NeoVim Install and Configure
Call me crazy, but I decided to have a look at using in this the year of our lord and saviour 2022. NeoVim is a minimal fork of VIM which supports LUA as a scripting engine. In this post, I will show you how to install and configure NeoVim with some fancy plugins and a smattering of TMUX...continue reading
How to enable Recurring Cloudwatch Alarms?
If you do not deal with AWS/CloudWatch you don’t have to read this post.
What: The issue was simple, we had a cloud watch alarm for Lambda Function invocation, now the way I wanted was to send us recurring email notifications if the alarm was not addressed, apparently this is not a cloud-watch native feature and there is a work-around for this.
Short Story: Implementing this will have a new step function which will start alarming based on an alert-timer, this won’t by default apply to all the alarms that you configure, you need to specifically tag it with a keyword, more of those options detailed in the article, so based on the timer you set, Cloud-watch say send SNS notification or any action of your choice to get implemented.
Why Article if you have a Link that explains ?: To start with not everything that I encountered was straightforward, the install process requires you to have a docker environment, and a proper node install and then a CDK install, I never did that and it did waste some time so I wanted to document and also this might help anyone to implement the same.
Spoilers:
Tech Bytes: Apstra Extends Intent-Based Data Center Networking To The Edge (Sponsored)
Today on the Tech Bytes podcast we’re talking about a new release of Juniper’s Apstra intent-based networking platform for data centers. Apstra is introducing new features including a collapsed fabric to extend intent-based networking to edge locations and a new capability that enables group-based policies for more fine-grained policy enforcement.Tech Bytes: Apstra Extends Intent-Based Data Center Networking To The Edge (Sponsored)
Today on the Tech Bytes podcast we’re talking about a new release of Juniper’s Apstra intent-based networking platform for data centers. Apstra is introducing new features including a collapsed fabric to extend intent-based networking to edge locations and a new capability that enables group-based policies for more fine-grained policy enforcement.
The post Tech Bytes: Apstra Extends Intent-Based Data Center Networking To The Edge (Sponsored) appeared first on Packet Pushers.
Revocation
A compromised private key should not be accepted. An attacker might use a compromised private key to impersonate a site, and this vulnerability needs to be prevented to ensure that users can use services over the network with trust in their integrity and security. The way to stop a compromised key from being accepted is to disseminate the information that the key is no longer trustable, and this is achieved by revoking the public key certificate. But we are having some problems in taking this theory and creating practical implementations of certificate revocation.Device Management From The Ground Up: Part 3 – Storage And Filesystems
Your Cisco devices store and interact with files. In this article I cover the different storage types and how to navigate and manipulate them in the device configuration, including printing directories, making new directories, and more.
The post Device Management From The Ground Up: Part 3 – Storage And Filesystems appeared first on Packet Pushers.
Network performance update: Security Week


Almost a year ago, we shared extensive benchmarking results of last mile networks all around the world. The results showed that on a range of tests (TCP connection time, time to first byte, time to last byte), and on different measures (p95, mean), Cloudflare was the fastest provider in 49% of networks around the world. Since then, we’ve worked to continuously improve performance towards the ultimate goal of being the fastest everywhere. We set a goal to grow the number of networks where we’re the fastest by 10% every Innovation Week. We met that goal last year, and we’re carrying the work over to 2022.
Today, we’re proud to report we are the fastest provider in 71% of the top 1,000 most reported networks around the world. Of course, we’re not done yet, but we wanted to share the latest results and explain how we did it.
Measuring what matters
To quantify network performance, we have to get enough data from around the world, across all manner of different networks, comparing ourselves with other providers. We used Real User Measurements (RUM) to fetch a 100kb file from several different providers. Users around the world report the performance of different providers. Continue reading
A New One-Stop Shop for Network Security Topics
Your trusty NSX blog is going through a big change.
We’re uniting our VMware security content in the newly designed VMware Security blog.
Don’t worry, you’ll still be able to find the latest on network automation, application mobility, and load balancing. All the networking content you count on, that’s staying right here.
However, if you’re looking for current and future articles on network security and threat research, those will now be found in a new home—a blog that centralizes security content across VMware into a single channel.
You no longer need to switch (blog) channels for security news, insights, and resources. The newly designed VMware Security Blog will become your new one-stop-shop for key perspectives from experts, specialists, and leaders across VMware NSX, Threat Analysis Unit, and Carbon Black.
On the new blog, you can expect to find all the network security content you know and love — including:
- Important insights and announcements regarding threat research, endpoint security, and network security
- Key analysis of recent ransomware attacks, insights on techniques deployed, and how threats can be detected and mitigated
- Infographics, data points, and award recognition illustrating the strength of VMware security solutions
- Invites Continue reading
Network Break 374: Pluribus Extends DC Fabric To NVIDIA DPUs; Intel Buries Three FPGAs
In this week's Network Break we discuss Pluribus porting its network OS to NVIDIA DPUs, why Intel is pulling the plug on three FPGA cards in its portfolio, the debut of a network operations startup that draws from multiple data sources to help NetOps teams troubleshoot problems faster, and more IT news.“Milan-X” 3D Vertical Cache Yields Epyc HPC Bang For The Buck Boost
Last fall ahead of the SC21 supercomputing conference, AMD said it was going to be the first of the major compute engine makers to add 3D vertical L3 cache to its chips, in this case to variants of the “Milan” Epyc 7003 series of processors that debuted in March 2021 called the “Milan-X” chips. …
“Milan-X” 3D Vertical Cache Yields Epyc HPC Bang For The Buck Boost was written by Timothy Prickett Morgan at The Next Platform.
