Juniper To The Enterprise: We’re Serious About Campus Networking
Juniper's latest product announcements are a signal that it's serious about campus networking. But the company has to make up ground in wireless and SD-WAN.Delivering a Serverless API in 10 minutes using Workers
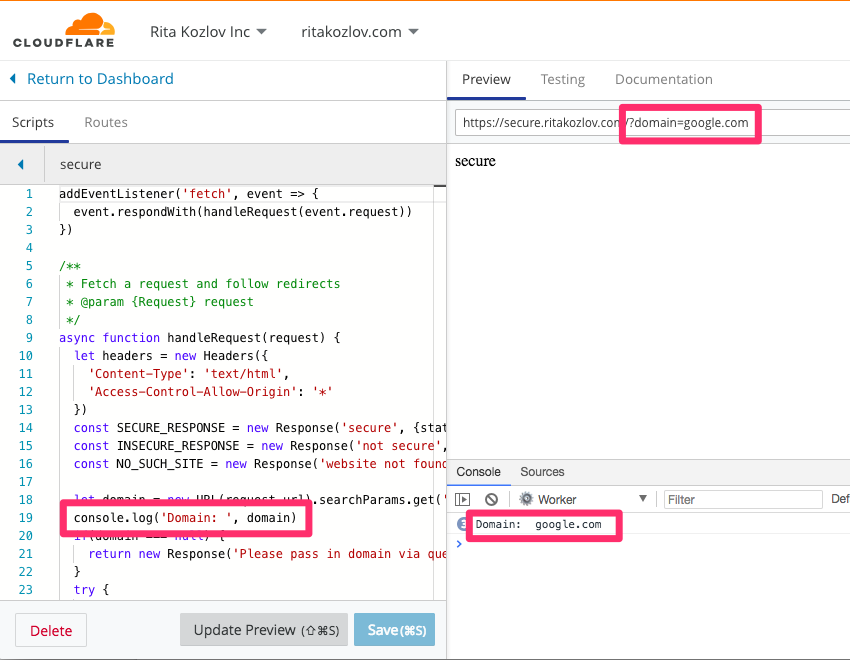
In preparation for Chrome’s Not Secure flag, which will update the indicator to show Not Secure when a site is not accessed over https, we wanted people to be able to test whether their site would pass. If you read our previous blog post about the existing misconceptions around using https, and preparing your site, you may have noticed a small fiddle, allowing you to test which sites will be deemed “Secure”. In preparation for the blog post itself, one of our PMs approached me asking for help making this fiddle come to life. It was a simple ask: we need an endpoint which runs logic to see if a given domain will automatically redirect to https.
The logic and requirements turned out to be very simple:
Make a serverless API endpoint
Input: domain (e.g. example.com)
Output: “secure” / “not secure”
Logic:
if http://example.com redirects to https://example.com
Return “secure”
Else
Return “not secure”
One additional requirement here was that we needed to follow redirects all the way; sites often redirect to http://www.example.com first, and only then redirect to https. That is an additional line of code I was prepared to handle.
I’ve done some Continue reading
O-RAN Alliance Snares 7 New Operator Members
 AT&T’s Andre Fuetsch will head the group’s board, which is made up of delegates from 12 operators.
AT&T’s Andre Fuetsch will head the group’s board, which is made up of delegates from 12 operators.
New Report Details Future Disruptions of Edge Computing
 The report includes a glossary of edge computing terms and definitions that is being funneled into The Linux Foundation.
The report includes a glossary of edge computing terms and definitions that is being funneled into The Linux Foundation.
