Meet the VMware Service-defined Firewall: A new approach to firewalling
VMware has had front row seats to the digital transformation that has touched virtually every organization. We’ve been there (and helped drive!) the journey from monolithic applications hosted on a single server, to distributed apps running in VMs, to further decentralization in the form of cloud-native apps composed of microservices. Now, we’re watching the proliferation of public clouds, the up and coming space of serverless and the adoption of functions as a service as ways to build and deploy applications faster than ever.
It’s this vantage point that also gives us clear line of sight to one of the biggest cyber security challenges that modern enterprises face: as their applications become more distributed, an organization’s attack surface significantly increases. Despite all of the advancements and innovation in the way applications are built, we have not seen the same rate of progress with respect to the way applications are secured. Adopting a zero-trust network security model in an enterprise environment remains incredibly hard to achieve. How do you know what security policies to create? How do you enforce those policies consistently across on-premises physical and virtual environments, let alone the public cloud? How do you enforce them across different Continue reading
VMware Unveils Service-Defined Firewall at RSA Conference
 It uses VMware’s ability to inspect the guest OS and application without being resident in the...
It uses VMware’s ability to inspect the guest OS and application without being resident in the...
Automating Brownfield Device Configuration (Part 2)
A month ago Josef Fuchs described the process he uses to merge existing Cisco IOS device configuration with configuration snippets generated by his network automation solution.
In the second part of his article he dived deep into implementation details, described Ansible playbook and Jinja2 templates he’s using, how he optimized the solution with a custom Jinja2 filter, and the caveats he encountered.
Did Someone Say 5G?
 5G was by far the biggest talking point at this year's MWC Barcelona event but Huawei did give it a...
5G was by far the biggest talking point at this year's MWC Barcelona event but Huawei did give it a...
MWC 2019 – 5G Fatigue? No Problem, Let’s Talk Edge
 Edge, the new overhyped term for MWC 2020.
Edge, the new overhyped term for MWC 2020.
Alphabet’s Security Startup Chronicle Sells Its Backstory
 It’s a cloud service built on Google infrastructure that lets companies upload, store, and...
It’s a cloud service built on Google infrastructure that lets companies upload, store, and...
SDxCentral’s Top 10 Articles — February 2019
 AT&T ties its 5G and Airship plans to the Mirantis core; the Linux community uncovers a runC...
AT&T ties its 5G and Airship plans to the Mirantis core; the Linux community uncovers a runC...
Tech Bytes: Leveraging Packets And Flows For NetOps And SecOps With VIAVI Solutions (Sponsored)
Find out how packet capture and flow data can serve both the network and security teams to solve performance problems and investigate security events in this sponsored Tech Bytes conversation with VIAVI Solutions. Our guest is Charles Thompson, Sr. Director, Product Management at VIAVI.
The post Tech Bytes: Leveraging Packets And Flows For NetOps And SecOps With VIAVI Solutions (Sponsored) appeared first on Packet Pushers.
Trump Campaign Revives Nationalized 5G Network Plan
 The plan calls for the government to take wireless spectrum from the Defense Department and use a...
The plan calls for the government to take wireless spectrum from the Defense Department and use a...
Juniper to Buy Mist Systems for $405 Million
 Juniper CEO called the purchase an "offensive move" against its networking competitors, namely...
Juniper CEO called the purchase an "offensive move" against its networking competitors, namely...
CrowdStrike Falcon Expands Wings to Target Mobile Device Security
 Falcon for Mobile identifies threats on mobile devices and provides visibility into situations...
Falcon for Mobile identifies threats on mobile devices and provides visibility into situations...
Network Break 224: Beware TLS Alternatives; Volta Networks And Veriflow Launch New Products
Today's Network Break examines a ETS, a proposed alternative to TLS 1.3 that enables decryption, looks at ICAAN's call for DNSSEC everywhere, discusses new products from startups Volta Networks and Veriflow, and much more tech news.
The post Network Break 224: Beware TLS Alternatives; Volta Networks And Veriflow Launch New Products appeared first on Packet Pushers.
Is it Balance, or Workism?
While we tend to focus on work/life balance, perhaps the better question is: how effective are we at using the time we use for work? From a recent study (which you may have already seen):
- Workers average just 2 hours and 48 minutes of productive device time a day
- 21% of working hours are spent on entertainment, news, and social media
- 28% of workers start their day before 8:30 AM (and 5% start before 7 AM)
- 40% of people use their computers after 10 PM
- 26% of work is done outside of normal working hours
- Workers average at least 1 hour of work outside of working hours on 89 days/year (and on ~50% of all weekend days)
- We check email and IM, on average, every 6 minutes
This is odd—we are starting work earlier, finishing later, and working over weekends, but we still only “work” less than three hours a day.
