Liquid Cooling Is The Next Key To Future AI Growth
Paid Feature Over the last several years, the limiting factors to large-scale AI/ML were first hardware capabilities, followed by the scalability of complex software frameworks. …
Liquid Cooling Is The Next Key To Future AI Growth was written by David Gordon at The Next Platform.
VMware named a Leader in Cloud Networking in GigaOm Radar Report
We’re delighted to report that GigaOm, a global provider of technology industry insights and analysis, has placed VMware in the leader ring in the GigaOm Radar Report for Cloud Networking 2022. In the leader ring, VMware is placed in the Platform Play and Maturity quadrant. This is a testament to the robustness of VMware’s cloud networking solution and its leading position in the cloud networking space. Click here to download the complete report.

Noting VMware’s broad portfolio of networking solutions, which covers the entire network stack and includes native network features for observability, micro-segmentation, and beyond, GigaOm says that VMware is in a leading position to help enterprises with complex networking requirements “modernize and optimize their infrastructure.”
Cloud Network Evaluation Criteria
The report evaluates 11 vendors that provide tools or platforms to help build and operate cloud networks. They include major enterprises like VMware, as well as several smaller companies.
GigaOm assessed the vendors on a variety of criteria, including:
- Network traffic security and micro-segmentation.
- Observability.
- Troubleshooting and diagnostics.
- Optimization and autoscaling.
- APIs and IaC integration.
- Application-aware infrastructure.
- Solution management.
VMware received a triple-plus score – the highest evaluation possible – for most of the categories given above.
Continue reading
Configuring an AWS dynamic inventory with Automation controller
One of the core components of Ansible is inventories. In its most basic form, an inventory provides host information to Ansible so it can trigger the tasks on the right host or system. In most environments, the static inventory is sufficient for the Ansible control node to work from, however as we expand our use of automation, we need to transition to more effective methods of gathering ever-changing environment details.
This is where the use of a dynamic inventory is beneficial. This allows the platform to gather information for the inventory from environments that are not static sources. A prime example of this is using a dynamic inventory plugin to gather inventory information from a cloud provider or hypervisor, enabling you to keep an inventory up to date with instance details.
Amazon Web Services (AWS) is one of the biggest public cloud providers used around the world. Organizations use their Elastic Compute Cloud services (EC2) for their workflows, however managing an inventory for your instances running on AWS would typically have to be done manually, which is problematic and time consuming. Using the AWS Identity and Access Management interface (IAM), we are able to get programmatic access to the AWS Continue reading
HS018 API Management is a Configuration Problem
Johna believes that API management is part of IT operations. Greg doesn't understand the question and so we set off in search of answers.HS018 API Management is a Configuration Problem
Johna believes that API management is part of IT operations. Greg doesn't understand the question and so we set off in search of answers.
The post HS018 API Management is a Configuration Problem appeared first on Packet Pushers.
Duplicate ARP Replies with Anycast Gateways
A reader sent me the following intriguing question:
I’m trying to understand the ARP behavior with SVI interface configured with anycast gateways of leaf switches, and with distributed anycast gateways configured across the leaf nodes in VXLAN scenario.
Without going into too many details, the core dilemma is: will the ARP request get flooded, and will we get multiple ARP replies. As always, the correct answer is “it depends” 🤷♂️
Duplicate ARP Replies with Anycast Gateways
A reader sent me the following intriguing question:
I’m trying to understand the ARP behavior with SVI interface configured with anycast gateways of leaf switches, and with distributed anycast gateways configured across the leaf nodes in VXLAN scenario.
Without going into too many details, the core dilemma is: will the ARP request get flooded, and will we get multiple ARP replies. As always, the correct answer is “it depends” 🤷♂️
The Mass Customization Wave Is Starting For Servers
Remember when only a couple of variations of processors were available for servers in any given generation of server CPUs? …
The Mass Customization Wave Is Starting For Servers was written by Timothy Prickett Morgan at The Next Platform.
What Enterprises Can Expect as Carriers to Spend Billions on Broadband Rollouts
From funding to the front door, IT managers can learn from state-level fiber expansions and benefit from programs created to speed high-speed Internet buildouts powered by federal legislation, the FCC, and annual carrier capital expenditures.Optimizing Magic Firewall’s IP lists
Magic Firewall is Cloudflare’s replacement for network-level firewall hardware. It evaluates gigabits of traffic every second against user-defined rules that can include millions of IP addresses. Writing a firewall rule for each IP address is cumbersome and verbose, so we have been building out support for various IP lists in Magic Firewall—essentially named groups that make the rules easier to read and write. Some users want to reject packets based on our growing threat intelligence of bad actors, while others know the exact set of IPs they want to match, which Magic Firewall supports via the same API as Cloudflare’s WAF.
With all those IPs, the system was using more of our memory budget than we’d like. To understand why, we need to first peek behind the curtain of our magic.
Life inside a network namespace
Magic Transit and Magic WAN enable Cloudflare to route layer 3 traffic, and they are the front door for Magic Firewall. We have previously written about how Magic Transit uses network namespaces to route packets and isolate customer configuration. Magic Firewall operates inside these namespaces, using nftables as the primary implementation of packet filtering.
