Automation 12. Automated EVPN Customer Deployment with Ansible, NETCONF, and NetBox. 6WIND version.
Hello my friend,
We’ve been preparing this blogpost for quite a while, but for various reasons it was put on the back burner. Now we finally are bringing this back to light. We’ll go over a practical use case of automation of 6WIND configuration with Ansible and NetBox relying NETCONF.
2
3
4
5
retrieval system, or transmitted in any form or by any
means, electronic, mechanical or photocopying, recording,
or otherwise, for commercial purposes without the
prior permission of the author.
Do I Need to Automate Everything?
The answer is, as usual: it depends. With our passion to automation, we would say: yes, definitely you should automate everything. But this is possible, only if you have unlimited resources (time, money, people). In reality, all the resources are limited and, moreover, may be even scarce. In such a case you would need to choose, where would you obtain the biggest leverage from automation. For example, some tasks are more frequent or time consuming than others. Clearly they are to be automated.
How to find them? Join our automation training and you will find that out!
We offer the Continue reading
Worth Reading: Misconceptions about Route Origin Validation
Use the email sent by Randy Bush to RIPE routing WG mailing list every time a security researcher claims a technology with no built-in security mechanism is insecure (slightly reworded to make it more generic).
Lately, I am getting flak about $SomeTechnology not providing protection from this or that malicious attack. Indeed it does not.
Worth Reading: Misconceptions about Route Origin Validation
Use the email sent by Randy Bush to RIPE routing WG mailing list every time a security researcher claims a technology with no built-in security mechanism is insecure (slightly reworded to make it more generic).
Lately, I am getting flak about $SomeTechnology not providing protection from this or that malicious attack. Indeed it does not.
Worth Reading: AI Makes Animists of Us All
Erik Hoel published a wonderful article describing how he’s fighting the algorithm that is deciding whether to approve a charge on his credit card.
My credit card now has a kami. Such new technological kamis are, just like the ancient ones, fickle; sometimes blessing us, sometimes hindering us, and all we as unwilling animists can do is a modern ritual to the inarticulate fey creatures that control our inboxes and our mortgages and our insurance rates.
There are networking vendors unleashing similar “spirits” on our networks. Welcome to the brave new world ;)
Worth Reading: AI Makes Animists of Us All
Erik Hoel published a wonderful article describing how he’s fighting the algorithm that is deciding whether to approve a charge on his credit card.
My credit card now has a kami. Such new technological kamis are, just like the ancient ones, fickle; sometimes blessing us, sometimes hindering us, and all we as unwilling animists can do is a modern ritual to the inarticulate fey creatures that control our inboxes and our mortgages and our insurance rates.
There are networking vendors unleashing similar “spirits” on our networks. Welcome to the brave new world ;)
AI is a Promotion

When I worked at IBM as an intern, part of my job was writing a deployment script to help make our lives easier when installing new ThinkPads. In order to change an MTU setting on the token ring PCMCIA cards (long story), I had to write a script that iterated through all the possible combinations of adapters in the registry to find the one I was looking for and change the value.
Now, I was 22 at the time and green behind the ears, especially when it came to programming. I finally figured out that the most efficient way to do this in the language that I was using was a very deep nested if statement. It wasn’t my best work but it operated properly. I mentioned this to my mentors on my team with a remark of how hard it was to understand the logic at first. My comment was “You know, if it’s hard to read for anyone else then I never have to worry about gettin fired.”
To which the response was, “Yes, but you can never be promoted either.”
That sage wisdom brings me to the modern world and how AI can fix that Continue reading
Hermetic Malware: Multi-component Threat Targeting Ukraine Organizations
Contributors: Giovanni Vigna, Oleg Boyarchuk, Stefano Ortolani
Introduction
The continued assault on Ukraine will go down in history as the first one that was truly carried out both kinetically on the battlefield and virtually using cyberattacks against the computer infrastructure of the invaded nation.
As the invasion started and escalated, new malware threats were introduced by malicious actors to harm Ukrainian organizations. Early in the assault, security researchers have observed the emergence of new threats that appears to be developed ad hoc to be key tools in cyber-war efforts.
