Heavy Networking 624: Solving Network Problems With Opmantek’s NMIS (Sponsored)
On today's sponsored Heavy Networking we speak with Opmantek, a FirstWave company. Opmantek's NMIS is a suite of network monitoring applications for managing fault, performance, configuration, compliance and automation. It supports multi-vendor, multi-tenant and multi-server solutions. We discuss the latest features and real-world use cases.
The post Heavy Networking 624: Solving Network Problems With Opmantek’s NMIS (Sponsored) appeared first on Packet Pushers.
Fast Friday Thoughts on Leadership

I’m once more taking part in the BSA Wood Badge leadership course for my local council. I enjoy the opportunity to hone my skills when it comes to leading others and teaching them how to train their own leaders. A lot of my content around coaching, mentoring, and even imposter syndrome has come from the lessons I’ve learned during Wood Badge. It sounds crazy but I enjoy taking vacation time to staff something that looks like work because it feels amazing!
A few random thoughts from the week:
- You need a sense of urgency in everything you do. You may not know exactly what’s coming or how to adjust for what needs to be done but you need to be moving with purpose to get it done. Not only does that help you with your vision to make things happen but it encourages others to do the same.
- Team building happens when you’re not focused entirely on the goal. It doesn’t take much for your group to come together but it can only happen when they aren’t charging toward the finish line. Remember that taking a few moments here and there to reinforce the group dynamic can do a lot Continue reading
Spectrum-4 Ethernet Leaps To 800G With Nvidia Circuits
When Nvidia announced a deal to buy Mellanox Technologies for $6.9 billion in March 2019, everyone spent a lot of time thinking about the synergies between the two companies and how networking was going to become an increasingly important part of the distributed systems that run HPC and AI workloads. …
Spectrum-4 Ethernet Leaps To 800G With Nvidia Circuits was written by Timothy Prickett Morgan at The Next Platform.
Putting Composability Through The Paces On HPC Systems
With HPC and AI workloads only getting larger and demanding more compute power and bandwidth capabilities, system architects are trying to map out the best ways to feed the beast as they ponder future systems. …
Putting Composability Through The Paces On HPC Systems was written by Jeffrey Burt at The Next Platform.
The end of the road for Cloudflare CAPTCHAs
There is no point in rehashing the fact that CAPTCHA provides a terrible user experience. It's been discussed in detail before on this blog, and countless times elsewhere. One of the creators of the CAPTCHA has publicly lamented that he “unwittingly created a system that was frittering away, in ten-second increments, millions of hours of a most precious resource: human brain cycles.” We don’t like them, and you don’t like them.
So we decided we’re going to stop using CAPTCHAs. Using an iterative platform approach, we have already reduced the number of CAPTCHAs we choose to serve by 91% over the past year.
Before we talk about how we did it, and how you can help, let's first start with a simple question.
Why in the world is CAPTCHA still used anyway?
If everyone agrees CAPTCHA is so bad, if there have been calls to get rid of it for 15 years, if the creator regrets creating it, why is it still widely used?
The frustrating truth is that CAPTCHA remains an effective tool for differentiating real human users from bots despite the existence of CAPTCHA-solving services. Of course, this comes with a huge trade off in terms Continue reading
Video: Combining Data-Link- and Network Layer Addresses
The previous videos in the How Networks Really Work webinar described some interesting details of data-link layer addresses and network layer addresses. Now for the final bit: how do we map an adjacent network address into a per-interface data link layer address?
If you answered ARP (or ND if you happen to be of IPv6 persuasion) you’re absolutely right… but is that the only way? Watch the Combining Data-Link- and Network Addresses video to find out.
Video: Combining Data-Link- and Network Layer Addresses
The previous videos in the How Networks Really Work webinar described some interesting details of data-link layer addresses and network layer addresses. Now for the final bit: how do we map an adjacent network address into a per-interface data link layer address?
If you answered ARP (or ND if you happen to be of IPv6 persuasion) you’re absolutely right… but is that the only way? Watch the Combining Data-Link- and Network Addresses video to find out.
