Introducing Single Sign-On for the Cloudflare Dashboard
The Challenge of Managing User Access to SaaS Applications
As the number of SaaS services people use everyday grows, it has become more challenging to juggle the number of password and multi-factor authentication combinations users have to keep track of to get online.
Adopting identity services have allowed companies to centralize employee authentication. With Cloudflare Access, companies can ensure employees use a company managed identity provider when accessing websites behind Cloudflare. Last week, Sam published a blog on how Cloudflare has made it easier to connect Cloudflare Access to the Atlassian suite of tools.
Since Cloudflare has simplified access control for corporate applications, many enterprise customers have commonly asked for the ability to extend the same ease of access and control to the Cloudflare dashboard itself.
Single Sign-On for the Cloudflare Dashboard
Today, we are announcing support for enterprise customers to use single sign-on (SSO) through their identity provider to access the Cloudflare dashboard.
Cloudflare is a critical piece of infrastructure for customers, and SSO ensures that customers can apply the same authentication policies to access the Cloudflare dashboard as other critical resources.
Once onboarded for SSO, all company user logins to the Cloudflare dashboard redirect to the customer’s identity provider. Once all required authentication checks complete successfully, the user is seamlessly redirected back to dash.cloudflare.com and logged in.
Leveraging Access & Workers to Build SSO
At Cloudflare, we dogfood our own services as both a way to make them better for our customers and to make developing new services more efficient and robust. With SSO, this is no different. Authentication configurations are managed through Access, which allows us to launch with support for the same identity providers available in Access today, including SAML.
Cloudflare is 8 years old and we built our user authentication system way before Cloudflare Access existed. In order to connect Access to our existing authentication system, we built a Cloudflare Worker that converts Access authentication tokens to our own authentication tokens. This greatly simplified the code changes required in our system, and results in faster SSO logins because the Worker runs at the network edge and reduces the number of round trips required to authenticate users.
In addition to leveraging Cloudflare services to build Single Sign-On, we are moving all Cloudflare employees to use SSO through our existing G Suite setup. This ensures Cloudflare can uniformly enforce multi-factor authentication policies for the services we protect with Cloudflare itself.
How to Start using SSO for the Cloudflare Dashboard
Cloudflare Enterprise customers can reach out to their Customer Success Manager to learn how to start using SSO to log-in to the Cloudflare dashboard. If you are interested in using SSO yourself and becoming a Cloudflare Enterprise customer, then please get in touch.
Dell, Microsoft Back CNEX Labs’ $23M Series D Round
 The company makes solid-state drive (SSD) controllers and software for cloud and hyperscale data centers.
The company makes solid-state drive (SSD) controllers and software for cloud and hyperscale data centers.
A Tour Inside Cloudflare’s G9 Servers

Cloudflare operates at a significant scale, handling nearly 10% of the Internet HTTP requests that is at peak more than 25 trillion requests through our network every month. To ensure this is as efficient as possible, we own and operate all the equipment in our 154 locations around the world in order to process the volume of traffic that flows through our network. We spend a significant amount of time specing and designing servers that makes up our network to meet our ever changing and growing demands. On regular intervals, we will take everything we've learned about our last generation of hardware and refresh each component with the next generation…
If the above paragraph sounds familiar, it’s a reflecting glance to where we were 5 years ago using today’s numbers. We’ve done so much progress engineering and developing our tools with the latest tech through the years by pushing ourselves at getting smarter in what we do.
Here though we’re going to blog about muscle.
Since the last time we blogged about our G4 servers, we’ve iterated one generation each of the past 5 years. Our latest generation is now the G9 server. From a G4 server comprising 12 Intel Continue reading
Red Hat OpenShift Update Is Heavy on Integration of CoreOS Features
 The CoreOS integration work will culminate with the next OpenShift 4.0 update. That platform will sit alongside Red Hat’s legacy Enterprise Linux and provide users with a choice of operating systems.
The CoreOS integration work will culminate with the next OpenShift 4.0 update. That platform will sit alongside Red Hat’s legacy Enterprise Linux and provide users with a choice of operating systems.
History Of Networking – Jana Iyengar – QUIC
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
The post History Of Networking – Jana Iyengar – QUIC appeared first on Network Collective.
Juniper Jumps On the Automation Bandwagon With EngNet
 The company says its approach is different from Cisco’s because it is focused on training the engineers behind the technology, not just releasing new products.
The company says its approach is different from Cisco’s because it is focused on training the engineers behind the technology, not just releasing new products.
Red Hat Ansible Network Automation Updates
For this blog post I am going to cover the following topics:
- The httpapi connection plugin
- Support for Arista eAPI and Cisco NX-API
- net_get and net_put
- netconf_get, netconf_rpc and netconf_config
- cli_command and cli_config
The HTTPAPI connection plugin
Connection plugins allow Ansible to connect to target hosts so it can execute tasks on them. With the Ansible 2.5 release the network_cli connection plugin was introduced, removing the requirement for the provider parameter and standardizing network modules to allow playbooks to look, feel and operate just like they do on Linux hosts. This also allowed Red Hat Ansible Tower to Continue reading
Mapping Factorio with Leaflet

