Carbon Negative Supercomputing is Closer than it Appears
Datacenters are notorious consumers of power but there is a revolution brewing. …
Carbon Negative Supercomputing is Closer than it Appears was written by Nicole Hemsoth at The Next Platform.
Full Stack Journey 060: The Argo Project – Tools To Help You Run Kubernetes
Today's Full Stack Journey podcast delves into the open-source Argo project, a collection of tools to help ops team use Kubernetes. Our guest is Hong Wang. He's an Argo maintainer and co-founder and CEO of Akuity, a for-profit company built around Argo.Full Stack Journey 060: The Argo Project – Tools To Help You Run Kubernetes
Today's Full Stack Journey podcast delves into the open-source Argo project, a collection of tools to help ops team use Kubernetes. Our guest is Hong Wang. He's an Argo maintainer and co-founder and CEO of Akuity, a for-profit company built around Argo.
The post Full Stack Journey 060: The Argo Project – Tools To Help You Run Kubernetes appeared first on Packet Pushers.
wrangler 2.0 — a new developer experience for Cloudflare Workers


Much of a developer’s work is about making trade-offs: consistency versus availability, speed over correctness, you name it. While there will always be different technical trade-offs to consider, we believe there are some that you, as a developer, should never need to make.
One of those decisions is an easy-to-use development environment. Whether you’re onboarding a new developer to your team or you simply want to develop faster, it’s important that even the smallest of things are optimized for speed and simplicity.
That’s why we're excited to announce the second-generation of our developer tooling for Cloudflare Workers. It’s a new developer experience that’s out-of-the-box, lightning fast, and can even run Workers on a local machine. (Yes!)
If you’re already familiar with our existing tools, we’re not just talking about the wrangler CLI, we’re talking about its next major release: wrangler 2.0. Stick around to get a sneak-peak at the new experience.
No config? No problem
We’ve made it much easier to get started with Cloudflare Workers. All you need is a single JavaScript file to run a Worker -- no configuration needed. You don't even need to decide on a name!
When you run wrangler dev <filename>, Continue reading
Developer Spotlight: James Ross, Nodecraft


Nodecraft allows gamers to host dedicated servers for their favorite games. James Ross is the Chief Technology Officer for Nodecraft and has advocated for Cloudflare — particularly Cloudflare Workers — within the company.
"We use Workers for all kinds of things. We use Workers to optimize our websites, handle redirects, and deal with image content negotiation for our main website. We're very fortunate that the majority of our users are using modern web browsers, so we can serve images in formats like JPEG XL and AVIF to users through a Workers script".
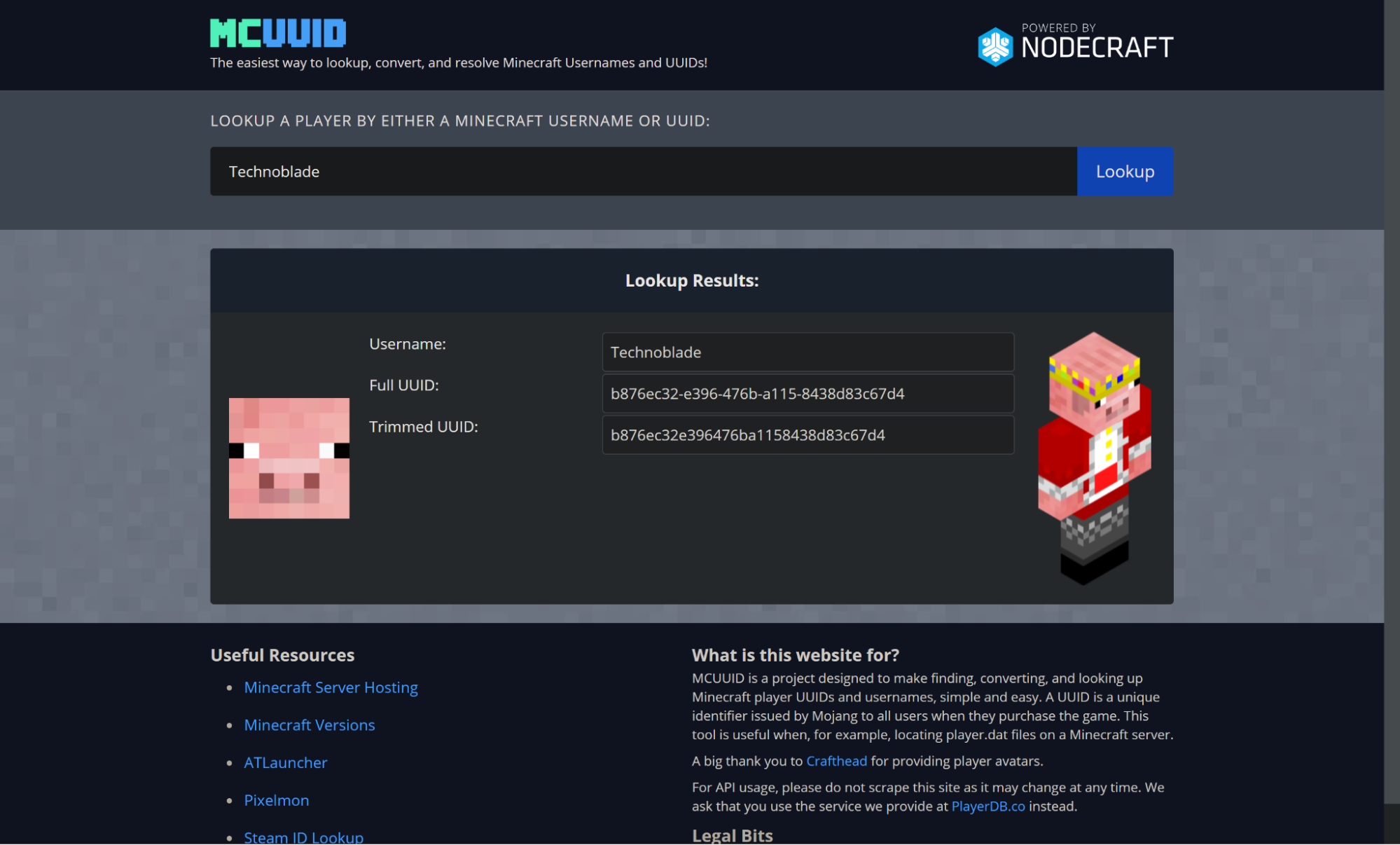