In addition to well-known attacks and threats, such as network DDoS and ransomware, these threats included “wipers,” whose sole purpose is the disabling of the targeted hosts, often combined with other tools that allow the attackers to infect the largest number of hosts possible.
While these attacks targeted specific organizations, there is a substantial risk that in the highly connected, distributed environments used to exchange and share information in multi-national organizations these attacks might spill beyond their intended targets.
It is therefore of paramount importance to understand these threats in order to help protect both Ukrainian organizations and the rest of the world. To this end, CISA has published a series Continue reading
Heavy Networking 620: High Frequency Trading And Big Data Network Design
Network design for high frequency trading and big data networks is the topic of today’s Heavy Networking. If you’re interested in what it’s like to carefully manage data center latency and maintain your sanity in a zero downtime environment, this is your show. Our guests are are Jeremy Filliben and Marc Washco of Jump Trading.
The post Heavy Networking 620: High Frequency Trading And Big Data Network Design appeared first on Packet Pushers.
Heavy Networking 620: High Frequency Trading And Big Data Network Design
Network design for high frequency trading and big data networks is the topic of today’s Heavy Networking. If you’re interested in what it’s like to carefully manage data center latency and maintain your sanity in a zero downtime environment, this is your show. Our guests are are Jeremy Filliben and Marc Washco of Jump Trading.Enterprises Need To Prepare for Broader Cyberwar
Russia has a long history of using cyberattacks against its enemies.Shields up: free Cloudflare services to improve your cyber readiness

Since our founding, Cloudflare's mission has been to "help build a better Internet," and we take it to heart. It used to be that the services required to adequately secure an online presence were only available to the largest of enterprises — organizations big enough to afford both the technology itself and the teams to manage it.
We've worked hard over the years to level the playing field. This has meant making more and more of the essential tools for protecting an online presence available to as many people as possible. Cloudflare offers unmetered DDoS protection — for free. We were the first to introduce SSL at scale — for free. And it’s not just protection for your external-facing infrastructure: we have a free Zero Trust plan that enables teams to protect their internal-facing infrastructure, too.
These types of tools have always been important for the billions of people on the Internet. But perhaps never as important as they've become this week.
