Hello world!
Welcome to WordPress. This is your first post. Edit or delete it, then start writing!
VXLAN/EVPN vs VRF Lite
A little background information first.
When having a business requirement of tenancy, most solutions will tend to lean towards VRF. That is because VLANs require a distributed L2 environment, which comes with spanning tree, mlag and a whole other glut of inefficient network control plane protocols. Upleveling the infrastructure to L3 ends up requiring VRF technology to enforce tenancy.
Once you’ve settled on this feature as the solution for the business requirement, the next question is: How do I successfully deploy VRFs in a large distributed environment at scale, that also allows me to minimize the burden of management while still enforcing tenancy in all the important parts of my network? Most conversations surrounding this question will lead down two solution paths:
- VXLAN with EVPN
- VRF Lite
Definitions of VXLAN with EVPN and VRF Lite.
VXLAN with EVPN leverages VRFs at every border and leaf switch, while all the intermediate devices (ie. spines, super spines) only see the encapsulated VXLAN traffic, and hence do not need any VRF intelligence or visibility.
A VRF Lite solution is fundamentally simpler since it uses less moving parts. The thought of enabling the EVPN address family and encapsulating traffic into a VXLAN tunnel Continue reading
Red Hat’s Susan James: How Open Source is Shaping 5G
Open source has been shaping the way service providers collaborate and work together, especially as...
The Week in Internet News: CIA Had Encryption Backdoor for Decades

We’re watching you: The U.S. CIA secretly had an ownership stake in Swiss encryption company Crypto AG for decades and was able to read encrypted messages sent using the company’s technology, the Washington Post reports. West German intelligence agencies worked with the CIA. Forbes columnist Jody Westby called for a congressional investigation.
We’re watching you, part two: Meanwhile, Russia’s Federal Security Service has ordered some large Internet companies in the country to give it continuous access to their systems, the New York Times reports. The FSB has targeted more than 200 companies, including popular messenger service Telegram, social network VK. and classified advertisement website Avito.ru.
Big bucks for space-based Internet: Astranis, a satellite Internet startup focused on bringing service to underserved areas, has raised $90 million in new funding, Fortune says. The new funding will help Astranis deploy its first satellite, focused on providing Internet service in Alaska.
Not so fast: Satellites, however, have some downsides, according to a story on TheConversation.com. Satellites are vulnerable to cyberattacks, with hackers potentially able to shut them down or even turn them into weapons, the story suggests.
New privacy push: U.S. Senator Kirsten Gillibrand, a New York Democrat, has Continue reading
Tech Bytes: Engineering Firm Builds Better End-User Experience With SD-WAN (Sponsored)
On today's Tech Bytes we talk with J-U-B Engineers, Inc., about how the company boosted employee productivity with an SD-WAN from Silver Peak. Silver Peak is our sponsor. Our guest is Tory Adams, Director of Information Technology at J-U-B Engineers.Tech Bytes: Engineering Firm Builds Better End-User Experience With SD-WAN (Sponsored)
On today's Tech Bytes we talk with J-U-B Engineering about how the company boosted employee productivity with an SD-WAN from Silver Peak. Silver Peak is our sponsor. Our guest is Tory Adams, Director of Information Technology at J-U-B Engineering.
The post Tech Bytes: Engineering Firm Builds Better End-User Experience With SD-WAN (Sponsored) appeared first on Packet Pushers.
Automation Story: Building a Network Inventory Database
What’s the next logical automation step after you cleaned up device configurations and started using configuration templates? It obviously depends on your pain points; for Anne Baretta it was a network inventory database stored in SQL tables (and thus readily accessible from his other projects).
Notes
- I’m always amazed that we have to solve simple problems decades after the glitzy slide decks from network management vendors proclaimed them solved;
- I’m also saddened that it’s often really hard to get data out of a network management product;
- Check out our network automation course when you’re ready to start your own automation journey.
Automation Story: Building a Network Inventory Database
What’s the next logical automation step after you cleaned up device configurations and started using configuration templates? It obviously depends on your pain points; for Anne Baretta it was a network inventory database stored in SQL tables (and thus readily accessible from his other projects).
Notes
- I’m always amazed that we have to solve simple problems decades after the glitzy slide decks from network management vendors proclaimed them solved;
- I’m also saddened that it’s often really hard to get data out of a network management product;
- Check out our network automation course when you’re ready to start your own automation journey.
CEX (Code EXpress) 03. Variable is better than fixed.
Hello my friend,
We are slowly but surely start talking about more and more useful and interesting topics staying yet at a basic level. Today you will learn about variables in Python, as variables are obviously the basic building block of any tool.
Network automation training – boost your career
Don’t wait to be kicked out of IT business. Join our network automation training to secure your job in future. Come to NetDevOps side.

How does the training differ from this blog post series? Here you get the basics and learn some programming concepts in general, whereas in the training you get comprehensive set of knowledge with the detailed examples how to use Python for the network and IT automation. You need both.
What are we going to do today?