3 people passed CCDE Practical/Lab exam on February 2018 from my class
3 people sent me their feedbacks after they pass February 2018 CCDE Practical/Lab exam. Exam result was announced on May 2018 (2 to 3 months after according to new CCDE Practical exam result policy) but I couldn’t find a chance to share their results on the website. I can’t count anymore how […]
The post 3 people passed CCDE Practical/Lab exam on February 2018 from my class appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
3 people passed CCDE Practical/Lab exam on February 2018 from my class
3 people sent me their feedbacks after they pass February 2018 CCDE Practical/Lab exam. Exam result was announced on May 2018 (2 to 3 months after according to new CCDE Practical exam result policy) but I couldn’t find a chance to share their results on the website. I can’t count anymore how …
Continue reading "3 people passed CCDE Practical/Lab exam on February 2018 from my class"
The post 3 people passed CCDE Practical/Lab exam on February 2018 from my class appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
3 people passed CCDE Practical/Lab exam on February 2018 from my class
3 people sent me their feedbacks after they pass February 2018 CCDE Practical/Lab exam. Exam result was announced on May 2018 (2 to 3 months after according to new CCDE Practical exam result policy) but I couldn’t find a chance to share their results on the website. I can’t count anymore how …
Continue reading "3 people passed CCDE Practical/Lab exam on February 2018 from my class"
The post 3 people passed CCDE Practical/Lab exam on February 2018 from my class appeared first on Cisco Network Design and Architecture | CCDE Bootcamp | orhanergun.net.
Jask Raises $25M Series B Funding for Autonomous Security Platform
 This brings its total to $39 million. Kleiner Perkins led the funding round with participation from Battery Ventures, Dell Technologies Capital, TenEleven Ventures, and Vertical Venture Partners.
This brings its total to $39 million. Kleiner Perkins led the funding round with participation from Battery Ventures, Dell Technologies Capital, TenEleven Ventures, and Vertical Venture Partners.
Ciena’s Blue Planet Dynamically Connects to a Variety of Clouds
 The company’s SDN technology was chosen by CoreSite Realty to help its customers connect to public and private clouds and to adjust bandwidth as needed.
The company’s SDN technology was chosen by CoreSite Realty to help its customers connect to public and private clouds and to adjust bandwidth as needed.
Codefresh Kubernetes-Native CI/CD Platform Lures Microsoft Cash
 The company's platform helps developers to automate their application deployment to Kubernetes in as little as 10 minutes and is more Kubernetes-centric than Spinnaker.
The company's platform helps developers to automate their application deployment to Kubernetes in as little as 10 minutes and is more Kubernetes-centric than Spinnaker.
NSX Cloud Blog Series Part 2: A Consistent Security Posture Across Your Hybrid Cloud
We now dig deeper into the cloud security use-case. As more and more companies embrace cloud, the cloud IT teams are tasked with the responsibility of ensuring that these cloud deployments are secure. Cloud inherently brings in new environments, and these cloud security teams are now faced with ensuring Enterprise security policy consistency across these multiple disparate cloud environments.
VMware NSX Cloud addresses these challenges, offering a common security and micro-segmentation platform across the on-premises and cloud environment. Together with NSX Data Center, it provides a single pane of glass to provision and manages consistent security controls not only for cross-cloud communication but also within each cloud.
Let’s start with VISIBILITY. You can’t protect what you can’t see. As a cloud infrastructure/security team, you may have to manage 1 AWS cloud account (subscription in Azure) and 1 AWS VPC (VNET in Azure) … or you may be managing 500+ accounts/subscriptions, each having multiple VPCs / VNETs. As cloud deployments bring automation and higher levels of agility, the cloud footprint that you would be responsible for can quickly become large and constantly evolve. How do you ensure that this dynamic environment is secure?