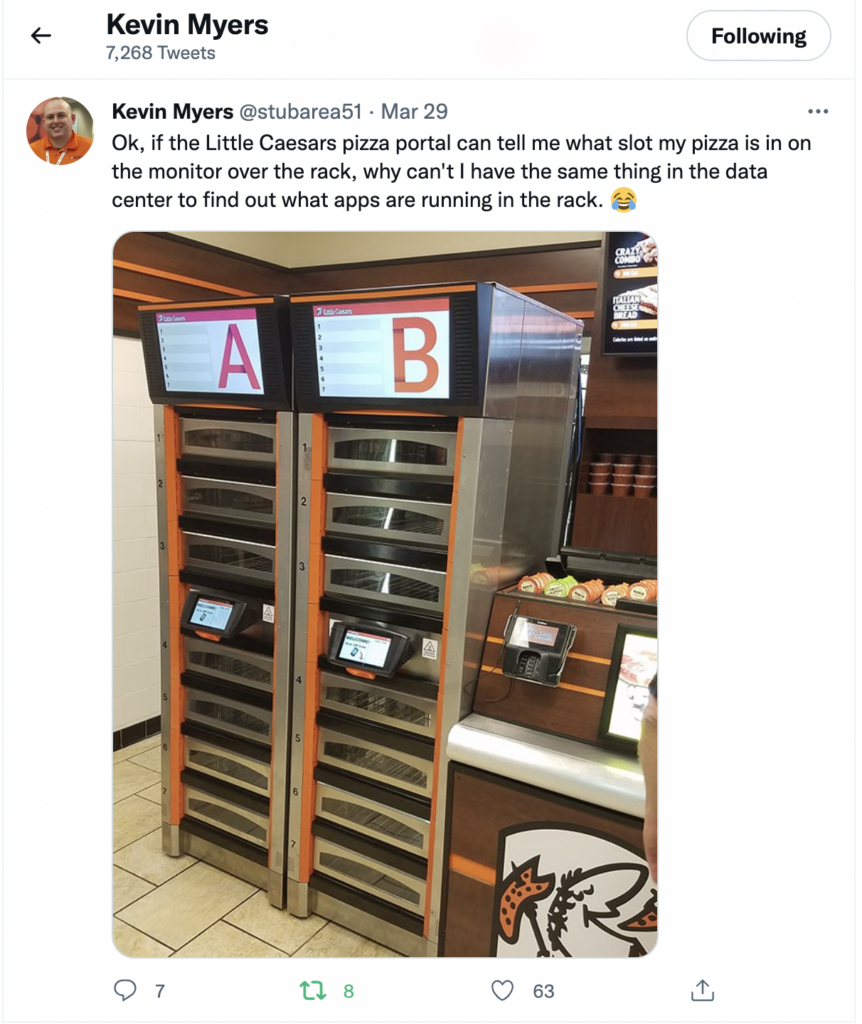
App delivery for an improved pizza experience
It’s been a while since we started work on one of our newest projects. We have been trying to solve a problem in app location. It all came from the notion that Little Caesars know where my pizza is, so why can’t the network resolve where the app is? We also thought it would be novel use of Anycast because the app can be anywhere.
So, what problems specifically have we solved using this design? Intent based gateways are a signaling mechanism allows the apps to be delivered along with the pizza. As we can see app Buffalo Wings can reach both the intent based gateway and Fried Pickles using TI-LFA, which strips the fat bits before they reach the gateway. Our unique caching solution using Tupperware, which are stacked in K8s, allows for the apps to be delivered in a bursty nexthop specific competitive manner. This has proven to keep the apps warm within the physical layer.
