Huawei Invests $1.5B in Developers, Teases AI Cloud
Huawei plans to invest $1.5 billion in developer tools and teased a bevy of AI cloud services and...
Heavy Networking 472: Grappling With Wireless QoS
If you are deploying an enterprise QoS scheme, wireless QoS matters to you. On today's episode, we go through the basics of wireless QoS, covering some of the standards, terminology, and thinking required to get your head around how we can prioritize packets over a shared medium. Our guest is Ryan Adzima.
The post Heavy Networking 472: Grappling With Wireless QoS appeared first on Packet Pushers.
When TCP sockets refuse to die
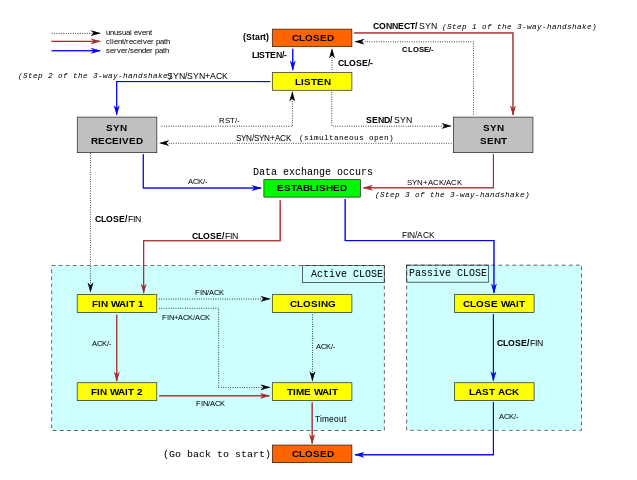
While working on our Spectrum server, we noticed something weird: the TCP sockets which we thought should have been closed were lingering around. We realized we don't really understand when TCP sockets are supposed to time out!
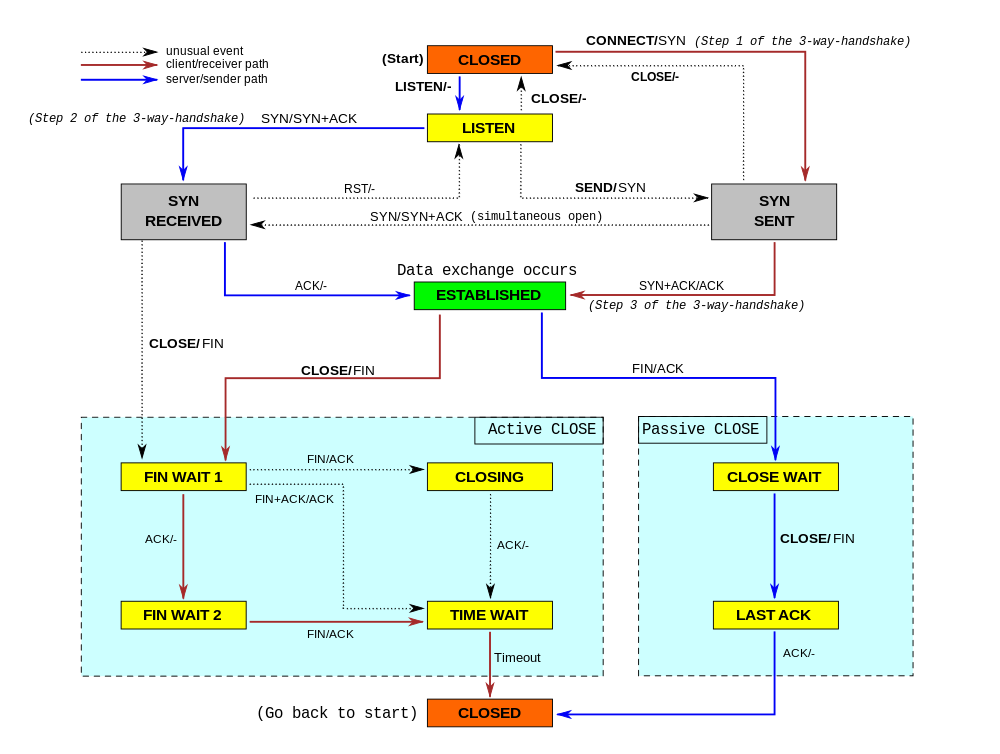
In our code, we wanted to make sure we don't hold connections to dead hosts. In our early code we naively thought enabling TCP keepalives would be enough... but it isn't. It turns out a fairly modern TCP_USER_TIMEOUT socket option is equally as important. Furthermore it interacts with TCP keepalives in subtle ways. Many people are confused by this.
In this blog post, we'll try to show how these options work. We'll show how a TCP socket can timeout during various stages of its lifetime, and how TCP keepalives and user timeout influence that. To better illustrate the internals of TCP connections, we'll mix the outputs of the tcpdump and the ss -o commands. This nicely shows the transmitted packets and the changing parameters of the TCP connections.
SYN-SENT
Let's start from the simplest case - what happens when one attempts to establish a connection to a server which discards inbound SYN packets?
$ Continue reading
Weekly Wrap: VMware CEO States IBM Paid Too Much for Red Hat
Weekly Wrap for Sept. 20, 2019: Kubernetes is central to the VMware-IBM rivalry; Cloudflare's IPO...
Community Spotlight – Terry Slattery
Terry Slattery has a distinguished career in networking and is well known for his contributions to the Cisco CLI, being the second person to obtain the CCIE, providing consultation to many organizations, and the list goes on. If it’s happened in networking, there’s a very good chance that Terry has experience in it. Today Terry joins us to to talk about how he got started into networking and how he’s navigated a very successful career in networking.
The post Community Spotlight – Terry Slattery appeared first on Network Collective.
It’s A Wireless Problem, Right?

