Blessay: Coin-Operated Evangelism

This article was first published in Packet Pushers Human Infrastructure Magazine. An email newsletter that talks about being a human in technology. You can subscribe, for free here. I struggle with the concept of ‘corporate evangelism’. So here are some thoughts on the topic. Religious Roots Evangelism is a religious principle that your belief is […]
The post Blessay: Coin-Operated Evangelism appeared first on EtherealMind.
Eventually Secure?

I have a Disney+ account. I have kids and I like Star Wars, so it made sense. I got it all set up the day it came out and started binge watching the Mandalorian. However, in my haste to get things up and running I reused an old password instead of practicing good hygiene. As the titular character might scold me, “This is not the way.” I didn’t think anything about it until I got a notification that someone from New Jersey logged into my account.
I panicked and reset my password like a good security person should have done in the first place. I waited for the usual complaints that people had been logged out of the app and prepared to log everyone in again and figure out how to remove my New Jersey interloper. Imagine my surprise when no one came to ask me to turn Phineas and Ferb back on. Imagine my further surprise when I looked in the app and on the Disney+ website and couldn’t find a way to see which devices were logged in to this account. Nor could I find a way to disconnect a rogue device as I could with Netflix Continue reading
Monitoring DDoS mitigation
Real-time DDoS mitigation using BGP RTBH and FlowSpec and Pushing BGP Flowspec rules to multiple routers describe how to deploy the ddos-protect application. This article focuses on how to monitor DDoS activity and control actions.The diagram shows the elements of the solution. Routers stream standard sFlow telemetry to an instance of the sFlow-RT real-time analytics engine running the ddos-protect application. The instant a DDoS attack is detected, RTBH and / or Flowspec actions are pushed via BGP to the routers to mitigate the attack. Key metrics are published using the Prometheus exporter format over HTTP and events are sent using the standard syslog protocol.
The sFlow-RT DDoS Protect dashboard, shown above, makes use of the Prometheus time series database and the Grafana metrics visualization tool to track DDoS attack mitigation actions.
The sFlow-RT Countries and Networks dashboard, shown above, breaks down traffic by origin network and country to provide an indication of the source of attacks. Flow metrics with Prometheus and Grafana describes how to build additional dashboards to provide additional insight into network traffic.
In this example, syslog events are directed to an Elasticsearch, Logstash, and Kibana (ELK) stack where they are archived, queried, and analyzed. Grafana Continue reading
Apple Dictionary Order

The right order for Apple Dictionaries in the app
The post Apple Dictionary Order appeared first on EtherealMind.
Stream Firewall Events directly to your SIEM
The highest trafficked sites using Cloudflare receive billions of requests per day. But only about 5% of those requests typically trigger security rules, whether they be “managed” rules such as our WAF and DDoS protections, or custom rules such as those configured by customers using our powerful Firewall Rules and Rate Limiting engines.
When enforcement is taken on a request that interrupts the flow of malicious traffic, a Firewall Event is logged with detail about the request including which rule triggered us to take action and what action we took, e.g., challenged or blocked outright.
Previously, if you wanted to ingest all of these events into your SIEM or logging platform, you had to take the whole firehose of requests—good and bad—and then filter them client side. If you’re paying by the log line or scaling your own storage solution, this cost can add up quickly. And if you have a security team monitoring logs, they’re being sent a lot of extraneous data to sift through before determining what needs their attention most.
As of today, customers using Cloudflare Logs can create Logpush jobs that send only Firewall Events. These events arrive much faster than our existing HTTP Continue reading
Overlay Networking with Ouroboros on Software Gone Wild
This podcast introduction was written by Nick Buraglio, the host of today’s podcast.
As private overlays are becoming more and more prevalent and as SD-WAN systems and technologies advance, it remains critical that we continue to investigate how we think about internetworking. Even with platforms such as Slack Nebula, Zerotier, or the wireguard based TailScale becoming a mainstream staple of many businesses, the question of “what is next” is being asked by an ambitious group of researchers.
Daily Roundup: Deutsche Telekom, Vodafone Embrace 5G DSS
Deutsche Telekom, Vodafone Germany embraced 5G DSS; Edgewise Networks CEO shared security-related...
AT&T Tops Managed SD-WAN Ranking, CenturyLink Surges
CenturyLink experienced the single largest gain in billable installations in 2019, according to...
