Announcing Tenant Control in Cloudflare Gateway


The tools we use at work are starting to look like the apps we use in our personal lives. We send emails for our jobs using Google Workspace and respond to personal notes in Gmail. We download PDFs from our team’s Dropbox and then upload images to our personal account. This can lead to confusion and mistakes—made worse by remote work when we forget to log off for the day.
Today, we’re excited to announce Tenant Control in Cloudflare Gateway, a new feature that helps keep our work at work. Organizations can deploy Cloudflare Gateway to their corporate devices and apply rules ensuring that employees can only log in to the corporate version of the tools they need. Now, teams can prevent users from logging in to the wrong instance of popular applications. What’s more, they can make sure corporate data stays within corporate accounts.
Controlling the application, alone, isn’t sufficient
Cloudflare Gateway provides security from threats on the Internet by sending all traffic leaving a device to Cloudflare’s network where it can be filtered. Organizations send traffic to Cloudflare by deploying the WARP agent, a WireGuard-based client built on feedback from our popular consumer app.

Cloudflare Gateway can be Continue reading
Lucky Web Framework Getting Started
I am a big fan of the web framework Ruby on Rails. Recently, I have been looking into the Crystal programming language and was excited to find out there are a couple of options for web frameworks similar in philosophy to Rails. One of those options is Lucky. "Lucky is a web...continue reading
Node JS and Yarn Install Ubuntu 2004
In this post I will show you how to install Node JS and the Yarn package manager on Ubuntu 2004 server. Software Used Ubuntu - 2004 server Node JS - v16.7.0 Yarn - 22.11 Install Node JS I am installing Node from the node source's distribution. Run the Node JS setup script from...continue reading
Lucky Web Framework Getting Started
I am a big fan of the web framework Ruby on Rails. Recently, I have been looking into the Crystal programming language and was excited to find out there are a couple of options for web frameworks similar in philosophy to Rails. One of those options is Lucky. "Lucky is a web...continue reading
Running Code
There was a discussion in a working group session at the recent IETF 111 meeting over a proposal that the working group should require at least two implementations of a draft before the working group would consider the document ready. What's going on here?kOps adds support for Calico’s eBPF data plane
Kubernetes operations (kOps) is one of the official Kubernetes (K8s) projects. The kOps project allows for rapid deployment of production-grade K8s clusters in multiple cloud platforms. By leveraging yaml manifests, kOps delivers a familiar experience to users who have worked with kubectl. Similar to K8s clusters in popular cloud platforms, kOps helps set up self-managed clusters to easily deliver high availability. Given its ease of use, it is a very popular choice when users want to deploy self-hosted Kubernetes clusters.
With the recent release of kOps (v1.19), support for the Calico eBPF data plane was added to the utility. In addition to the above-mentioned features, the latest kOps update offers an effortless way to autodeploy K8s clusters utilizing Project Calico for networking and the Calico eBPF data plane. Calico eBPF data plane implementation replaces kube-proxy and delivers equivalent functionality; it also leverages the most optimal datapath for traffic. These changes deliver a network performance boost and source IP preservation to your cluster.
In this blog post, we will showcase the steps required to deploy a cluster that utilizes these newly available features.
What is eBPF?
eBPF is a virtual machine embedded within the Linux kernel. Continue reading
Intel Finally Gets Chiplet Religion With Server Chips
When the top brass at Intel say that the “Sapphire Rapids” Xeon SP CPUs and “Ponte Vecchio” Xe HPC GPUs that are coming out early next year represent the “largest architectural shift in over a decade,” they ain’t kidding. …
Intel Finally Gets Chiplet Religion With Server Chips was written by Timothy Prickett Morgan at The Next Platform.
With AMX, Intel Adds AI/ML Sparkle to Sapphire Rapids
All processor designs are the result of a delicate balancing act, perhaps most touchy in the case of a high performance CPU that needs to be all things to users, whether they’re running large HPC simulations, handling transaction processing, dispatching training runs or whipping out inference results. …
With AMX, Intel Adds AI/ML Sparkle to Sapphire Rapids was written by Nicole Hemsoth at The Next Platform.
ShortestPathFirst finalizes partnership deal with Nutanix!
ShortestPathFirst finalizes partnership deal with Nutanix! Very exciting things on the horizon and we are beyond thrilled to offer this awesome technology to our customer base!Managing Mobile Devices in a New Era Of 5G LANs
As companies deploy unlicensed private cellular network technology, they face new challenges and opportunities in onboarding mobile devices.A Partnership to Advance Digital Rights and Internet Development in Africa

The Internet Society and CIPESA have commited to work together for an open, secure, and trustworthy Internet for Africa.
The post A Partnership to Advance Digital Rights and Internet Development in Africa appeared first on Internet Society.