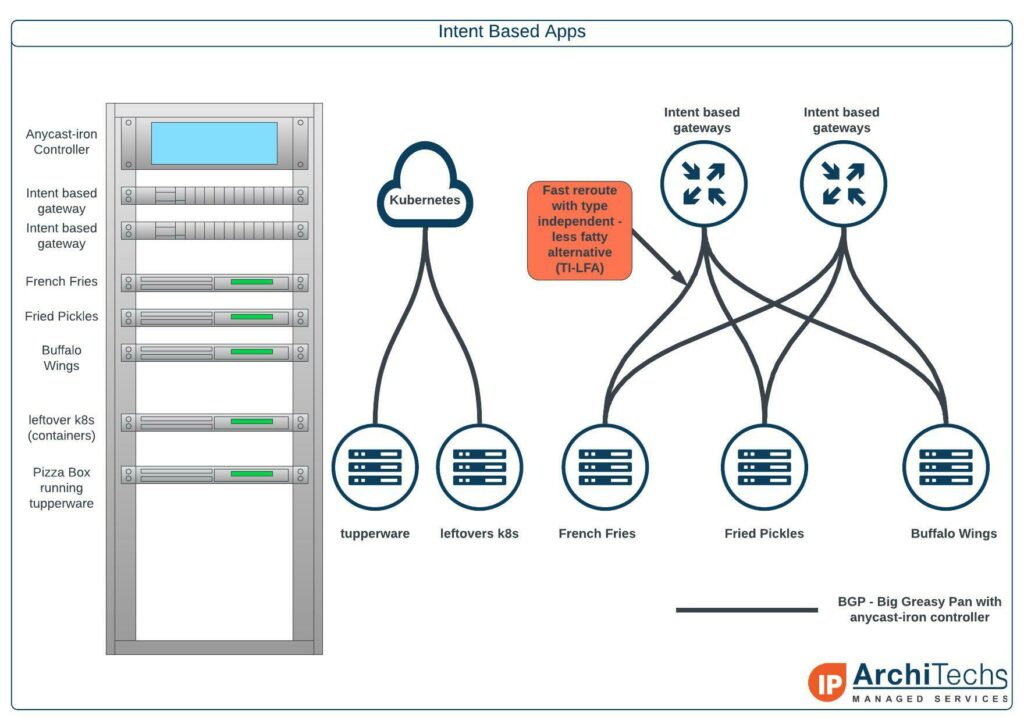
In our example, the Delivery Center Interconnect, we are doing an east to west Multi Pizza Layered Service that can drop the apps with full BTU into any of the regions. The apps are Continue reading
Infosec Useful Resources
This post is a collection of links to resources I have found useful on infosec related topics. CVE {{ link.href( path="https://www.exploit-db.com/", description="Exploit DB" ) }} - CVE compliant archive of public exploits and corresponding vulnerable software,...continue reading
Infosec Useful Resources
This post is a collection of links to resources I have found useful on infosec related topics. CVE {{ link.href( path="https://www.exploit-db.com/", description="Exploit DB" ) }} - CVE compliant archive of public exploits and corresponding vulnerable software,...continue reading
Deep Dive Into Nvidia’s “Hopper” GPU Architecture
With each passing generation of GPU accelerator engines from Nvidia, machine learning drives more and more of the architectural choices and changes and traditional HPC simulation and modeling drives less and less. …
Deep Dive Into Nvidia’s “Hopper” GPU Architecture was written by Timothy Prickett Morgan at The Next Platform.
A Walk-Through Of Fortinet’s Zero Trust Network Access (ZTNA) Architecture
Fortinet’s Zero Trust Network Access (ZTNA) lets network and security teams enforce fine-grained access policies for users working remotely and in the office. It can control access to applications hosted on premises, in the public cloud, or delivered via SaaS. This post walks through the elements required to deploy ZTNA and offers advice on transitioning to a zero-trust approach.
The post A Walk-Through Of Fortinet’s Zero Trust Network Access (ZTNA) Architecture appeared first on Packet Pushers.
A visual guide to Calico eBPF data plane validation
Validating the Calico eBPF Data Plane
In previous blog posts, my colleagues and I have introduced and explored the Calico eBPF data plane in detail, including learning how to validate that it is configured and running correctly. If you have the time, those are still a great read; you could dive in with the Calico eBPF Data Plane Deep-Dive.
However, sometimes a picture paints a thousand words! I was inspired by Daniele Polencic’s wonderful A Visual Guide on Troubleshooting Kubernetes Deployments. With his permission and kind encouragement, I decided to adapt the validation part of my previous deep-dive post to this easy-to-digest flowchart. Feel free to share it far and wide; wherever you think a Calico-learning colleague might benefit! It includes a link back here in case the diagram is updated in the future.

Next Steps
Did you know you can become a certified Calico operator? Learn container and Kubernetes networking and security fundamentals using Calico in this free, self-paced certification course.
There are additional level-two courses as well. One of them specifically addresses eBPF and the Calico eBPF data plane!
The post A visual guide to Calico eBPF data plane validation appeared first on Tigera.
Hedge 124: Geoff Huston and the State of BGP
Another year of massive growth in the number and speed of connections to the global Internet—what is the impact on the global routing table? Goeff Huston joins Donald Sharp and Russ White to discuss the current state of the BGP table, the changes in the last several years, where things might go, and what all of this means. This is part two of a two part episode.