Will Zero-Trust Security Stick After COVID-19?
Edgewise Networks CEO Peter Smith discusses the rapid shift to remote work because of COVID-19 and...
Deutsche Telekom, Vodafone Germany Embrace 5G DSS
The race to blanket Germany with 5G got underway last July and market leader Deutsche Telekom now...
Internet performance during the COVID-19 emergency
A month ago I wrote about changes in Internet traffic caused by the COVID-19 emergency. At the time I wrote:
Cloudflare is watching carefully as Internet traffic patterns around the world alter as people alter their daily lives through home-working, cordon sanitaire, and social distancing. None of these traffic changes raise any concern for us. Cloudflare's network is well provisioned to handle significant spikes in traffic. We have not seen, and do not anticipate, any impact on our network's performance, reliability, or security globally.
That holds true today; our network is performing as expected under increased load. Overall the Internet has shown that it was built for this: designed to handle huge changes in traffic, outages, and a changing mix of use. As we are well into April I thought it was time for an update.
Growth
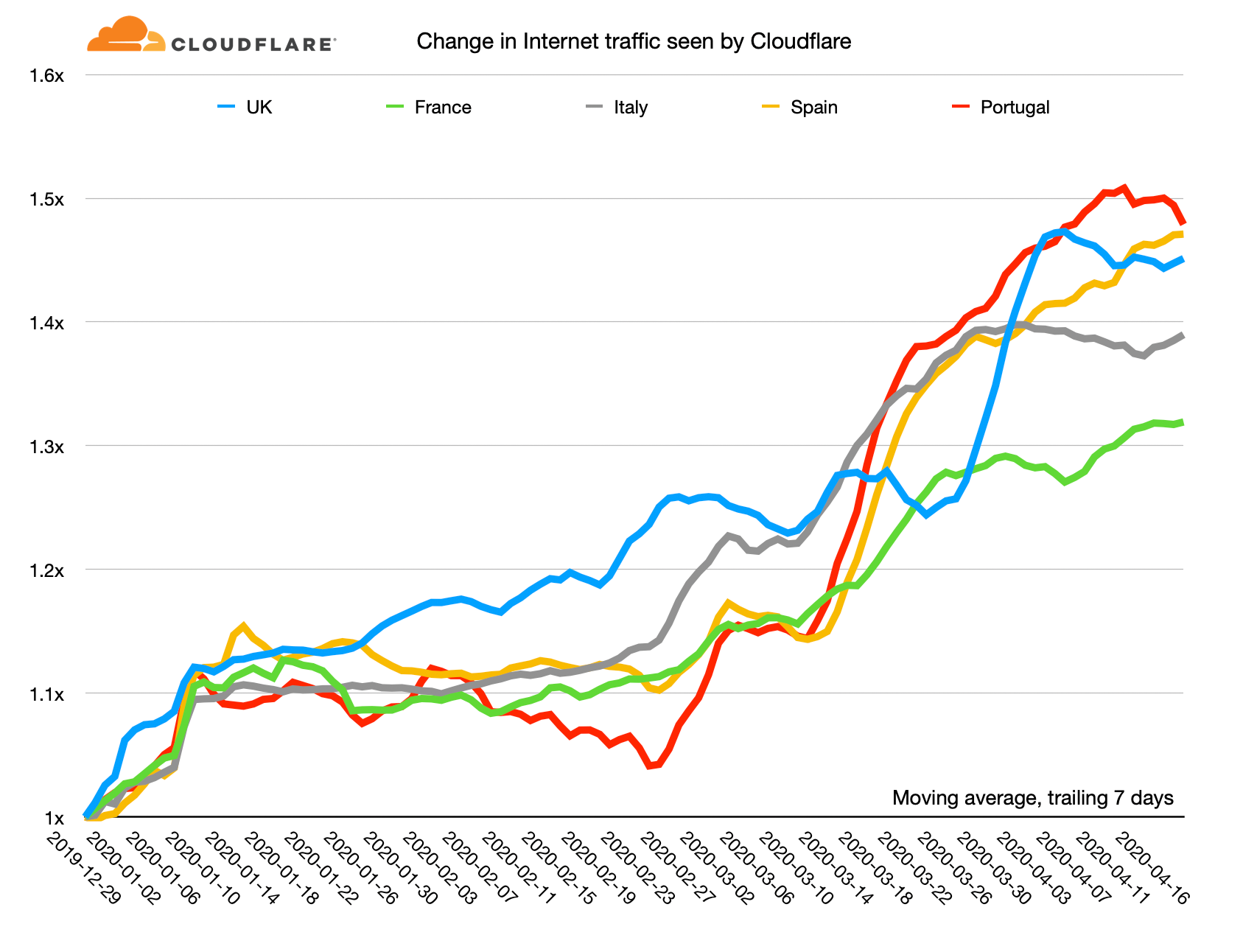
Here's a chart showing the relative change in Internet use as seen by Cloudflare since the beginning of the year. I've calculated moving average of the trailing seven days for each country and use December 29, 2019 as the reference point.