What’s New in the Ansible Content Collection for Kubernetes 2.3
With increased adoption of container automation, IT organizations continue to expand their requirements when it comes to deploying and managing their Kubernetes clusters. As such, we at Red Hat continue to add new features and capabilities to meet those demands by announcing the availability of kubernetes.core version 2.3, our Red Hat Ansible Certified Content Collection for Kubernetes and Helm.
In this blog post, we’ll go over what’s new and what’s different in this release of our Kubernetes Collection.
New Module - k8s_taint
With the release of kubernetes.core 2.3, we introduce the k8s_taint module. This module provides the ability for a Kuberentes node to repel a pod or set of pods from being scheduled unless they have a matching toleration. This establishes that with taints and tolerations in place, pods are not scheduled onto inappropriate nodes.
This feature is quite useful when you are trying to ensure exclusivity of a particular set of nodes (only allow a particular group of users access) or you want to provide particular nodes with special hardware (such as GPUs) to only run pods that require the use of the specialized hardware and keep out the pods that don’t require Continue reading
Application security: Cloudflare’s view


Developers, bloggers, business owners, and large corporations all rely on Cloudflare to keep their applications secure, available, and performant.
To meet these goals, over the last twelve years we have built a smart network capable of protecting many millions of Internet properties. As of March 2022, W3Techs reports that:
“Cloudflare is used by 80.6% of all the websites whose reverse proxy service we know. This is 19.7% of all websites”
Netcraft, another provider who crawls the web and monitors adoption puts this figure at more than 20M active sites in their latest Web Server Survey (February 2022):
“Cloudflare continues to make strong gains amongst the million busiest websites, where it saw the only notable increases, with an additional 3,200 sites helping to bring its market share up to 19.4%”
The breadth and diversity of the sites we protect, and the billions of browsers and devices that interact with them, gives us unique insight into the ever-changing application security trends on the Internet. In this post, we share some of those insights we’ve gathered from the 32 million HTTP requests/second that pass through our network.
Definitions
Before we examine the data, it is useful to define Continue reading
New cities on the Cloudflare global network: March 2022 edition
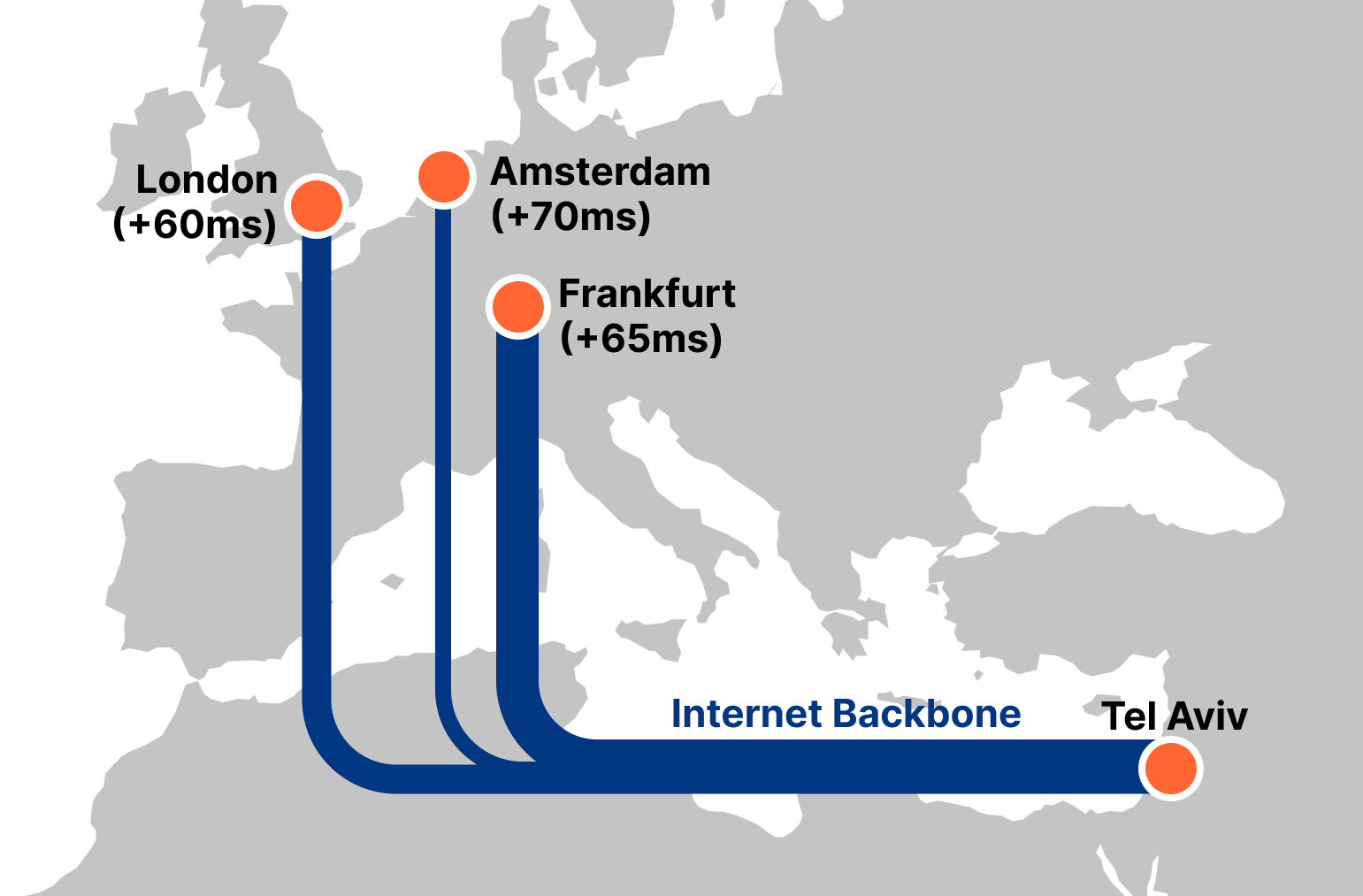
If you follow the Cloudflare blog, you know that we love to add cities to our global map. With each new city we add, we help make the Internet faster, more reliable, and more secure. Today, we are announcing the addition of 18 new cities in Africa, South America, Asia, and the Middle East, bringing our network to over 270 cities globally. We’ll also look closely at how adding new cities improves Internet performance, such as our new locations in Israel, which reduced median response time (latency) from 86ms to 29ms (a 66% improvement) in a matter of weeks for subscribers of one Israeli Internet service provider (ISP).
