The Four Essential Personalities for a Strong Cybersecurity Team
A security team with a broader view of issues can provide better plans and solutions to problems and the ability to react effectively and quickly in a security emergency.
A security team with a broader view of issues can provide better plans and solutions to problems and the ability to react effectively and quickly in a security emergency.
Recent releases of Firefox have introduced the concept of DNS privacy under the name “Trusted Recursive Resolver”. Although Firefox ships with DNS-over-HTTPS (DoH) disabled by default, there has been some discussion within the Mozilla developer community about changing the default to “enabled”.
Although DoH is somewhat controversial because it moves control plane (signalling) messages to the data plane (data forwarding), and can thereby bypass local network policies, DoH advocates argue that it makes it harder to block or monitor DNS queries which is a commonly used method for restricting access to the Internet and/or monitoring user behaviour.
But putting these arguments aside, if you want to try out DoH then the DNS privacy (or “TRR” in Firefox speak) configuration in Firefox can be accessed as follows:
A sample output of DNS privacy configuration in Mozilla Firefox is as follows:
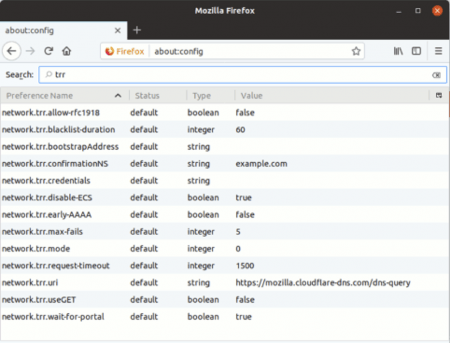
Firefox offers its technical users quite a few settings to play with, but the most important options (along with their recommended settings) for TRR are:
“network.trr.bootstrapAddress” specifies the IP address of a recursive resolver that should Continue reading

Last year we published some crypto challenges to keep you momentarily occupied from the festivities. This year, we're doing the same. Whether you're bored or just want to learn a bit more about the technologies that encrypt the internet, feel free to give these short cryptography quizzes a go.
We're withholding answers until the start of the new year, to give you a chance to solve them without spoilers. Before we reveal the answers; if you manage to solve them, we'll be giving the first 5 people to get the answers right some Cloudflare swag. Fill out your answers and details using this form so we know where to send it.
Have fun!
NOTE: Hints are below the questions, avoid scrolling too far if you want to avoid any spoilers.

Client says hello, as follows:
00000c07ac01784f437dbfc70800450000f2560140004006db58ac1020c843c
7f80cd1f701bbc8b2af3449b598758018102a72a700000101080a675bce16787
abd8716030100b9010000b503035c1ea569d5f64df3d8630de8bdddd1152e75f
528ae577d2436949ce8deb7108600004400ffc02cc02bc024c023c00ac009c0
08c030c02fc028c027c014c013c012009f009e006b0067003900330016009d
009c003d003c0035002f000a00af00ae008d008c008b010000480000000b
000900000663666c2e7265000a00080006001700180019000b0002010000
0d0012001004010201050106010403020305030603000500050100000000
001200000017000052305655494338795157524c656d6443436c5246574651
675430346754456c4f52564d674e434242546b51674e513d3d
[Raw puzzle without text wrap]
A user has an authenticator device to generate one time passwords for logins to their banking website. The implementation contains a fatal flaw.
At the following times, the following codes are generated (all in GMT/UTC):
Day 2 of our top blog posts of 2018 and coming in at Number 4 is the launch of Docker Enterprise 2.0 (formerly Docker Enterprise Edition). Docker’s industry-leading container platform is the only platform that simplifies Kubernetes and manages and secures applications on Kubernetes in multi-Linux, multi-OS and multi-cloud customer environments. To learn more about our Docker Enterprise, read on…
We are excited to announce Docker Enterprise Edition 2.0 – a significant leap forward in our enterprise-ready container platform. Docker Enterprise Edition (EE) 2.0 is the only platform that manages and secures applications on Kubernetes in multi-Linux, multi-OS and multi-cloud customer environments. As a complete platform that integrates and scales with your organization, Docker EE 2.0 gives you the most flexibility and choice over the types of applications supported, orchestrators used, and where it’s deployed. It also enables organizations to operationalize Kubernetes more rapidly with streamlined workflows and helps you deliver safer applications through integrated security solutions. In this blog post, we’ll walk through some of the key new capabilities of Docker EE 2.0.
As containerization becomes core to your IT strategy, the importance of having a platform Continue reading
Organizations that proactively monitor cloud applications gain critical insights into security, usage, performance, and compliance.
As 2018 comes to a close, we looked back at the top five blogs that were most popular with our readers. For those of you that had difficulties with memory and CPU sizing/usage when running Java Virtual Machine (JVM) in a container, we are kicking off the week with a blog that explains how to get improved Docker container integration with Java 10 in Docker Desktop ( Mac or Windows) and Docker Enterprise environments.