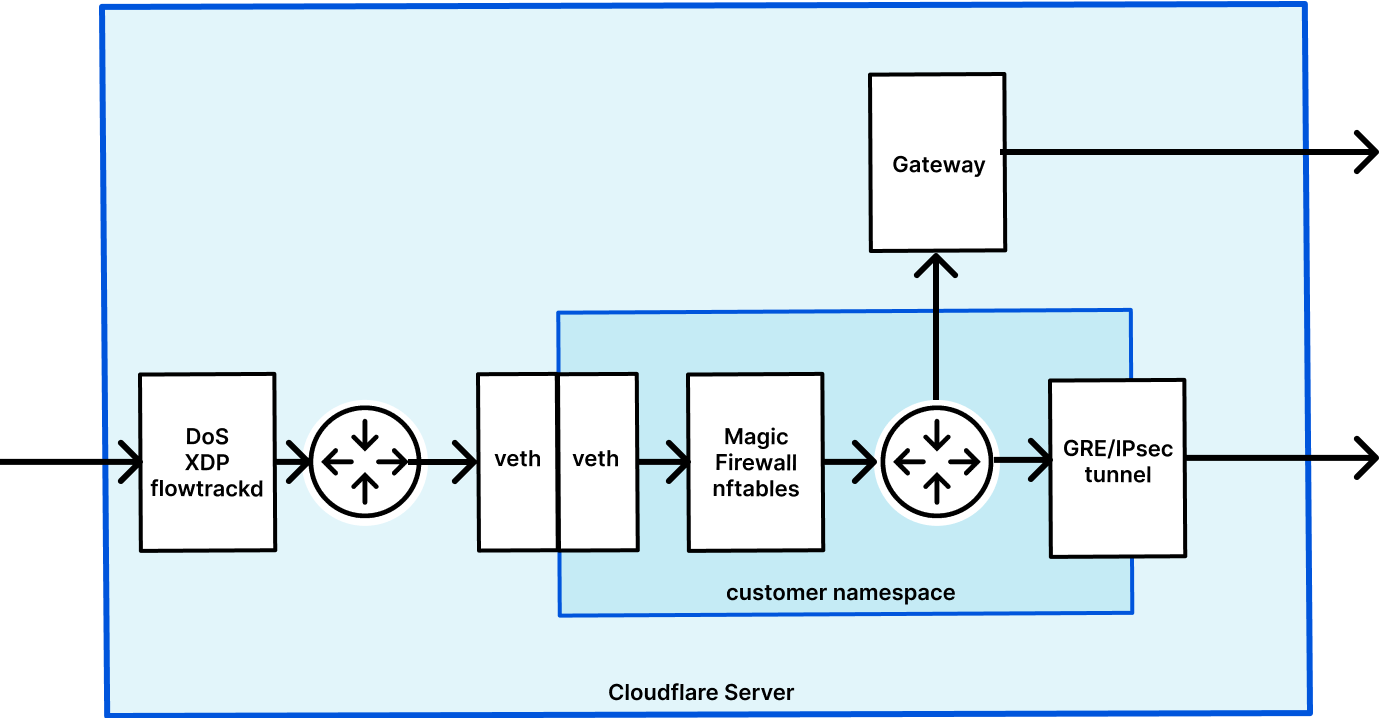
When a user makes an API request to configure their Continue reading
Understanding Data Center Fabrics 09: Other Considerations – Video
In the final video of this series on data center fabrics, Russ White walks through a set of considerations you might want to ponder as you design your data center fabric. These considerations include whether to single-home or dual-home a server in a fabric (it depends!), why Russ isn’t a fan of MLAGs in a […]
The post Understanding Data Center Fabrics 09: Other Considerations – Video appeared first on Packet Pushers.
Can Fantastical Openings Replace Calendly?
TL;DR
Fantastical Openings can’t replace Calendly for my scheduling needs yet, but it’s close.
The Rest Of The Story
I use Calendly so that folks can schedule me for appointments. I send people a Calendly link, and they choose an available time slot. Calendly creates calendar invitations and sends them to me and the requestor. Calendly also integrates with Zoom, so that an invite comes with a Zoom meeting already attached.
In my years of Calendly use, I’ve found it to be…
- Reliable. It just works.
- Flexible. The availability rules engine allows me to configure conditions such as “leave a gap of X minutes between appointments” that I rely on to keep my calendar sane.
- Expensive. $144/year for the features I need.
I also use Fantastical by Flexibits. In my few months as a Fantastical user, I’ve found it to be…
- Beautiful. It’s the best calendaring interface of anything I’ve tried.
- Integrated. I use Fantastical to integrate with multiple calendars, Zoom, and the Todoist task manager. I use Fantastical both on my Mac and iOS devices.
- A super power. Fantastical happens to be highly compatible with how I work. I am more productive with Fantastical.
- Affordable. $40/year for the features Continue reading
CVE-2022-1096: How Cloudflare Zero Trust provides protection from zero day browser vulnerabilities


On Friday, March 25, 2022, Google published an emergency security update for all Chromium-based web browsers to patch a high severity vulnerability (CVE-2022-1096). At the time of writing, the specifics of the vulnerability are restricted until the majority of users have patched their local browsers.
It is important everyone takes a moment to update their local web browser. It’s one quick and easy action everyone can contribute to the cybersecurity posture of their team.
Even if everyone updated their browser straight away, this remains a reactive measure to a threat that existed before the update was available. Let’s explore how Cloudflare takes a proactive approach by mitigating the impact of zero day browser threats with our zero trust and remote browser isolation services. Cloudflare’s remote browser isolation service is built from the ground up to protect against zero day threats, and all remote browsers on our global network have already been patched.
How Cloudflare Zero Trust protects against browser zero day threats
Cloudflare Zero Trust applies a layered defense strategy to protect users from zero day threats while browsing the Internet:
- Cloudflare’s roaming client steers Internet traffic over an encrypted tunnel to a nearby Cloudflare data center for inspection and Continue reading