Concurrent with the Russian invasion of Ukraine, we've seen increasing cyberattacks on the Internet, too. Governments around the world are encouraging organizations to go “shields up” — with warnings coming from the United States’ Cybersecurity & Infrastructure Security Continue reading
Internet traffic patterns in Ukraine since February 21, 2022
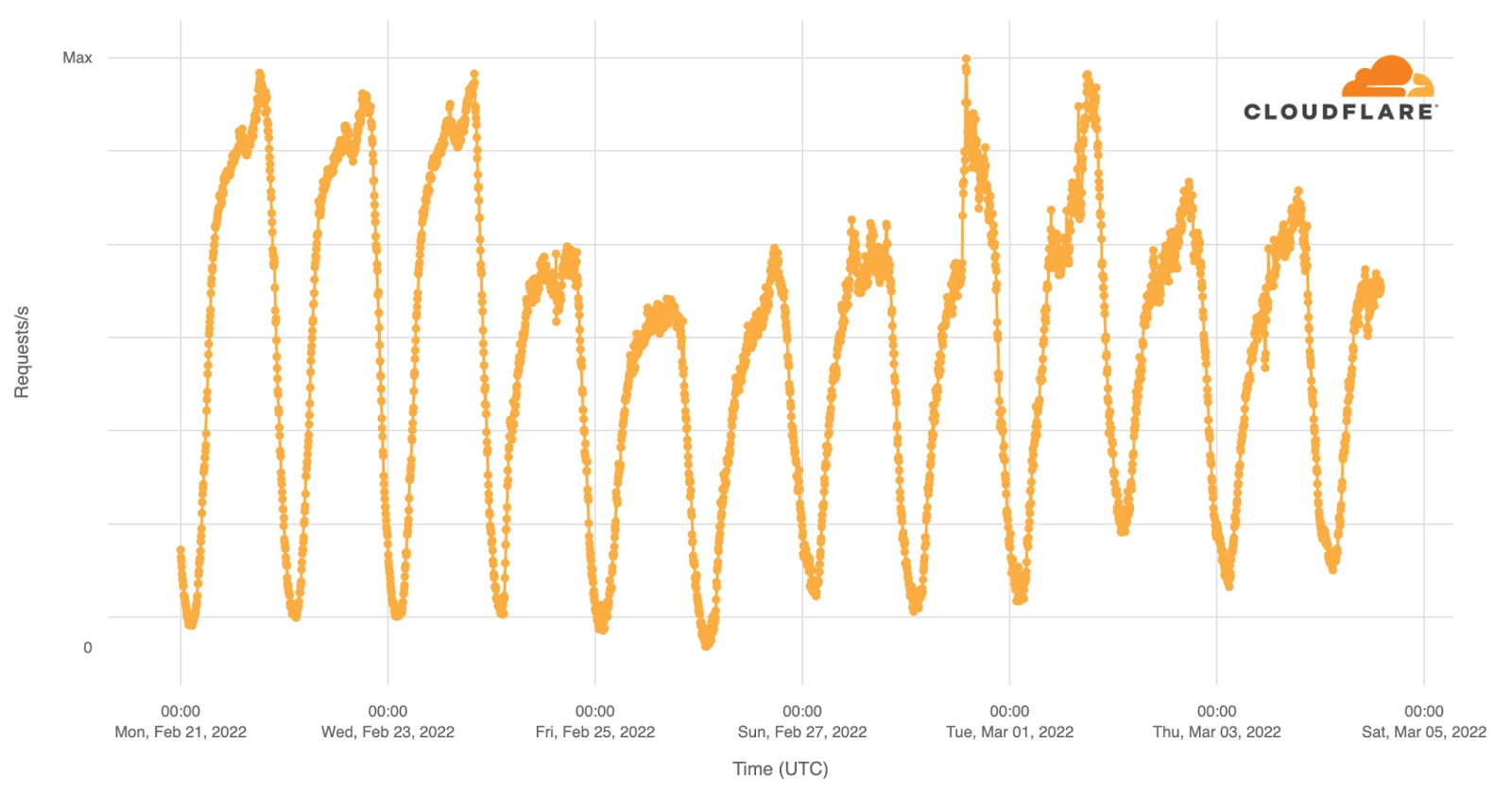
Cloudflare operates in more than 250 cities worldwide where we connect our equipment to the Internet to provide our broad range of services. We have data centers in Ukraine, Belarus and Russia and across the world. To operate our service we monitor traffic trends, performance and errors seen at each data center, aggregate data about DNS, and congestion and packet loss on Internet links.
Internet Traffic
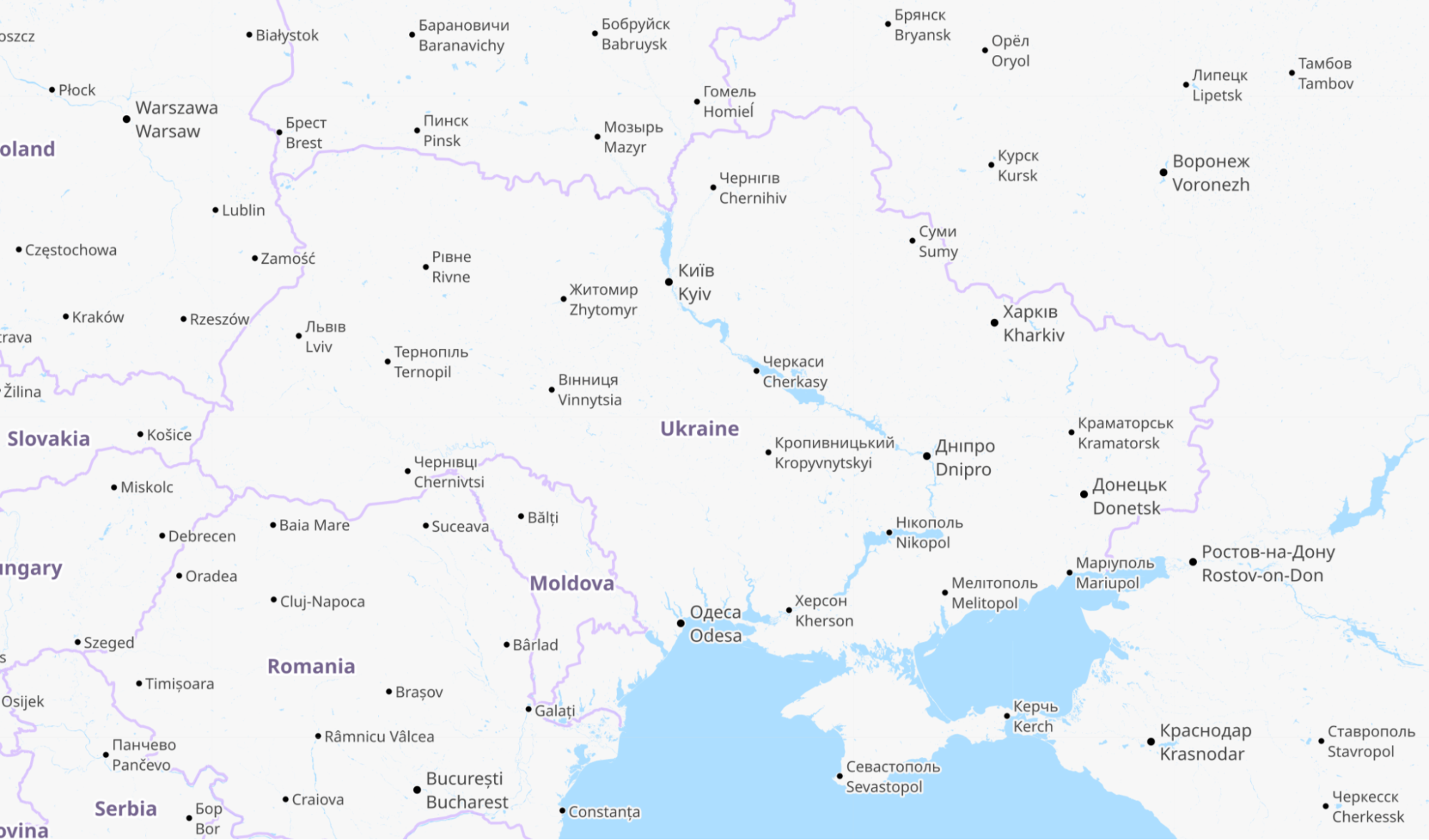
For reference, here is a map of Ukraine showing its major cities. Note that whenever we talk about dates and times in this post, we are using UTC. Ukraine’s current time zone is UTC+2.
Internet traffic in Ukraine generally follows a pretty predictable pattern based on day and night. Lowest in the hours after local midnight and picking up as people wake up. It’s not uncommon to see a dip around lunchtime and a peak when people go home in the evening. That pattern is clearly visible in this chart of overall Internet traffic seen by Cloudflare for Ukrainian networks on Monday, Tuesday, and Wednesday prior to the invasion.
