Top 10 Trends Transforming the Cloud, According to Forrester
Hyperscalers offering composability and concerns about dependence on megavendors among the trends molding the future of the cloud.Heavy Networking 649: Cisco NSO 6.0 Boosts Performance, Improves Usability (Sponsored)
On today’s sponsored Heavy Networking we dive into new features of Cisco’s Network Services Orchestrator, or NSO. NSO is a network orchestration platform for large enterprises and service providers that offers multi-vendor automation, configuration management, service creation, ongoing monitoring and upgrades, and more.
The post Heavy Networking 649: Cisco NSO 6.0 Boosts Performance, Improves Usability (Sponsored) appeared first on Packet Pushers.
Heavy Networking 649: Cisco NSO 6.0 Boosts Performance, Improves Usability (Sponsored)
On today’s sponsored Heavy Networking we dive into new features of Cisco’s Network Services Orchestrator, or NSO. NSO is a network orchestration platform for large enterprises and service providers that offers multi-vendor automation, configuration management, service creation, ongoing monitoring and upgrades, and more.RobotFramework Debug Logs

This is a very short post, as a complement to my previous post about PyATS, Genie, and RobotFramework. How to see the debug logs of RobotFramework? I’m doing a lot of testing with RobotFramework and Genie right now. And I had a little trouble getting the right level of debugging to fix my mistakes. Here is a short and efficient way to generate a log file with RobotFramework: Just add the options -L trace and –b your_debug_file.log to have everything you need. For example: robot -d ./output -L trace…
The post RobotFramework Debug Logs appeared first on AboutNetworks.net.
Gateway + CASB: alphabetti spaghetti that spells better SaaS security
This post is also available in 简体中文 and Español.
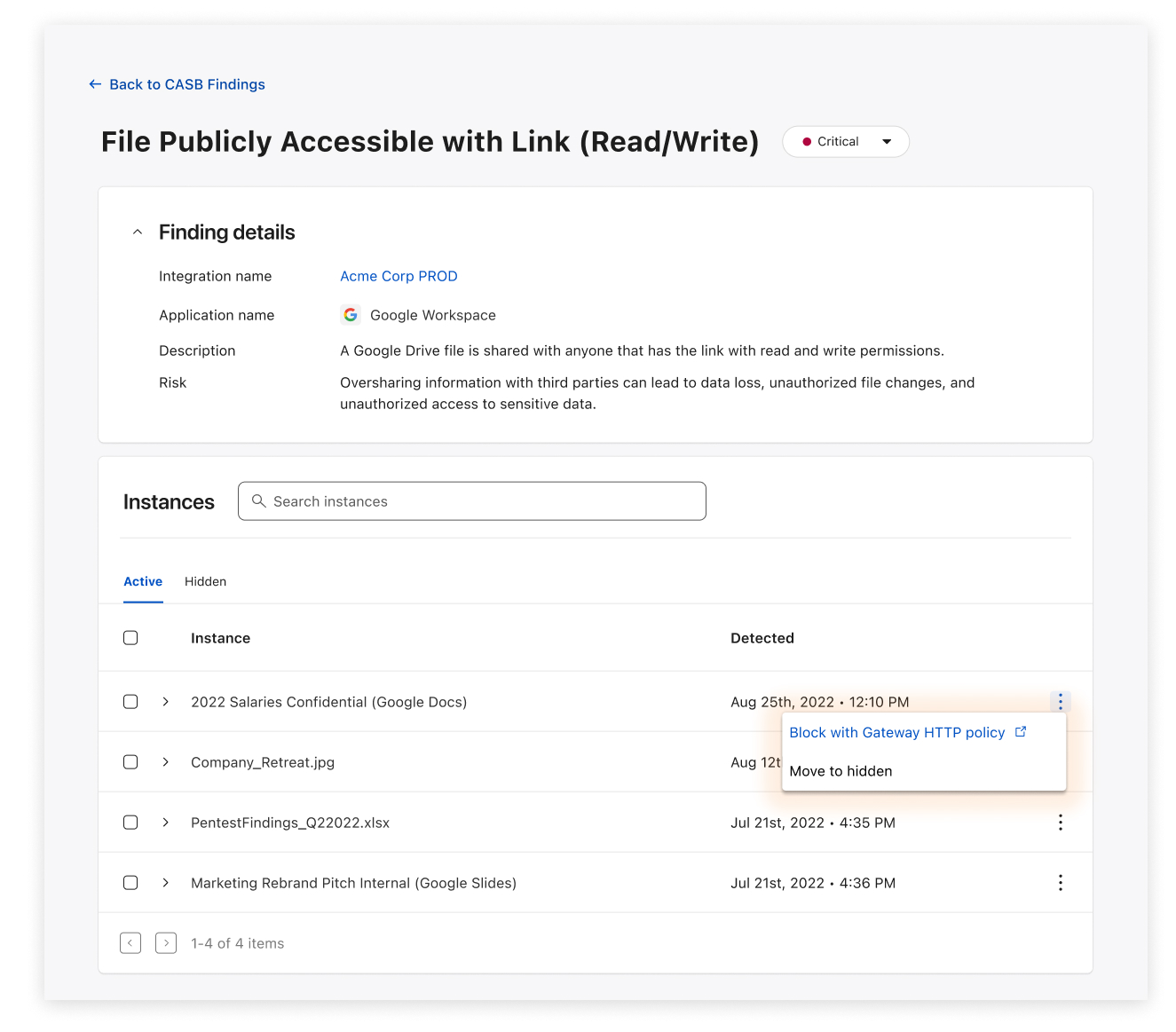
Back in June 2022, we announced an upcoming feature that would allow for Cloudflare Zero Trust users to easily create prefilled HTTP policies in Cloudflare Gateway (Cloudflare’s Secure Web Gateway solution) via issues identified by CASB, a new Cloudflare product that connects, scans, and monitors your SaaS apps - like Google Workspace and Microsoft 365 - for security issues.
With Cloudflare’s 12th Birthday Week nearing its end, we wanted to highlight, in true Cloudflare fashion, this new feature in action.
What is CASB? What is Gateway?
To quickly recap, Cloudflare’s API-driven CASB offers IT and security teams a fast, yet effective way to connect, scan, and monitor their SaaS apps for security issues, like file exposures, misconfigurations, and Shadow IT. In just a few clicks, users can see an exhaustive list of security issues that may be affecting the security of their SaaS apps, including Google Workspace, Microsoft 365, Slack, and GitHub.
Cloudflare Gateway, our Secure Web Gateway (SWG) offering, allows teams to monitor and control the outbound connections originating from endpoint devices. For example, don’t want your employees to access gambling and social media websites on company devices? Just block Continue reading
The status page the Internet needs: Cloudflare Radar Outage Center