Focused on this specific Continue reading
T-25 days until Chrome starts flagging HTTP sites as “Not Secure”
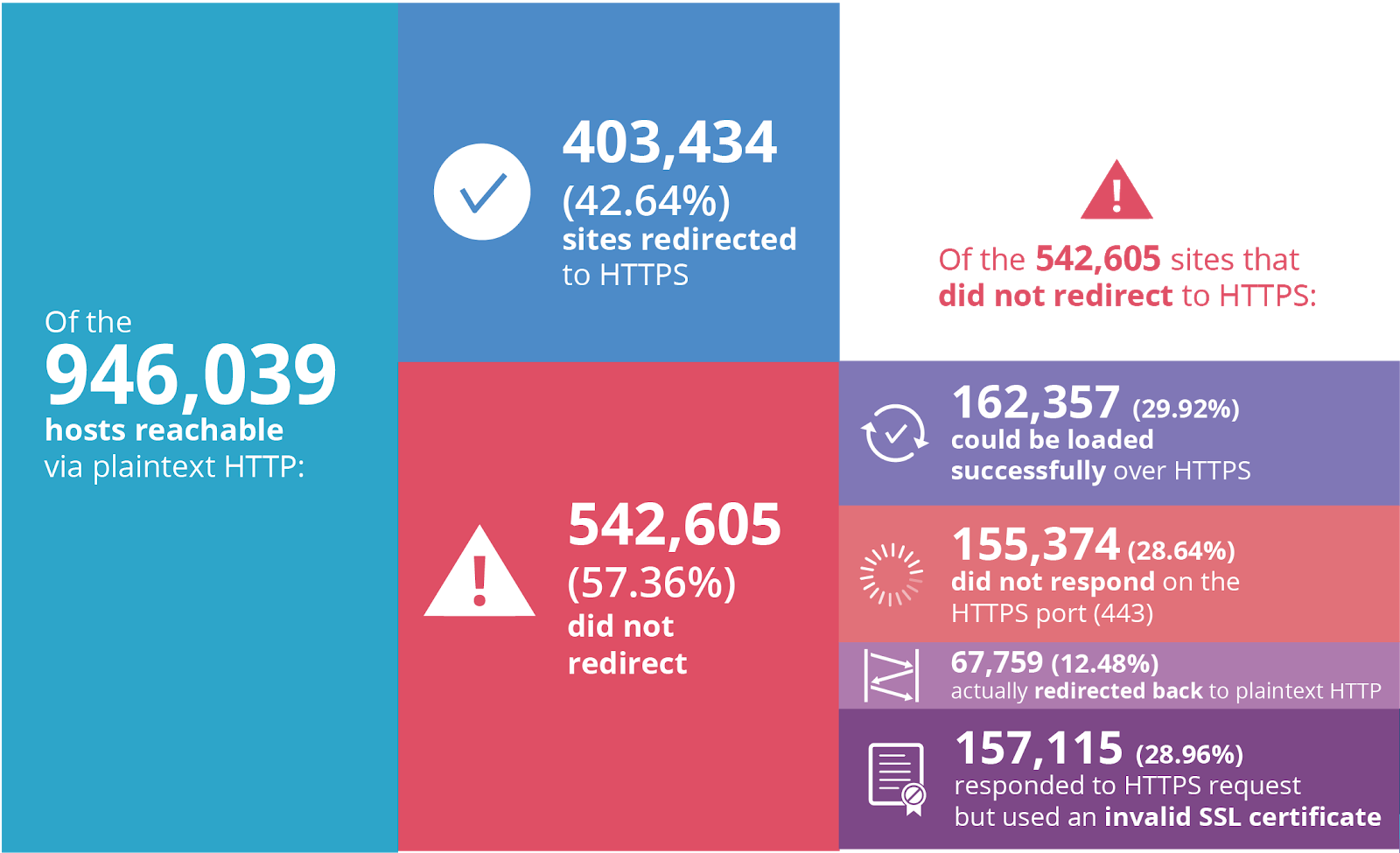
Less than one month from today, on July 23, Google will start prominently labeling any site loaded in Chrome without HTTPS as "Not Secure".
When we wrote about Google’s plans back in February, the percent of sites loaded over HTTPS clocked in at 69.7%. Just one year prior to that only 52.5% of sites were loaded using SSL/TLS—the encryption protocol behind HTTPS—so tremendous progress has been made.
Unfortunately, quite a few Continue reading