How Alibaba Architects Around Massive Graph Complexity
Graph processing at hyperscale has historically been a challenge because of the sheer complexity of algorithms and graph workflows. …
How Alibaba Architects Around Massive Graph Complexity was written by Nicole Hemsoth at The Next Platform.
Building a Pet Cam using a Raspberry Pi, Cloudflare Tunnels and Teams


I adopted Ziggy in late 2020. It took me quite a while to get used to his routine and mix it with mine. He consistently jumped on the kitchen counter in search of food, albeit only when no one was around. And I only found out when he tossed the ceramic butter box. It shattered and made a loud bang in the late hours of the night. Thankfully, no one was asleep yet.
This got me thinking that I should keep an eye on his mischievous behaviour, even when I'm not physically at home. I briefly considered buying a pet cam, but I remembered I had bought a Raspberry Pi a few months before. It was hardly being used, and it had a case (like this) allowing a camera module to be added. I hadn’t found a use for the camera module — until now.
This was a perfect weekend project: I would set up my own pet cam, connect it to the Internet, and make it available for me to check from anywhere in the world. I also wanted to ensure that only I could access it and that it had some easy way to login, possibly using Continue reading
Cloudflare thwarts 17.2M rps DDoS attack — the largest ever reported
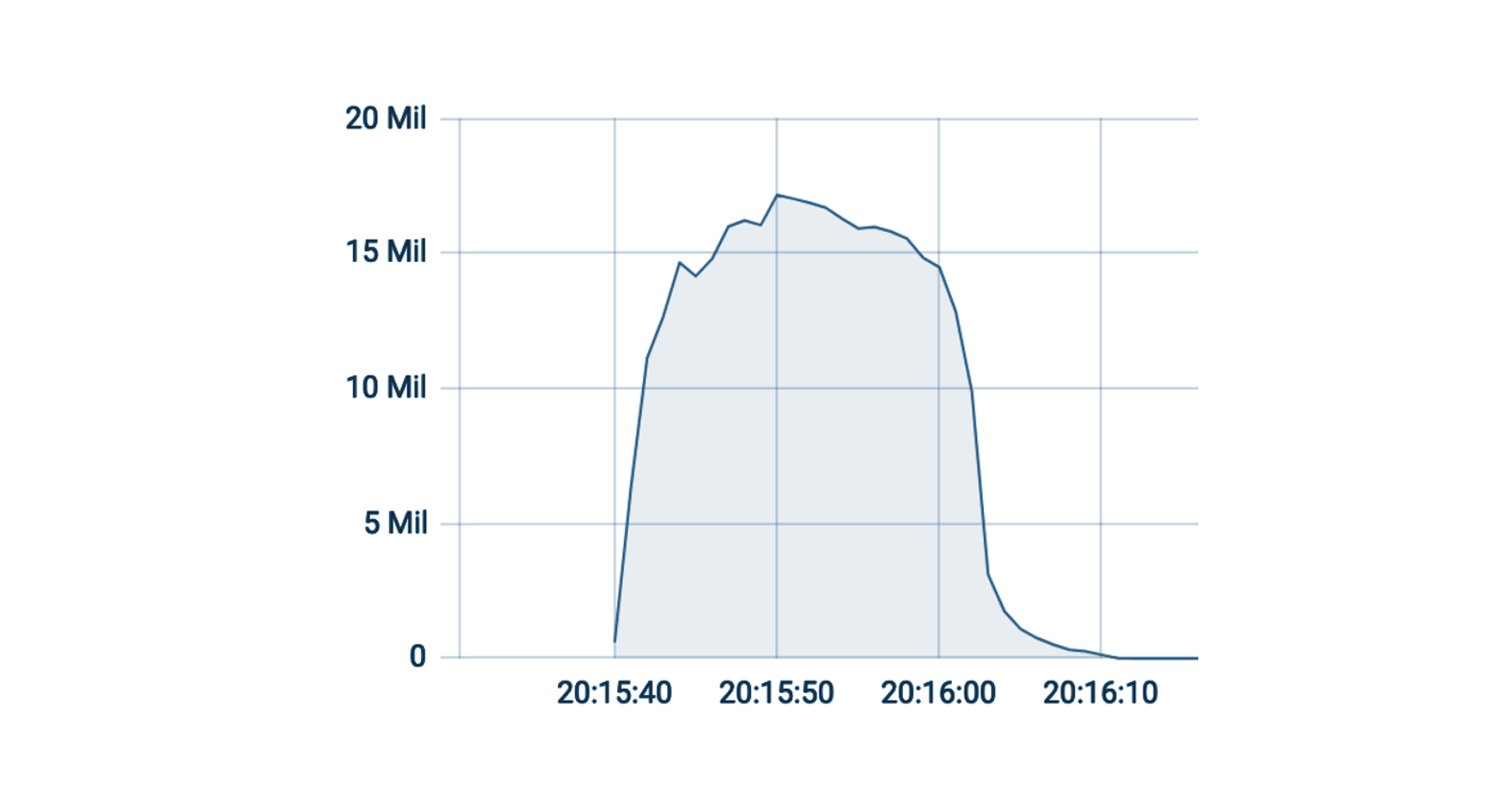