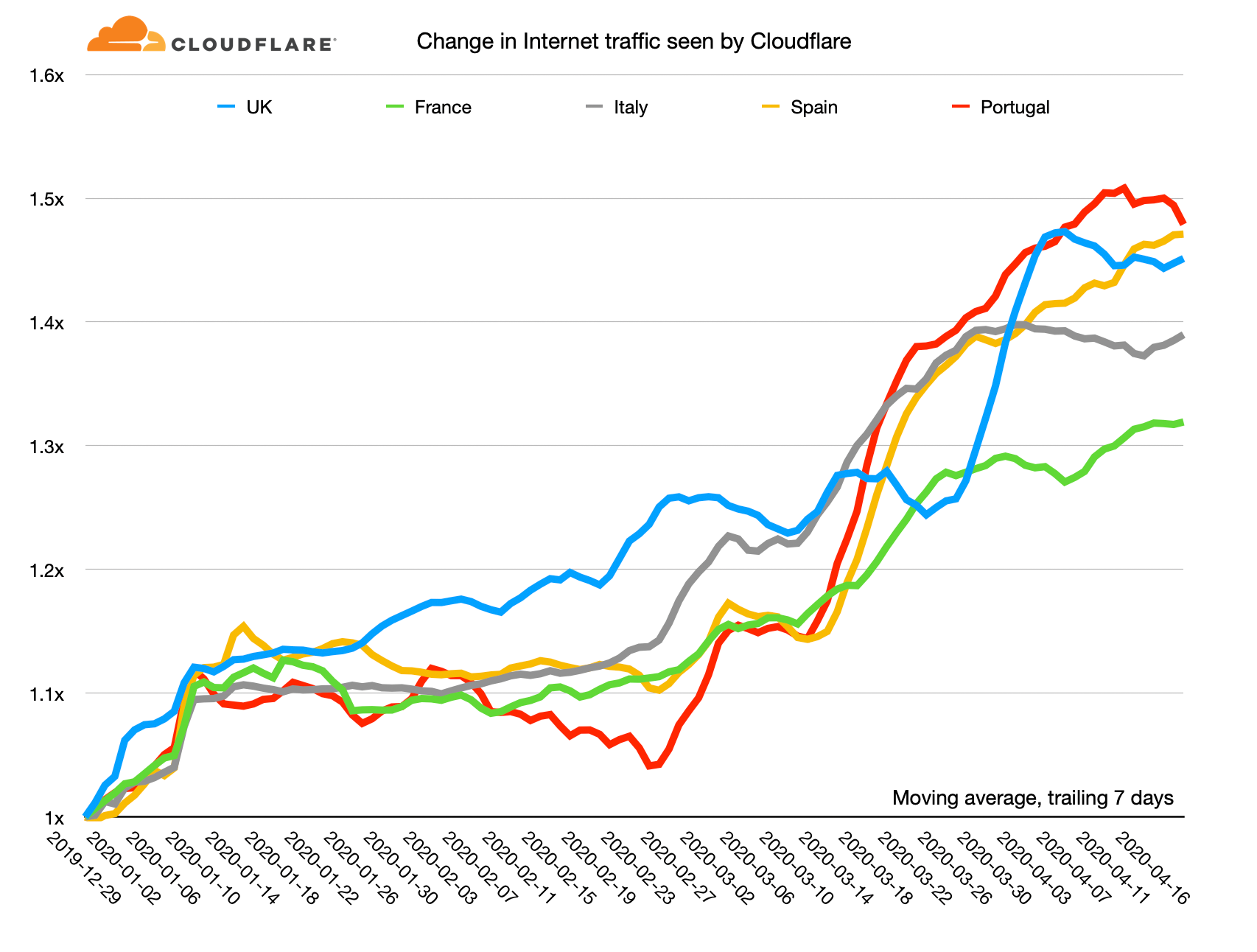
On this chart the highest growth in Internet use has been in Portugal: it's currently running at about a 50% increase Continue reading
Final Results of the 2020 Board Elections and IETF Selection
The Internet Society Elections Committee is pleased to announce the final results of the 2020 elections and the IETF selection for the Board of Trustees.
