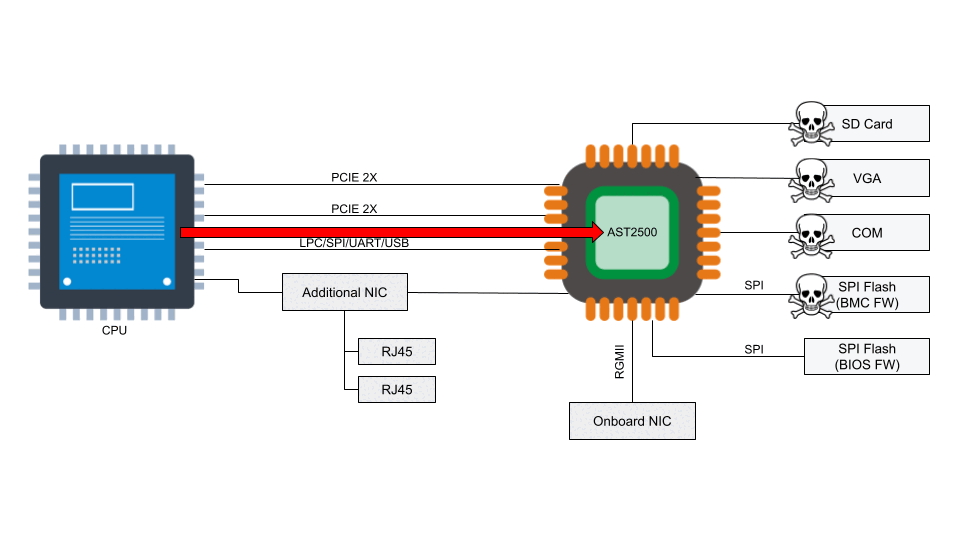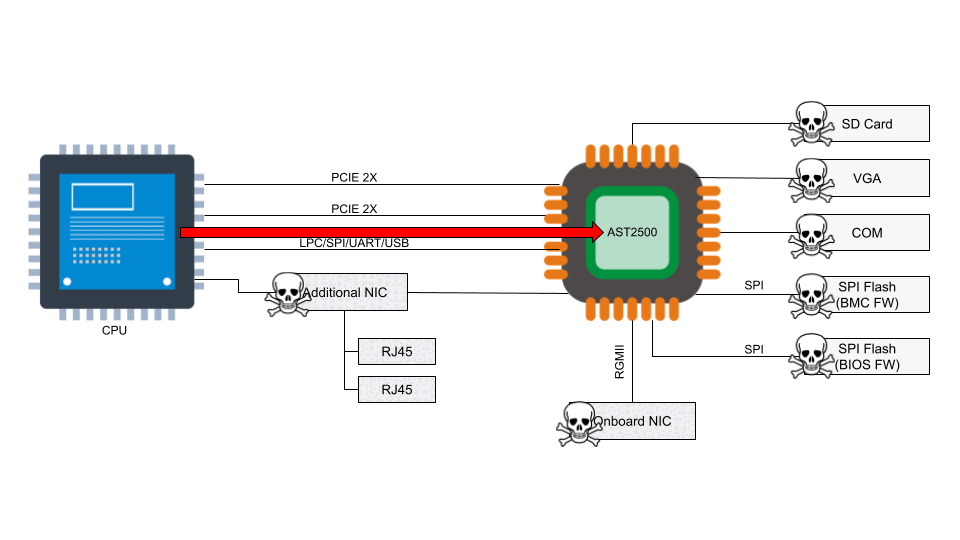
Access to the BMC can be local or, in some cases, remote. With remote vectors open, there is potential for malware to be installed on the BMC from the local host via PCI Express or the Low Pin Count (LPC) interface. With compromised software on the BMC, malware or spyware could maintain persistence on the server.