Nodecraft also maintains a number of microsites and APIs that are relied upon by the gaming community to retrieve game information. PlayerDB provides a JSON API for looking up information on user profiles for a number of gaming services, and MCUUID and SteamID are wrapped frontends for users of those services to interact with that API. Each of these is written and deployed as a Cloudflare Worker:
"Whenever a player joins a Minecraft server, we want to get their information — like their name and player image — and show it to our users. That API receives a hundred million requests a month. And we use the same Continue reading
Automatically generating types for Cloudflare Workers
Historically, keeping our Rust and TypeScript type repos up to date has been hard. They were manually generated, which means they ran the risk of being inaccurate or out of date. Until recently, the workers-types repository needed to be manually updated whenever the types changed. We also used to add type information for mostly complete browser APIs. This led to confusion when people would try to use browser APIs that aren’t supported by the Workers runtime they would compile but throw errors.
That all changed this summer when Brendan Coll, whilst he was interning with us, built an automated pipeline for generating them. It runs every time we build the Workers runtime, generating types for our TypeScript and Rust repositories. Now everything is up-to-date and accurate.
A quick overview
Every time the Workers runtime code is built, a script runs over the public APIs and generates the Rust and TypeScript types as well as a JSON file containing an intermediate representation of the static types. The types are sent to the appropriate repositories and the JSON file is uploaded as well in case people want to create their own types packages. More on that later.
This means the static types Continue reading
JavaScript modules are now supported on Cloudflare Workers


We’re excited to announce that JavaScript modules are now supported on Cloudflare Workers. If you’ve ever taken look at an example Worker written in JavaScript, you might recognize the following code snippet that has been floating around the Internet the past few years:
addEventListener("fetch", (event) => {
event.respondWith(new Response("Hello Worker!"));
}
The above syntax is known as the “Service Worker” API, and it was proposed to be standardized for use in web browsers. The idea is that you can attach a JavaScript file to a web page to modify its HTTP requests and responses, acting like a virtual endpoint. It was exactly what we needed for Workers, and it even integrated well with standard Web APIs like fetch() and caches.
Before introducing modules, we want to make it clear that we will continue to support the Service Worker API. No developer wants to get an email saying that you need to rewrite your code because an API or feature is being deprecated; and you won’t be getting one from us. If you’re interested in learning why we made this decision, you can read about our commitment to backwards-compatibility for Workers.
What are JavaScript modules?