The voting concluded on 3 April. The results were announced and the challenge period was opened on 6 April. The deadline to file challenges was 15 April. One challenge was filed in the Chapters election. In accordance with the Procedures for Selecting Trustees, Internet Society President Andrew Sullivan, the chairs of the Nominations and Elections committees, and the other members of the board discussed the merits of the challenge. In the end, the board decided that the challenge was without merit and rejected it.
Therefore, the election results announced on 6 April stand:
- Ndeye Maimouna Diop and George Sadowsky have been elected by Chapters, and
- Ted Hardie has been elected by Organization Members.
Also, following the process documented in RFC 3677, the Internet Architecture Board, on behalf of the IETF, has selected:
The term of office for all of the new Trustees will be three years, commencing with the 2020 Annual General Meeting, 1-2 August.
The Elections Committee congratulates all the new Trustees and expresses its gratitude once more to all Continue reading
Las Vegas Networking Groups
If you’re in Las Vegas, Nevada, and are looking for the best places to enjoy your time and your quality business networking, do your research first and don’t spread yourself too thin.
There is a huge difference between the Las Vegas business referral organization and Las Vegas business networking organization. Here are a few you should get to know well.
3 Las Vegas Business Networking Groups
BNI
Both networking organizations and business referral organizations could be really valuable to make your business grow. If you are a member of BNI for a very long time in Las Vegas and if you put the effort into the business networking group, it would help your business grow in ways you can’t imagine. They both meet every week and attendance is necessary.
Trustegrity
Trustegrity gathers its members once a month and gives you relationships and increase the number of referrals among those in it. It is not strict about the whole one person per profession like BNI. In Las Vegas, there are a lot of different other business networking organizations that feature one member per profession. They usually have a structure in which they meet either twice a week or once a week. Continue reading
Can We Trust Server DSCP Marking?
A reader of my blog sent me this question:
Do you think we can trust DSCP marking on servers (whether on DC or elsewhere - Windows or Linux )?
As they say “not as far as you can throw them”.
Does that mean that the network should do application recognition and marking on the ingress network node? Absolutely not, although the switch- and router vendors adore the idea of solving all problems on their boxes.
AWS CLI Installation and Setup
Getting the AWS CLI installed and setup.AWS CLI Installation and Setup
In this post I will show you how to get the AWS CLI install and setup so that you can interact with AWS service via the CLI on your local machine. Installation At the time of writing there are two version of the AWS CLI. It is recommended to install version 2 of the software as all the...Daily Roundup: IBM Container Apps Hide Behind Fortanix
IBM and Fortanix doubled down on confidential computing; Google Anthos built a bridge to AWS; and...
Kernel of Truth season 3 episode 5: Routing protocols in the datacenter fabric
Subscribe to Kernel of Truth on iTunes, Google Play, Spotify, Cast Box and Sticher!
Click here for our previous episode.
Hosts Roopa Prabhu and Pete Lumbis are joined by a special guest to the podcast, Russ White! The group come together virtually to discuss what we should think about when it comes to routing protocols in the datcenter. What are the tradeoffs when using traditional protocols like OSPF or BGP? What about new protocols like RIFT or a hybrid approach with things like BGP-link state? Spoiler alert: it depends.
Guest Bios
Roopa Prabhu: Roopa Prabhu is Chief Linux Architect at Cumulus Networks. At Cumulus she and her team work on all things kernel networking and Linux system infrastructure areas. Her primary focus areas in the Linux kernel are Linux bridge, Netlink, VxLAN, Lightweight tunnels. She is currently focused on building Linux kernel dataplane for E-VPN. She loves working at Cumulus and with the Linux kernel networking and debian communities. Her past experience includes Linux clusters, ethernet drivers and Linux KVM virtualization platforms. She has a BS and MS in Computer Science. You can find her on Twitter at @__roopa.
Pete Lumbis: Pete, CCIE R&S #28677 and CCDE 2012::3, is Continue reading