What’s new in Ansible Automation Platform 2.2

The Ansible product team at Red Hat is thrilled to announce the general availability of Red Hat Ansible Automation Platform 2.2, which includes numerous features and bug fixes that further solidify Ansible Automation Platform as the de facto enterprise IT automation solution for developers to operations teams in data centers, clouds, and at the edge. A few of the most noteworthy features in this release include:
- New automation topology viewer in automation controller
- Red Hat Ansible Certified Content Collections to be digitally signed in Ansible automation hub
- Updated Ansible developer and creator tooling: ansible-navigator, ansible-lint, and VSCode language server support
- Enhanced network automation Collections
- Automation services catalog now available on-premise
- Reporting and analytics of automation data are now further integrated and streamlined
- Red Hat Enterprise Linux 9 support
Don’t forget to check out the product documentation including the release notes!
Automation topology viewer
Let’s face it, automating at enterprise scale is really hard. Although many features were added for the content creator and developer in Ansible Automation Platform 2, the automation operations teams are typically responsible for making sure automation is up and running as it should across all inventories, worldwide, with 24/7 availability and uptime. As enterprise Continue reading
How we treat content as a product

At Cloudflare, we talk a lot about how to help build a better Internet. On the Product Content Experience (PCX) team, we treat content like a product that represents and fulfills this mission. Our vision is to create world-class content that anticipates user needs and helps build accessible Cloudflare products. We believe we can impact the Cloudflare product experience and make it as wonderful as possible by intentionally designing, packaging, and testing the content.
What is “content like a product”?
I like taking on projects. A singular goal is met, and I clearly know I’m successful because the meaning of “done” is normally very clear. For example, I volunteer some of my time editing academic papers about technology. My role as an editor is temporary and there is a defined beginning and end to the work. I send my feedback and my task is largely complete.
“Content like a product” is when you shift your mindset from completing projects to maintaining a product, taking into consideration the user and their feedback. Product content at Cloudflare is an iterative, living, breathing thing. Inspired by the success of teams that adopt an agile mindset, along with some strategic functions you might find Continue reading
Kubernetes Unpacked 001: Prerequisites For Kubernetes Success
Welcome to the inaugural episode of Kubernetes Unpacked, a new podcast in the Packet Pushers Community Channel. The goal of this podcast is to help IT professionals understand Kubernetes: how it works; how and why it's used; how to deploy, operate, and manage the platform on premises and in the cloud; Kubernetes networking and security concepts; and more.Kubernetes Unpacked 001: Prerequisites For Kubernetes Success
Welcome to the inaugural episode of Kubernetes Unpacked, a new podcast in the Packet Pushers Community Channel. The goal of this podcast is to help IT professionals understand Kubernetes: how it works; how and why it's used; how to deploy, operate, and manage the platform on premises and in the cloud; Kubernetes networking and security concepts; and more.
The post Kubernetes Unpacked 001: Prerequisites For Kubernetes Success appeared first on Packet Pushers.
Worth Reading: Resolverless DNS
Every network engineer should be familiar with the DNS basics – after all, all network failures are caused by DNS… unless it’s BGP.
The May 2022 ISP Column by Geoff Huston is an excellent place to brush up on your DNS basics and learn about new ideas, including a clever one to push DNS entries that will be needed in the future to a web client through a DNS-over-HTTPS session.
Worth Reading: Resolverless DNS
Every network engineer should be familiar with the DNS basics – after all, all network failures are caused by DNS… unless it’s BGP.
The May 2022 ISP Column by Geoff Huston is an excellent place to brush up on your DNS basics and learn about new ideas, including a clever one to push DNS entries that will be needed in the future to a web client through a DNS-over-HTTPS session.
Datacenter Becomes Nvidia’s Largest Business
Something that we have been waiting for a decade and a half to see has just happened: The datacenter is now the biggest business at Nvidia. …
Datacenter Becomes Nvidia’s Largest Business was written by Timothy Prickett Morgan at The Next Platform.
Once Again, Meta Buys Rather Than Builds A Supercomputer
For a company that has been so enthusiastic about designing and building its own infrastructure and datacenters, Meta Platforms, the parent company to Facebook as well as WhatsApp and Instagram and one of the champions of the metaverse virtual reality a lot of us first read about in Burning Chrome, sure has not been building its own AI supercomputers lately. …
Once Again, Meta Buys Rather Than Builds A Supercomputer was written by Timothy Prickett Morgan at The Next Platform.