The Cities
Without further ado, here are the 18 new cities in 10 countries we welcomed to our global network: Accra, Ghana; Almaty, Kazakhstan; Bhubaneshwar, India; Chiang Mai, Thailand; Joinville, Brazil; Erbil, Iraq; Fukuoka, Japan; Goiânia, Brazil; Haifa, Israel; Harare, Zimbabwe; Juazeiro do Norte, Brazil; Kanpur, India; Manaus, Brazil; Naha, Japan; Patna, India; São José do Rio Preto, Brazil; Tashkent, Uzbekistan; Uberlândia, Brazil.
Cloudflare’s ISP Edge Partnership Program
But let’s take a step back Continue reading
DC Fabric Webinar

Sorry for the short notice … I’m teaching a three-hour webinar on DC fabrics and control planes this coming Friday, the 25th, through Safari Books Online. This course covers the basics of spine-and-leaf fabrics, as well as some high level information on various DC fabric control plane options (BGP, RIFT, and IS-IS). Please register here.
How to Pass AWS CLF
AWS CLF Exam
How to pass the Certified Cloud Practitioner from AWS, exam details and type, and what to expect
AWS CLF Exam Content & Topics
The exam agenda starts with the concept of cloud computing and differences of it with on-premise networks.
then it shows you all the AWS services that will be more than enough to migrate or establish a network on AWS’s cloud
which will have all the facilities and can be fully or partially managed by AWS for you.
and of course everything comes for a price, AWS will declare the prices of their services, what is for FREE and what is not
and will provide many easy tools for costs calculation and best practices with AWS.
Amazon’s Touch in the CLF Exam
Amazon provides a free tier 12-month access to whomever creates an account for the 1st time with them
the account has a free access to many AWS services that will allow for both studying and actual testing/benefiting from their services.
AWS CLF Exam Nature & Type
The current version of this exam CLF-C01 has a 65 written question in the exam.
all the questions are single/multi-answer MCQs and no other type of questions Continue reading
What is AWS CLF
What is AWS CLF
Amazon Web Services (AWS) CLF or CCP, how you want to name it (CLF is the official exam and badge name).
as it stands for Certified Cloud Practitioner, with the current version of CLF-C01.
AWS CLF is the very first step for any engineer, regardless of their experience in the IT domain,
to start understanding and put a step in the world of cloud computing.
CLF with AWS Services
The exam/certificate focuses on many different aspects, some are shared with other exams from AWS, some are CLF-Focused.
This includes the concept of cloud computing, comparison of many aspects of networking between On-premise networks and cloud networks.
Introduction to AWS and how much does AWS covers/offers of on-premise services on their cloud, ready to be directly initiated and used.
AWS most critical aspect when you decide to network on their infrastructure, and that is “Billing”, this is a very important and critical concept to really understand and know how to deal with when you start working with AWS networks.
Is AWS-CLF important?
Many tends to skip this exam, and keeps spreading the idea that “SAA is the Associate exam of AWS Services, and it should be the Continue reading