The Week in Internet News: IoT Hacked? Who Knows?

IoT survey: Nearly half of all companies using IoT devices don’t have mechanisms in place to detect if any of their devices have been hacked, according to a survey featured in a Fast Company story. Just 14 percent of the respondents to the Gemalto survey believe providing security is an ethical consideration.
Huge leak: More than 22 million unique passwords and 772 million email addresses were leaked and distributed by hackers in a folder named “Collection #1,” Mashable reports. The cache of emails and passwords were collected from several data, dating back to 2008.
Pushing back: WhatsApp is planning to fight India’s recent crackdown on encryption, FT.com reports. Indian policymakers have proposed rules that would allow authorities to trace the origin of encrypted messages, but WhatsApp says it will protest the proposals.
Fighting fake news: Japan’s government plans to come up with a plan to fight fake news by June, Japan Times says. The plan could include requiring social media companies to create codes of conduct. Several other attempts by governments to fight fake news have led to concerns about censorship, however.
AI as a weapon: Forbes.com has a story raising concerns about the weaponization of Artificial Intelligence. Continue reading
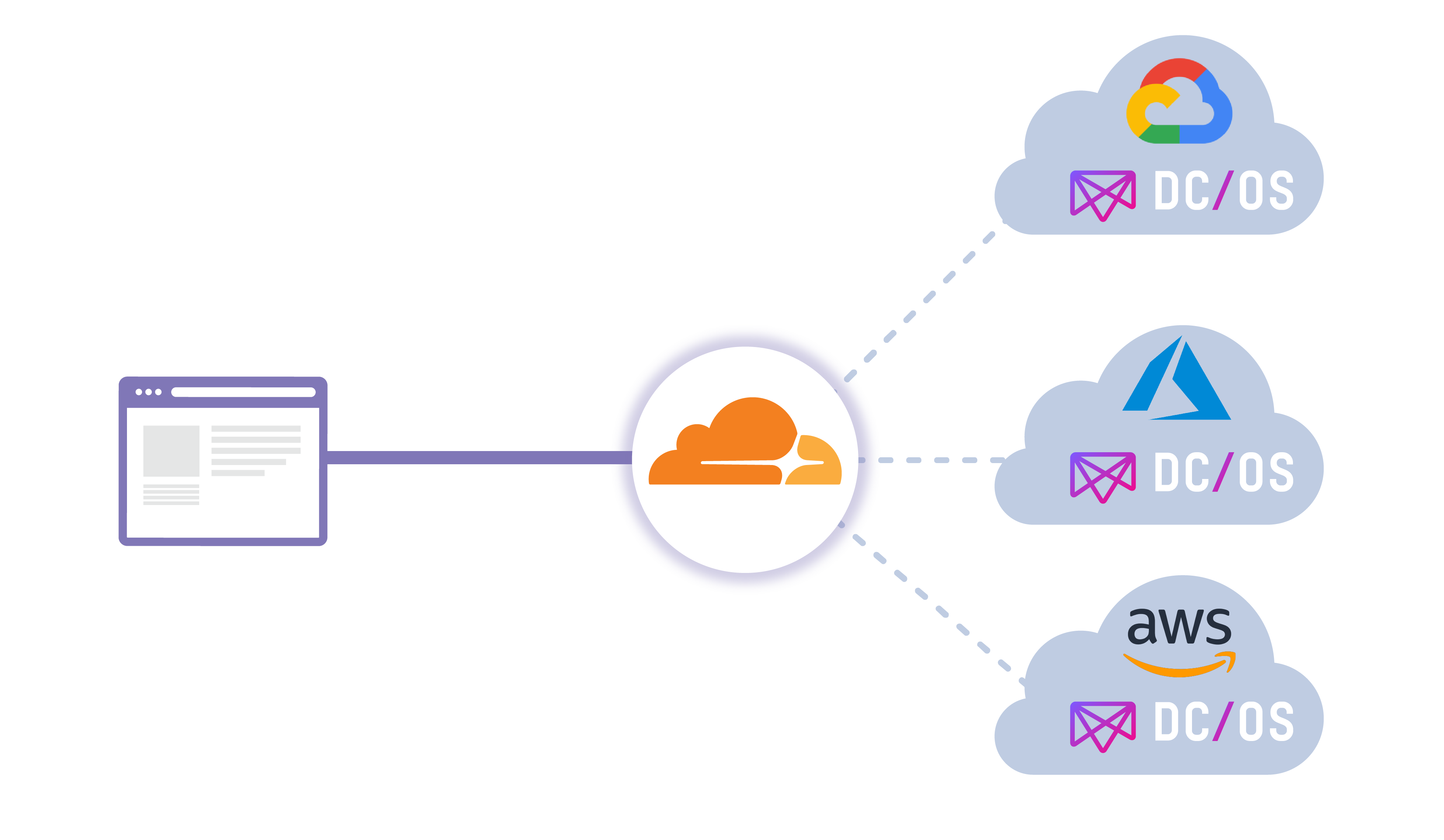
Argo Tunnel + DC/OS
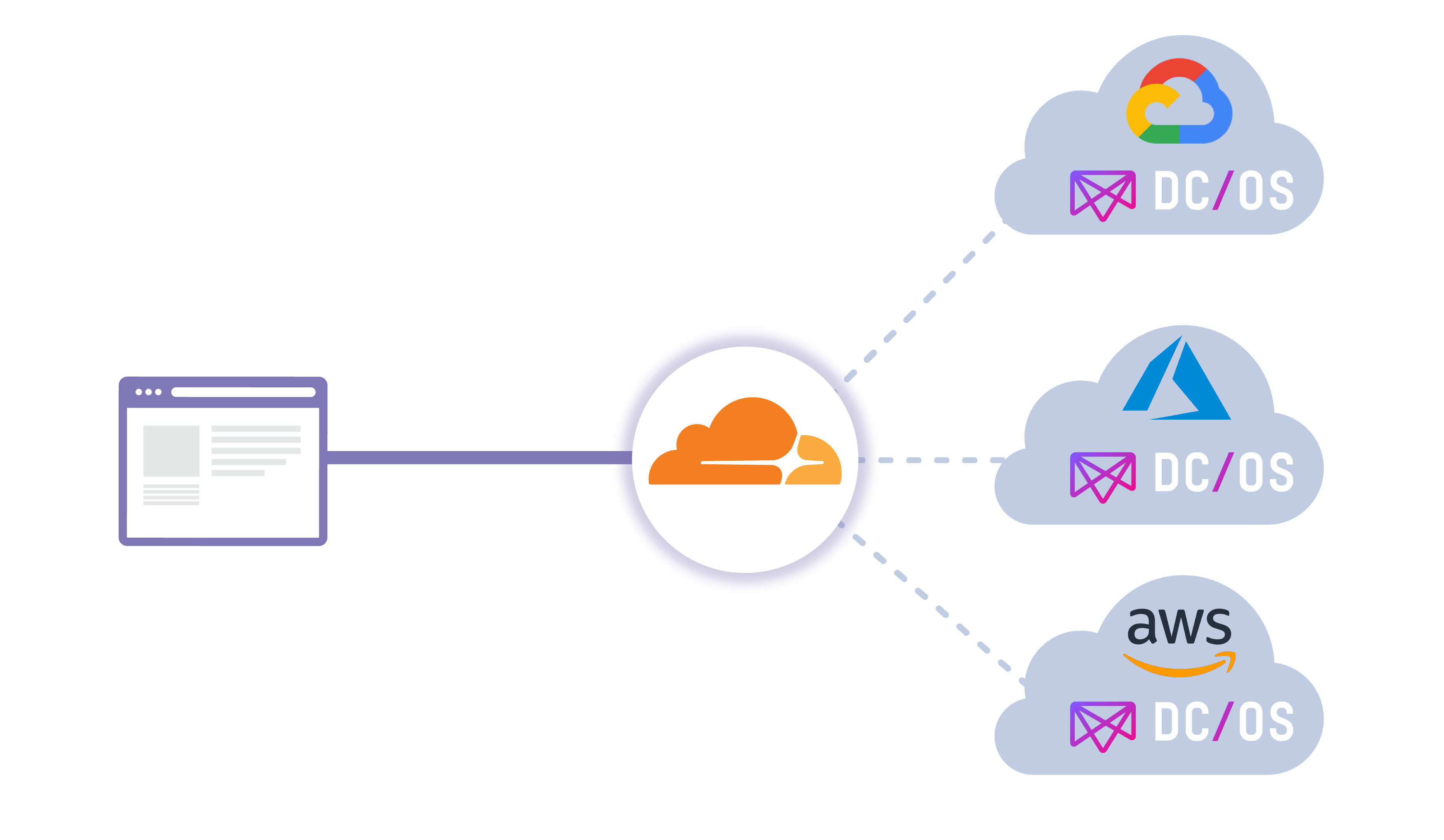
Cloudflare is proud to partner with Mesosphere on their new Argo Tunnel offering available within their DC/OS (Data Center / Operating System) catalogue! Before diving deeper into the offering itself, we’ll first do a quick overview of the Mesophere platform, DC/OS.
