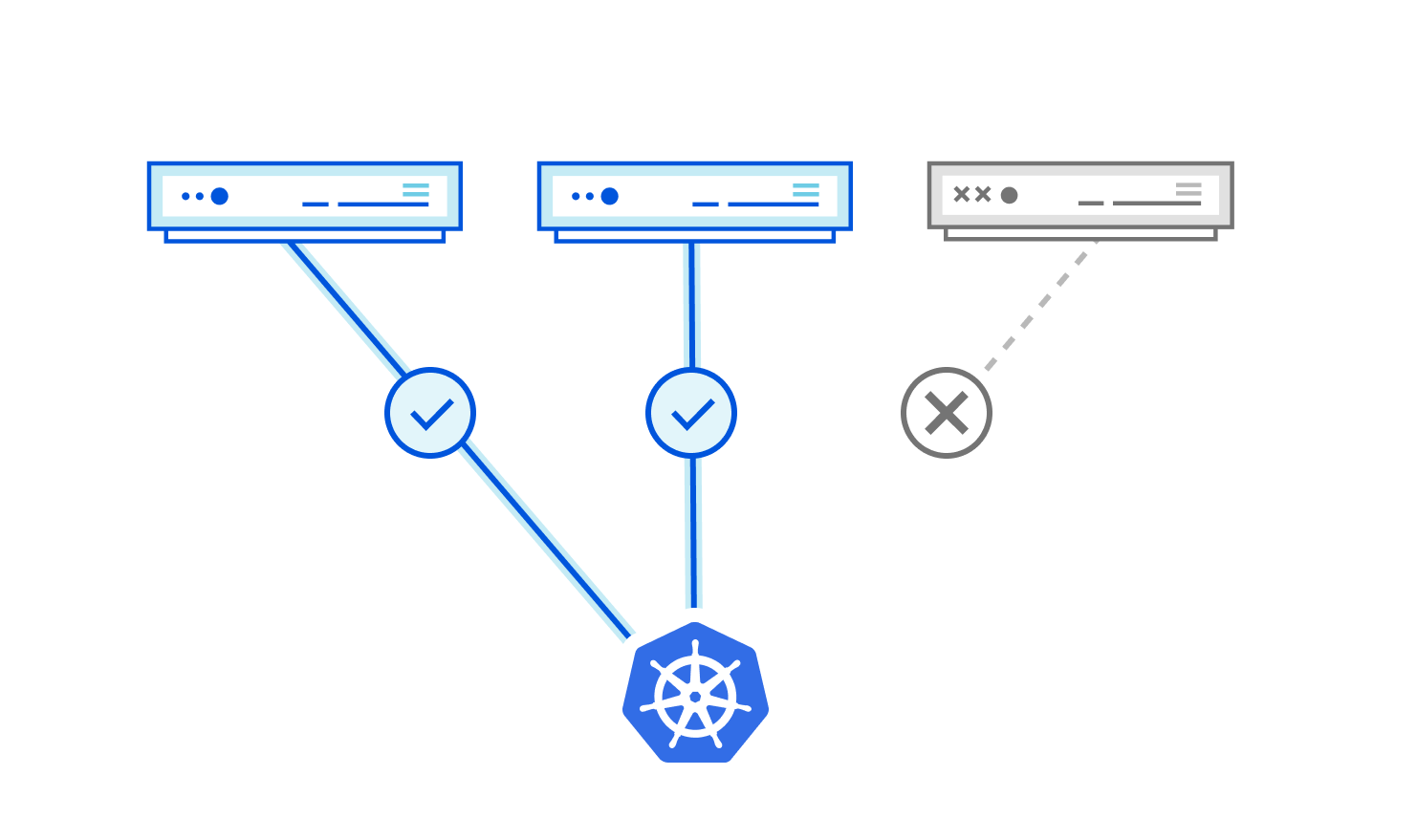
Kubernetes security policy design: 10 critical best practices
In this blog post, I will be looking at 10 best practices for Kubernetes security policy design. Application modernization is a strategic initiative that changes the way enterprises are doing business. The journey requires a significant investment in people, processes, and technology in order to achieve the desired business outcomes of accelerating the pace of innovation, optimizing cost, and improving an enterprise’s overall security posture. It is crucial to establish the right foundation from the beginning, to avoid the high cost of re-architecture. Developing a standard and scalable security design for your Kubernetes environment helps establish the framework for implementing the necessary checks, enforcement, and visibility to enable your strategic business objectives.
High-level design
Building a scalable Kubernetes security policy design requires that you adopt a fully cloud-native mindset that takes into account how your streamlined CI/CD process should enable security policy provisioning. A sound design would enable your enforcement and policy provisioning requirements in Day-N, while accommodating Day-1 requirements. The following list summarizes the fundamental requirements that a cloud-native security policy design should include:
- Segmentation of the control, management, and data planes
- Segmentation of deployment environments
- Multi-tenancy controls
- Application microsegmentation
- Cluster hardening
- Ingress access control
- Egress access control
- Continue reading
 I’ve just published the latest episode of Heavy Strategy with Johna Til-Johnson. In this episode we discuss five issues that we think IT Architects should be considered for 2021. The discussion on why and why not should be helpful for your own thinking and prepare you for discussions in your own organisations. You can find […]
I’ve just published the latest episode of Heavy Strategy with Johna Til-Johnson. In this episode we discuss five issues that we think IT Architects should be considered for 2021. The discussion on why and why not should be helpful for your own thinking and prepare you for discussions in your own organisations. You can find […]
 Pays bug bounty pittance, spends big on speculative product
Pays bug bounty pittance, spends big on speculative product