Aruba Assembles SDN Tech for Edge Services Platform
Aruba Edge Services Platform is comprised of 35 services, including a dozen new insights that were...
Aruba Edge Services Platform is comprised of 35 services, including a dozen new insights that were...
IBM quit the facial recognition business; A10, Dell teamed up on application delivery; and Alibaba...
I recently had a need to test a configuration involving the use of a single NAT Gateway servicing multiple private subnets across multiple availability zones (AZs) within a single VPC. While there are notable caveats with such a design (see the “Caveats” section at the bottom of this article), it could make sense in some use cases. In this post, I’ll show you how I used TypeScript with Pulumi to automate the creation of this design.
For the most part, if you’re familiar with Pulumi and using TypeScript with Pulumi, this will be pretty straightforward. The code I’ll show you makes a couple assumptions:
vpc.pubSubnetIds (for public subnets) or privSubnetIds (for private subnets). (How to create the subnets and capture the list of IDs is left as an exercise for the reader. If you’d be interested in seeing how I do it, let me know. Continue readingThis week is the second in a two-part series on the Internet of Things. We cover IoT security...
Ivan Pepelnjak was a founding member of the first IX in Slovenia twenty-five years ago. He joins us to describe the origins of the Internet, from the first dial-up circuits to the founding of the first IX and local DNS services here on the History of Networking. Ivan is an independent consultant and trainer; his work can be found at https://ipspace.net.
The announcement comes weeks after the Taiwanese chipmaker announced plans to build the facility.
CEO Arvind Krishna made the pledge in a letter to the U.S. Congress. It’s one of three policy...
Both bundles can use A10’s Harmony Controller for application management and integration into...
The company is recruiting IT professionals with expertise in networking, database management,...
Today's Heavy Networking, sponsored by Cisco, examines results and insights from 1,300 global CIOs in Cisco's CIO Perspectives 2020 survey. Guest Jo Peterson, VP of Cloud & Security for Clarify360, shares highlights and learnings on CIO priorities, security, digital transformation, empowering teams, and more.
The post Heavy Networking 522: How CIOs Prioritize Security – Cisco’s CIO Perspectives 2020 Survey (Sponsored) appeared first on Packet Pushers.
Long gone are the days when high performance computing was limited solely to traditional simulation and modeling at academic and government research labs. …
A New Era In High Performance Computing was written by Timothy Prickett Morgan at The Next Platform.
Dan Stanzione has a lot of compute power at his fingertips. …
Attacking The Novel Coronavirus With Supercomputing Cycles was written by Jeffrey Burt at The Next Platform.

When people connect to the Internet, they can change the world for the better. And so many people have done just that, using this transformative technology to make strides in education, economic opportunity, and health outcomes. But Internet access is only part of the equation. There’s now a different kind of divide: the gap between those who have the knowledge and skills to use the Internet to empower themselves and their communities – and those who don’t.
To address this gap, the Internet Society Foundation is launching SCILLS: Strengthening Communities, Improving Lives and Livelihoods. The program aims to expand economic growth, improve health outcomes, and increase educational opportunities – by supporting communities to more knowledgeably and skillfully use the Internet.
In its pilot year, the program is open to eligible organizations in Bangladesh, Colombia, and Senegal, with expansion to additional countries planned in coming years. It provides grants of up to $150,000 USD for projects lasting up to 24 months. Applications are open between 9 June and 3 July, and grantees will be announced in early September.
The Internet is for everyone – a critical lifeline that can Continue reading
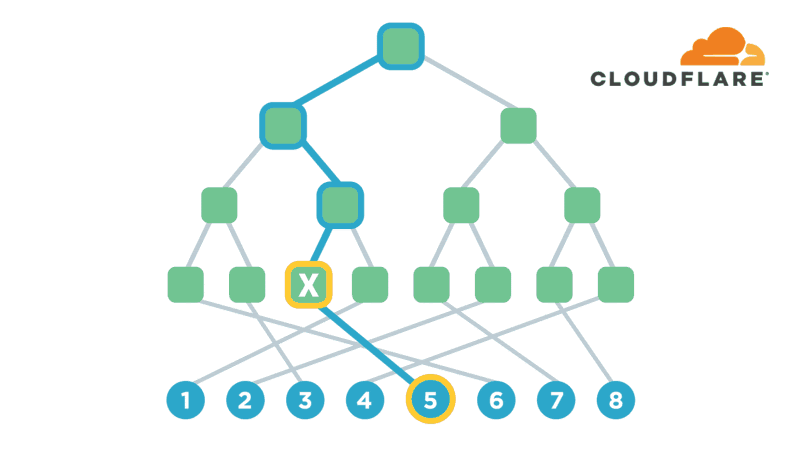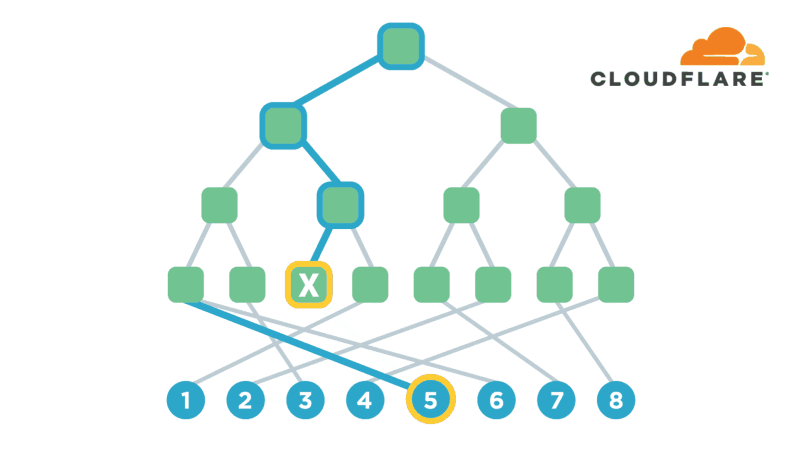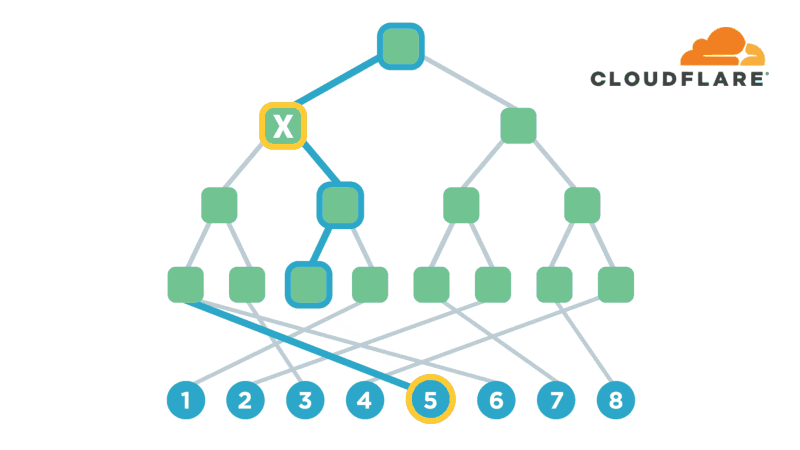