The first question must be: is this right? How are they measuring productive versus unproductive device time? What is “work time,” really? I know I don’t keep any sort of recognizable “office hours,’ so it seems like it would be hard to measure how much time I spend Continue reading
AT&T Claims Open ROADM Success Validates Interoperability Work
 The demonstration is using open APIs to connect the entire system to a programmable optical network...
The demonstration is using open APIs to connect the entire system to a programmable optical network...
Google, VMware Team Up With Lookout on Post-Perimeter Security Alliance
 Alliance members will demonstrate how their products and services work together to secure...
Alliance members will demonstrate how their products and services work together to secure...
Wireshark 3.0 Released
Recently, Wireshark dropped a major release which adds a few cool features (some new and some old). However outside of the new features, there is one major under the hood change this feature introduces. WireShark v3 for Windows now ships with Npcap as opposed to Winpcap that we have been used forever now. Npcap is […]Building fast interpreters in Rust
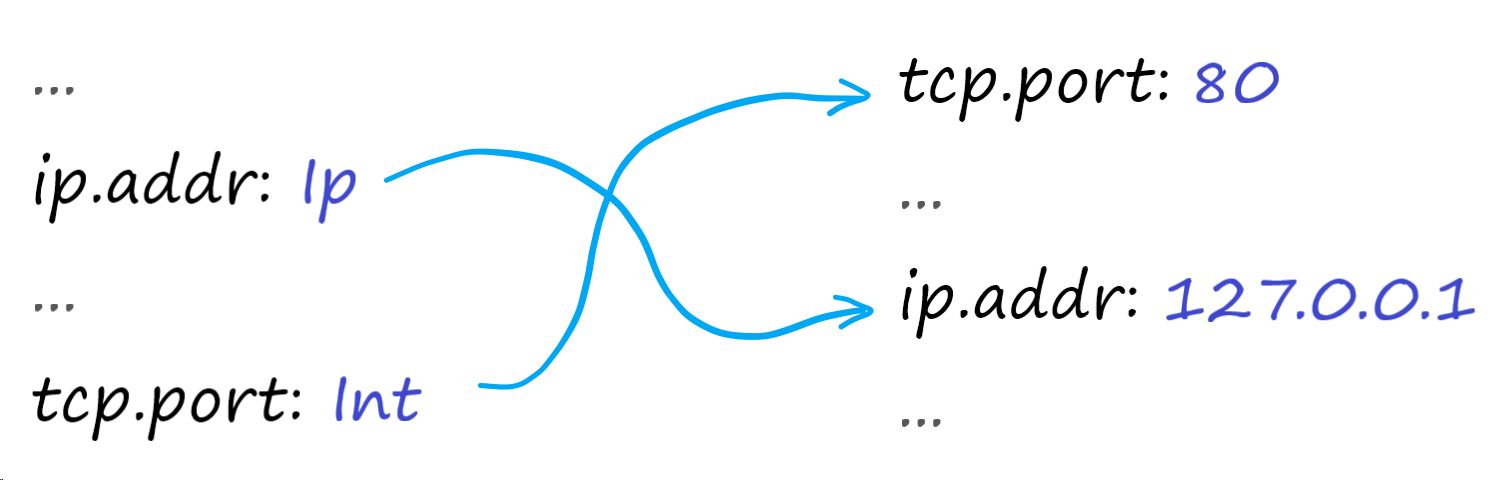
In the previous post we described the Firewall Rules architecture and how the different components are integrated together. We also mentioned that we created a configurable Rust library for writing and executing Wireshark®-like filters in different parts of our stack written in Go, Lua, C, C++ and JavaScript Workers.
With a mixed set of requirements of performance, memory safety, low memory use, and the capability to be part of other products that we’re working on like Spectrum, Rust stood out as the strongest option.
We have now open-sourced this library under our Github account: https://github.com/cloudflare/wirefilter. This post will dive into its design, explain why we didn’t use a parser generator and how our execution engine balances security, runtime performance and compilation cost for the generated filters.
Parsing Wireshark syntax
When building a custom Domain Specific Language (DSL), the first thing we need to be able to do is parse it. This should result in an intermediate representation (usually called an Abstract Syntax Tree) that can be inspected, traversed, analysed and, potentially, serialised.
There are different ways to perform such conversion, such as:
- Manual char-by-char parsing using state machines, regular expression and/or native string APIs.
- Parser combinators, which use Continue reading
Microsoft Azure Sentinel Moves SIEM to the Cloud
 The vendor claims it’s the first cloud native security information and event management (SIEM)...
The vendor claims it’s the first cloud native security information and event management (SIEM)...
Short Take – Navigating Technology Change
In and industry where technology seems to change overnight sometimes, how should you decide what you should and shouldn’t invest time in? Are there techniques you can use to optimize navigating technology change? In this Short Take, Russ shares his take on how you should analyze new technologies and intelligently approach new tech to not be ahead or behind of the curve.
The post Short Take – Navigating Technology Change appeared first on Network Collective.