Historically, Cloudflare has covered large-scale Internet outages with timely blog posts, such as those published for Iran, Sudan, Facebook, and Syria. While we still explore such outages on the Cloudflare blog, throughout 2022 we have ramped up our monitoring of Internet outages around the world, posting timely information about those outages to @CloudflareRadar on Twitter.
The new Cloudflare Radar Outage Center (CROC), launched today as part of Radar 2.0, is intended to be an archive of this information, organized by location, type, date, etc.
Furthermore, this initial release is also laying the groundwork for the CROC to become a first stop and key resource for civil society organizations, journalists/news media, and impacted parties to get information on, or corroboration of, reported or observed Internet outages.

What information does the CROC contain?
At launch, the CROC includes summary information about observed outage events. This information includes:
- Location: Where was the outage?
- ASN: What autonomous system experienced a disruption in connectivity?
- Type: How broad was the outage? Did connectivity fail nationwide, or at a sub-national level? Did just a single network provider have an outage?
- Scope: If it was a sub-national/regional Continue reading
The home page for Internet insights: Cloudflare Radar 2.0


Cloudflare Radar was launched two years ago to give everyone access to the Internet trends, patterns and insights Cloudflare uses to help improve our service and protect our customers.
Until then, these types of insights were only available internally at Cloudflare. However, true to our mission of helping build a better Internet, we felt everyone should be able to look behind the curtain and see the inner workings of the Internet. It’s hard to improve or understand something when you don’t have clear visibility over how it’s working.
On Cloudflare Radar you can find timely graphs and visualizations on Internet traffic, security and attacks, protocol adoption and usage, and outages that might be affecting the Internet. All of these can be narrowed down by timeframe, country, and Autonomous System (AS). You can also find interactive deep dive reports on important subjects such as DDoS and the Meris Botnet. It’s also possible to search for any domain name to see details such as SSL usage and which countries their visitors are coming from.
Since launch, Cloudflare Radar has been used by NGOs to confirm the Internet disruptions their observers see in the field, by journalists looking for Internet trends related to Continue reading
Lights, Camera, Action! Business and Pro customers get bundled streaming video