The following is a guest post by Jacob Hands, Creator of FactorioMaps.com. He is building a community site for the game Factorio centered around sharing user creations.
Factorio is a game about building and maintaining factories. Players mine resources, research new technology and automate production. Resources move along the production line through multiple means of transportation such as belts and trains. Once production starts getting up to speed, alien bugs start to attack the factory requiring strong defenses.

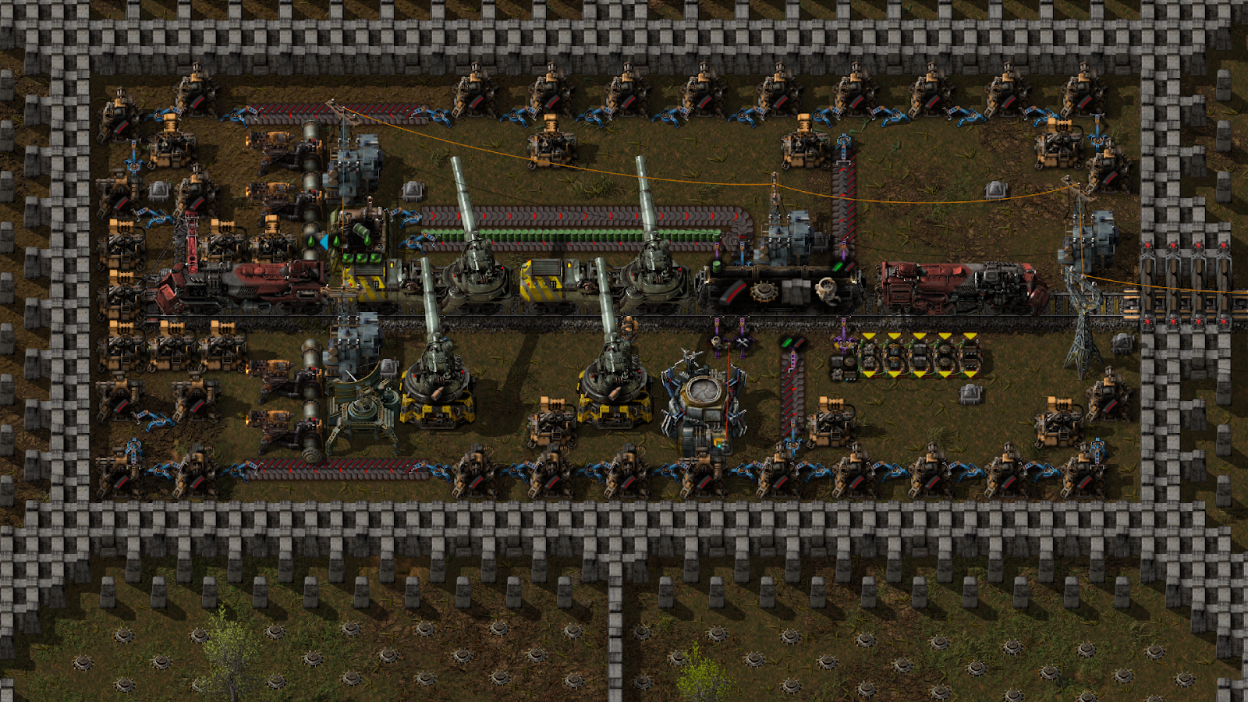

At FactorioMaps.com, I am building a place for the community of Factorio players to share their factories as interactive Leaflet maps. Due to the size and detail of the game, it can be difficult to share an entire factory through a few screenshots. A Leaflet map provides a Google Maps-like experience allowing viewers to pan and zoom throughout the map almost as if they are playing the game.
Hosting
Leaflet maps contain thousands of small images for X/Y/Z coordinates. Amazon S3 and Google Cloud Storage are Continue reading
Africa Is on a Steady Journey to Digital Transformation

