 When I was a young lad I had my heart set of being a car designer when I grew up. This dream carried on into my teens, then for some reason it vanished. Around the same time I discovered I could 'work' computers, and that I quite enjoyed it.
When I was a young lad I had my heart set of being a car designer when I grew up. This dream carried on into my teens, then for some reason it vanished. Around the same time I discovered I could 'work' computers, and that I quite enjoyed it.
Fast forward a great many years and I am looking back at over two decades of experience as an IT engineer. But my interest in design has never really waned - I still find great pleasure in things that have been designed well.
Just over six years ago I discovered the furniture manufacturer, Vitsœ. Although they started life as a Danish/German partnership they are now very much a British company - based in the UK with an Englishman at the helm. They produce a shelving system, called the 606, and I invested in some for my home office.
The 606 is extremely flexible in its usage, it can form an office space...

or somewhere to keep a record collection...

or even a kitchen...

Impressively, it also scales; from a small start...

to massive installations...

But the most impressive thing about this bespoke shelving system is that it's not bespoke at all. Continue reading

 Join SDxCentral and Brocade for the SDN Controller Report webinar on September 29th. Register today!
Join SDxCentral and Brocade for the SDN Controller Report webinar on September 29th. Register today!
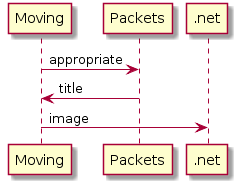
 To create this, I used the following PlantUML:
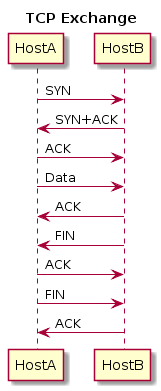
To create this, I used the following PlantUML: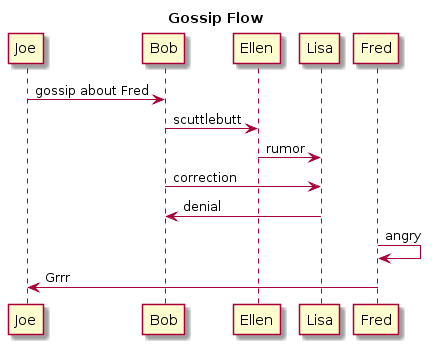
 The PlantUML to generate this was:
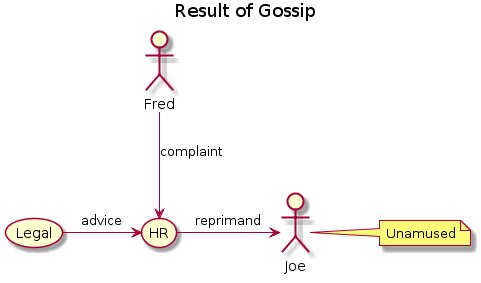
The PlantUML to generate this was: How often, in our careers, are we told to focus on one thing at a time? I would guess I see some message about this, such as the image to the left in this post, at least once a week, if not once a day.
How often, in our careers, are we told to focus on one thing at a time? I would guess I see some message about this, such as the image to the left in this post, at least once a week, if not once a day. 
 The 'Fight of the Century' ran on NSX, it turns out.
The 'Fight of the Century' ran on NSX, it turns out.