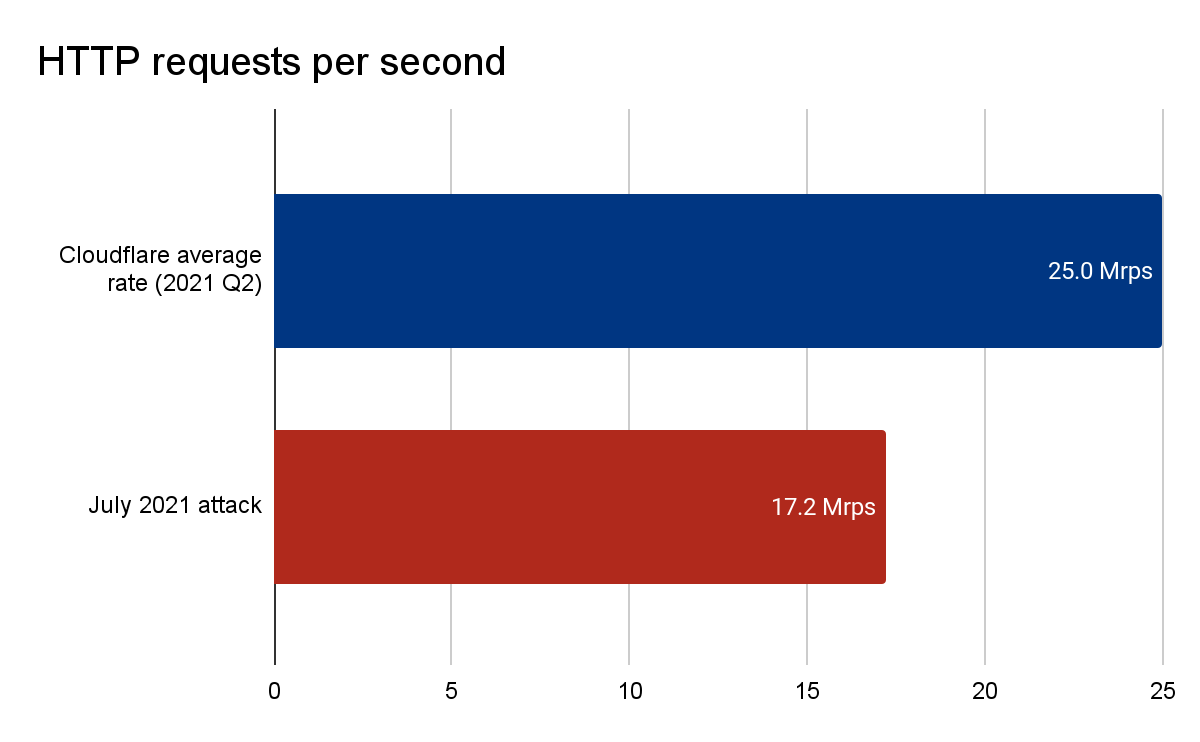
Earlier this summer, Cloudflare’s autonomous edge DDoS protection systems automatically detected and mitigated a 17.2 million request-per-second (rps) DDoS attack, an attack almost three times larger than any previous one that we're aware of. For perspective on how large this attack was: Cloudflare serves over 25 million HTTP requests per second on average. This refers to the average rate of legitimate traffic in 2021 Q2. So peaking at 17.2 million rps, this attack reached 68% of our Q2 average rps rate of legitimate HTTP traffic.
Automated DDoS mitigation with Cloudflare’s autonomous edge
This attack, along with the additional attacks provided in the next sections, were automatically detected and mitigated by our autonomous edge DDoS protection systems. The system is powered by our very own denial of service daemon (dosd). Dosd is a home-grown software-defined daemon. A unique dosd instance runs in every server in each one of our data centers around the world. Each dosd instance independently analyzes traffic samples out-of-path. Analyzing traffic out-of-path allows us to scan asynchronously for DDoS attacks without causing latency and impacting performance. DDoS findings are also shared between the Continue reading
Maybe Nvidia Should Buy VMware Instead Of Intel?
It is hard to imagine how anyone could run Nvidia better than it is being run right now. …
Maybe Nvidia Should Buy VMware Instead Of Intel? was written by Timothy Prickett Morgan at The Next Platform.