3 Reasons to Process Closer to the Edge
Being able to increase processing speeds will inevitably improve productivity and efficiency, but more importantly, edge computing will help with the management and use of data. In today's world and business environment, we have endless data being collected and transmitted.Mauritius Must Not Fall into the ‘Mass Surveillance’ Trap

This article was originally published in French in L’express. On 17 May, 2020, The Internet Society, alongside the IGF Mauritius, submitted a response to the call to the government of Mauritius’ call to provide input to the proposed amendments to the ICT ACT for regulating the use and addressing the abuse and misuse of Social Media […]
The post Mauritius Must Not Fall into the ‘Mass Surveillance’ Trap appeared first on Internet Society.
Video: Kubernetes Principles
After answering the “why should I care about Kubernetes?” question, Stuart Charlton explained the Kubernetes principles you should keep in mind if you want to have a chance of understanding what’s going on.
Video: Kubernetes Principles
After answering the “why should I care about Kubernetes?” question, Stuart Charlton explained the Kubernetes principles you should keep in mind if you want to have a chance of understanding what’s going on.
Cisco Meraki Claim Devices
Tune in for a fun fact about claiming Meraki devices in the Meraki portal. How To Claim Devices There are two ways to "claim" Meraki devices in the Meraki portal. via serial number via order number I found this out on a project where a couple of AP's were mounted on a 30ft high...continue reading
Learn from industry experts at the Kubernetes Security and Observability Summit—next week!
The Kubernetes Security and Observability Summit is only 1 week away! The industry’s first and only conference solely focused on Kubernetes security and observability will be taking place online June 3, 2021.
During the Summit, DevOps, SREs, platform architects, and security teams will enjoy the chance to network with industry experts and explore trends, strategies, and technologies for securing, observing and troubleshooting cloud-native applications.
What does security and observability mean in a cloud-native context? What challenges should Kubernetes practitioners anticipate and what opportunities should they investigate? Join us to explore these types of questions and gain valuable insight you’ll be able to take back to your teams.
Speakers & sessions
Tigera’s President & CEO, Ratan Tipirneni, will kick off the Summit with an opening keynote address. Two additional keynotes from Graeme Hay of Morgan Stanley and Keith Neilson of Discover Financial Services will follow. Attendees will then have the opportunity to attend breakout sessions organized into three tracks:
- Stories from the real world
- Best practices
- Under the hood
During these sessions, experts from industry-leading companies like Amazon, Box, Citi, EY, Mirantis, Morgan Stanley, PayPal, Salesforce, and of course, Tigera, will share real-world stories, best practices, and technical concepts related to Continue reading
Dennis Jennings and the History of NSFNET
The NSFNET followed the CSNET, connecting the campuses of several colleges and supercomputing systems with a 56K core in 1986. The NSFNET was the first large-scale implementation of Internet technologies in a complex environment of many independently operated networks, and forced the Internet community to iron out technical issues arising from the rapidly increasing number of computers and address many practical details of operations, management and conformance. The NSF eventually became the “seed” of the commercialized core of the Internet, playing an outsized role in the current design of routing, transport, and other Internet technologies.
In this episode of the History of Networking, Dennis Jennings joins Donald Sharp and Russ White to discuss the origins and operation of the NSFNET.
You can find out more about Dennis and the NSFNET in the following links.
https://internethalloffame.org/inductees/dennis-jennings
https://en.wikipedia.org/wiki/National_Science_Foundation_Network
https://www.nsf.gov/news/news_summ.jsp?cntn_id=103050
http://arvidc.weebly.com/nsfnet.html
Learn from industry experts at the Kubernetes Security and Observability Summit—next week!
The Kubernetes Security and Observability Summit is only 1 week away! The industry’s first and only conference solely focused on Kubernetes security and observability will be taking place online June 3, 2021.
During the Summit, DevOps, SREs, platform architects, and security teams will enjoy the chance to network with industry experts and explore trends, strategies, and technologies for securing, observing and troubleshooting cloud-native applications.
What does security and observability mean in a cloud-native context? What challenges should Kubernetes practitioners anticipate and what opportunities should they investigate? Join us to explore these types of questions and gain valuable insight you’ll be able to take back to your teams.
Speakers & sessions
Tigera’s President & CEO, Ratan Tipirneni, will kick off the Summit with an opening keynote address. Two additional keynotes from Graeme Hay of Morgan Stanley and Keith Neilson of Discover Financial Services will follow. Attendees will then have the opportunity to attend breakout sessions organized into three tracks:
- Stories from the real world
- Best practices
- Under the hood
During these sessions, experts from industry-leading companies like Amazon, Box, Citi, EY, Mirantis, Morgan Stanley, PayPal, Salesforce, and of course, Tigera, will share real-world stories, best practices, and technical concepts related to Continue reading
Multi-cloud is more about Tibco, SAP, Salesforce, Oracle etc than GCP/AWS/AZR.
 Off prem cloud has hype
Off prem cloud has hype
Matching 5G Demands with the Right Technology
The push for 5G-enabled apps reveals the need for data platforms to sync and scale across diverse networks. Are your applications ready to engage?African Women to Drive Digitalization and Transformation: AfChix and Internet Society Renew Partnership

African economies are making bold moves to speed up digitalization and transformation. We want women to play a key part in that. In a new partnership agreement, we are committing to closing the digital gender gap and helping women embrace technology to drive change. Africa’s growing Internet economy has the potential to contribute nearly $180 […]
The post African Women to Drive Digitalization and Transformation: AfChix and Internet Society Renew Partnership appeared first on Internet Society.
Local TCP Anycast Is Really Hard
Pete Lumbis and Network Ninja mentioned an interesting Unequal-Cost Multipathing (UCMP) data center use case in their comments to my UCMP-related blog posts: anycast servers.
Here’s a typical scenario they mentioned: a bunch of servers, randomly connected to multiple leaf switches, is offering a service on the same IP address (that’s where anycast comes from).
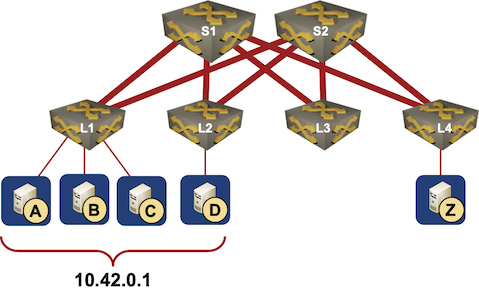
Typical Data Center Anycast Deployment
Local TCP Anycast Is Really Hard
Pete Lumbis and Network Ninja mentioned an interesting Unequal-Cost Multipathing (UCMP) data center use case in their comments to my UCMP-related blog posts: anycast servers.
Here’s a typical scenario they mentioned: a bunch of servers, randomly connected to multiple leaf switches, is offering a service on the same IP address (that’s where anycast comes from).

Typical Data Center Anycast Deployment
The Evolution of Labbing
A trip down memory lane on how things have changed in labbing from using prehistoric switches bought on eBay through emulators that took longer to configure than the labs to the present day solutions that can programmatically build a multi-vendor lab in minutes. Kids today don’t know they are born…..