What is Mesosphere and DC/OS?
Mesosphere DC/OS provides application developers and operators an easy way to consistently deploy and run applications and data services on cloud providers and on-premise infrastructure. The unified developer and operator experience across clouds makes it easy to realize use cases like global reach, resource expansion, and business continuity.
In this multi cloud world Cloudflare and Mesosphere DC/OS are great complements. Mesosphere DC/OS provides the same common services experience for developers and operators, and Cloudflare provides the same common service access experience across cloud providers. DC/OS helps tremendously for avoiding vendor lock-in to a single provider, while Cloudflare can load balance traffic intelligently (in addition to many other services) at the edge between providers. This new offering will allow you to load balance through the use of Argo Tunnel.
Quick Tunnel Refresh
Cloudflare Argo Tunnel is a private connection between your services and Cloudflare. Tunnel makes it such that only traffic that routes through the Continue reading
Exporting Flow to multiple servers (Flow Samplicators)
The post Exporting Flow to multiple servers (Flow Samplicators) appeared first on Noction.
Can a Hybrid Cloud Strategy Boost IT Transformation Adoption?
Breaking out of old perceptions about the role of IT departments be the key to being part of companies' overall digital transformation strategies.
QNA: How could an EIGRP Stuck In Active event ever happen in real life?

War stories on EIGRP Stuck In Active.
The post QNA: How could an EIGRP Stuck In Active event ever happen in real life? appeared first on EtherealMind.
Continuous Integration in Network Automation
In the first part of his interview with Christoph Jaggi Kristian Larsson talked about the basics of CI testing. Now let’s see how you can use these concepts in network automation (and you’ll learn way more in Kristian’s talk on April 9th… if you register for our network automation course).
How does CI testing fit into an overall testing environment?
Traditionally, in particular in the networking industry, it's been rather common to have proof of concepts (POC) delivered by vendors for various networking technologies and then people have sat down and manually tested that the POC meets some set of requirements.
Read more ...New Year, New Home
We have left the Bay Area, and headed North. We have moved to the Greater Seattle area - specifically the Eastside, between Bellevue and Redmond. We’ve given up the old apartment in San Francisco for a larger, nicer house…for a lot less in rent. A lot fewer bars & restaurants, a lot more trees, parks and lakes.
But Why?
The typical Bay Areas response is: “But why??? It rains all the time in the Pacific Northwest!!!!”
A few things:
1. Yes, it rains more here than San Francisco, but not as much as people think. It’s not even in the top 10 cities in the US for annual rainfall. Boston, New York, Washington DC all receive more.
2. Rain is OK. In fact rain is good. You don’t get lush forests through irrigation. You also don’t get clean streets just from street sweepers.
The main attractions for us are:
-
Much better lifestyle for us. It’s easy to go mountain biking, running, hiking, skiing here.
-
Much lower rent. Yes, rents have gone up a lot here, but it’s still much better value than San Francisco. I pay much less rent here, but I get a nice place, and the Continue reading
New Year, New Home
We have left the Bay Area, and headed North. We have moved to the Greater Seattle area - specifically the Eastside, between Bellevue and Redmond. We’ve given up the old apartment in San Francisco for a larger, nicer house…for a lot less in rent. A lot fewer bars & restaurants, a lot more trees, parks and lakes.
But Why?
The typical Bay Areas response is: “But why??? It rains all the time in the Pacific Northwest!!!!”
A few things:
1. Yes, it rains more here than San Francisco, but not as much as people think. It’s not even in the top 10 cities in the US for annual rainfall. Boston, New York, Washington DC all receive more.
2. Rain is OK. In fact rain is good. You don’t get lush forests through irrigation. You also don’t get clean streets just from street sweepers.
The main attractions for us are:
-
Much better lifestyle for us. It’s easy to go mountain biking, running, hiking, skiing here.