JavaScript modules, Continue reading
Introducing Services: Build Composable, Distributed Applications on Cloudflare Workers
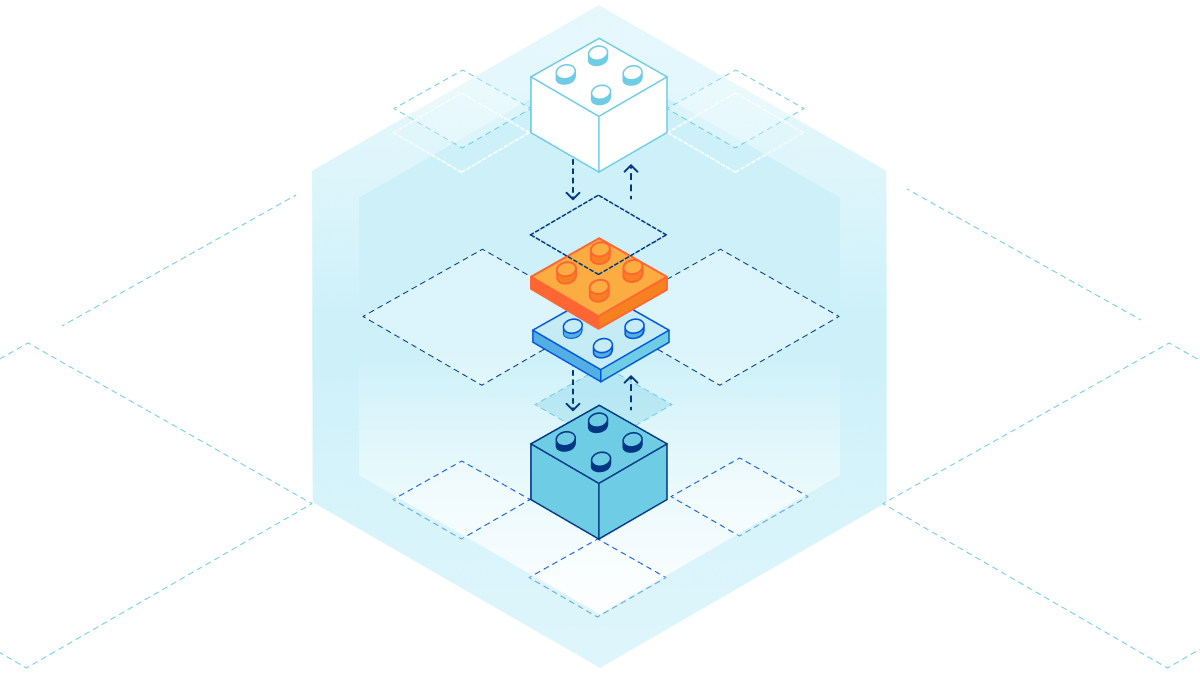
First, there was the Worker script. It was simple, yet elegant. With just a few lines of code, you could rewrite an HTTP request, append a header, or make a quick fix to your website.
Though, what if you wanted to build an entire application on Workers? You’d need a lot more tools in your developer toolbox. That’s why we’ve introduced extensions to Workers platform like KV, our distributed key-value store; Durable Objects, — a strongly consistent, object-oriented database; and soon R2, the no-egress object storage. While these tools allow you to build a more robust application, there’s still a gap when it comes to building a system architecture, composed of many applications or services.
Imagine you’ve built an authentication service that authorizes requests to your API. You’d want to re-use that logic among all your other services. Moreover, when you make changes to that authentication service, you’d want to test it in a controlled environment that doesn’t affect those other services in production. Well, you don’t need to imagine anymore.
Introducing Services
Services are the new building block for deploying applications on Cloudflare Workers. Unlike the script, a service is composable, which allows services to talk Continue reading
Optimizing the Time-to-First-Byte
I don’t think I’ve ever met someone saying “I wish my web application would run slower.” Everyone wants their stuff to run faster, but most environments are not willing to pay the cost (rearchitecting the application). Welcome to the wonderful world of PowerPoint “solutions”.
The obvious answer: The Cloud. Let’s move our web servers closer to the clients – deploy them in various cloud regions around the world. Mission accomplished.
Not really; the laws of physics (latency in particular) will kill your wonderful idea. I wrote about the underlying problems years ago, wrote another blog post focused on the misconceptions of cloudbursting, but I’m still getting the questions along the same lines. Time for another blog post, this time with even more diagrams.
Optimizing the Time-to-First-Byte
I don’t think I’ve ever met someone saying “I wish my web application would run slower.” Everyone wants their stuff to run faster, but most environments are not willing to pay the cost (rearchitecting the application). Welcome to the wonderful world of PowerPoint “solutions”.
The obvious answer: The Cloud. Let’s move our web servers closer to the clients – deploy them in various cloud regions around the world. Mission accomplished.
Not really; the laws of physics (latency in particular) will kill your wonderful idea. I wrote about the underlying problems years ago, wrote another blog post focused on the misconceptions of cloudbursting, but I’m still getting the questions along the same lines. Time for another blog post, this time with even more diagrams.