Many applications that run in a Java Virtual Machine (JVM), including data services such as Apache Spark and Kafka and traditional enterprise applications, are run in containers. Until recently, running the JVM in a container presented problems with memory and cpu sizing and usage that led to performance loss. This was because Java didn’t recognize that it was running in a container. With the release of Java 10, the JVM now recognizes constraints set by container control groups (cgroups). Both memory and cpu constraints can be used manage Java applications directly in containers, these include:
Java 10 improvements are realized in both Docker Desktop ( Mac Continue reading

This month, we’ve asked parents to share their experiences of raising kids in the tech age. Today’s guest author is Kimberly Rae Miller, author of Beautiful Bodies and the bestselling memoir Coming Clean.
Being a parent means living with constant, underlying anxiety over just about everything from how to slice hot dogs, to the age old winter jacket vs. car seat conundrum, to whether all the tech used to keep kids alive/make life with them easier is actually going to screw them up/destroy your life.
The latter takes a fair bit of cognizant dissonance. Most of us know at least some of the pitfalls of our wired life. After all, the digital assistant in my living room knew that I was pregnant again about five seconds after I did (and yes, there are Bluetooth-enabled home pregnancy tests), and voila, almost immediately targeted ads for diapers and nursery furniture started showing up when I shopped online. Most of the time I brush aside how uncomfortable it all makes me, because the gizmos and gadgets that make momming slightly easier are maybe worth the invasion of privacy.
When I was pregnant with my now two-year-old son, I knew that I didn’t know Continue reading
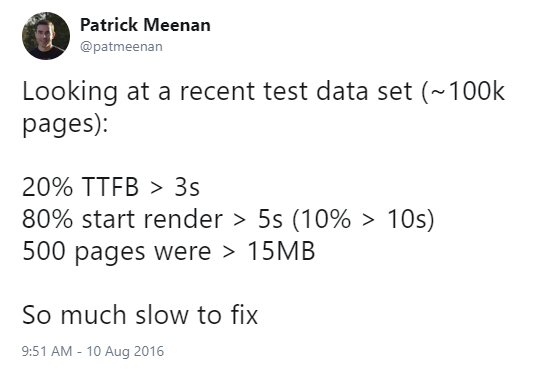
The Time to First Byte (TTFB) of a site is the time from when the user starts navigating until the HTML for the page they requested starts to arrive. A slow TTFB has been the bane of my existence for more than the ten years I have been running WebPageTest.
Looking at a recent test data set (~100k pages):
— Patrick Meenan (@patmeenan) August 10, 2016
20% TTFB > 3s
80% start render > 5s (10% > 10s)
500 pages were > 15MB
So much slow to fix
There is a reason why TTFB appears as one of the few “grades” that WebPageTest scores a site on and, specifically, why it is the first grade in the list.
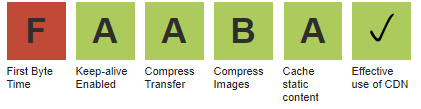
If the first byte is slow, EVERY other metric will also be slow. Improving it is one of the few cases where you can predict what the impact will be on every other measurement. Every millisecond improvement in the TTFB translates directly into a millisecond of savings in every other measurement (i.e. first paint will be 500ms faster if TTFB improves by 500ms). That said, a fast ttfb doesn't guarantee a fast experience but a slow ttfb does guarantee a slow Continue reading

Keep the pipes flowing: The Indian government’s Department of Telecommunications has told state governments they should avoid Internet shutdowns in situations not involving an emergency or public safety, Business Insider India reports. There were about 130 Internet shutdowns in the country in 2018, up from 79 the year before. But shutdowns close off residents’ access to banking and other online services, the agency said in its notice.
A fragmenting Internet: The global Internet is fracturing with governments increasingly exerting their influence on digital companies, markets, and rights, Foreign Policy says. The authors see a future Internet Warring States Period, in which several countries jockey for influence on the Internet, which could lead to a fragmented Internet in areas where there was once common ground.
Fake crackdown: Egypt is using a crackdown on so-called fake news to detain or jail “scores” of journalists, bloggers, and social media users, the Los Angeles Times reports. In 2018, Egypt jailed 19 journalists for allegedly “disseminating false information,” while all other countries jailed a total of nine journalists.
Beware the cryptominers: Internet users saw a 4,000 percent increase in crytomining malware in 2018, The Next Web says. MacAfee Labs noted more than 4 million new Continue reading
Develop a well-thought-out approach to the migration and make sure your management and operations teams understand the potential opportunities and challenges.

In December 2017 we unveiled the true potential of Cloudflare’s scale: to find the best commercially available mince pie and let the world know about it. In 2018 we’ve all been extremely busy helping Cloudflare & our customers and therefore we left it very late this year. Uncomfortably late.
If you want to know the best mince pie to buy in 2018 right now, skip straight to the bottom of this post where we reveal the winner. If you want to understand more about what makes a mince pie great and how we can learn this at Cloudflare’s scale - read on.
With a very short amount of time to get this research out to a discerning and demanding public, we engaged the entire Cloudflare London team to help. Team members diligently went out and purchased mince pies from all over the South East of England for everyone to taste.