Beginning December 1, 2022, if you have a Business or Pro subscription, you will receive a complimentary allocation of Cloudflare Stream. Here’s what this means:
- All Cloudflare customers with a Biz or Pro domain will be able to store up to 100 minutes of video content and deliver up to 10,000 minutes of video content each month at no additional cost
- If you need additional storage or delivery beyond the complimentary allocation, you will be able to upgrade to a paid Stream subscription from the Stream Dashboard.
Cloudflare Stream simplifies storage, encoding and playback of videos. You can use the free allocation of Cloudflare Stream for various use cases, such as background/hero videos, e-commerce product videos, how-to guides and customer testimonials.
Upload videos with no code
To upload your first video Stream, simply visit the Stream Dashboard and drag-and-drop the video file:
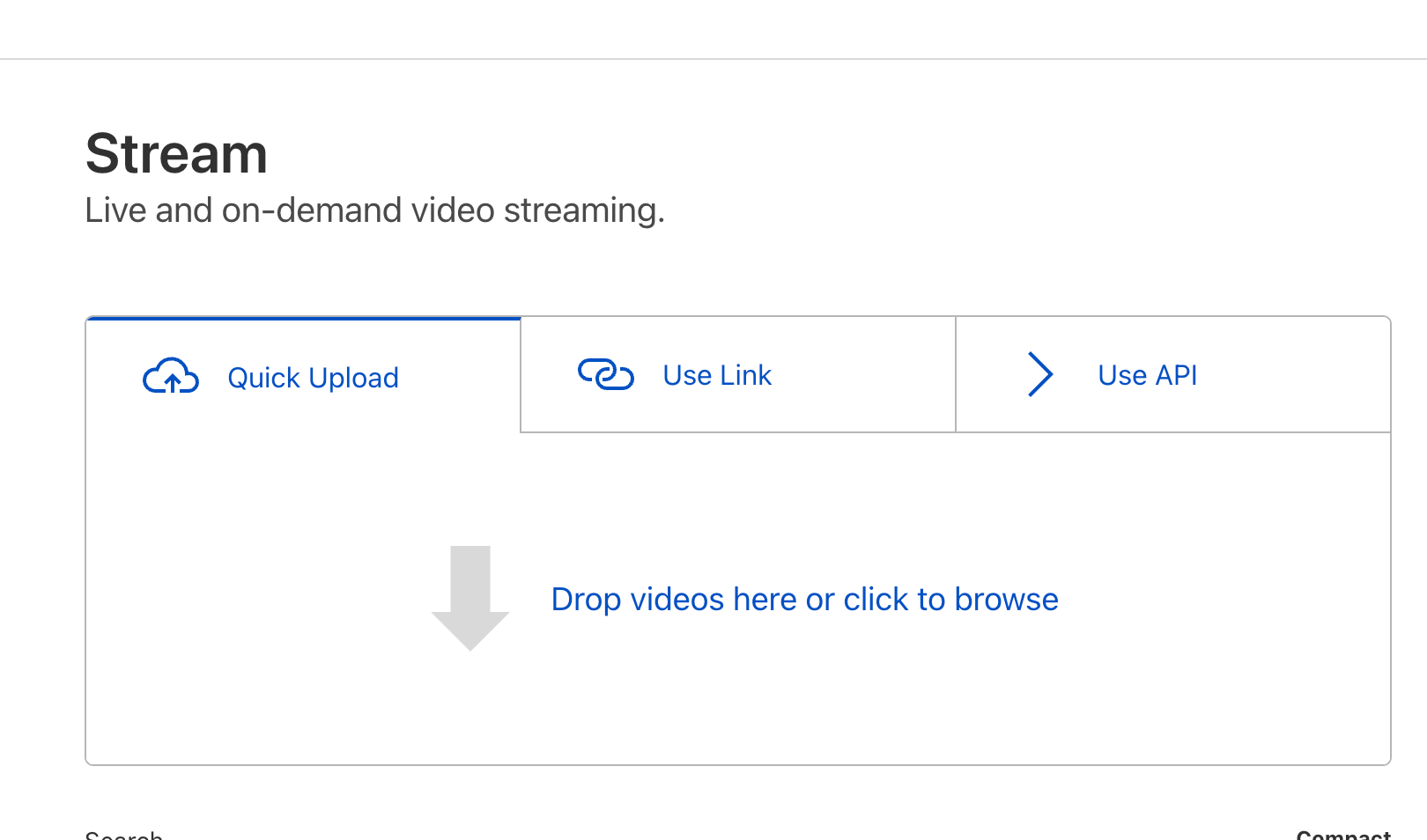
Once you upload a video, Stream will store and encode your video. Stream automatically optimizes your video uploads by creating multiple versions of it at different quality levels. This happens behind-the-scenes and requires no extra effort from your side. The Stream Player automatically selects the optimal quality level based on your website visitor’s Internet connection using a technology Continue reading
Don’t roll your own high cardinality analytics, use Workers Analytics Engine