HPE Wins Another European HPC Center With Cray EX Plus AMD Compute
Per aspera, ad astra, an old Latin adage that means “through striving, to the stars,” is the root of the name for a hybrid HPC and AI supercomputer that the Grand Équipment National de Calcul Intensif (GENCI), working in conjunction with the Centre Informatique National de l’Enseignement Supérieur (CINES), one of three national HPC centers in France, will be building next year to bring a factor of 20X more compute power to bear on scientific applications. …
HPE Wins Another European HPC Center With Cray EX Plus AMD Compute was written by Timothy Prickett Morgan at The Next Platform.
AX.25 in user space
The Linux kernel AX.25 implementation (and userspace) is pretty poor. I’ve encountered many problems. E.g.:
-
you can’t read() and write() from the same socket at the same time
-
CRC settings default such that at least all my radios (and direwolf) drop the first two packets sent. (fix with
kissparms radio -c 1) -
On 64bit Raspberry Pi OS
setsockoptfor some flags don’t take effect at all (e.g. settingAX25_EXTSEQ), and treat other obvious correct ones as invalid (e.g. can’t setAX25_WINDOWto any value at all). -
I also get kernel null pointer dereferences on 32bit Raspberry Pi OS when testing AX.25. Not exactly comforting.
-
Other OSs don’t have AX.25 socket support. E.g. OpenBSD. And it’s not obvious to me that this is best solved in kernel space.
-
It doesn’t seem clear to anyone how the AX.25 stack in the kernel is supposed to work. E.g. should
axparms -assocbe an enforcing ACL? It’s not, but is it supposed to be? -
I’ve also seen suggestions that AX.25 should be ripped out of the Linux kernel. Continue reading
Learn How Real-World Organizations Benefited from an Overhaul of their Security Lifestyle
Achieving better security is something we all know is necessary but can struggle to get there. It’s like improving your diet: you know you need to eat better and exercise to cultivate a healthier, more well-rounded lifestyle. But you don’t do it because it’s hard, often expensive, and can be a pain. So, you avoid it (trust me, we’ve all been there). But, you learn that putting one foot in front of the other forces you to take small steps toward big results. The same notion applies to needing better security. We know we need it, but it’s not always easy to know where to begin.
There is no quick fix for sustainable change. Sure, we can make better choices each day, but it takes consistency and a solid structural foundation – a lifestyle change – to maintain these advancements. Losing weight is one thing; when it comes to better multi-cloud security, this is a process that leaves little room for fluctuation. Start with the fundamentals and tighten your belt over time.
Let’s take a look at real-world organizations that have benefitted from doing the hard stuff. They’ve done the work and have seen the results. Continue reading
Why Did China Keep Its Exascale Supercomputers Quiet?
There are no greater bragging rights in supercomputing than those that come with top ten listing on the bi-annual list of the world’s most powerful systems—the Top 500. …
Why Did China Keep Its Exascale Supercomputers Quiet? was written by Nicole Hemsoth at The Next Platform.
Top500 Supercomputers: Hungry For The Exascale Feast
Let’s just cut right to the chase scene. The latest Top500 ranking of supercomputers, announced today at the SC21 supercomputing conference being held in St Louis, needed the excitement of an actual 1 exaflops sustained performance machine running the High Performance Linpack benchmark at 64-bit precision. …
Top500 Supercomputers: Hungry For The Exascale Feast was written by Timothy Prickett Morgan at The Next Platform.
Nexus Dashboard Fabric Controller 12
Good day every one,
As you certainly know, we are now rebranding DCNM 11 to Nexus Dashboard Fabric Controller, consequently, NDFC 12 is the new acronym to automate and operate NX-OS based fabrics
It is NOT just about changing the name, there are several significant changes with NDFC 12. To list few of them:
- Enhanced Topology View
- Ability to modify switch discovery IP
- Flexible CLI option – config profile or native NXOS CLI
- Performance Programmable reports
- Granular RBAC
- Secure POAP User
- Simplified and flexible Image Management
- Server Smart Licensing
- Automate IOS-XR configuration
- Automate VXLAN EVPN fabric deployment with Cat9k
One of the key evolution in regard to NDFC is that it now joins the ecosystem of services that runs natively on top of the common Nexus dashboard platform.

One of the key advantages for the network operators with this evolution, is that they just need a single experience, it doesn’t really matter what application you run, from the installation process to the common Web GUI. All applications or services look with the same logic behind any requests.
You have a single pane of glass which is the Nexus dashboard platform through which the end-user can consume different applications for the Continue reading
