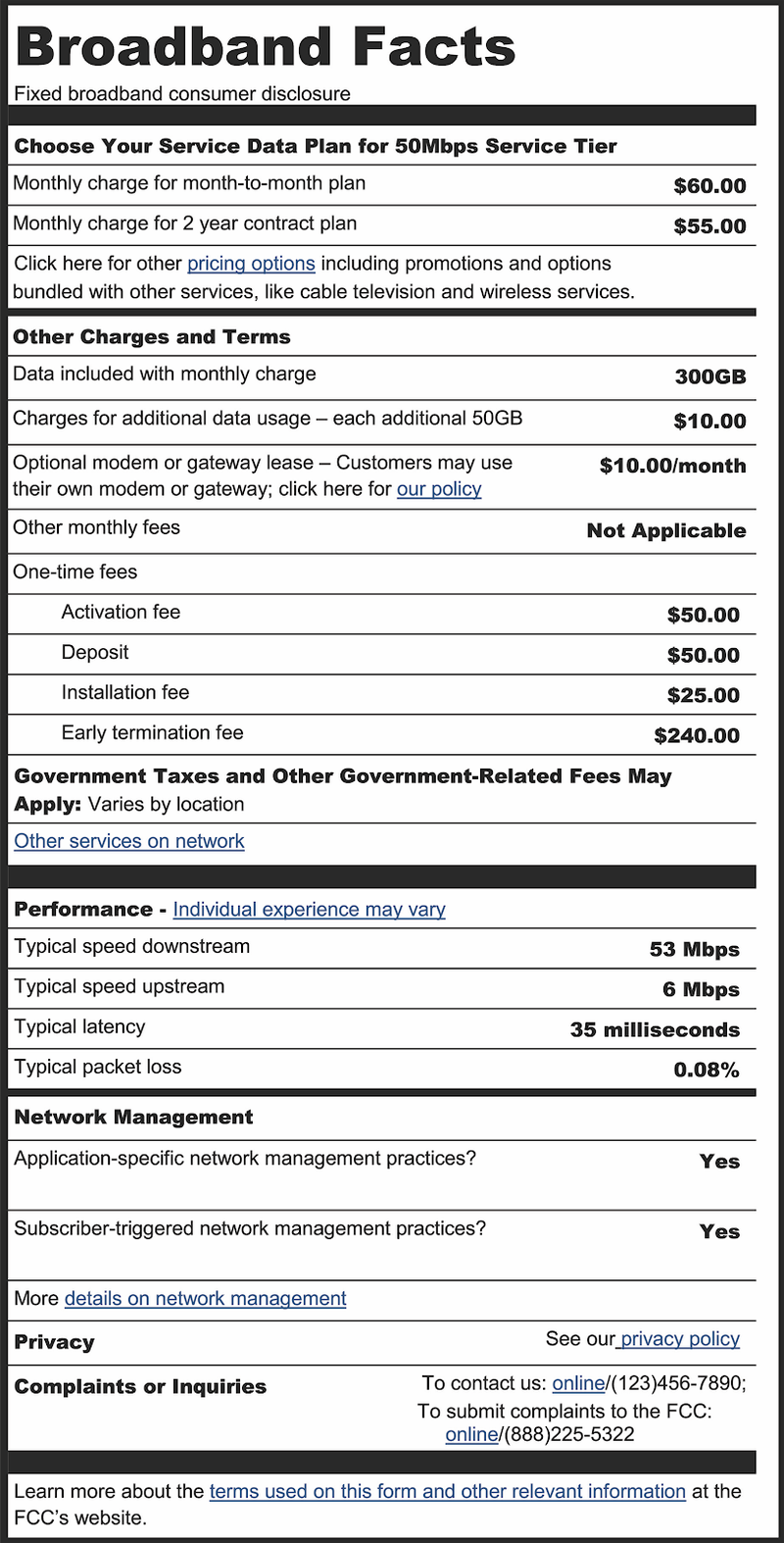
0
In the first installment of our Community Spotlight series, I asked Geoff Burke from Tsunati to share his experience with Kubernetes and Calico Open Source. Geoff talks about how he got started with Kubernetes, the challenges that led him to search for a Container Network Interface (CNI), and why he has chosen Calico Open Source as his preferred CNI.
If you are just getting started with Kubernetes and curious about where other people start their journey, this blog post provides valuable insight and information.
Q: Please tell us a little bit about yourself, including where you currently work and what you do there.
I’m currently a senior cloud solutions architect at Tsunati. We are a data protection company and we focus on backup and recovery, mainly trying to help service providers enhance their services. We have a lot of virtualization expertise. In fact, I am a Veeam legend and a Veeam Vanguard. I also work quite intensely with Kasten by Veeam, which is a Kubernetes-native backup and recovery migration application.
Q: There are many people who are just getting started with Kubernetes and might have a lot of questions. Could you please talk a little bit about your own journey?
Continue reading