Encryption is one of the most powerful technologies that everyone uses on a daily basis without realizing it. Transport-layer encryption, which protects data as it’s sent across the Internet to its intended destination, is now ubiquitous because it’s a fundamental tool for creating a trustworthy Internet. Disk encryption, which protects data while it’s sitting idly on your phone or laptop’s hard drive, is also becoming ubiquitous because it prevents anybody who steals your device from also being able to see what’s on your desktop or read your email.
The next improvement on this technology that’s starting to gain popularity is end-to-end encryption, which refers to a system where only the end-users are able to access their data -- not any intermediate service providers. Some of the most popular examples of this type of encryption are chat apps like WhatsApp and Signal. End-to-end encryption significantly reduces the likelihood of a user’s data being maliciously stolen from, or otherwise mishandled by a service provider. This is because even if the service provider loses the data, nobody will have the keys to decrypt it!
Several months ago, I realized that I had a lot of sensitive files on my computer (my diary, if Continue reading
There’s one thing no cloud vendor ever managed to change: virtual machines running on top of cloud infrastructure expect to have Ethernet interfaces.
It doesn’t matter if the virtual Ethernet Network Interface Cards (NICs) are implemented with software emulation of actual hardware (VMware emulated the ancient Novell NE1000 NIC) or with paravirtual drivers - the virtual machines expect to send and receive Ethernet frames. What happens beyond the Ethernet NIC depends on the cloud implementation details.
As service providers adopt virtualization and SDN capabilities, they are being held back by...
I recently purchased a new Apple Magic Mouse 2 and an Apple Magic Trackpad 2—not to use with my MacBook Pro, but to use with my Fedora-powered laptop (a Lenovo 5th generation ThinkPad X1 Carbon; see my review). I know it seems odd to buy Apple accessories for a non-Apple laptop, and in this post I’d like to talk about why I bought these items as well as provide some (relatively early) feedback on how well they work with Fedora.
First, let me talk about the why behind my purchase of these items. Several years ago, I started simultaneously using both an external trackpad/touchpad and an external mouse with my macOS-based home office setup. I realize this is probably odd, but I adopted the practice as a way of eliminating “mouse finger” on my right hand. With this arrangement, I stopped trying to scroll with my right-hand (either using a mouse wheel with older mice or using the scroll-enabled back of the Magic Mouse), and instead shifting scrolling to my left hand (using two-finger scrolling on the trackpad). This “division of labor” worked well. Because my existing Magic Mouse and Magic Trackpad—both earlier generations—don’t work with Continue reading
AT&T activated the first US dynamic spectrum sharing deployment; Ericsson burned cash on China...
Today, the operational role of IT is obvious. The rapid developments enabled by automation create genuine business value. The results that can be achieved by automation have a direct link to a company’s business goals.
As a CTO or CIO, sometimes you need help articulating this to stakeholders. Translating IT departments’ performance into business prioritized KPIs. Most see efficiency gains, cost and risk reductions, for example. Automation is clearly an executive-level issue.
At first, Ansible was a classical tool that was utilized for specific automation. Ansible helps your team automate routine tasks, so that they can instead focus on what you want to do. The platform enables you to structure work by automating your processes.
The global, all-day digital event – Ansible Automates 2020 – takes place on June 10. The event provides inspiration as to how the automation journey can be accelerated and taken to the next level. And no, we’re not going to discuss functionality and technology all day. We want to highlight the cultural and behavioral changes that are linked to the trend towards greater automation.
For organizations to achieve the best results, Continue reading