How many times have your users come to your office and told you the wireless was down? Or maybe you get a phone call or a text message sent from their phone. If there’s a way for people to figure out that the wireless isn’t working they will not hesitate to tell you about it. But is it always the wireless?
Path of Destruction
During CWNP Wi-Fi Trek 2019, Keith Parsons (@KeithRParsons) gave a great talk about Tips, Techniques, and Tools for Troubleshooting Wireless LAN. It went into a lot of detail about how many things you have to look at when you start troubleshooting wireless issues. It makes your head spin when you try and figure out exactly where the issues all lie.
However, I did have to put up a point that I didn’t necessarily agree with Keith on:
Juniper JNCIE-ENT Refresh
A few months ago Juniper announced that the JNCIE-ENT lab exam would be getting a much-needed refresh. On November 1st …
The post Juniper JNCIE-ENT Refresh appeared first on Fryguy's Blog.
Cascadia Code | Windows Command Line Tools For Developers

Another free and open monospaced font for code development this time from Microsoft. A key differentiator is the inclusion of ligatures for programming symbols (see below). Ligature support is rare among text editors and very rare for TTF encoded fonts. Its more common to see OTF ligatures supported. Also, no italics support yet. Creating fonts […]
The post Cascadia Code | Windows Command Line Tools For Developers appeared first on EtherealMind.
Opinionated Automation: Packaged, Extensible & Closed Systems
Network engineers for the last twenty years have created networks from composable logical constructs, which result in a network of some structure. We call these constructs “OSPF” and “MPLS”, but they all inter-work to some degree to give us a desired outcome. Network vendors have contributed to this composability and network engineers have come to expect it by default. It is absolute power from both a design and an implementation perspective, but it’s also opinionated. For instance, spanning-tree has node level opinions on how it should participate in a spanning-tree and thus how a spanning-tree forms, but it might not be the one you desire without some tweaks to the tie-breaker conditions for the root bridge persona.
Moving to the automated world primarily means carrying your existing understanding forward, adding a sprinkle of APIs to gain access to those features programmatically and then running a workflow, task or business process engine to compose a graph of those features to build your desired networks in a deterministic way.
This is where things get interesting in my opinion. Take Cisco’s ACI platform. It’s closed and proprietary in the sense of you can’t change the way it works internally. You’re lumped with a Continue reading
Privacy Regulations Are Evolving: Are Organizations Ready?

Privacy statements are both a point of contact to inform users about their data and a way to show governments the organization is committed to following regulations. On September 17, the Internet Society’s Online Trust Alliance (OTA) released “Are Organizations Ready for New Privacy Regulations?“ The report, using data collected from the 2018 Online Trust Audit, analyzes the privacy statements of 1,200 organizations using 29 variables and then maps them to overarching principles from three privacy laws around the world: General Data Protection Regulation (GDPR) in the European Union, California Consumer Privacy Act (CCPA) in the United States, and Personal Information Protection and Electronics Document Act (PIPEDA) in Canada.
In many cases, organizations lack key concepts covering data sharing in their statements. Just 1% of organizations in our Audit disclose the types of third parties they share data with. This is a common requirement across privacy legislation. It is not as onerous as having to list all of the organizations; simply listing broad categories like “payment vendors” would suffice.
Data retention is another area where many organizations are lacking. Just 2% had language about how long and why they would retain data. Many organizations have Continue reading
Video: The Need for Network Layers
After identifying some of the challenges every network solution must address (part 1, part 2, part 3) we tried to tackle an interesting question: “how do you implement this whole spaghetti mess in a somewhat-reliable and structured way?”
The Roman Empire had an answer more than 2000 years ago: divide-and-conquer (aka “eating the elephant one bite at a time”). These days we call it layering and abstractions.
In the Need for Network Layers video I listed all the challenges we have to address, and then described how you could group them in meaningful modules (called networking layers).
You need free ipSpace.net subscription to watch the video, or a paid ipSpace.net subscriptions to watch the whole webinar.
How To Network To Get A Mental Health Research Job
Once you have received all of the education you need in order to get a mental health research job, the next thing you have to do is look for a job that you are most suited for. Depending on your education and your interest, a mental health research job ranges from being an actual researcher to a data analyst to a facility manager to a research moderator who monitors the way the research is being conducted. Oftentimes, it takes a great deal of networking and effort on your part to get the right mental health research job that you desire. Here are a few ways to network to help you find your dream job in this very special field.
3 Ways to Get a Mental Health Research Job
Take an Internship
Sometimes you can work as an unpaid intern in a mental health research facility while still getting your formal education. The benefit of this is the experience you’ll receive, as well as possible class credit and professional references.
In other cases, once you have your degree and take all the necessary tests, you may be able to secure a paid internship or an entry level job in mental health Continue reading
Deutsche Telekom Taps VMware for Disaster Recovery
VMware's vCloud Availability will power Deutsche Telekom's Dynamic Services for Infrastructure...
Have Lots of Unused or Free Disk Space on your Mac

More memory didn't solve the problem but free disk space did
The post Have Lots of Unused or Free Disk Space on your Mac appeared first on EtherealMind.
Splunk Bumps Up VC Fund, Plunks Out New Pricing Tiers
Splunk unveils data-to-everything platform, a VC arm, and new partner initiatives, to "remove the...
Microsoft Gifts Semmle to GitHub, Plans $40B Stock Buyback
Semmle’s semantic code analysis engine allows developers and security teams to discover and track...