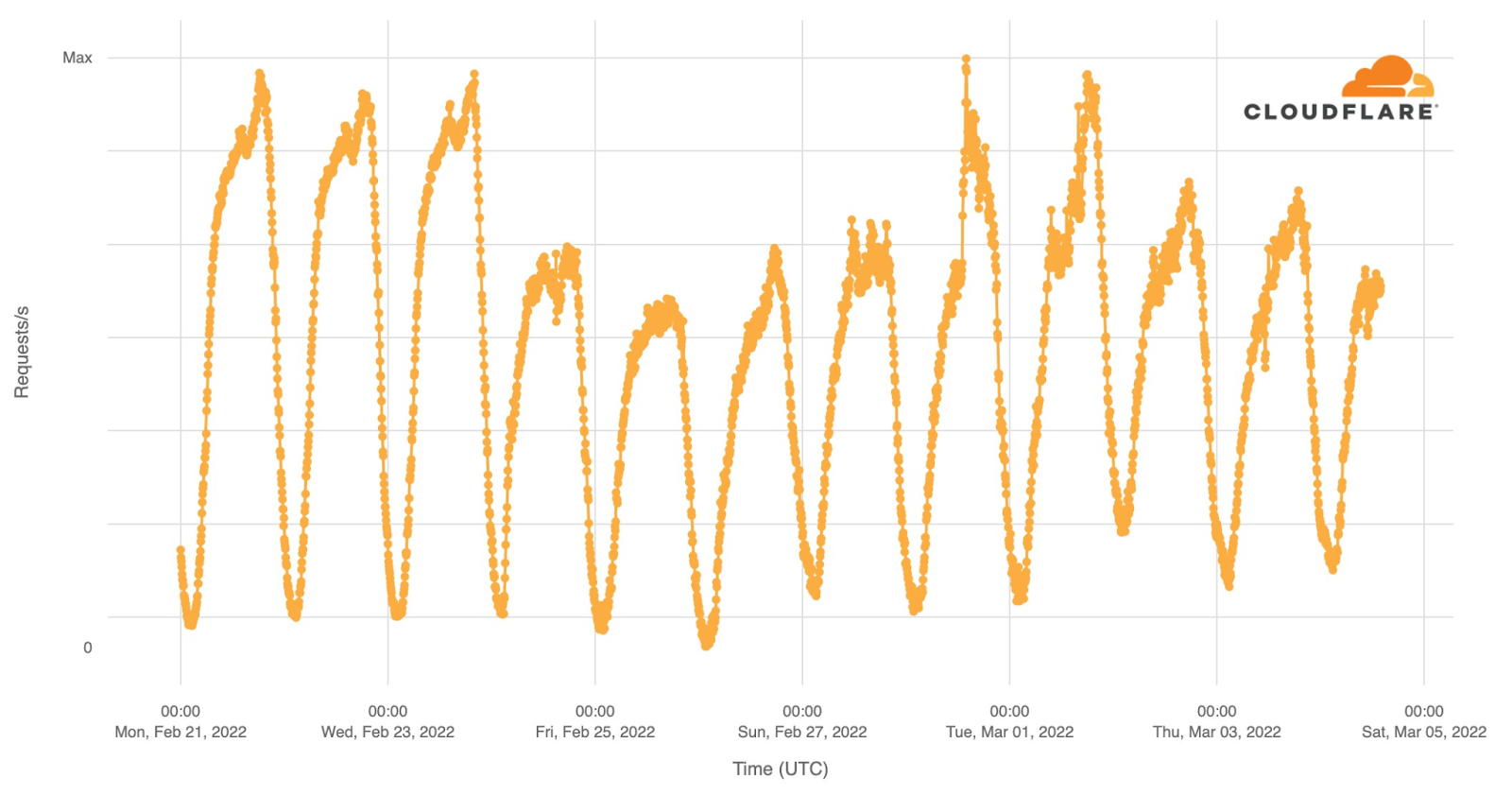
Starting Thursday, traffic was significantly lower. On Thursday, we saw about 70% of our normal request volume and about 60% on Friday. Continue reading
Video: Comparing TCP/IP and CLNP
If you were building networks in early 1990s you probably remember at least a half-dozen different network protocols. Only one of them survived (IPv6 came later), with another one (CLNP) providing an interesting view into a totally different parallel universe that evolved using a different set of fundamental principles.
After introducing the network-layer addressing, I compared the two and pointed out where one or the other was clearly better.
You might think that it makes no sense to talk about protocols that were rarely used in old days, and that are almost non-existent today, but as always those who cannot remember the past are doomed to repeat it, this time reinventing CLNP principles in IPv6-based layer-3-only data center fabrics.
Video: Comparing TCP/IP and CLNP
If you were building networks in early 1990s you probably remember at least a half-dozen different network protocols. Only one of them survived (IPv6 came later), with another one (CLNP) providing an interesting view into a totally different parallel universe that evolved using a different set of fundamental principles.
After introducing the network-layer addressing, I compared the two and pointed out where one or the other was clearly better.
You might think that it makes no sense to talk about protocols that were rarely used in old days, and that are almost non-existent today, but as always those who cannot remember the past are doomed to repeat it, this time reinventing CLNP principles in IPv6-based layer-3-only data center fabrics.