We will learn how to create and use in Python 3.8 several types of the variables such as:
- Numbers
- Strings
- Boolean
The different types of variables are used for the different purposes, that’s why the more variables’ type you know, the better code you can write. We must admit that this list of the variables isn’t complete. That is why in the next couple of blogposts you will see Continue reading
MikroTik – RouterOSv7 first look – VxLAN
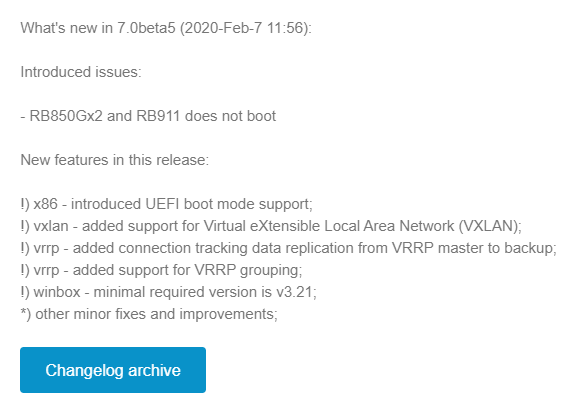
VxLAN support added in 7.0beta5
MikroTik announced VxLAN support on Valentine’s Day (Feb 14th) of 2020.
This is a significant feature addition for RouterOSv7 as it will pave the way for a number of other additions like EVPN in BGP.
It will also give MikroTik the ability to appeal to enterprises and data centers that might need cost-effective VxLAN capable devices.
Service Providers are also moving towards VxLAN as a future replacement for VPLS so this is helpful for that market as well.
Download the OVA here:
https://download.mikrotik.com/routeros/7.0beta5/chr-7.0beta5.ova
Implementation
The initial release of VxLAN is based on unicast and multicast to deliver Layer 2 frames.
As there is no EVPN support, the VTEPs must be manually configured for each endpoint in a full mesh configuration.
The VxLAN interface can then be bridged to a physical ethernet port or VLAN interface to deliver the traffic to the end host.
Lab Example
Here is an overview lab in EVE-NG with a basic setup using 3 linux servers on the same 10.1.1.0/24 subnet which is carried as an overlay by VxLAN.
VxLAN reachability for VTEPs is acheived with OSPFv2 and loopback addresses.
VNI: 100
Continue reading
Real-time DDoS mitigation using BGP RTBH and FlowSpec
DDoS Protect is a recently released open source application running on the sFlow-RT real-time analytics engine. The software uses streaming analytics to rapidly detect and characterize DDoS flood attacks and automatically applies BGP remote triggered black hole (RTBH) and/or FlowSpec controls to mitigate their impact. The total time to detect and mitigate an attack is in the order of a second.The combination of multi-vendor standard telemetry (sFlow) and control (BGP FlowSpec) provide the real-time visibility and control needed to quickly and automatically adapt the network to address a range of challenging problems, including: DDoS, traffic engineering, and security.
Solutions are deployable today: Arista BGP FlowSpec describes the recent addition of BGP FlowSpec support to Arista EOS (EOS has long supported sFlow), and sFlow available on Juniper MX series routers describes the release of sFlow support on Juniper MX routers (which have long had BGP FlowSpec support). This article demonstrates DDoS mitigation using Arista EOS. Similar configurations should work with any router that supports sFlow and BGP FlowSpec.
The diagram shows a typical deployment scenario in which an instance of sFlow-RT (running the DDoS Protect application) receives sFlow from the site router (ce-router). A Continue reading
Must Read: Impact of Tomahawk-4 on Data Center Fabric Designs
Dinesh Dutt, a pragmatic IP routing guru, the mastermind behind great concepts like simplified BGP configuration, and one of the best ipSpace.net authors, finally decided to start blogging. His first article: describing the impact of having 256 100GE ports in a single ASIC (Tomahawk 4). Hope you’ll enjoy his musings as much as I did ;)
Must Read: Impact of Tomahawk-4 on Data Center Fabric Designs
Dinesh Dutt, a pragmatic IP routing guru, the mastermind behind great concepts like simplified BGP configuration, and one of the best ipSpace.net authors, finally decided to start blogging. His first article: describing the impact of having 256 100GE ports in a single ASIC (Tomahawk 4). Hope you’ll enjoy his musings as much as I did ;)
Daily Roundup: Cloud Titans Tank Arista’s Q4
Cloud titans tanked Arista’s Q4; US charged Huawei with theft and espionage; and Microsoft JEDI...
BiB 088: Mastering Python Networking Third Edition by Eric Chou
Eric Chou, author of Master Python Networking Third Edition, discusses what's new in this edition of the book. Quite a lot!BiB 088: Mastering Python Networking Third Edition by Eric Chou
Eric Chou, author of Master Python Networking Third Edition, discusses what's new in this edition of the book. Quite a lot!
The post BiB 088: Mastering Python Networking Third Edition by Eric Chou appeared first on Packet Pushers.
Is SD-Branch Worth the Hype?
As the SD-WAN market explodes, some service providers are pushing SD-branch as a way to build an...
Heavy Networking 502: Get Off My VLAN! Old Network Engineers On What New Engineers Should Know
As more abstractions and automation layers creep into the network, are network engineers losing their grasp on core fundamentals? Three grumpy old network engineers ponder this question, talk about how we got here, and what can be done about it. Our guests are Chris Young and Ivan Pepelnjak.
The post Heavy Networking 502: Get Off My VLAN! Old Network Engineers On What New Engineers Should Know appeared first on Packet Pushers.