-
Much lower rent. Yes, rents have gone up a lot here, but it’s still much better value than San Francisco. I pay much less rent here, but I get a nice place, and the Continue reading
New Year, New Home
We have left the Bay Area, and headed North. We have moved to the Greater Seattle area - specifically the Eastside, between Bellevue and Redmond. We’ve given up the old apartment in San Francisco for a larger, nicer house…for a lot less in rent. A lot fewer bars & restaurants, a lot more trees, parks and lakes.
But Why?
The typical Bay Areas response is: “But why??? It rains all the time in the Pacific Northwest!!!!”
A few things:
1. Yes, it rains more here than San Francisco, but not as much as people think. It’s not even in the top 10 cities in the US for annual rainfall. Boston, New York, Washington DC all receive more.
2. Rain is OK. In fact rain is good. You don’t get lush forests through irrigation. You also don’t get clean streets just from street sweepers.
The main attractions for us are:
-
Much better lifestyle for us. It’s easy to go mountain biking, running, hiking, skiing here.
-
Much lower rent. Yes, rents have gone up a lot here, but it’s still much better value than San Francisco. I pay much less rent here, but I get a nice place, and the Continue reading
Docker and Netdata – Awesome for Monitoring our home servers !
I don’t belong to any DevOps space but I keep hearing things like Docker / kubernetes and what not. I Quickly wanted to see what these are capable of and if I can use them to my advantage so that later I can see the use case for networking.
Docker so far seems to be far more capable and am enjoying it. Thanks to one of my friends who suggested this wonderful Repo, monitoring my server has been more granular.
I will have a detailed post on Juniper MX image via docker but for now, I have used it for something out of networking space to serve a small purpose.
https://github.com/netdata/netdata
This what Netdata UI looks like while monitoring my server, this is really wonderful as for the long time I was trying to implement many Monitoring systems and most of them required some dedicated hardware or at least a Vmware spin-off instance, which is fine for me I suppose but I wanted something small and yet effective.
Netdata operates on port 19999 of localhost and should be reachable via any web-browser.
I made a small cronjob which starts this instance on every reboot.
Installation is pretty straight forward, Continue reading
Google Dominates CNCF Code Commits, Stackalytics Says
 The Stackalytics numbers show that Google was the source of nearly 53 percent of all code commits, which was seven-times more than the second largest contributor, Red Hat.
The Stackalytics numbers show that Google was the source of nearly 53 percent of all code commits, which was seven-times more than the second largest contributor, Red Hat.
SDxCentral Weekly Wrap: Vodafone, IBM Launch $550 Million Multi-Cloud Joint Venture
 SDxCentral Weekly Wrap for January 18, 2019: Vodafone and IBM launch a multi-cloud joint venture, and AWS buys TSO Logic to help customers decide where to best run workloads.
SDxCentral Weekly Wrap for January 18, 2019: Vodafone and IBM launch a multi-cloud joint venture, and AWS buys TSO Logic to help customers decide where to best run workloads.
Weekend Reads 011819
Your job search can feel like a movie you’ve seen over and over. The same thing seems to happen every time. You get motivated to finally start looking for a new job. You hunt around the internet and make a list of intriguing jobs. You start imagining yourself getting out of your current job. You start applying, there’s progress, you get some call backs, maybe you even go on-site to interview a few times. There’s a Continue reading
T-Mobile Lures Former Ericsson CTO to Head Its 5G Strategy
 Former Ericsson executive Ulf Ewaldsson is joining T-Mobile US’ network operations where he will serve under current T-Mobile CTO Neville Ray. A former colleague at Ericsson is also on the move.
Former Ericsson executive Ulf Ewaldsson is joining T-Mobile US’ network operations where he will serve under current T-Mobile CTO Neville Ray. A former colleague at Ericsson is also on the move.
Microsoft Adds AzureDevOps Bug Bounty, Offers $20K Rewards
 This isn’t Microsoft’s first bounty program. Its largest reward offers up to $250,000 for finding critical flaws in its Hyper-V hypervisor.
This isn’t Microsoft’s first bounty program. Its largest reward offers up to $250,000 for finding critical flaws in its Hyper-V hypervisor.
SDxCentral’s Weekly Roundup — January 18, 2019
 ZTE releases a cybersecurity statement; Microsoft wins $1.76M contract with the DoD; CenturyLink opens security center in Singapore.
ZTE releases a cybersecurity statement; Microsoft wins $1.76M contract with the DoD; CenturyLink opens security center in Singapore.

