Join our upcoming live roadshow series: ‘Zero Trust, Zero Nonsense’


Many companies now believe that Zero Trust is the answer to common perimeter network infrastructure problems. But they sometimes struggle to make the progress they’d like, frequently pushing adoption timelines back.
The most common reason we hear from our customers is: “We aren’t sure how to get started.” There’s a lot of Zero Trust talk in the market, but comparatively little substance — leading to uncertainty about how to proceed.
Businesses need a strategy for tackling Zero Trust adoption and security modernization one step at a time. Cloudflare wants to help. So we’re hosting in-person discussions with security and IT leaders to do just that.
We’re hosting a series of Zero Trust Roadshows in various North American cities. These events will feature Cloudflare executives, industry experts, and other organizations like yours, and focus on ways of breaking the Zero Trust roadmap into manageable pieces, allowing organizations to make steps towards:
- Augmenting (or replacing) a VPN: Provide simple, secure access to resources and maintain a great employee experience, while mitigating risk of lateral movement—a favorite hacker and ransomware tactic.
- Streamlining SaaS security: Empower IT with the visibility and controls of SaaS apps and email they deserve to better care for Continue reading
Take Our SD-WAN and SASE Survey
Take our SASE and SD-WAN survey to help identify industry issues as these services become more common.Supporting next level IXP topologies
Netlab 1.4 sneak preview (unofficial)

Imagine you are an IXP deploying technologies like RFC9161 EVPN with proxy ARP and MPLS over RSVP-TE, and you need to come up with a validated multi-vendor design. How would you go about that?
The Netlab team has got you covered. Check out this example — a sneak preview with upcoming Netlab 1.4 features (work in progress)
- S1/S2 are data center routers doing EVPN/VXLAN with proxy ARP; iBGP control plane and ISIS IGP. Anycast gateways are available in the ‘red-hot’ vlan
- C1/C2 are core nodes doing SRv6 over ISIS (one might call this BGP-Free :)
- PE1/PE2 are MPLS core nodes doing MPLS EVPN over LDP, with OSPF
netlab up
…is all it takes to bring this topology to life!



Bringing the best live video experience to Cloudflare Stream with AV1


Consumer hardware is pushing the limits of consumers’ bandwidth.
VR headsets support 5760 x 3840 resolution — 22.1 million pixels per frame of video. Nearly all new TVs and smartphones sold today now support 4K — 8.8 million pixels per frame. It’s now normal for most people on a subway to be casually streaming video on their phone, even as they pass through a tunnel. People expect all of this to just work, and get frustrated when it doesn’t.
Consumer Internet bandwidth hasn’t kept up. Even advanced mobile carriers still limit streaming video resolution to prevent network congestion. Many mobile users still have to monitor and limit their mobile data usage. Higher Internet speeds require expensive infrastructure upgrades, and 30% of Americans still say they often have problems simply connecting to the Internet at home.
We talk to developers every day who are pushing up against these limits, trying to deliver the highest quality streaming video without buffering or jitter, challenged by viewers’ expectations and bandwidth. Developers building live video experiences hit these limits the hardest — buffering doesn’t just delay video playback, it can cause the viewer to get out of sync with the live event. Buffering Continue reading
Day Two Cloud 166: VMware: How Multi-Cloud Services Address Cloud Complexity (Sponsored)
Multi-cloud services are an emerging category of software designed to make your Dev and Ops teams' multi-cloud reality easier to cope with. Sponsor VMware stops by the Day Two Cloud podcast to talk about how the operational challenges of running workloads in a mix of public and private clouds and how its multi-cloud services initiative can help.
The post Day Two Cloud 166: VMware: How Multi-Cloud Services Address Cloud Complexity (Sponsored) appeared first on Packet Pushers.
Day Two Cloud 166: VMware: How Multi-Cloud Services Address Cloud Complexity (Sponsored)
Multi-cloud services are an emerging category of software designed to make your Dev and Ops teams' multi-cloud reality easier to cope with. Sponsor VMware stops by the Day Two Cloud podcast to talk about how the operational challenges of running workloads in a mix of public and private clouds and how its multi-cloud services initiative can help.Tech Bytes: Juniper Integrates SD-WAN, AI Ops To Solve WAN Challenges (Sponsored)
On today's Tech Bytes podcast we talk with sponsor Juniper Networks about its AI-driven SD-WAN. While SD-WAN solves a number of problems for network engineers, it also introduces new ones: more site links, more link types, more paths, more ISPs, and more apps, all of which means more data. The Mist AI integration with SD-WAN looks for network anomalies that could lead to problems, and can often fix those problems automatically.
The post Tech Bytes: Juniper Integrates SD-WAN, AI Ops To Solve WAN Challenges (Sponsored) appeared first on Packet Pushers.
Tech Bytes: Juniper Integrates SD-WAN, AI Ops To Solve WAN Challenges (Sponsored)
On today's Tech Bytes podcast we talk with sponsor Juniper Networks about its AI-driven SD-WAN. While SD-WAN solves a number of problems for network engineers, it also introduces new ones: more site links, more link types, more paths, more ISPs, and more apps, all of which means more data. The Mist AI integration with SD-WAN looks for network anomalies that could lead to problems, and can often fix those problems automatically.Who Needs a Network Digital Twin and Why
Organizations with hybrid, multi-cloud environments that require many operators across disciplines will reap the greatest rewards today from using a digital twin.HS033 Getting real about LEO Space Networking
Should LEO space networks be part of your network ? Are there common questions about using and designing for them ? What should be expecting from your telco ?
The post HS033 Getting real about LEO Space Networking appeared first on Packet Pushers.
HS033 Getting real about LEO Space Networking
Should LEO space networks be part of your network ? Are there common questions about using and designing for them ? What should be expecting from your telco ?EVPN/MPLS Bridging Forwarding Model
Most networking engineers immediately think about VXLAN and data center switches when they hear about EVPN. While that’s the most hyped use case, EVPN standardization started in 2012 as a layer-2 VPN solution on top of MPLS transport trying to merge the best of VPLS and MPLS/VPN worlds.
If you want to understand how any technology works, and what its quirks are, you have to know how it was designed to be used. In this blog post we’ll start that journey exploring the basics of EVPN used in a simple MLPS network with three PE-routers:
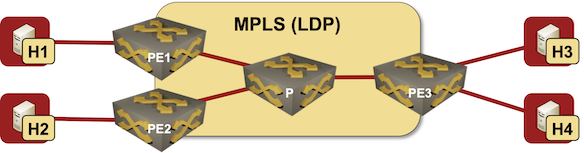
Lab topology
EVPN/MPLS Bridging Forwarding Model
Most networking engineers immediately think about VXLAN and data center switches when they hear about EVPN. While that’s the most hyped use case, EVPN standardization started in 2012 as a layer-2 VPN solution on top of MPLS transport trying to merge the best of VPLS and MPLS/VPN worlds.
If you want to understand how any technology works, and what its quirks are, you have to know how it was designed to be used. In this blog post we’ll start that journey exploring the basics of EVPN used in a simple MLPS network with three PE-routers:

Lab topology