Workers Analytics Engine (or for short, Analytics Engine) is a new way for developers to store and analyze time series analytics about anything using Cloudflare Workers, and it’s now in open beta! Analytics Engine is really good at gathering time-series data for really high cardinality and high-volume data sets from Cloudflare Workers. At Cloudflare, we use Analytics Engine to provide insight into how our customers use Cloudflare products.
Log, log, logging!
As an example, Analytics Engine is used to observe the backend that powers Instant Logs. Instant Logs allows Cloudflare customers to stream a live session of the HTTP logs for their domain to the Cloudflare dashboard. The backend for Instant Logs is built on Cloudflare Workers.
Briefly, the Instant Logs backend works by receiving requests from each Cloudflare server that processes a customer's HTTP traffic. These requests contain the HTTP logs for the customer’s HTTP traffic. The Instant Logs backend then forwards these HTTP logs to the customer’s browser via a WebSocket.
In order to ensure that the HTTP logs are being delivered smoothly to a customer's browser, we need to track the request rates across all active Instant Logs sessions. We also need to track the request rates Continue reading
Project A11Y: how we upgraded Cloudflare’s dashboard to adhere to industry accessibility standards


At Cloudflare, we believe the Internet should be accessible to everyone. And today, we’re happy to announce a more inclusive Cloudflare dashboard experience for our users with disabilities. Recent improvements mean our dashboard now adheres to industry accessibility standards, including Web Content Accessibility Guidelines (WCAG) 2.1 AA and Section 508 of the Rehabilitation Act.
Over the past several months, the Cloudflare team and our partners have been hard at work to make the Cloudflare dashboard1 as accessible as possible for every single one of our current and potential customers. This means incorporating accessibility features that comply with the latest Web Content Accessibility Guidelines (WCAG) and Section 508 of the US’s federal Rehabilitation Act. We are invested in working to meet or exceed these standards; to demonstrate that commitment and share openly about the state of accessibility on the Cloudflare dashboard, we have completed the Voluntary Product Accessibility Template (VPAT), a document used to evaluate our level of conformance today.
Conformance with a technical and legal spec is a bit abstract–but for us, accessibility simply means that as many people as possible can be successful users of the Cloudflare dashboard. This is important because each day, more and more Continue reading
Goodbye, Alexa. Hello, Cloudflare Radar Domain Rankings


The Internet is a living organism. Technology changes, shifts in human behavior, social events, intentional disruptions, and other occurrences change the Internet in unpredictable ways, even to the trained eye.
Cloudflare Radar has long been the place to visit for accessing data and getting unique insights into how people and organizations are using the Internet across the globe, as well as those unpredictable changes to the Internet.
One of the most popular features on Radar has always been the “Most Popular Domains,” with both global and country-level perspectives. Domain usage signals provide a proxy for user behavior over time and are a good representation of what people are doing on the Internet.
Today, we’re going one step further and launching a new dataset called Radar Domain Rankings (Beta). Domain Rankings is based on aggregated 1.1.1.1 resolver data that is anonymized in accordance with our privacy commitments. The dataset aims to identify the top most popular domains based on how people use the Internet globally, without tracking individuals’ Internet use.
There are a few reasons why we're doing this now. One is obviously to improve our Radar features with better data and incorporate new learnings. But also, ranking Continue reading
Video: Kubernetes Services Types
Kubernetes services are like networking standards: there are so many to choose from. In his brief introduction to Kubernetes service types, Stuart Charlton listed six of them, and I’m positive there are more. That’s what you get when you’re trying to reinvent every network load balancing method known to mankind ;)
Video: Kubernetes Services Types
Kubernetes services are like networking standards: there are so many to choose from. In his brief introduction to Kubernetes service types, Stuart Charlton listed six of them, and I’m positive there are more. That’s what you get when you’re trying to reinvent every network load balancing method known to mankind ;)
DNS Evolution: Innovation or Fragmentation?
How should we engage with evolution and innovation in the Internet’s name space? How can we evolve this name environment if we avoid fragmentation and stay within the confines of the incumbent name system? Are all that we are permitted to vary when we try to innovate in the name space are the values of the labels used within DNS names? This was never a satisfactory answer, and many actors have experimented with various forms of alternative name systems running over the Internet for many years. These efforts inevitably result in a fragmented name space. Is there a better way to respond to these conflicting pressures?Kubernetes Unpacked 010: Troubleshooting And Alerting On Kubernetes
In this episode, Michael catches up with Natan Yellin, CEO of Robusta.dev. Michael and Ned chat about how logging and troubleshooting works in Kubernetes today. They discuss three stages of troubleshooting evolution - manual playbooks, automatic playbooks, and the third stage, which is what you do with logs and how automatic remediation can come into play for any Kubernetes environment.
The post Kubernetes Unpacked 010: Troubleshooting And Alerting On Kubernetes appeared first on Packet Pushers.