On Monday the team assembled for a “Mince Pie Jam”, where we would taste & consistently review each pie:


As we can see from even the most cursory Internet Continue reading

The Internet Society continued its engagement with Middle East networking community by participating in the e-AGE18 Conference, where we took the opportunity to promote the importance of DNS Security and Privacy. The conference was held on 2-3 December 2018 at the Marriott Hotel in Amman, Jordan and was organised by the Arab States Research and Education Network (ASREN) and co-sponsored by the Internet Society.

Kevin Meynell from the Internet Society’s Middle East Bureau, highlighted the importance of implementing DNSSEC which allows DNS resolvers to authenticate the origin of data in the DNS through a verifiable chain-of-trust. This reduces the possibility of spoofing where incorrect or corrupt data is introduced into a resolver, or a man-in-the-middle attack whereby DNS queries are re-directed to a name server returning forged responses.
Unfortunately, only the Saudi Arabia ccTLD (.sa) has operationally deployed DNSSEC in the Middle East region at the present time, although Iran (.ir) and Iraq (.iq) have deployed it on an experimental basis. On the positive side, around 18% of DNS queries originated from Middle East countries are being validated compared to 12% globally, with Yemen (45.1%), Saudi Arabia (32.1%), Iraq (30.6%), Bahrain (23.2%) and Continue reading
Network segmentation…. air gap segmentation… the names go on and on. But no matter what you call it, you designed it and deployed it for a reason. Likely a very good reason. Potentially even a reason with fines and consequences should the segmentation not work. So once you deploy it…. what then? Just trust it is working and will always stay working?
 Trust, But Verify
Trust, But VerifyI admit I am likely viewed as boringly logical when it comes to the network. It just doesn’t seem logical to me to spend so many hours in the design and the deploy phase and then just trust that it is working.
Don’t just trust. Verify.
Use whatever tool you want. Just please… know what is really going on in your network. Know reality.
In this blog I’m going to show you how you can use Stealthwatch to get visibility into what is REALLY going on in your networking in reference to your segmentation.
How can Stealthwatch tell you if your segmentation is working or not? I refer to Stealthwatch as “Your Network Detective Command Center”. If Continue reading
In early 2017 I kicked off an effort to start using Linux as my primary desktop OS, and I blogged about the journey. That particular effort ended in late October 2017. I restarted the migration in April 2018 (when I left VMware to join Heptio), and since that time I’ve been using Linux (Fedora, specifically) full-time. However, I thought it might be helpful to collect the articles I wrote about the experience together for easy reference. Without further ado, here they are.
Other Users’ Stories: Part 1, Part 2, Part 3, Part 4
Corporate Collaboration: Part 1, Part 2, Part 3
These are only the articles directly related to the migration efforts, but many more articles were spawned as a result of the project. Browse through all the Fedora-tagged articles to see some related articles.
If you have any questions about migrating to Linux or about any of these articles (or related articles), you’re welcome to contact me on Twitter. I look forward to hearing from you!
We are now at the 22nd of December, and it is time to take a break to spend time with family and friends (as well as prepping up a lot of work for next year). From my family to yours, we wish you the merriest of Christmas’, and a very happy new year.
Remember, at this time of year, “He who made the blind men see, and the lame men walk,” as Tiny Tim would say.
A bit of retrospect from 2018, and prospect for 2019…
As Marley might say: “Look to see me no more, and expect the first post in the new year…”
Rogue DNS kinda reminds of me of a crime scene show I saw once. The killer was hijacking the GPS mapping system in the rental cars of their victims.
Imagine that who you think is your valid DNS server actually isn’t. Yeah… i know – scary. …. If you are not familiar with the term “Rogue DNS” … maybe you might know the exposure via other terms like DNS hijacking or DNS redirection to name just a few.
In this blog I’m not going to teach about what Rogue DNS… DNS hijacking… or DNS redirection. Nor am I going to talk about solutions like OpenDNS (Cisco’s Umbrella). I’m going to just show you how you can use Stealthwatch to get visibility into what is REALLY going on in your network in reference to DNS. We are going to cover 2 situations where having a tool like Stealthwatch could help you with your DNS.
How does Stealthwatch do this? I refer to Stealthwatch as “Your Network Detective Command Center”. If there are rogue DNS in your network and your end devices are Continue reading

As cloud computing continues to transform every business and industry, developers at global enterprises and emerging startups alike are increasingly leveraging container technologies to accelerate how they build modern web, mobile and IoT applications.
IBM has achieved certification of its flagship Db2 database, Websphere-Liberty middleware server and Security Access Manager products now available on Docker Hub. These Certified Containers enable developers to accelerate building cloud-native applications for the Docker Enterprise platform. Developers can deploy these solutions from IBM to any on-premises infrastructure or public cloud. They are designed to assist in the modernization of traditional applications moving from on-premises monoliths into hybrid cloud microservices.
These solutions are validated by both Docker and IBM and are integrated into a seamless support pipeline that provides customers the world-class support they have become accustomed to when working with Docker and IBM.