0
Digital infrastructure outages get more costly
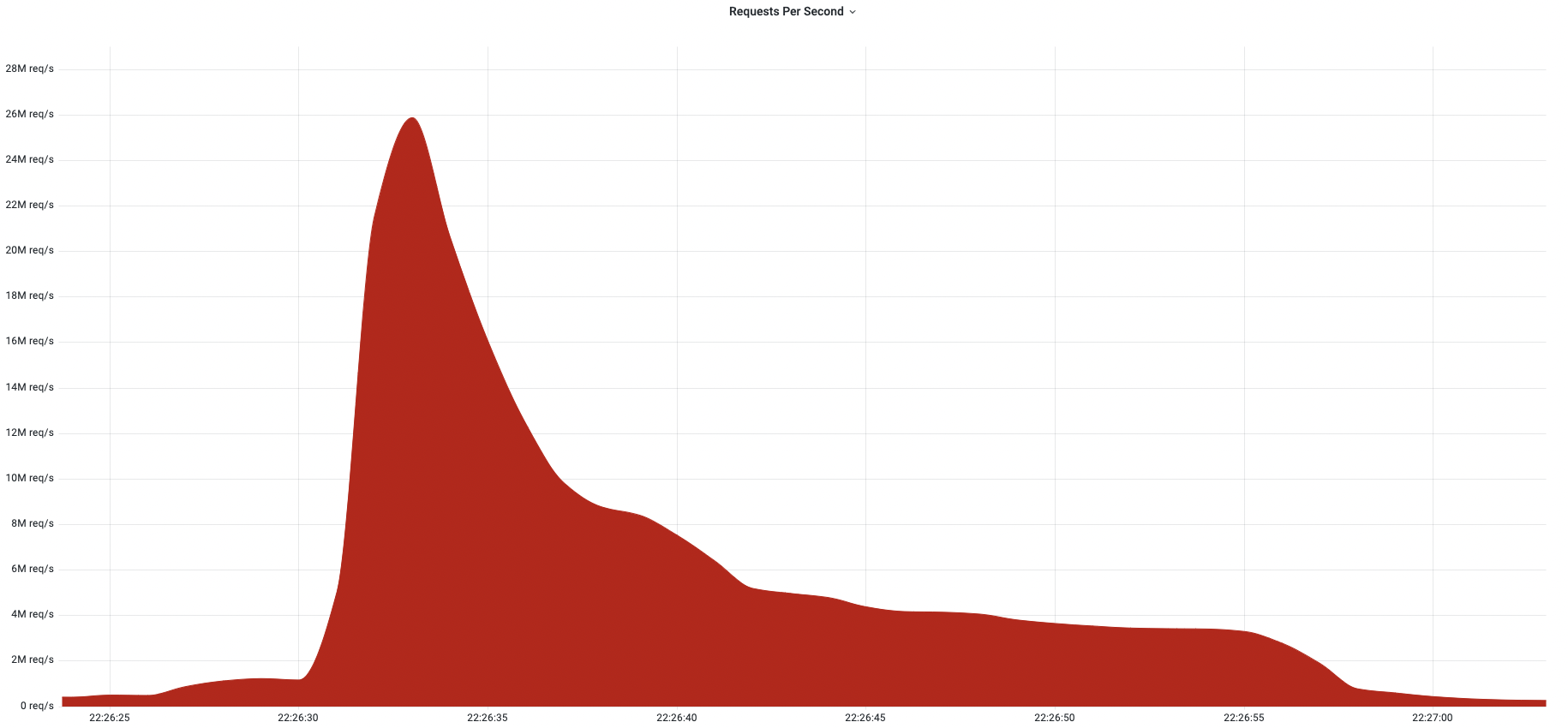
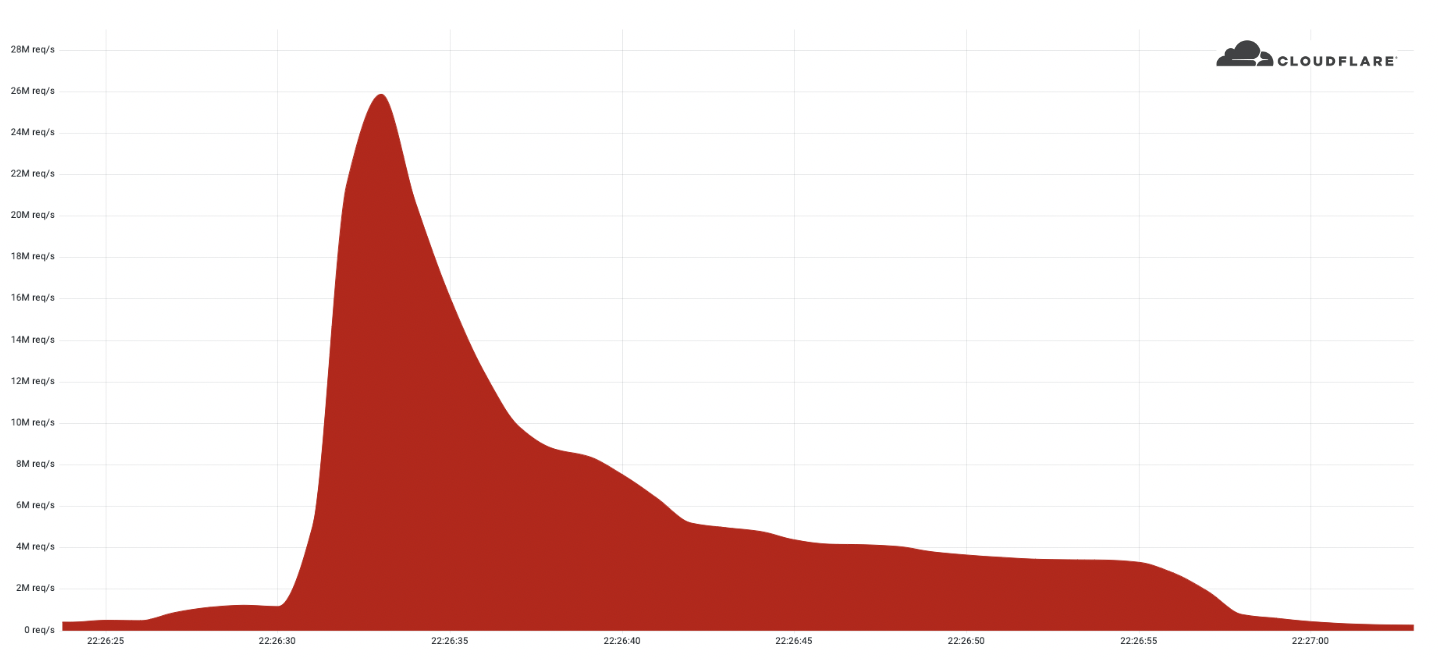
Digital infrastructure outages have gotten more and more expensive over the course of the past several years, according to a report from the Uptime Institute. Meanwhile, the total number of major outages has remained the same—meaning that, on average, an increasingly large amount of money is getting spent on recovering from each disruption.The proportion of individual outages resulting in losses of over $100,000 is increasing, according to the report, up to 47% of all outages in 2021 from 40% in the previous year. The institute said that, while it doesn't calculate an average overall cost per outage, overall trends are toward more costs being incurred by the average outage.To read this article in full, please click here