The world has seen Africa’s digital future advancing by leaps and bounds in the adoption and use of information and communication technologies (ICTs) in the private and public sectors. What makes this more interesting and promising, is the level of investment and growth of women Engineers in recent years making headlines.
The Gambia has seen much of these developments in recent years with examples of inspiring women Engineers like Mrs Anna Secka Saine who has contributed in building many backbone Networks in Africa such as, Internet eXchange Points (IXPs), National Research and Education Networks (NRENs), and, as well helped trained many young and Professionals engineers.
We have also seen rise in the number of Computer Science clubs, after school coding, summer coding camps, Robotic clubs among others, which all projects the level of awareness and interest.
In August, two brilliant young Gambian High School science students, Sera Momodou Ndure and Ajie Isatou Ceesay from Marina International School (MIS) and West African International School (WAIS) respectively represented The Gambia at the Africa Girls Can Code Initiative (AGCCI2018) in Addis Ababa, Ethiopia.

The Africa Girls Can Code Initiative (AGCCI) 2018-2022 is an Africa Wide Initiative being developed and implemented by the U Continue reading
Too Many Choices! Picking the Right PoE for Your Application
Selecting a PoE power source for a powered device can be challenging since there are many options. Here is a brief overview to help you narrow down your choices and make the right decision.
Leaf-and-Spine Fabric Myths (Part 2)
The next set of Leaf-and-Spine Fabric Myths listed by Evil CCIE focused on BGP:
BGP is the best choice for leaf-and-spine fabrics.
I wrote about this particular one here. If you’re not a BGP guru don’t overcomplicate your network. OSPF, IS-IS, and EIGRP are good enough for most environments. Also, don’t ever turn BGP into RIP with AS-path length serving as hop count.
Read more ...Detecting spacecraft anomalies using LSTMs and nonparametric dynamic thresholding
Detecting spacecraft anomalies using LSTMs and nonparametric dynamic thresholding Hundman et al., KDD’18
How do you effectively monitor a spacecraft? That was the question facing NASA’s Jet Propulsion Laboratory as they looked forward towards exponentially increasing telemetry data rates for Earth Science satellites (e.g., around 85 terabytes/day for a Synthetic Aperture Radar satellite).
Spacecraft are exceptionally complex and expensive machines with thousands of telemetry channels detailing aspects such as temperature, radiation, power, instrumentation, and computational activities. Monitoring these channels is an important and necessary component of spacecraft operations given their complexity and cost. In an environment where a failure to detect and respond to potential hazards could result in the full or partial loss of spacecraft, anomaly detection is a critical tool to alert operations engineers of unexpected behavior.
Anomaly detection systems deployed today typically consist of tiered alarms indicating when values fall outside of pre-defined limits. There are also limited instances of expert systems and nearest-neighbour based approaches being tried, but their limitations prevented widespread adoption. A more accurate and scalable approach to anomaly detection that makes better use of limited engineering resources is required.
Any such system needs to work with data that is highly Continue reading
Docker Certified Plugins From Networking Partners

The Docker Certified Technology Program is designed for ecosystem partners and customers to recognize Containers and Plugins that excel in quality, collaborative support and compliance. Docker Certification gives organizations enterprises an easy way to run trusted software and components in containers on the Docker Enterprise container platform with support from both Docker and the publisher.
In this review, we’re looking at Docker Network Plugins. Networking has long been a vertical in the enterprise cloud and data center that has no shortage of complexity. Just as an overarching goal of Docker Enterprise is to make deploying and operating containers as simple as possible, the same goal applies to making Swarm networking as simple as possible. This powerful abstraction of complexity, is applicable regardless of whether in the customers data center or spread across multiple clouds. In some cases Docker Enterprise solves customer problems by shipping built-in plugins and in other scenarios the user’s needs are solved by innovations from the extensive Docker ecosystem. These solutions are validated by both Docker and the partner company and integrated into a seamless support pipeline that provide customers the world class support they have become accustomed to when working with Docker.
Check out the Continue reading